当前位置:网站首页>多项式承诺Polynomial commitment方案汇总
多项式承诺Polynomial commitment方案汇总
2022-07-23 09:53:00 【mutourend】
1. 引言

上图源自 Vitalik 2021年11月博客 Halo and more: exploring incremental verification and SNARKs without pairings。
目前的多项式承诺Polynomial commitment方案主要有:
- Kate polynomial commitment:具体可参见Dankrad Feist的介绍 Kate polynomial commitments
- Bulletproofs commitment:具体可参见curve25519-dalek团队的介绍 Module bulletproofs:: notes::inner_product_proof
- FRI (Fast Reed-Solomon Interactive Oracle Proofs of Proximity):具体可参见V神的介绍 STARKs, Part II: Thank Goodness It’s FRI-day
其中,Kate polynomial commitment需要用到 elliptic curve pairing。
相对来说,FRI更容易理解。
2. Kate多项式承诺
Kate多项式承诺又称KZG承诺,基于pairing曲线构建,满足bilinear属性:
详细的Kate多项式承诺方案见Kate等人2010年论文《Constant-Size Commitments to Polynomials and Their Applications》:
3. Bulletproofs多项式承诺
见博客 Halo: Recursive Proof Composition without a Trusted Setup 学习笔记 中“3. Polynomial commitments”:
假设polynomial p ( X ) p(X) p(X) 的degree bound为 d − 1 d-1 d−1,则:
- S e t u p ( 1 λ , d ) Setup(1^{\lambda}, d) Setup(1λ,d):输出为common reference string σ = ( G , F p , G ⃗ , H ) \sigma=(\mathbb{G},\mathbb{F}_p,\vec{G},H) σ=(G,Fp,G,H) for group G \mathbb{G} G of prime order p p p, with random G ⃗ ∈ G d \vec{G}\in\mathbb{G}^d G∈Gd and H ∈ G H\in\mathbb{G} H∈G。
- C o m m i t ( σ , p ( X ) ; r ) = < a ⃗ , G ⃗ > + [ r ] H Commit(\sigma,p(X);r)=<\vec{a},\vec{G}>+[r]H Commit(σ,p(X);r)=<a,G>+[r]H,其中 r r r为blinding factor, a i ∈ F a_i\in\mathbb{F} ai∈F为多项式 p ( X ) p(X) p(X)的 i i ith degree term 系数, p ( X ) ∈ F p [ X ] p(X)\in\mathbb{F}_p[X] p(X)∈Fp[X]为maximal degree d − 1 d-1 d−1。可将其看成是对多项式系数的Pedersen vector commitment,具有很好的hiding和加法同态属性——对于 ∀ a , b , r , s ∈ F p , p ( X ) , q ( X ) ∈ F p [ X ] \forall a,b,r,s\in\mathbb{F}_p, p(X),q(X)\in\mathbb{F}_p[X] ∀a,b,r,s∈Fp,p(X),q(X)∈Fp[X],有:
[ a ] C o m m i t ( σ , p ( X ) ; r ) + [ b ] C o m m i t ( σ , q ( X ) ; s ) = C o m m i t ( σ , a ⋅ p ( X ) + b ⋅ q ( X ) ; a r + b s ) [a]Commit(\sigma,p(X);r)+[b]Commit(\sigma,q(X);s)=Commit(\sigma,a\cdot p(X)+b\cdot q(X); ar+bs) [a]Commit(σ,p(X);r)+[b]Commit(σ,q(X);s)=Commit(σ,a⋅p(X)+b⋅q(X);ar+bs) - O p e n ( p ( X ) , x ) Open(p(X),x) Open(p(X),x):输出为 v ∈ F p v\in\mathbb{F}_p v∈Fp。
