当前位置:网站首页>According to the atlas of data security products and services issued by the China Academy of information technology, meichuang technology has achieved full coverage of four major sectors
According to the atlas of data security products and services issued by the China Academy of information technology, meichuang technology has achieved full coverage of four major sectors
2022-07-02 19:10:00 【database security】
In recent days, , By China Academy of information and communication 、 China Communications Standardization Association , The big data industry summit hosted by the big data technology standards Promotion Committee of China Communications Standardization Association was held . At the meeting , China information and Communication Research Institute officially released 《 Database Development Research Report (2022)》 and 《 Global database industry map 》、《 Map of data security products and services 1.0》.
Meichuang technology was selected 《 Global database industry map 》 The database security camp represents enterprises , Products and services are fully covered 《 Map of data security products and services 》 Data security protection detection 、 Data security operation and maintenance 、 Data security sharing and circulation 、 Data security services 4 Large plate , shortlisted 12 Item segmentation .
《 Global database industry map 》
The database security camp represents enterprises

Involving data ( library ) More than ten years in the field of safety , Meichuang technology is based on the in-depth study of database kernel technology , A leading data security product service matrix has been formed , Participate in data desensitization 、( database ) A firewall 、 Data backup and recovery, etc 10 More than national standards are formulated ,5 Department of database technology and data security research works , It is the technical support unit of the national network and information security information notification mechanism 、CNCERT Provincial support unit for network security emergency service 、 Zhejiang meichuang Sensitive Information Security Research Institute .
The development of digitalization puts forward new requirements for data security , Based on the new generation of zero trust data security architecture 、 Intrusion lifecycle 、 Risk management , Meichuang Technology From data security governance consulting 、 Product capability configuration in the whole life cycle of data 、 Data security operation platform based on comprehensive data security capability , Build overlay data access security for users 、 Data flow security 、 External intrusion security 、 A new generation of active data security protection system under the scenes of blackmail virus protection .
1 Consulting planning based on data security governance : Take data security governance as the starting point , Help users build more comprehensive 、 More targeted data security planning and compliance construction .
2 Product system based on the whole life cycle of data : With database security 、 Audit cloud management 、 Terminal security 、 Disaster recovery replication 、 Flow control and other complete product lines , Security protection covering the whole life cycle of data .
3 Data security operation platform based on comprehensive data security capability : Standardize management with assets 、 Secure multi terminal linkage 、 High efficiency intelligent management ability of operational value-added , Fully activate the data security protection scenario , Improve the overall operation level of data security .
《 Map of data security products and services 》
Four plates 12 Item segmentation

《 Map of data security products and services 1.0》 Including data security protection detection 、 Data security operation and maintenance 、 Data security sharing and circulation 、 There are four parts of data security services . Meichuang covers all , Involving terminal safety protection ( Anti blackmail )、 Database firewall 、 Data desensitization 、 Data watermark traceability 、 Database audit, etc 12 Item segmentation , With first-class product technology ability and continuous innovation accumulation , Widely in the government 、 Finance 、 Medical care 、 Logistics, transportation and other industries , Fully recognized by the market .
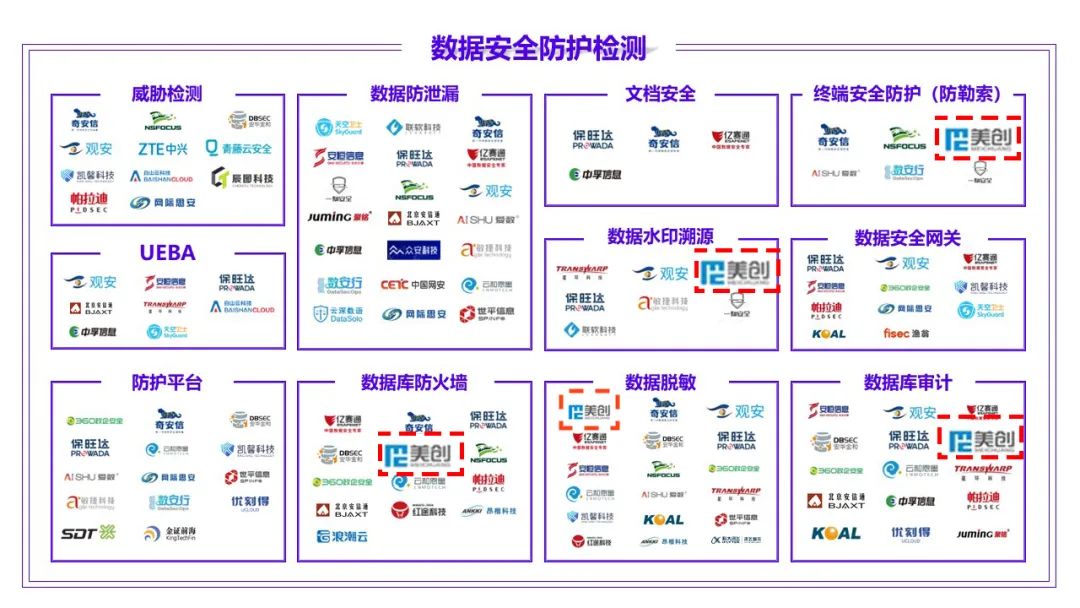
Data desensitization :1 National standards 、5 Participate in the formulation of local industry standards , Two years in a row CCIA Network security innovation product excellence award .
Database firewall : Firewall national standard - The core drafting unit of database firewall
Noah anti blackmail : Zero trust blackmail software protection represents manufacturers , a 2020 CCIA Network security innovation product excellent and most investment value award double award recognition
Data watermark traceability : It was selected into the first edition of software application and promotion guidance directory in Zhejiang Province
Database security audit : The first batch passed the functional evaluation of data security products of China Academy of communications 、 Golden wisdom award annual excellent product award

