当前位置:网站首页>Actual combat | a tortuous fishing counteraction
Actual combat | a tortuous fishing counteraction
2022-06-24 14:35:00 【Safety of 100 million people】
The article was first published in : The prophet community
https://xz.aliyun.com/t/11471
The origin of the story
It was a beautiful day , I am fishing , All of a sudden QQ A message pops up in the group , I'll open it up , I don't think it's easy . Here's the picture :
After scanning the code, I found that I jumped to QQ Email login interface , Identified as a phishing site , The domain name is http://kak2.cn.
Just type it here , The page jumps to the following interface .
good heavens , Young man, you are good at playing , Collection complete QQ Email account password , Then collect a wave of personal information , You can't be too greedy . Get to work !
Traceability Angler
We now have his domain name , Now collect the information about the domain name . Use the webmaster tool , Here's the picture .
You can find the name and email address of the domain name registrant . The mailbox is not displayed completely , Here, you can query by micro step . Here's the picture
Here are two things to focus on , Here I got the complete email address and knew that this is Alibaba cloud .
Check the mailbox , It is found that multiple domain names have been registered under this mailbox in May and June , The names are all liujuda , The probability is used for fishing .
Try to add QQ, It was found that this man could not be found , This is awkward .
The collection of information about anglers has come to an end , Next, start working on its website .
Attack phishing sites
We got the domain name before , Now infiltrate the site , What's the idea ? We can do a domain name 、 Directory scanning , If there is no information , Then start looking at the phishing site itself to see if it can be used .
First, scan the domain name , Nothing , Here's the picture :
Then start to scan the domain name , Here's the picture
The directory that came out , Basically no permission , All are 403. There is nothing to use .
Now it seems that we can only infiltrate the website itself , See if there is anything you can use . Now open the form for collecting personal information , Press F12 See if there is anything we should pay attention to , as follows :
The previous directory scan found uploads Directory but no permissions , We found it here uploads/ads route , Try whether the path back end receives files , Construct upload packets , send data , Still failed . as follows :
Don't lose heart. , Go on with , We also found that form Form submission data , Then I customized a function chk(), Now let's follow up this function and take a look at . as follows
Here we can learn , The website uses ajax For data transmission , Submit the data to the website wap Catalog , Then the ID number makes a simple regular judgment , Specify that the input is a number and the number of digits is 18 position . Now that the data is submitted to this site , Then, if the angler directly splices the parameters to when receiving data at the back end SQL In the sentence , Then there may be SQL Inject . Now let's construct the data , Submit data , Then grab the packets for testing , The captured packets are as follows :
Next, start testing for the presence of SQL Inject ,name Add a single quotation mark after the parameter , send data , Found an error , There is SQL Inject !
Guess the database name , Database version , structure payload
' and updatexml(1,concat(0x7e,(select database()),0x7e),1)%23
and updatexml(1,concat(0x7e,(select @@version,0x7e),1)%23The database name is a7, Guess the name of the watch , structure payload as follows
'and updatexml(1,concat(0x7e,(select table_name from information_schema.tables where table_schema='a7')),0)%23Found unable to get table name , I have a bad feeling .
Sure enough, I used some other functions , The table name cannot be obtained after discovery , Maybe I don't have permission . It's so sad , This old six .
Now use sqlmap Run for a while. , give the result as follows
Can only run out a7 This database ,information_schema This library cannot get , No wonder you can't get the table name by manual injection . alas , Now try os-shell Well , See if you're lucky . as follows
Looks like bad luck , failed . however , In spite of the failure , But we also know that the current server system is Linux, And have a path , Let's take it as an absolute path , make every possible effort , See if you can write to the file , structure payload:
into outfile '\\www\\wwwroot\\p******7.a******ka.cn\\config\\wap\\test.php' FIELDS TERMINATED BY '<?php phpinfo();?>'%23give the result as follows , Still failed .
Tried some other methods , Find that the harvest is not big .
the path winds along mountain ridges
Really can't take down its server ? I don't believe it , At night , Things are turning around , I was paddling , A friend application broke the peace , When I agree , Big brother doesn't talk much , direct URL And the account and password , The compressed package including the source code is also scanned out . Give me a cigarette here .
The master here also broadened my mind , Try a few more tools when scanning the directory , There may be different surprises . visit url Log in with your account and password , The interface is as follows .
After landing , We found that , This is an open source of the imperial backup king CMS. When we know it is open source , The first idea is whether there are some open loopholes on the Internet for us to use . For example, we can search like this EmpireBak v2010 backstage RCE, give the result as follows
The red arrow refers to this article , By reading the article , We also understand getshell The idea of , Is to replace the contents of the file . The specific process is that we can back up the data first , Then click Manage backup directory , Click Replace file contents .
The idea is to have , But there are still problems , The backup king is not linked mysql, The backup function cannot be used , But not in a hurry , Here the backup King provides a function , Parameter setting . as follows
If we know the database account password and database name , Can I try to connect to the database . So now the key is to get the database account and password . How to get this ? Don't forget , Before that, we got the source code compression package of the phishing website , Now let's unpack and analyze the source code . Look for the configuration file , There may be information we need . The source code directory is as follows
Now try to find the configuration file of the database , as follows , Sure enough, we got the information we wanted
Now go to the website and try to see if the connection is successful , Sure enough , Successful connection , as follows
Now you can try to take shell 了 . The pressure of drinking water is frightening , Synchronize the information with master , Fighting alone , How can it be worth the happiness of two people standing together .
Go backstage
Before we look at the source code , Found a a1 Folder , View folder related files , Know that this is the background path
Let's visit , Find out 404
It should have changed the background path , It doesn't matter , Let's simply try , Change the discovery to a7 了 , Now access a7 The interface is as follows
Or try to use backup Wang's account password , I found that the landing was successful
The backstage also won . Check the information , Most of them are dirty data . Go to ask the master if he has any information .
The address provided by the login master is as follows
There are still some data here , There are still people who have been cheated , Your personal information has been cheated , Finally, I input my mobile number , Received the verification code , Also submitted the verification code to the phishing website . Tencent's anti-theft mechanism , The second authentication can not stop many phishing websites . I would like to remind you to be vigilant , Be careful where you are prompted to enter your personal information .
Getshell
Now let's follow the previous train of thought Getshell, Compress first , Then download the compressed package .
And then there are new problems , The downloaded files are all empty ,
No data , So it can't be replaced , It's impossible Getshell 了 . What kind of human suffering is this . Now ask Master , Let's see what step master has taken .
It seems to be stuck , Don't lose heart. , Don't give up any details , Then go to the backup directory , Try downloading the original backup file , To view the .
Everything comes to him who waits , success .
Go to the following interface to replace , Fill in the original contents , Replace the contents with ice scorpion Trojan horse .
Trying to replace config.php The content of the document . I want to visit first , The Damascus interface appears unexpectedly , Master, I'm one step ahead of you ? Go and ask
It was really the work of the master , Unexpectedly, ice scorpion and Godzilla's horse have gone up , I love you . Ice scorpion , View the file management as follows
The way to raise power
We got it webshell, Completed the first step , Now it's time to raise the power , Ice scorpion provides us with a rebound shell The function of , Here we use the ice scorpion to shell Bounce to MSF in . Go and have a look at the master's progress .
Is this the feeling of the thigh ? It's so happy . Here is the idea of raising rights .msf There is one that can automatically raise the right suggester, We can choose directly , as follows
After selecting the first , Right to start !
Here we also successfully got the server root jurisdiction . Here's the picture
Get root It's easy to work with authority , View account , Also found ssh Port and account password , land ssh as follows :
Because phishing websites are built with pagodas , So here is the information about the pagoda , Include panel landing pages , Account numbers, passwords, etc . Great master has sorted out all the assets he got .
The first master sends the first json There is a leak in the document Access key We can directly take over relevant servers by using relevant tools .
There are tools available online , Here's the picture , Tool Links :https://github.com/mrknow001/aliyun-accesskey-Tools
Last , The master summed up the text attentively , Love the . Summed up the pagoda ,phpmyadmin,SSH And other related assets .
Summary
The relevant content about phishing websites is shared here , Let's start with the first one Web Weak password , To wear the phishing server , In the middle, there have been twists and turns , Finally, I was lucky to live up to my fate , I'll see you next time !
边栏推荐
- How to implement redis cache of highly paid programmers & interview questions series 115? How do I find a hot key? What are the possible problems with caching?
- Method of inputting dots under letters in markdown/latex
- Overview of SAP marketing cloud functions (III)
- Bert-whitening 向量降维及使用
- Successfully solved: selenium common. exceptions. SessionNotCreatedException: Message: session not created: This versi
- Stm32f1 and stm32cubeide programming examples -ws2812b full color LED driver (based on spi+dma)
- box-sizing
- 【环境搭建】zip 分卷压缩
- 阿里OSS对象存储服务
- 【Pytorch】量化
猜你喜欢

