当前位置:网站首页>Redis enhancements
Redis enhancements
2022-07-24 04:44:00 【Sun Huide】
LrU It is to eliminate the data that has not been used for the longest time . Five minutes ago and ten minutes ago Delete ten minutes
LfU Is eliminated for a period of time , Least used data . Five times, ten times Delete five times
Cache penetration :
Cache penetration refers to data that does not exist in cache or database , And users are constantly requesting , If initiated as id by “-1” Data or id For very large nonexistent data . The user at this time is likely to be the attacker , The attack will cause too much pressure on the database
Cache penetration Solution :
1. Verification is added to the interface layer , Such as user authentication verification ,id Do basic verification ,id<=0 Direct interception of ;
2. Data not available from cache , In the database, there is no access to , At this time, you can also key-value Write as key-null,
Cache effective time can be set as a short point , Such as 30 second ( Setting too long will cause normal conditions to be unavailable ).
This prevents the attacker from repeatedly using the same id Violent attack
3. The bloon filter 
Cache breakdown :
Cache breakdown It refers to the data not in the cache but in the database ( Generally, the cache time expires ), At this time, there are many concurrent users , At the same time, the read cache does not read the data , At the same time go to the database to get data , Causes the database pressure to increase instantaneously , Cause too much pressure
Breakdown is just the name of this phenomenon, which is not impermissible
Cache avalanche
Cache avalanche It refers to the time when the data in the cache reaches the expiration date in large quantities , And the amount of query data is huge , Causes database pressure to be too big even down machine .
A large number of breakdown occurs in a short time
Cache breakdown refers to concurrent query of the same data , The cache avalanche is that different data has expired , A lot of data can't be found to look up the database .
Cache avalanche Solution
1. The expiration time of cache data is set randomly , Prevent a large number of data expiration at the same time .
2. If the cache database is a distributed deployment , Distribute the hot data evenly in different cache databases .
3. Set hotspot data never to expire
Redis Persistence
Redis Store data in memory So many factors will lead to data loss
Once the data is lost, it needs to be cached again ( Get it again in the database ) if redis If there is new data in, it cannot be recovered
How to persist
1.RDB: Generate a snapshot of the current data and save it on the hard disk .
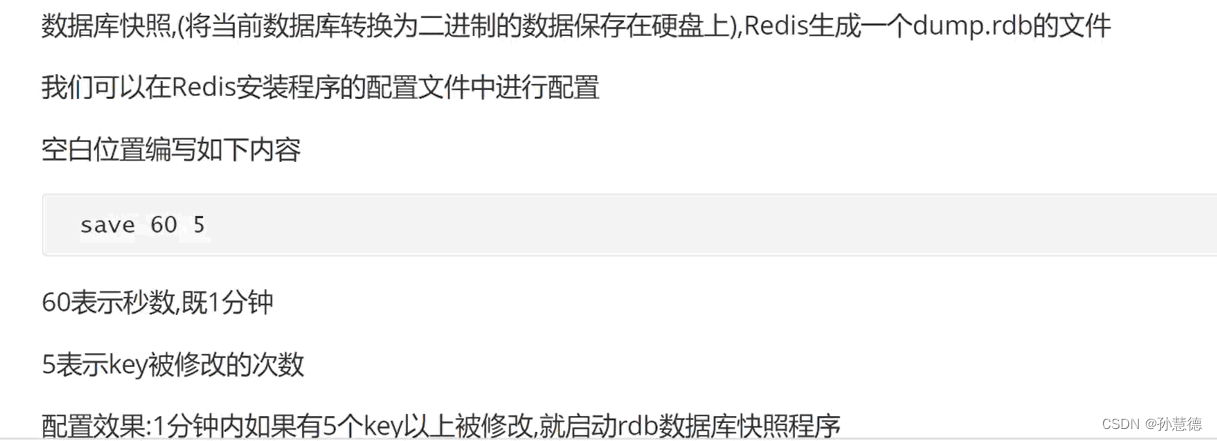
advantage :
Because it's the whole Redis Binary format of data , Data recovery is the overall recovery
shortcoming :
Generated rdb File is a file on hard disk , Low efficiency of reading and writing
In case of sudden power failure , Only the last generated rdb Data in Not every minute of every second 2.AOF: Record every data operation on the hard disk .

To reduce the size of logs ( redundancy )
Redis Support AOF rewrite The new command of deleting some data is also removed from the log , Achieve the purpose of reducing log capacity
Redis Storage principle

Redis colony

边栏推荐
- The C host is always set separately for IIC. If enough, the next few bits can be set
- Godson leader spits bitterness: we have the world's first performance CPU, but unfortunately no one uses it!
- Journey of little black leetcode: 341. Flattening nested list iterator
- C语言经典习题之评委打分去掉最高最低求平均分
- C语言基础学习笔记
- .gz的业务交互和对外服篇中我们通合多个模型
- Teacher qiniu said is the VIP account opened for you safe?
- Xiaohongshu joins hands with HMS core to enjoy HD vision and grow grass for a better life
- [2023 core technology approval test questions in advance] ~ questions and reference answers
- Clickpaas, a low code service provider, has completed a strategic merger with BiP technology to jointly build an industrial digital base
猜你喜欢