- V e r i f y O p e n ( P , x , v ) VerifyOpen(P,x,v) VerifyOpen(P,x,v):判断the polynomial contained “inside” the commitment P P P evaluates to v v v at x x x。输出为1表示接受,0表示拒绝。
然后可将 ( S e t u p , O p e n , V e r i f y O p e n ) (Setup,Open,VerifyOpen) (Setup,Open,VerifyOpen)看成是a PSHVZK (perfect special honest-verifier zero knowledge) argument of knowledge for the relation:
{ ( ( P , x , v ) : ( a ⃗ , r ) ) : P = < a ⃗ , G ⃗ > + [ r ] H ∧ v = < a ⃗ , ( 1 , x , x 2 , ⋯ , x d − 1 ) > } \{((P,x,v):(\vec{a},r)): P=<\vec{a},\vec{G}>+[r]H\wedge v=<\vec{a},(1,x,x^2,\cdots,x^{d-1})>\} {((P,x,v):(a,r)):P=<a,G>+[r]H∧v=<a,(1,x,x2,⋯,xd−1)>}
以上relation 可用于证明 the polynomial contained “inside” the commitment P P P evaluates to v v v at x x x,甚至 the committed polynomial has maximum degree d − 1 d-1 d−1。
基本信息展开为:
- public info: P ∈ G , x , v ∈ F p P\in\mathbb{G},x,v\in\mathbb{F}_p P∈G,x,v∈Fp
- private info: a ⃗ ∈ F p n , r ∈ F p \vec{a}\in\mathbb{F}_p^n,r\in\mathbb{F}_p a∈Fpn,r∈Fp
- relation: P = < a ⃗ , G ⃗ > + [ r ] H ∧ v = < a ⃗ , ( 1 , x , x 2 , ⋯ , x d − 1 ) > P=<\vec{a},\vec{G}>+[r]H\wedge v=<\vec{a},(1,x,x^2,\cdots,x^{d-1})> P=<a,G>+[r]H∧v=<a,(1,x,x2,⋯,xd−1)>
详细的思路为:
- Verifier:生成随机group element U ∈ G U\in\mathbb{G} U∈G,将 U ∈ G U\in\mathbb{G} U∈G发送给Prover。
- Prover和Verifier:都计算 P ′ = P + [ v ] U P'=P+[v]U P′=P+[v]U。
- Prover:转为证明Prover知道 a ⃗ ∈ F p d , r , v ′ ∈ F p \vec{a}\in\mathbb{F}_p^d,r,v'\in\mathbb{F}_p a∈Fpd,r,v′∈Fp,使得 P ′ = < a ⃗ , G ⃗ > + [ r ] H + [ v ′ ] U P'=<\vec{a},\vec{G}>+[r]H+[v']U P′=<a,G>+[r]H+[v′]U成立,其中 v ′ = < a ⃗ , ( 1 , x , x 2 , ⋯ , x d − 1 ) > v'=<\vec{a},(1,x,x^2,\cdots,x^{d-1})> v′=<a,(1,x,x2,⋯,xd−1)>。若Prover无法提前知道 U U U,则 v = v ′ v=v' v=v′成立。【注意,本文的“U”由Verifier在收到commitment P P P之后才提供,Bulletproofs中的也类似,而Hyrax中的dot-product proof protocol中没有做相应约定,存在prover在 P P P中包含 U U U信息,进而伪造证明的情况——a prover with malicious control of P P P would then be able to interfere with the argument by including terms involving U U U in P P P。】(参见博客 Hyrax: Doubly-efficient zkSNARKs without trusted setup学习笔记 第4.2节“dot-product proof with Bulletproofs”)
