当前位置:网站首页>MySQL master-slave replication
MySQL master-slave replication
2022-06-12 21:33:00 【Besieged city_ city with high walls】
Copy how it works
- master Log changes to binary log (binary log) in ( These records are called binary log events ,binary log events);
- slave take master Of binary log events Copy to its trunk log (relay log);
- slave Redo events in relay log , Will change the data that reflects itself .
The above is just an overview , In fact, every step is complicated 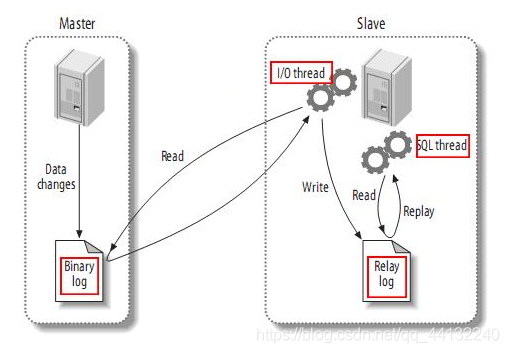
Configure replication
by MySQL Server configuration replication is very simple . But because of the different scenes , The basic steps are different . The most basic scenario is a completely new master library and slave library , In general, it is divided into the following steps :
- Create a replication account on each server .
- Configure the main database and the standby database .
- Notify the standby database to connect to the primary database and copy data from the primary database .
Let's assume that most of the configurations are default values , Both the primary database and the standby database are newly installed and have the same data ( Default MySQL database ) Next we show how to configure replication step by step : Suppose you have a server server1(IP Address 10.100.2.122) And the server server2(IP Address 10.100.2.143).
Create a copy account
MySQL Will give some special permissions to the replication thread . Running in the standby database I/O The thread will create a to the main library TCP/IP Connect , This means that you must create a user in the main library , And give them appropriate authority . For the library I/O The thread connects to the main library with this user name and reads its binary log . Create a user account with the following statement :
GRANT REPLICATION SLAVE, REPLICATION CLIENT ON *.*
TO [email protected]'10.100.2.%' IDENTIFIED BY 'p4ssword',;
We create this account in both the primary database and the standby database . Note that we restrict this account to the local network , Because this is a privileged account ( Although the account cannot be executed select Or modify data , But you can still get some data from the binary log ).
In fact, to copy an account, you only need to have REPLICATION SLAVE jurisdiction , You don't have to have... On each end of the server REPLICATION CLIENT jurisdiction , Then why do we give these two permissions to the master / All the spare parts are given ? There are two reasons for this :
- The accounts used to monitor and manage replication need to be REPLICATION CLIENT jurisdiction , And it's easier to use the same account for both purposes ( Instead of creating a separate account for a particular purpose ).
- If an account is established on the main database , When cloning data from the primary database to the secondary database , The standby database is set up —— The configuration needed to become the main library . In this way, the roles of the primary and standby databases can be easily exchanged if necessary .
This is the norm , But this is just a demonstration and case , The user was not created , Using two databases directly root Permission account
Configure the main database and the standby database
Next, you need to enable some settings on the main database , Suppose that the main database is a server server1, You need to open the binary log and specify a unique server ID(server ID), In the main warehouse my.ini(linux The system name is my.cnf) Add or modify the following contents in the document :
log-bin
server-id = 2
The actual value is up to you , This is just for simplicity , Of course, you can also set more required configurations . Using the default value may result in... With other servers ID Conflict , A common practice in the company is to use servers IP End of address 8 position , But make sure it is constant and unique ( for example , The servers are all in a subnet ). We'd better choose some meaningful conventions and follow them , But here it's free .
It should be noted that , my mysql Version is 5.7, In different systems , Different versions have different names , Such as log_bin,server_id; After the save , Don't forget to restart mysql Service makes it effective
The standby database also needs to be in my.ini Add similar configuration in , also You also need to restart the server .
log_bin
server_id = 1
read_only = 1
Technically , These options are not always necessary . For some of these options, we just explicitly list the default values . In fact only server_id It's necessary , because server-id The default is 1, So I haven't modified the slave library here . Here we also use log_bin, And uses the default name . Of course, if you like , It can also be set to other values .
Best use read_only configuration option , This option will prevent any threads without privileges from modifying data ( So it's best not to give users more permissions than they need ). but read_only Options are often not very practical , Especially for those applications that need to create tables in the standby database .
Start replication
We are executing this statement on the slave Library ,host Fill in the main database ip Address , The account password is the same , For the binary log file of the main library, we need show Just copy and paste ; The name can actually be configured , In the above log-bin Prefix can be configured in , Do not configure to use the device name as the prefix by default .
CHANGE MASTER TO MASTER_HOST='10.100.2.122',
MASTER_USER='root',
MASTER_PASSWORD='123456',
MASTER_LOG_FILE='DESKTOP-V351QGI-bin.000003',
MASTER_LOG_POS=0;
After execution , We can see Slave The state of , If there is any mistake, it will be in the result LAST_ERROR It shows that
SHOW SLAVE STATUS;
If there is no mistake , perform START SLAVE, Master-slave replication begins , The data inserted or modified in the master database will be asynchronously executed in the slave database ;
边栏推荐
- Can flush open an account? Can you directly open the security of securities companies on the app
- How do complex systems detect anomalies? North Carolina UNCC and others' latest overview of graph based deep learning anomaly detection methods in complex distributed systems describes the latest prog
- Zip压缩解压缩
- Limit of advanced mathematics
- A high-value MySQL management tool
- 好数对的求解
- Allegro Xile technology, a developer of distributed cloud services, received millions of dollars of angel round financing and was independently invested by Yaotu capital
- Smart management of green agriculture: a visual platform for agricultural product scheduling
- Lake shore PT-100 platinum resistance temperature sensor
- 选择排序
猜你喜欢

