当前位置:网站首页>More than 40 Qualcomm chips have been exposed to security vulnerabilities, affecting billions of mobile phones!
More than 40 Qualcomm chips have been exposed to security vulnerabilities, affecting billions of mobile phones!
2022-07-24 16:17:00 【Xinzhixun】
4 month 28 Daily news , Recently, British security agencies NCC Group Announced a piece of heavy news : exceed 40 Qualcomm chips exist “ Bypass vulnerability ”, This vulnerability can be used to steal confidential information stored in the chip , And affect those who use related chips Android Mobile phones and other related devices . however , Earlier this month , Qualcomm has fixed this vulnerability that it learned last year .
According to Qualcomm safety bulletin , This number is CVE-2018-11976 A loophole in the , Involving Qualcomm chip security execution environment (Qualcomm Secure Execution Environment,QSEE) Elliptic curve digital signature algorithm (Elliptic Curve Digital Signature Algorithm,ECDSA), Will allow hackers to speculate that it is stored in QSEE in 、 With ECDSA Encrypted 224 Bit and 256 Bit key .
It is listed as a major vulnerability by Qualcomm , And the impact exceeds 40 Qualcomm chips , It may affect billions of Android Mobile phones and devices .
QSEE From Arm Of TrustZone Design ,TrustZone It is the safety core of the system single chip , It establishes an isolated security world for reliable software and confidential information , Other software can only be executed in the general world ,QSEE That is Qualcomm according to TrustZone Create a safe execution environment .
although ,NCC Group This vulnerability was discovered as early as last year , And last year 3 Qualcomm was notified in August , But Qualcomm has been until this year 4 Months before the official repair , And was officially exposed recently .
It is worth noting that , Last year Intel 、AMD、Arm Cortrex A series of chips have been exposed successively, and there are many security vulnerabilities , Although since then, each company has launched patches , However, this does not mean that similar events will not happen in the future . at that time ,ARM The person in charge also said , It's absolutely safe without , Chip vulnerabilities may occur again .
edit : Smart core - Woods
边栏推荐
- Yolov6 trains its own data set
- Lsyncd set up synchronous image - use lsyncd to realize real-time synchronization between local and remote servers
- Configuring WAPI certificate security policy for Huawei wireless devices
- Programming in CoDeSys to realize serial communication [based on raspberry pie 4B]
- Getting started with OpenMP
- Leetcode 220. duplicate element III exists
- leetcode:162. 寻找峰值【二分寻找峰值】
- Traverse, delete, judge whether JSON data is empty, and recursion
- Servlet framework (servlet+jsp) + addition, deletion, modification and query + paging implemented by MySQL (function package student information entry, addition, deletion, modification and query of st
- Leetcode 231. 2 的幂
猜你喜欢

With this machine learning drawing artifact, papers and blogs can get twice the result with half the effort!
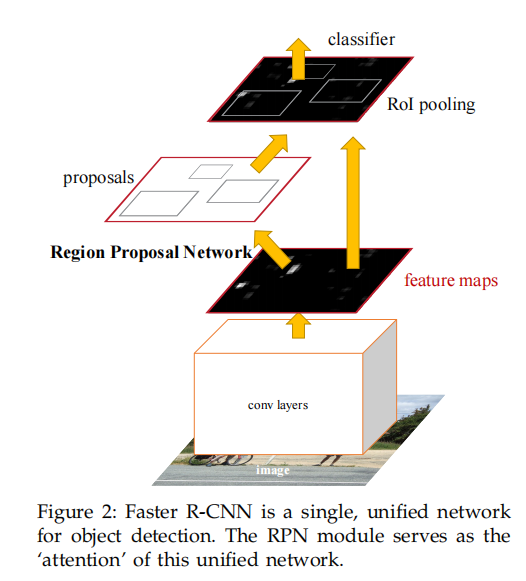
Fast RCNN trains its own data set

After data management, the quality is still poor

22 bracket generation
105 constructing binary trees from preorder and inorder traversal sequences

【LOJ3247】「USACO 2020.1 Platinum」Non-Decreasing Subsequences(DP,分治)

How to prevent XSS in PHP

31 next spread

Windows10 installation free redis

Knowledge points of MySQL (12)
随机推荐
Dynamics crm: how to set the order of forms
Leetcode:162. looking for peak [two points looking for peak]
自适应设计和响应式设计
2022 / 7 / 20 training record
About SQL data query statements
Yolov6 trains its own data set
287 finding duplicates
R language Visual facet chart, multivariable grouping nested multilevel t-test, and specify reference level, visual multivariable grouping nested multilevel faceting boxplot, and add significance leve
Vscode common shortcut keys
Leetcode 220. duplicate element III exists
My first blog
31 next spread
Best practices for preventing XSS in PHP web applications
AttributeError: module ‘seaborn‘ has no attribute ‘histplot‘
To create a private Ca, I use OpenSSL
REST风格
Yolov3 trains its own data set
Varnish4.0 cache agent configuration
TCP协议调试工具TcpEngine V1.3.0使用教程
Class assignment (6) - 575. Word division (word)