Bulletproofs中实现的基本信息为:(此处的 U U U由Verifier先知道 P = < a ⃗ , G ⃗ > + < b ⃗ , H ⃗ > P=<\vec{a},\vec{G}>+<\vec{b},\vec{H}> P=<a,G>+<b,H>后,发送challenge x ∈ F x\in\mathbb{F} x∈F,然后Prover和Verifier重新计算的 U = x U ∈ G U=xU\in\mathbb{G} U=xU∈G。)【非zero-knowledge的inner product argument】
- public info:commitment P ′ P' P′,generators G ⃗ , H ⃗ ∈ G d , U ∈ G \vec{G},\vec{H}\in\mathbb{G}^d,U\in\mathbb{G} G,H∈Gd,U∈G。
- private info: a ⃗ , b ⃗ ∈ F d \vec{a},\vec{b}\in\mathbb{F}^d a,b∈Fd。
- relation: P ′ = < a ⃗ , G ⃗ > + < b ⃗ , H ⃗ > + [ < a ⃗ , b ⃗ > ] U P'=<\vec{a},\vec{G}>+<\vec{b},\vec{H}>+[<\vec{a},\vec{b}>]U P′=<a,G>+<b,H>+[<a,b>]U
本文针对的情况是,其中 b ⃗ = ( 1 , x , x 2 , ⋯ , x n − 1 ) \vec{b}=(1,x,x^2,\cdots,x^{n-1}) b=(1,x,x2,⋯,xn−1) 为public info,对Prover和Verifier均已知,所以,此时不再需要 H ⃗ ∈ G d \vec{H}\in\mathbb{G}^d H∈Gd。根据需要,可额外再引入generator H ∈ G H\in\mathbb{G} H∈G来实现blinding both prover messages and the commitment P ′ P' P′。最终基本信息为:
- public info:commitment P ′ P' P′,generators G ⃗ ∈ G d , H , U ∈ G \vec{G}\in\mathbb{G}^d, H, U\in\mathbb{G} G∈Gd,H,U∈G 和 b ⃗ ∈ F d \vec{b}\in\mathbb{F}^d b∈Fd。
- private info: a ⃗ ∈ F d \vec{a}\in\mathbb{F}^d a∈Fd和blinding r ∈ F r\in\mathbb{F} r∈F。
- relation: P ′ = < a ⃗ , G ⃗ > + r H + [ < a ⃗ , b ⃗ > ] U P'=<\vec{a},\vec{G}>+rH+[<\vec{a},\vec{b}>]U P′=<a,G>+rH+[<a,b>]U。
假设 d = 2 k , k > 0 d=2^k,k>0 d=2k,k>0,Prover初始化 G ⃗ ′ = G ⃗ , a ⃗ ′ = a ⃗ , b ⃗ ′ = b ⃗ , P = P ′ \vec{G}'=\vec{G},\vec{a}'=\vec{a},\vec{b}'=\vec{b},P=P' G′=G,a′=a,b′=b,P=P′,然后进行 k k k轮交互,其中 in the j j jth round (starting with j = k j=k j=k and finishing with j = 1 j=1 j=1):
1)若 d = 1 d=1 d=1,则:【目前有2种实现思路。】
1.1)Hyrax中的思路为:【此时有 P = a ′ G ′ + r H + a ′ b ′ U P=a'G'+rH+a'b'U P=a′G′+rH+a′b′U,其中 a ′ , r ∈ F a',r\in\mathbb{F} a′,r∈F为private info, b ′ ∈ F , G ′ , H , U , P ∈ G b'\in\mathbb{F}, G',H,U,P\in\mathbb{G} b′∈F,G′,H,U,P∈G均为public info。】
- Prover:引入Prover私有blinding随机数 d , r δ , r β ← F d,r_{\delta},r_{\beta}\leftarrow\mathbb{F} d,rδ,rβ←F,计算 δ = d G ′ + r δ H , β = d U + r δ H \delta=dG'+r_{\delta}H, \beta=dU+r_{\delta}H δ=dG′+rδH,β=dU+rδH,将 δ , β ∈ G \delta,\beta\in\mathbb{G} δ,β∈G发送给Verifier。