What's a good gift for the goddess Festival? Gift recommendation for the goddess Festival on March 8

@loadbalance annotation of resttemplate

How do complex systems detect anomalies? North Carolina UNCC and others' latest overview of graph based deep learning anomaly detection methods in complex distributed systems describes the latest prog

Shell script Basics

nn. PReLU(planes)

The ifeq, filter and strip of makefile are easy to use

结构体知识点all in

复杂系统如何检测异常?北卡UNCC等最新《复杂分布式系统中基于图的深度学习异常检测方法综述》,阐述最新图异常检测技术进展

#113 Path Sum II

My way of programming
随机推荐
zgc的垃圾收集的主要阶段
阅读笔记 Deep Hough Voting for 3D Object Detection in Point Clouds
DRF receives nested data and creates objects. Solution: DRF not NULL constraint failed
结构体知识点all in
递归调用知识点-包含例题求解二分查找、青蛙跳台阶、逆序输出、阶乘、斐波那契、汉诺塔。
Pointer and array & pointer and const & struct and Const
Pixel level reconstruction and restoration technology to solve severe image blur
Smart management of green agriculture: a visual platform for agricultural product scheduling
Teamwork collaboration application experience sharing | community essay solicitation
Lake shore PT-100 platinum resistance temperature sensor
Distributed cloud service developer'allegro Xile technology 'received an angel round financing of US $3million
ICML2022 | GALAXY:極化圖主動學習
Oracle 19c 安装文档
求解一维数组前缀和
Turing prize winner: what should I pay attention to if I want to succeed in my academic career?
CUDA out of memory
(4) Pyqt designs and implements the [factory production management system] order page - add, delete, modify and query (including source code analysis)
Common error in script execution: build sh: caller: not found
Can flush open an account? Can you directly open the security of securities companies on the app
Research Report on hydraulic solenoid valve industry - market status analysis and development prospect forecast