当前位置:网站首页>Secondary vocational network security skills competition P100 web penetration test
Secondary vocational network security skills competition P100 web penetration test
2022-07-25 03:22:00 【Beluga】
One 、 What is penetration testing
Penetration test (penetration testing) It is an authorization attack on computer system , To evaluate the system / The security of the network , Perform tests to identify vulnerabilities and their risks . generally speaking , The penetration test process is divided into five stages : Including identifying the target system 、 Detect the existing vulnerabilities and the availability of each vulnerability . The goal of penetration testing is to find as many vulnerabilities as possible , And deliver reports in a common format acceptable to customers .
Two 、 Penetration test type
White box (white box): In the white box test , The testee will generally provide the target system to the tester 、 The Internet 、 Application and other details ( Including account number 、 password 、SSH/Telnet login information 、 framework 、 Network structure 、 Source code … … wait ).
Black box (black box): Test simulating the attacker scenario . Act as a real attacker's perspective , There is no information about the target system ( White box test description ), The biggest feature of this test is that the tester will pay more attention to the first stage of penetration test —— information gathering . The more information you collect , The better the effect of post test .
Gray box (gray box): Between black and white box test , In a typical gray box test , The tester will know the relevant target system in advance 、 Applications 、 Internet Information … … wait . This kind of test is usually applicable to organizations with time limit requirements , The tested person provides effective information , Testers can focus on systems that are more risky , Save the early information collection time .
3、 ... and 、 Penetration test phase
according to Harpreet Singh、Himanshu Sharma Professional description of others , The infiltration process can be divided into the following stages :
Stage 1: Information collection and investigation
Stage 2: enumeration
边栏推荐
- Canvas record
- C language introduction practice (9): completion judgment
- Resolve the error: org.apache.ibatis.binding.bindingexception
- Error: tomee required to support ear/ejb deployment
- How is the virtual DOM different from the actual DOM?
- Task02 | EDA initial experience
- Li Kou 343 integer partition dynamic programming
- mysql_ Backup restore_ Specify table_ Backup table_ Restore table_ innobackup
- Swagger key configuration items
- NC | progress has been made in the study of the ecological network relationship between dissolved organic carbon and microorganisms in the context of global change
猜你喜欢
![[template engine] microservice Learning Notes 6: freemaker](/img/6a/cfe9c5aea0f7fc83d0812237de2256.png)
[template engine] microservice Learning Notes 6: freemaker

Bgy development small example
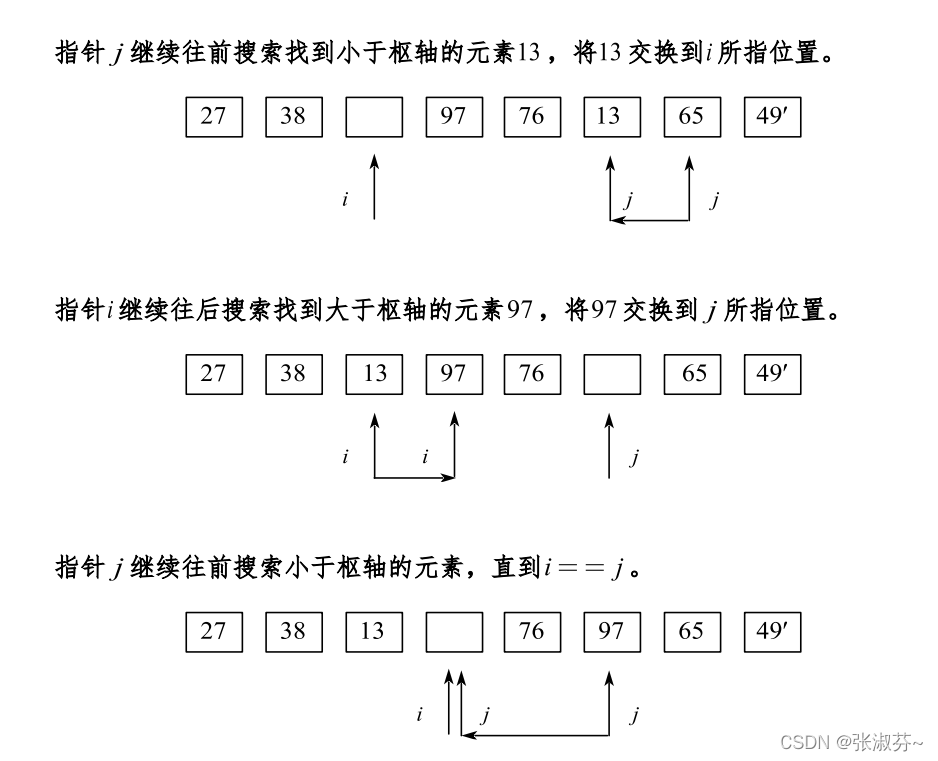
Merge sort / quick sort
How does Jupiter notebook change themes and font sizes?

Chrome process architecture
Banana pie bpi-m5 toss record (2) -- compile u-boot

Detailed explanation of three factory modes

Use reflection to convert RDD to dataframe

55k is stable, and the recommendation system will always drop God!
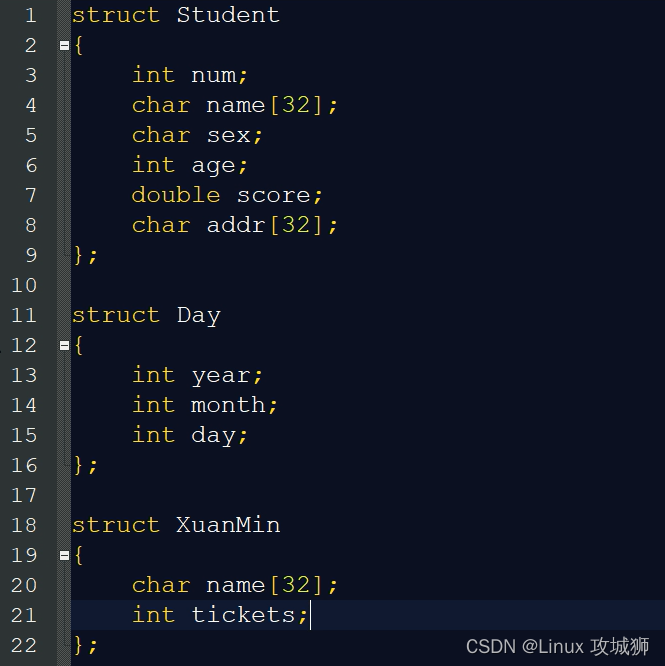
C language_ Structure introduction
随机推荐
JS method encapsulation summary
Learning record 12
Bubble sort / heap sort
Riotboard development board series notes (VIII) -- building desktop system
File permission management
Use and introduction of vim file editor
Openlayers ol ext: Transform object, rotate, stretch, zoom in
Node queries the path of all files (files or folders) named filename under the target directory
Color space (2) -- YUV
Chrome process architecture
Backtracking to solve subset problem
Question B: shunzi date
NC | progress has been made in the study of the ecological network relationship between dissolved organic carbon and microorganisms in the context of global change
Message queue (MQ)
The dolphin scheduler calls the shell script and passes multiple parameters
ES6 - study notes
ECMAScript new features
A 20 yuan facial cleanser sold tens of thousands in seven days. How did they do it?
A. Subtle Substring Subtraction
Reasons for not sending requests after uni app packaging