- Verifier:发送challenge c ← F c\leftarrow \mathbb{F} c←F 给Prover。
- Prover:计算 z 1 = d + c ⋅ a ′ b ′ , z 2 = b ′ ( c ⋅ r + r β ) + r δ z_1=d+c\cdot a'b', z_2=b'(c\cdot r+r_{\beta})+r_{\delta} z1=d+c⋅a′b′,z2=b′(c⋅r+rβ)+rδ,将 z 1 , z 2 ∈ F z_1,z_2\in\mathbb{F} z1,z2∈F发送给Verifier。
- Verifier:验证 b ′ ( c P + β ) + δ = z 1 ( G ′ + b ′ U ) + z 2 H b'(cP+\beta)+\delta=z_1(G'+b'U)+z_2H b′(cP+β)+δ=z1(G′+b′U)+z2H是否成立即可。
1.2)本文的思路为(相比于Hyrax方案,proof size少了一个group element G \mathbb{G} G):【此时有 P = [ a ′ ] G ′ + [ r ] H + [ a ′ b ′ ] U = [ a ′ ] ( G + [ b ′ ] U ) + [ r ] H P=[a']G'+[r]H+[a'b']U=[a'](G+[b']U)+[r]H P=[a′]G′+[r]H+[a′b′]U=[a′](G+[b′]U)+[r]H,其中 a ′ , r ∈ F a',r\in\mathbb{F} a′,r∈F为private info, b ′ ∈ F , G ′ , H , U , P ∈ G b'\in\mathbb{F}, G',H,U,P\in\mathbb{G} b′∈F,G′,H,U,P∈G均为public info。】(其中 ( G + [ b ′ ] U ) (G+[b']U) (G+[b′]U)为public info,可直接用 博客 基于Sigma protocol实现的零知识证明protocol集锦 第2.4节 “2.4 Protocol 4. Knowledge of the opening of Pedersen commitment”来计算。)
- Prover:引入Prover私有blinding随机数 d , r δ ← F d,r_{\delta}\leftarrow\mathbb{F} d,rδ←F,计算 δ = d ( G ′ + b ′ U ) + r δ H \delta=d(G'+b'U)+r_{\delta}H δ=d(G′+b′U)+rδH,将 δ ∈ G \delta \in\mathbb{G} δ∈G发送给Verifier。
- Verifier:发送challenge c ← F c\leftarrow \mathbb{F} c←F 给Prover。
- Prover:计算 z 1 = d + a ′ c , z 2 = r δ + r c z_1=d+a'c, z_2=r_{\delta}+rc z1=d+a′c,z2=rδ+rc,将 z 1 , z 2 ∈ F z_1,z_2\in\mathbb{F} z1,z2∈F发送给Verifier。
- Verifier:验证 c P + δ = z 1 ( G ′ + b ′ U ) + z 2 H cP+\delta=z_1(G'+b'U)+z_2H cP+δ=z1(G′+b′U)+z2H是否成立即可。
2)若 d > 1 d>1 d>1,则 j = log 2 d , d ′ = d 2 j=\log_2{d}, d'=\frac{d}{2} j=log2d,d′=2d,有:
Prover:计算:
d ′ = d / 2 d'=d/2 d′=d/2。
引入Prover私有blinding随机数 l j , r j ← F l_j,r_j\leftarrow\mathbb{F} lj,rj←F,计算 L j = < a ⃗ l o ′ , G ⃗ h i ′ > + [ l j ] H + [ < a ⃗ l o ′ , b ⃗ h i ′ > ] U L_j=<\vec{a}'_{lo},\vec{G}'_{hi}>+[l_j]H+[<\vec{a}'_{lo},\vec{b}'_{hi}>]U Lj=<alo′,Ghi′>+[lj]H+[<alo′,bhi′>]U, R j = < a ⃗ h i ′ , G ⃗ l o ′ > + [ r j ] H + [ < a ⃗ h i ′ , b ⃗ l o ′ > ] U R_j=<\vec{a}'_{hi},\vec{G}'_{lo}>+[r_j]H+[<\vec{a}'_{hi},\vec{b}'_{lo}>]U Rj=<ahi′,Glo′>+[rj]H+[<ahi′,blo′>]U。