Data security management platform :2022 Leading scientific and technological achievement award of data blog , The unique multi tenant function has been successfully implemented in the big data Bureau
Dark data discovery and classification : The first batch passed the authoritative evaluation of China Academy of communications ( The first four companies ), government affairs 、 Finance 、 Take the lead in manufacturing .
Data security operation platform : Innovative combination CARTA Model , The whole scene 、 Closed loop data security operation

Data flow control platform :API Level data flow control 、 Data protection and value mining , Master the data flow situation of the whole link

Data security governance consulting : Finance 、 The government 、 Energy enterprises took the lead in landing , Help users acquire the data security governance capability of China Academy of communications (DSG) Evaluate excellent grade
Data security risk assessment : Improve the data security risk assessment system and professional consulting team ,500 Strong enterprise 、 Large energy groups have successful cases
Blackmail virus defense Insurance : The first blackmail Protection Insurance , Realize the whole process risk prevention and control of extortion defense
Besides , In the field of data security training , Ad hoc art and entrepreneurship College , It is the national plan for improving the ability of electronic information talents - Training base , Have a perfect curriculum system and lecturer team ; Emergency response and drill , It is the technical support unit of the national network and information security information notification mechanism 、CNCERT Provincial support unit for network security emergency service 、 Network security technical support unit of Network Information Office of Zhejiang provincial Party committee ; Data classification , With a perfect landing methodology 、 The consulting team and product solutions are practiced in various industries .
At this conference , Hebaohong, director of the Institute of cloud computing and big data, China Academy of communications and communications, released “2022 Ten key words of big data ”. He Baohong pointed out that , With data officially becoming a factor of production ,2022 year , Policies in the field 、 idea 、 technology 、 Security and other aspects are booming around this main line .
policy :“ Data elements unify the big market 、 Data management capability maturity ” Further improve the top-level design ;
In terms of concept :“ Data center 、 Data valuation 、DataOps” Continue to consolidate the theoretical foundation of enterprise digital intelligence transformation ;
Technical aspects ,“ Innovative database 、 Privacy computing all-in-one machine 、 Figure calculation ” Strongly support the value mining and efficient circulation of data elements ;
security ,“ Data security compliance 、 Data classification ” Promote further clarity of the red line of the data industry .
As a family, it is rooted in “ data ”, With “ Focus on data security , Unleash the value of data “ Enterprises with strategic positioning , Meichuang technology is based on the digital development needs of the industry , Also accelerating the new concept of products 、 Innovation and application of new technology , Actively seek and build more professional 、 Solutions that better fit the business attributes of the industry , Help the free flow of data elements 、 Efficient management and safe use .

边栏推荐
- How to clean up discarded PVs and their corresponding folders
- ORA-01455: converting column overflows integer datatype
- Industrial software lecture - core technology analysis of 3D CAD design software - the second lecture of the Forum
- 使用 Cheat Engine 修改 Kingdom Rush 中的金钱、生命、星
- How to enable the run dashboard function of idea
- Progress progress bar
- The student Tiktok publicized that his alma mater was roast about "reducing the seal of enrollment". Netizen: hahahahahahahaha
- Deep learning mathematics foundation
- 页面标题组件
- R语言ggplot2可视化:可视化折线图、使用labs函数为折线图添加自定义的X轴标签信息
猜你喜欢

迷你高尔夫球场:伦敦休闲旅游好去处
深度学习数学基础
The difference between SLC, MLC, TLC and QLC NAND SSD: which is better?

Obligatoire pour les débutants, cliquez sur deux boutons pour passer à un contenu différent

Mysql高级篇学习总结7:Mysql数据结构-Hash索引、AVL树、B树、B+树的对比
PyTorch函数中的__call__和forward函数
![[论文阅读] CA-Net: Leveraging Contextual Features for Lung Cancer Prediction](/img/ef/bb48ee88d5dc6fe876a498ab53106e.png)
[论文阅读] CA-Net: Leveraging Contextual Features for Lung Cancer Prediction

开发固定资产管理系统,开发固定资产管理系统用什么语音

Thoroughly understand the point cloud processing tutorial based on open3d!

Talk about the design of red envelope activities in e-commerce system
随机推荐
[daily question] first day
C文件输入操作
Use cheat engine to modify money, life and stars in Kingdom rush
When converting from list to map, if a certain attribute may cause key duplication and exceptions, you can set the way to deal with this duplication
Learning summary of MySQL advanced 6: concept and understanding of index, detailed explanation of b+ tree generation process, comparison between MyISAM and InnoDB
Golang concurrent programming goroutine, channel, sync
Comprendre complètement le tutoriel de traitement de Point Cloud basé sur open3d!
Markdown基础语法
Looking for innocence in New York -- a beautiful day at the discovery center of Legoland, New Jersey
【JVM调优实战100例】03——JVM堆调优四例
[100 cases of JVM tuning practice] 01 - introduction of JVM and program counter
Hospital online inquiry source code hospital video inquiry source code hospital applet source code
9D电影是怎样的?(+维度空间常识)
R语言使用epiDisplay包的lrtest函数对多个glm模型(logisti回归)执行似然比检验(Likelihood ratio test)对比两个模型的性能是否有差异、广义线性模型的似然比检
新加坡暑假旅游攻略:一天玩转新加坡圣淘沙岛
Troubleshooting: kubectl reports an error validationerror: unknown field \u00a0
潇洒郎:彻底解决Markdown图片问题——无需上传图片——无需网络——转发给他人图片无缺失
LightGroupButton* sender = static_ cast<LightGroupButton*>(QObject::sender());
MySQL advanced learning summary 7: MySQL data structure - Comparison of hash index, AVL tree, B tree and b+ tree
UML 类图