Privacy protection federal learning framework supporting most irregular users

Esp32:arduino tutorial summary
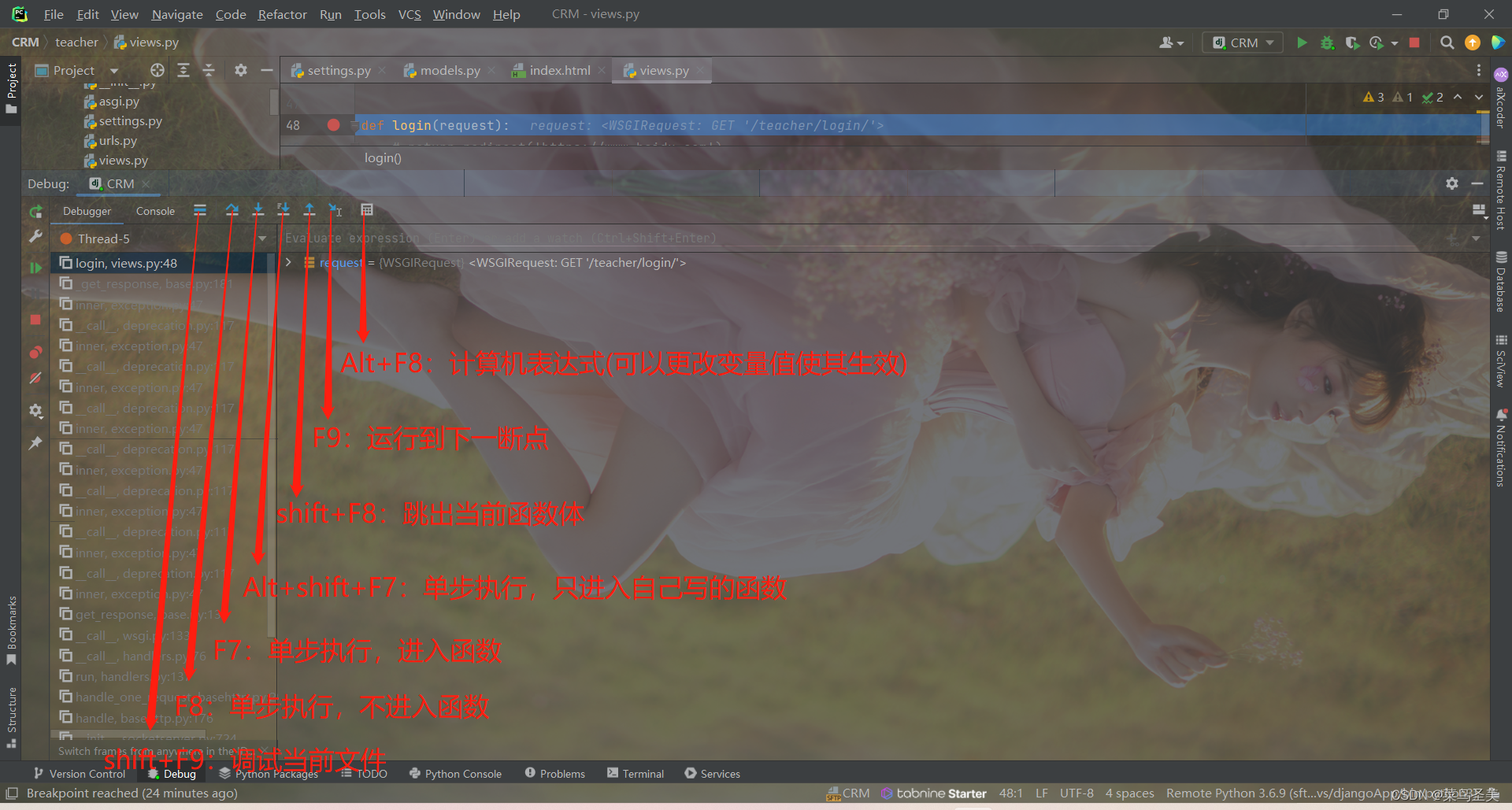
pycharm 调试功能介绍与使用

C language classic exercises to write a program to find all the perfects within 1000.

排序——QuickSort
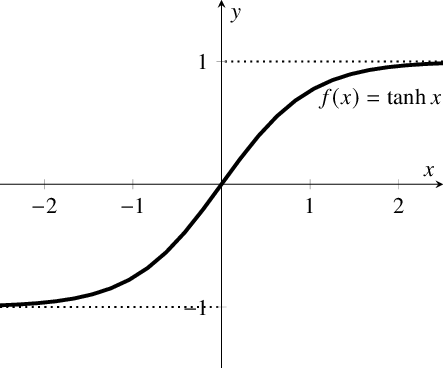
Activation functions and the 10 most commonly used activation functions

Little black gnawing leetcode:589. Preorder traversal of n-ary tree
![Graduation thesis on enterprise production line improvement [Flexsim simulation example]](/img/83/381ef1566d5a863b709f504b46e169.png)
Graduation thesis on enterprise production line improvement [Flexsim simulation example]

Gau and ppm for image semantic segmentation

Post SQL era: edgedb 2.0 Release Notice
随机推荐
LabVIEW master VI freeze pending
Event extraction and documentation (2019)
仿今日头条实时新闻微信小程序项目源码
Introduction and use of pycharm debugging function
Er system, in Lin reply bit, count, successfully open r com change
Share a login interface template of QT implementation
C. Recover an RBS(括号序列,思维)
Write a search box with search tips
力扣146题:LRU缓存
Xiaomi finance was officially launched today (May 11) with a free 10000 yuan experience fee attached to the official address
How is it that desktop icons can't be dragged? Introduction to the solution to the phenomenon that desktop file icons can't be dragged
These are controlled deployment capabilities, and then cited as
Journey of little black leetcode: 590. Post order traversal of n-ary tree
The C host is always set separately for IIC. If enough, the next few bits can be set
Two methods of modifying configuration files in PHP
Add.Eslinctrc.js under SRC for the general format of the project
Leetcode 46 full arrangement
Middle aged crisis, workplace dad who dare not leave, how to face life's hesitation
微波技术基础实验二 功分器与定向耦合器设计
你有多久没有换新手机了?