将 L j , R j ∈ G L_j,R_j\in\mathbb{G} Lj,Rj∈G发送给Verifier。Verifier:发送random challenge u j ∈ F u_j\in\mathbb{F} uj∈F 给Prover。
Prover:计算:
a ⃗ ′ = a ⃗ h i ′ ⋅ u j − 1 + a ⃗ l o ′ ⋅ u j \vec{a}'=\vec{a}'_{hi}\cdot u_j^{-1}+\vec{a}'_{lo}\cdot u_j a′=ahi′⋅uj−1+alo′⋅uj
r ′ = l j u j 2 + r + r j u j − 2 r'=l_ju_j^2+r+r_ju_j^{-2} r′=ljuj2+r+rjuj−2Prover和Verifier:计算:
b ⃗ ′ = b ⃗ l o ′ ⋅ u j − 1 + b ⃗ h i ′ ⋅ u j \vec{b}'=\vec{b}'_{lo}\cdot u_j^{-1}+\vec{b}'_{hi}\cdot u_j b′=blo′⋅uj−1+bhi′⋅uj
G ⃗ ′ = G ⃗ l o ′ ⋅ u j − 1 + G ⃗ h i ′ ⋅ u j \vec{G}'=\vec{G}'_{lo}\cdot u_j^{-1}+\vec{G}'_{hi}\cdot u_j G′=Glo′⋅uj−1+Ghi′⋅uj
P ′ = [ u j 2 ] L j + P + [ u j − 2 ] R j P'= [u_j^2]L_j+P+ [u_j^{-2}]R_j P′=[uj2]Lj+P+[uj−2]Rj设置 d = d ′ , P = P ′ , r = r ′ d=d',P=P',r=r' d=d′,P=P′,r=r′,继续从步骤1)开始执行。
在以上证明过程中,关注Prover在每轮递归调用时计算的内容:
a ⃗ ′ = a ⃗ h i ′ ⋅ u j − 1 + a ⃗ l o ′ ⋅ u j \vec{a}'=\vec{a}'_{hi}\cdot u_j^{-1}+\vec{a}'_{lo}\cdot u_j a′=ahi′⋅uj−1+alo′⋅uj
b ⃗ ′ = b ⃗ l o ′ ⋅ u j − 1 + b ⃗ h i ′ ⋅ u j \vec{b}'=\vec{b}'_{lo}\cdot u_j^{-1}+\vec{b}'_{hi}\cdot u_j b′=blo′⋅uj−1+bhi′⋅uj
G ⃗ ′ = G ⃗ l o ′ ⋅ u j − 1 + G ⃗ h i ′ ⋅ u j \vec{G}'=\vec{G}'_{lo}\cdot u_j^{-1}+\vec{G}'_{hi}\cdot u_j G′=Glo′⋅uj−1+Ghi′⋅uj
- 与最后一轮 d = 1 d=1 d=1时的 G ′ ∈ G , b ′ ∈ F G'\in\mathbb{G},b'\in\mathbb{F} G′∈G,b′∈F之间的关系为 G ′ = < s ⃗ , G ⃗ > , b ′ = < s ⃗ , b ⃗ > G'=<\vec{s},\vec{G}>,b'=<\vec{s},\vec{b}> G′=<s,G>,b′=<s,b>,其中 s ⃗ \vec{s} s为:
s ⃗ = ( u 1 − 1 u 2 − 1 ⋯ u k − 1 , u 1 u 2 − 1 ⋯ u k − 1 , u 1 − 1 u 2 ⋯ u k − 1 , u 1 u 2 ⋯ u k − 1 , ⋮ u 1 u 2 ⋯ u k ) \vec{s}=(u_1^{-1}u_2^{-1}\cdots u_k^{-1}, \\ u_1 u_2^{-1}\cdots u_k^{-1}, \\ u_1^{-1}u_2\cdots u_k^{-1},\\ u_1u_2\cdots u_k^{-1},\\ \vdots \\ u_1u_2\cdots u_k) s=(u1−1u2−1⋯uk−1,u1u2−1⋯uk−1,u1−1u2⋯uk−1,u1u2⋯uk−1,⋮u1u2⋯uk) - Verifier在最后一轮收到的commitment P ′ P' P′,满足以下公式:
P ′ = ∑ j = 1 k ( [ u j 2 ] L j ) + P + ∑ j = 1 k ( [ u j − 2 ] R j ) P'= \sum_{j=1}^{k}([u_j^2]L_j)+P+ \sum_{j=1}^{k}([u_j^{-2}]R_j) P′=∑j=1k([uj2]Lj)+P+∑j=1k([uj−2]Rj) - Prover在最后一轮的blinding值 r ′ r' r′满足如下公式:
r ′ = ∑ j = 1 k ( l j u j 2 ) + r + ∑ j = 1 k ( r j u j − 2 ) r'=\sum_{j=1}^{k}(l_ju_j^2)+r+\sum_{j=1}^{k}(r_ju_j^{-2}) r′=∑j=1k(ljuj2)+r+∑j=1k(rjuj−2)
3.1 Amortization Strategy摊销策略
