当前位置:网站首页>Data Encryption Standard DES security
Data Encryption Standard DES security
2022-06-26 17:50:00 【lmn_】

Even though DES Cryptanalysis has more information than other block ciphers , But by far the most practical attack is still brute force .
Brute force attack
There's a lot about DES Password attack techniques have been made public , The brute force method is one of the most effective attacks ,

Brute force attack can be understood as the commonly known brute force attack , It usually appears when the user name and password are exploded , Once the existing user name is determined , Many attackers will try to return the size of the packet echo , Content, etc. , Crack the password through brute force attack , The length of the key determines the number of possible keys , This determines the feasibility of this method .
DES History of cracking machine
Neither of the following two early proposals has been publicly recognized :
- 1977 year ,Diffie and Hellman A value of about 2000 A million dollar machine , Can be found in a day DES secret key .
- 1993 year ,Wiener Put forward a kind of value 100 Million dollar key search machine , Can be in 7 Key found within hours .
1990 In the late S, some people began to pay attention to DES The vulnerability of ,
- 1997 year ,RSA Security Sponsored a series of competitions , To the first crack game DES The team that encrypts the message provides 10,000 Dollar bonus .
- Quick crack DES The feasibility of 1998 It was confirmed in , At that time, the Electronic Frontier Foundation, a civil rights organization in cyberspace (EFF) Built a custom DES Cracker , The cost is about 250,000 dollar .

- 2006 Developed by the teams of Bohong University and Kiel University in DES The cracker was built in Germany COPACOBANA machine .
COPACOBANA Commercially available 、 Reconfigurable integrated circuit composition ,COPACOBANA The cost of a machine is about 10,000 dollar , And EFF Compared with machines , The cost has been reduced by about 25 times , This is an example of the continuous improvement of digital hardware .
Differential cryptanalysis (DC)
Eli Biham and Adi Shamir stay 1980 It was rediscovered in the late s DC( Differential cryptanalysis ), To crack the complete 16 round , Differential cryptanalysis requires 2 Of 47 To the power of a choice of plaintext ,DES Designed to resist DC.
Linear cryptanalysis (LC)
Mitsuru Matsui Linear cryptanalysis was discovered (LC), This technology requires 2 Of 43 Power known plaintext , Was the first to be reported DES Experimental cryptanalysis .
Davies attack
80 years ,Donald Davies For the first time Davies attack ,Davies An attack is a specialized DES Technology is also a technology that only applies to DES Special attacks on (LC and DC It belongs to a general attack of many algorithms ).
Davies The attack requires 2 Of 50 Power known plaintext , The success rate is about 51%.
边栏推荐
- Concurrent thread safety
- 解决pycharm里面每个字母占一格空格的问题
- SIGIR 2022 | University of Hong Kong and others proposed the application of hypergraph comparative learning in Recommendation System
- 10 cloud security best practices that enterprises need to know
- Various types of gypsum PBR multi-channel mapping materials, please collect them quickly!
- SIGIR 2022 | 港大等提出超图对比学习在推荐系统中的应用
- 股票开账户如何优惠开户?现在在线开户安全么?
- ACL 2022 | 基于神经标签搜索的零样本多语言抽取式文本摘要
- 在国金证券开户怎么样?保障安全吗?
- 陈强:阿里千亿级大规模数字商业知识图谱助力业务增长
猜你喜欢

【推荐系统学习】推荐系统架构
![[buuctf.reverse] 126-130](/img/df/e35633d85caeff1dece62a66cb7804.png)
[buuctf.reverse] 126-130

Notes on flowus

9、智慧交通项目(2)

Synchronized description of concurrency

MySQL add column failed because there was data before, not null by default

Platform management background and merchant menu resource management: Design of platform management background data service
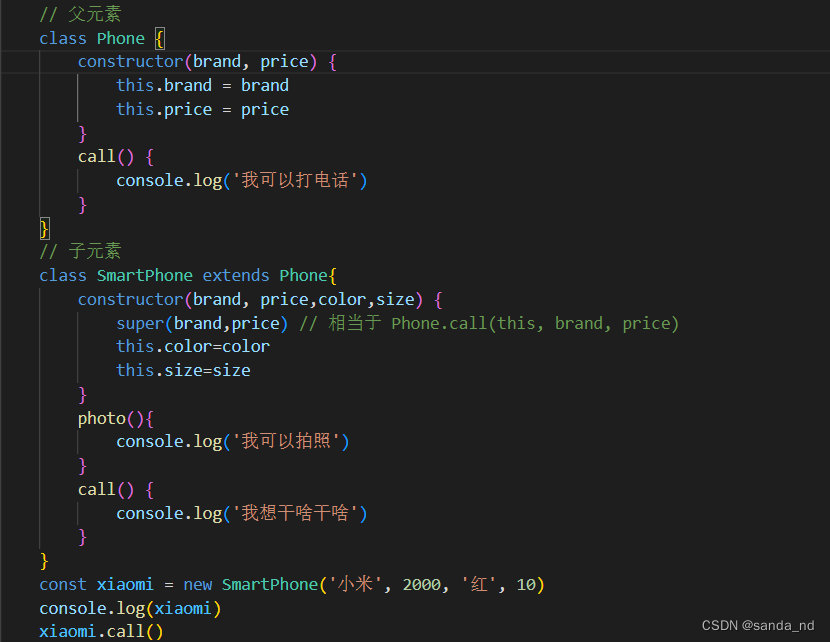
#25class的类继承

Leetcode - 226. Retourner l'arbre binaire (bfs)
Which low code platform is more friendly to Xiaobai? Here comes the professional evaluation!
随机推荐
KDD 2022 | how to use comparative learning in cross domain recommendation?
halcon之区域:多种区域(Region)特征(5)
DoS及攻擊方法詳解
QPushButton 样式使用示例(以及按钮setmenu添加下拉菜单的方法)
并发之线程安全
分布式架构概述
Microservice architecture practice: business management background and SSO design: SSO design
[buuctf.reverse] 126-130
next(iter(dataloader))的一点点体会
你好,现在网上股票开户买股票安全吗?
SIGIR 2022 | University of Hong Kong and others proposed the application of hypergraph comparative learning in Recommendation System
接水面试题
Leetcode topic [array] -268- missing numbers
wechat_微信小程序中解决navigator进行页面跳转并传递参数问题
腾讯钱智明:信息流业务中的预训练方法探索与应用实践
Concurrent thread safety
Viteconfigure project path alias
Niuke network: Design LRU cache structure design LFU cache structure
手写promise.all
Leetcode HOT100 (22--- bracket generation)