当前位置:网站首页>Possible security vulnerabilities in NFT
Possible security vulnerabilities in NFT
2022-06-22 20:16:00 【Blockchain Star Club】
Blockchain 、NFT And others have been loved and trusted by people with high security , however , High security does not mean absolute security , There are always many loopholes in the Internet , Network hackers are eyeing it .
in fact , Even in places known for their safety NFT in , We have also encountered many cases of asset theft . Hackers use NFT Loopholes in smart contracts , Attack the user account or platform , Only this year , There have been several large-scale security incidents .

NFT There are two types of security vulnerabilities in , One is its own vulnerability , The other is the business vulnerability from the platform .
Its own loopholes
NFT The whole process includes casting 、 issue 、 The circulation 、 Destruction and other stages . There are basically no problems in the casting and destruction stages ,NFT The security problems of the company mainly focus on the issue and circulation .
NFT The circulation mainly involves the security of the circulation address , In this respect, there may be more “ phishing ” And other potential safety hazards , There are relatively few contractual loopholes .

The release phase is one of the most vulnerable phases . Generally speaking ,NFT The issue will be divided into pre-sale and formal sale . At pre-sale , The project party will provide users with pre-sale qualification through the white list . A common way is for hackers to exploit vulnerabilities in the white list , Bypass restrictions , Get pre sold NFT.
The platform's verification vulnerability to the white list led to NFT The project was attacked , such as APE Coin Airdrop incident 、NBA The two typical cases of the Hoover incident are the security problems caused by the white list vulnerability . The former is due to white list verification , Only verify that the user is right NFT The instantaneous state of ownership , Therefore, hackers use the method of lightning loan , A large number of NFT, After the final repayment of the lightning loan , Will make a profit APE Coin To transfer ; The latter is due to insufficient review when verifying the user's signature , Generally speaking , A signature can only be used once , but NBA Project party's NFT Verified vulnerability , Make the signature reusable , Finally, one signature can receive multiple NFT.
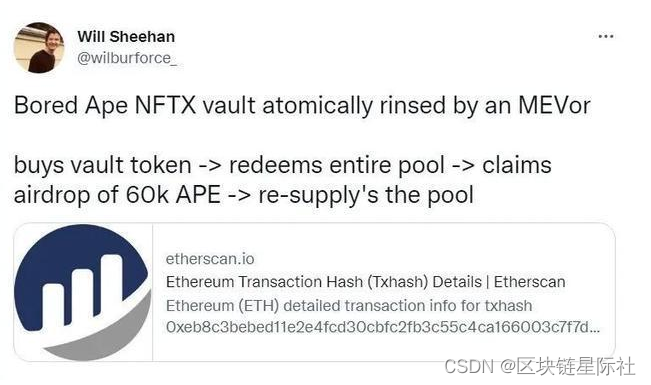
Platform vulnerabilities
NFT The platform is also vulnerable to vulnerabilities , The most typical one is right NFT The protocol standard for . Although they are collectively referred to as NFT, But not all NFT All adopt the same standard . classical ERC-721, It was born later ERC-1155、ERC-998 etc. , All are NFT Common protocol . such as TreasureDAO In a security incident , Just confused ERC-721 and ERC -1155 The difference between , It leads to logic confusion , Finally, it gives hackers an opportunity .
in addition , There are also platforms that will NFT As a kind of liquidity asset token or loan collateral, etc , If these platforms are used during business execution , Inspection is not fully considered - Interaction, etc , It is very easy to lead to loopholes in the business process , Security issues arise .
Summary
NFT The security incidents that occur from time to time in the market remind us , There is no absolute safety “ RIZ-ZOAWD ”. therefore , We are choosing NFT when , We should be more cautious , Do not invest blindly , At the same time, they also need to constantly enrich their relevant knowledge , Make it easier to avoid projects or platforms with potential security risks .
边栏推荐
- Which securities firm is better to choose for opening an account in flush? Is it safe to open a mobile account?
- 【深入理解TcaplusDB技术】TcaplusDB机型管理
- 【深入理解TcaplusDB技术】TcaplusDB 表管理——修改表
- NFT 中可能存在的安全漏洞
- Nlp-d57-nlp competition D26 & skimming questions D13 & reading papers & finding bugs for more than an hour
- 【深入理解TcaplusDB技术】创建游戏区
- Redis中的Multi事务
- 希尔排序
- Random talk about redis source code 122
- 北京大学|通过对比学习实现离线元强化学习的鲁棒任务表示
猜你喜欢
Redis持久化的几种方式——深入解析RDB

芯和半导体“射频EDA/滤波器设计平台”闪耀IMS2022
![[deeply understand tcapulusdb knowledge base] common problems in deploying tcapulusdb local](/img/2b/3ab5e247ac103728b4d3579c3c5468.png)
[deeply understand tcapulusdb knowledge base] common problems in deploying tcapulusdb local

510000 prize pool invites you to join the war! The second Alibaba cloud ECS cloudbuild developer competition is coming

【深入理解TcaplusDB技术】入门MySQL Driver
请你描述下从浏览器上输入一个url到呈现出页面的整个过程。

【深入理解TcaplusDB技术】TcaplusDB 表管理——清理表

【深入理解TcaplusDB技术】查看TcaplusDB线上运行情况

如何低成本快速搭建企业知识库?
![[compréhension approfondie de la base de connaissances tcaplusdb] déploiement de la version locale de tcaplusdb FAQ](/img/2b/3ab5e247ac103728b4d3579c3c5468.png)
[compréhension approfondie de la base de connaissances tcaplusdb] déploiement de la version locale de tcaplusdb FAQ
随机推荐
Search, insert and delete of binary sort tree
[deeply understand tcapulusdb technology] tcapulusdb table management - modify table
[deeply understand tcapulusdb technology] realize tcapulusdb transaction management in the operation and maintenance platform
年中大促 | 集成无忧,超值套餐 6 折起
NFT 中可能存在的安全漏洞
佐治亚理工学院|具有服务质量保证的多无人机野火协同覆盖和跟踪规划
ZABBIX learning notes (37)
程序员应该怎么查日期
[petty bourgeoisie database] break down the concept: data, database, database system, database management system, database technology
[in depth understanding of tcapulusdb technology] introduction tcapulusdb problem summary
Topological sorting
web技术分享| 【高德地图】实现自定义的轨迹回放
阿波罗使用注意事项
图的存储结构(邻接矩阵)
希尔排序
Metu stability and operation and maintenance guarantee scheme
What can the accelerated implementation of digital economy bring to SMEs?
Which securities firm is better to choose for opening an account in flush? Is it safe to open a mobile account?
Shell Sort
Random talk about redis source code 122