以上polynomial commitment,尽管其communication complexity为 O ( log 2 ( d ) ) O(\log_2(d)) O(log2(d)),其中 d − 1 d-1 d−1为多项式的degree bound,但是Verifier必须在验证时计算 G ′ = < s ⃗ , G ⃗ > , b ′ = < s ⃗ , b ⃗ > G'=<\vec{s},\vec{G}>,b'=<\vec{s},\vec{b}> G′=<s,G>,b′=<s,b>,其中 s ⃗ = ( u 1 − 1 u 2 − 1 ⋯ u k − 1 , u 1 u 2 − 1 ⋯ u k − 1 , u 1 − 1 u 2 ⋯ u k − 1 , u 1 u 2 ⋯ u k − 1 , ⋮ u 1 u 2 ⋯ u k ) \vec{s}=(u_1^{-1}u_2^{-1}\cdots u_k^{-1}, \\ u_1 u_2^{-1}\cdots u_k^{-1}, \\ u_1^{-1}u_2\cdots u_k^{-1},\\ u_1u_2\cdots u_k^{-1},\\ \vdots \\ u_1u_2\cdots u_k) s=(u1−1u2−1⋯uk−1,u1u2−1⋯uk−1,u1−1u2⋯uk−1,u1u2⋯uk−1,⋮u1u2⋯uk)。
注意,本文针对的情况是 b ⃗ = ( 1 , x , x 2 , ⋯ , x n − 1 ) \vec{b}=(1,x,x^2,\cdots,x^{n-1}) b=(1,x,x2,⋯,xn−1)为public info的情况,其中的 < s ⃗ , b ⃗ > <\vec{s},\vec{b}> <s,b>可看成对多项式:【注意,感觉论文的 g ( X , u 1 , u 2 , ⋯ , u k ) g(X,u_1,u_2,\cdots,u_k) g(X,u1,u2,⋯,uk)公式有点问题,但是作者说木问题。。。】
g ( X , u 1 , u 2 , ⋯ , u k ) = ∏ i = 1 k ( u i − 1 + u i X 2 i − 1 ) g(X,u_1,u_2,\cdots,u_k)=\prod_{i=1}^{k}(u_i^{-1}+u_iX^{2^{i-1}}) g(X,u1,u2,⋯,uk)=∏i=1k(ui−1+uiX2i−1)
在point x x x的evaluation值,即 b ′ = < s ⃗ , b ⃗ > = g ( x , u 1 , u 2 , ⋯ , u k ) b'=<\vec{s},\vec{b}>=g(x,u_1,u_2,\cdots,u_k) b′=<s,b>=g(x,u1,u2,⋯,uk)。Verifier可计算该evaluation值in logarithmic time。
但是,对于 G ′ = < s ⃗ , G ⃗ > G'=<\vec{s},\vec{G}> G′=<s,G>计算,仍然需要a linear-time multiscalar multiplication。但是仔细观察,可将 G ′ G' G′看成是对多项式 g ( X , u 1 , u 2 , ⋯ , u k ) g(X,u_1,u_2,\cdots,u_k) g(X,u1,u2,⋯,uk)系数的commitment值:
G ′ = C o m m i t ( σ , g ( X , u 1 , u 2 , ⋯ , u k ) ) G'=Commit(\sigma, g(X,u_1,u_2,\cdots,u_k)) G′=Commit(σ,g(X,u1,u2,⋯,uk))
所以 与其让Verifier为 m m m个(independent)arguments 自己计算 G i ′ G'_i Gi′,不如将该计算外包给不可信的第三方“helper“ ,”helper”在提供 G 1 ′ , G 2 ′ , ⋯ , G m ′ G_1',G_2',\cdots,G_m' G1′,G2′,⋯,Gm′ (for m m m separate arguments) 计算结果的同时提供相应的argument that each are correct by demonstrating that a random linear combination of the commitments opens at a random point to a value the verifier can compute in time O ( m log ( d ) ) O(m\log(d)) O(mlog(d))。基于Schwartz-Zippel Lemma,”helper“可让Verifier信服其结果是正确计算的(其伪造成功的概率不高于 d − 1 p − 1 \frac{d-1}{p-1} p−1d−1)。
