当前位置:网站首页>How to protect e-commerce websites from network attacks?
How to protect e-commerce websites from network attacks?
2022-07-26 19:25:00 【HENGCHUANG technology HK】
E-commerce is an important source of income for many enterprises . At present , Groups of customers prefer to use computers or tablets to complete shopping in a comfortable home , Therefore, security has naturally become a concern of online shopping customers . To avoid damaging your e-commerce transactions and customer churn , Learn more about the most common security risks , Including injection 、 Authentication 、 Cross-site scripting 、 Denial of service and security configuration errors , It is conducive to taking targeted measures to protect e-commerce websites from network attacks .

Network attack #1 – Inject
What's the danger ?
Injection attacks may result in data loss 、 Data corruption 、 Access denied , It may even cause the host that has a negative impact on your corporate reputation to take over completely .
How it works ?
Untrusted data is injected Web Applications , And induce the application to execute commands and access data . Common in SQL、LDAP、Xpath、NoSQL Inquire about 、 Operating system commands 、XML Parser 、SMTP Headers, etc .
How to prevent ?
Use safe API Can prevent injection attacks , in addition , Keep your Web Application updates are also very important , After all, outdated applications are particularly vulnerable to injection attacks .
Network attack #2 – Authentication
What's the danger ?
Authentication vulnerabilities are common , It can provide attackers with authorized users who can attack . Stolen session ID It can be used repeatedly to impersonate users on the website .
How it works ?
The attacker used the exposed account 、 Weak passwords or other flaws in authentication or session management functions to impersonate users .
How to prevent ?
Protect your application from sessions ID Attacks require a strong set of authentication and session management controls 、 Secure communication and credential storage .
Network attack #3 – Cross site scripts (XSS)
What's the danger ?
XSS Is one of the most common security risks . Attackers hijack user sessions to change websites 、 Insert bad content 、 Conduct phishing and malware attacks —— All of these will have a negative impact on the reputation of your website .
How it works ?
This attack exploits browser user trust . An attacker can send a text-based attack script executed in the victim's browser , Thus hijacking user sessions .
How to prevent ?
Correctly escape all untrusted data and include white list input verification , Maintenance update Web Applications .
Network attack #4 – Denial of service (DDoS)
What's the danger ?
Distributed denial of service (DDoS), This type of attack is particularly worrying . Because after being attacked , Slow or even inaccessible websites will seriously reduce the conversion rate .
How it works ?
stay DDoS During the attack , The attacker flooded the access router with false traffic , Until the system overloads and fails .DDoS Attacks involve coordinated attacks from many different sources .
How to prevent ?
relieve DDoS The direct method of attack is to monitor incoming traffic . such as , You can use advanced anti DDoS server defense , It can distinguish between legitimate traffic and malicious traffic , Only legal traffic is allowed . Or access advanced anti DDoS IP, Divert attack traffic to advanced defense IP, It can block attack traffic and occupy server resources , It can also protect the user origin .
Network attack #5 – Security configuration error
What's the danger ?
The misconfigured security settings are implemented Web Server and application are often neglected . Attackers are easy to exploit , Unauthorized access to system data or server functions , Steal or modify your data .
How it works ?
Attackers can take advantage of misconfigured settings in many ways , Included in Web The server 、 Application server 、 database 、 Application framework and custom code . They can use the default account 、 Unpaved vulnerabilities 、 Unprotected files 、 Directory etc. .
How to prevent ?
Ensure that secure environments are deployed quickly and easily 、 Maintain updated software 、 Safely separating components and regularly auditing your security can help avoid security threats .
边栏推荐
- Simulated 100 questions and simulated examination of refrigeration and air conditioning equipment operation examination in 2022
- torch. Usage and comparison of unsqueeze() squeeze() expand() repeat()
- C#创建及读取DAT文件案例
- conda+pytorch环境教程
- [刷题] 二分答案求解
- C language - Introduction - syntax - string (11)
- ReentrantLock学习之公平锁过程
- The difference between advanced anti DDoS server and advanced anti DDoS IP
- Here comes the most complete introduction to MES system
- Wechat applet plug-in -- wxml to canvas (generate pictures)
猜你喜欢

C语言-入门-语法-字符串(十一)

ReentrantLock学习之公平锁过程

用低代码搭建千人食品制造企业高效管理系统案例分析

篇7:exited on DESKTOP-DFF5KIK with error code -1073741511.