业务与技术双向结合构建银行数据安全管理体系

常见的缺陷管理工具——禅道,从安装到使用手把手教会你

同样是初级测试工程师,为啥他薪资高?会这几点面试必定出彩

Linux 安装 CenOS7 MySQL - 8.0.26

Method of establishing unity thermodynamic diagram
Laravel8 uses faker to call factory to fill data

如何避免下重复订单
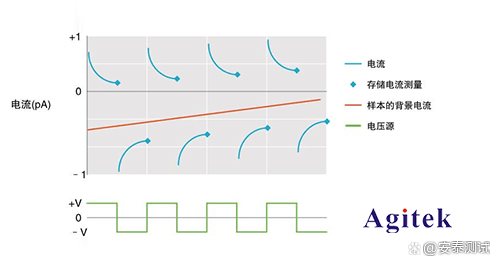
Wide measuring range of jishili electrometer

postgresql之词法分析简介

Unit contour creation method
随机推荐
3 ring kill 360 security guard process
postgresql之List
CVPR2022 | 可精簡域適應
常见的单例模式&简单工厂
Laravel8 uses faker to call factory to fill data
ssh-keygen 配置无需每次输入密码
Overview of SAP marketing cloud functions (IV)
Linux Installation cenos7 MySQL - 8.0.26
时间同步业务的闭环管理——时间监测
ES mapping之keyword;term查询添加keyword查询;更改mapping keyword类型
[pytoch] quantification
Successfully solved: selenium common. exceptions. SessionNotCreatedException: Message: session not created: This versi
CVPR2022 | 可精简域适应
openinstall携手书链:助力渠道数据分析,共创书联网时代
[sdx62] wcn685x IPA registration failure analysis and solution
Laravel 8 realizes auth login
在CVS中恢复到早期版本
IDEA 插件 Material Theme UI收费后的办法
Defeat the binary tree!
专精特新“小巨人”再启动,“企业上云”数字赋能