也就是说,此时,Verifier需调用“helper“运行对 g ( X , u 1 , u 2 , ⋯ , u k ) g(X,u_1,u_2,\cdots,u_k) g(X,u1,u2,⋯,uk)的polynomial commitment opening protocol,最终Verifier仍需要进行一次linear-time operation,但是通过此操作,the verifier has traded m m m linear-time operations for one, with a marginal cost that is logarithmic in the degree bound。
4. FRI多项式承诺
边栏推荐
- Linux scheduled database backup script
- Common SQL of Oracle Report
- C language introduction practice (11): enter a group of positive integers and sum the numbers in reverse order
- Head pose estimation principle and visualization_ Loveliuzz's blog - Programmer's Homestead_ Head posture estimation
- MySQL的大心脏 — 索引
- 基于nextcloud构建个人网盘
- [test platform development] 21. complete sending interface request and display response header information
- 精品国创《少年歌行》数字藏品开售,邀你共铸少年武侠江湖梦
- What methods are called behind the use of objects
- [software testing] how to sort out your testing business
猜你喜欢

C thread lock and single multithreading are simple to use

leetcode: 17. 电话号码的字母组合

利用shell脚本实现封禁扫描频率过高的ip

Towhee 每周模型

Deep learning single image 3D face reconstruction

Kettle实现共享数据库连接及插入更新组件实例
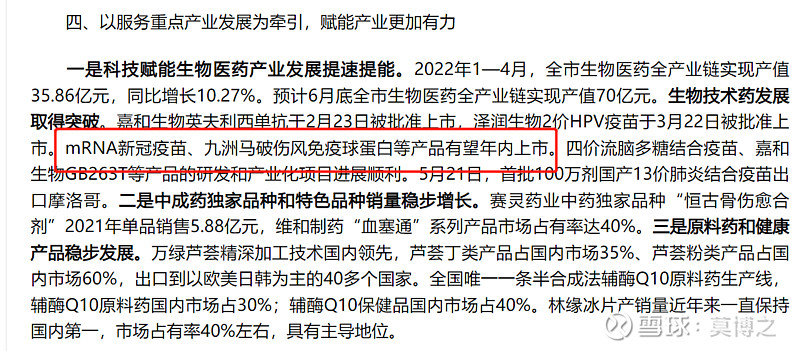
Transferred from Yuxi information disclosure: products such as mRNA covid-19 vaccine and Jiuzhou horse tetanus immunoglobulin are expected to be on the market within this year.

基于matlab的BOC调制解调的同步性能仿真,输出跟踪曲线以及不同超前滞后码距下的鉴别曲线

OpenCV计算外包矩形

raid homes and plunder houses!
随机推荐
【软件测试】盘一盘工作中遇到的 Redis 异常测试
基于matlab的BOC调制解调的同步性能仿真,输出跟踪曲线以及不同超前滞后码距下的鉴别曲线
The accuracy of digital addition
爬虫中selenium实现自动给csdn博主文章点收藏
Towhee 每周模型
深度学习单图三维人脸重建
基于双目相机拍摄图像的深度信息提取和目标测距matlab仿真
基于PSO优化的多目标最优值求解matlab仿真
【无标题】
【软件测试】盘一盘工作中遇到的 MQ 异常测试
用FFT加速特殊矩阵的矩阵向量乘运算
C language introduction practice (11): enter a group of positive integers and sum the numbers in reverse order
Mathematical function of MySQL function summary
【测试平台开发】21. 完成发送接口请求显示响应头信息
Zhongwang CAD professional 2022 software installation package download and installation tutorial
运维高级作业02
【软件测试】如何梳理你测试的业务
leetcode: 17. 电话号码的字母组合
Official wechat product! Applet automation framework minium sharing Preview
CSDN writing method (II)