边栏推荐
猜你喜欢

DoS及攻击方法详解

Vue--vuerouter cache routing component

深层次安全定义剖析及加密技术

No manual prior is required! HKU & Tongji & lunarai & Kuangshi proposed self supervised visual representation learning based on semantic grouping, which significantly improved the tasks of target dete

RSA概念详解及工具推荐大全 - lmn

数据加密标准DES安全性
![[ten thousand words summary] starting from the end, analyze in detail how to fill in the college entrance examination volunteers](/img/77/715454c8203d722e246ed70e1fe0d8.png)
[ten thousand words summary] starting from the end, analyze in detail how to fill in the college entrance examination volunteers

Detailed explanation of asymmetric cryptosystem
IDEA收藏代码、快速打开favorites收藏窗口

Rich professional product lines, and Jiangling Ford Lingrui · Jijing version is listed
随机推荐
I want to know. I am in Zhaoqing. Where can I open an account? Is it safe to open an account online?
js强制转换
KDD 2022 | how to use comparative learning in cross domain recommendation?
清华&商汤&上海AI&CUHK提出Siamese Image Modeling,兼具linear probing和密集预测性能!
MySQL add column failed because there was data before, not null by default
Static registration and dynamic registration of JNI
Vscode usage - Remote SSH configuration description
行锁与隔离级别案例分析
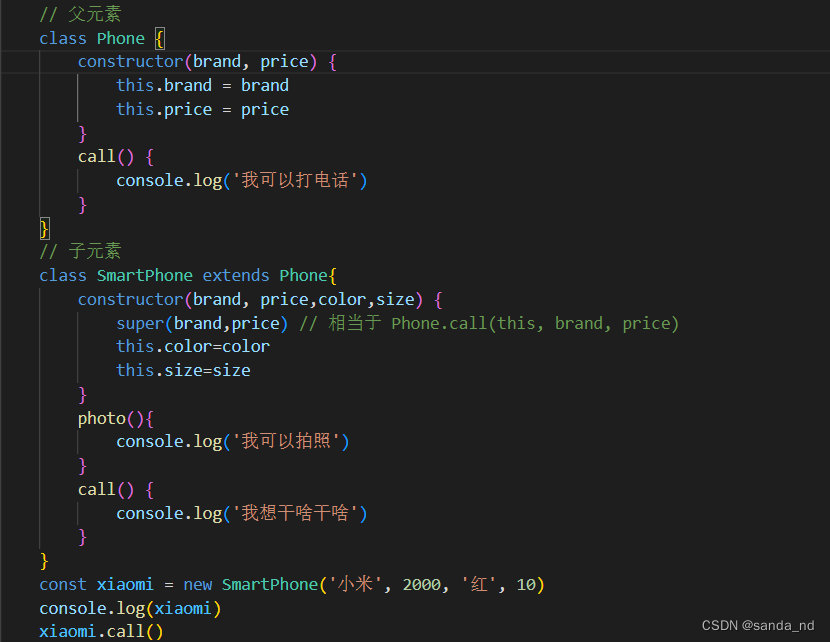
#25class的类继承
How about opening an account at Guojin securities? Is it safe?
MYSQL的下载与配置 mysql远程操控
KDD 2022 | 如何在跨域推荐中使用对比学习?
正则匹配相同字符
LeetCode——226. 翻轉二叉樹(BFS)
Row lock analysis and deadlock
Chen Qiang: Alibaba's 100 billion level large-scale digital business knowledge map helps business growth
Use middleware to record slow laravel requests
Detailed explanation of asymmetric cryptosystem
Strength and appearance Coexist -- an exclusive interview with Liu Yu, a member of Apache pulsar PMC
Analysis of deep security definition and encryption technology