How many pairs can an array of leetcode simple questions form
2022g1 industrial boiler stoker certificate question bank and simulation examination

分布式事务-seata

MySQL - function and constraint commands

Description of MDM separation of powers and classification and grading authority
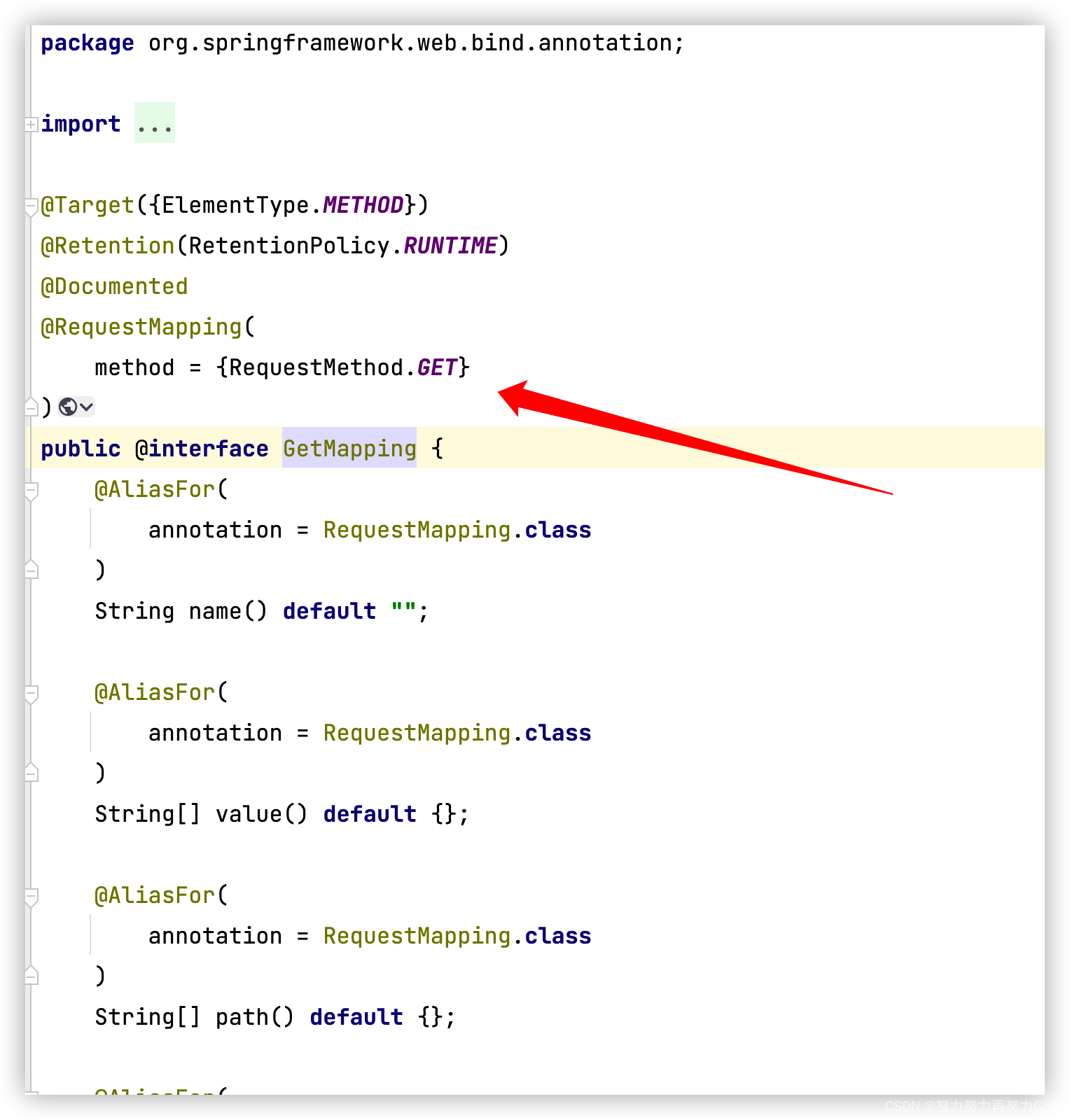
Introduce the difference between @getmapping and @postmapping in detail
随机推荐
[刷题] 二分答案求解
C # get local time / system time
MySQL log introduction
深度学习的数学基础
Cannot find current proxy: Set ‘exposeProxy‘ property on Advised to ‘true‘ to make it available
What aspects should be considered in the selection of MES system?
After the exam on June 25, see how the new exam outline reviews PMP
Is it safe for CSC qiniu members to open preferential accounts? I don't know if it's the lowest Commission
The first letter of leetcode simple question appears twice
NLP 学习之路
MySQL教程:MySQL数据库学习宝典(从入门到精通)
Simulated 100 questions and simulated examination of refrigeration and air conditioning equipment operation examination in 2022
Don't casually pass the request to the asynchronous thread. You can't handle it. You have to use the startasync method
Data Lake -- concept, characteristics, architecture and case overview
从6月25日考试之后,看新考纲如何复习PMP
PMP每日一练 | 考试不迷路-7.26(包含敏捷+多选)
节约gas-ChiToken的用法
Sentinel isolation and degradation
Unity farm 2 - planting system
节省50%成本 京东云发布新一代混合CDN产品