当前位置:网站首页>6-11 vulnerability exploitation - use the built environment to send emails
6-11 vulnerability exploitation - use the built environment to send emails
2022-07-25 01:45:00 【Mountain Rabbit 1】

We can have a look , What's under the email
ls
cd mail/
ls
cat Sent

This is the time , Will send the original email message
Before sending , We need to add corresponding users
sudo adduser test1
Y

This is the time , Our current computer has one test1 user , After we prepare the users , You can start sending and receiving mail
Send E-mail
utilize Linux Next thunderbird The software sends and receives emails
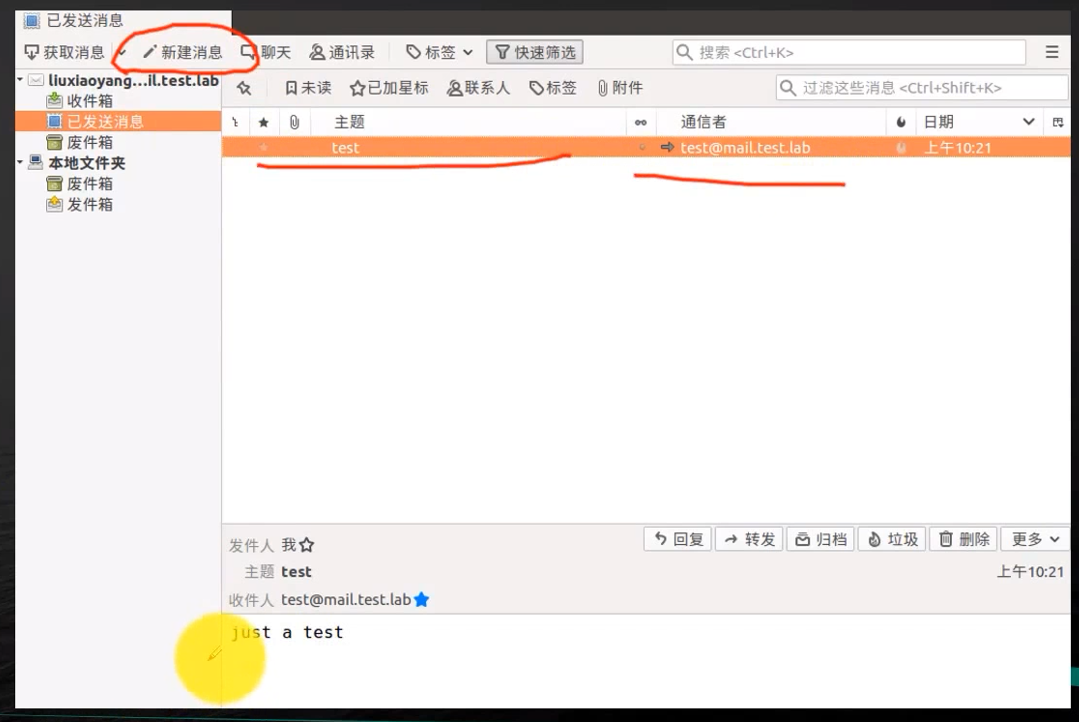
We need login users , Click new message , The writing of the topic and the communicator of the message 、 Sending of corresponding message
thunderbird
test1
[email protected]
192.168.42.137 143
192.168.42.137 25

Click I have learned about the relevant risks > complete
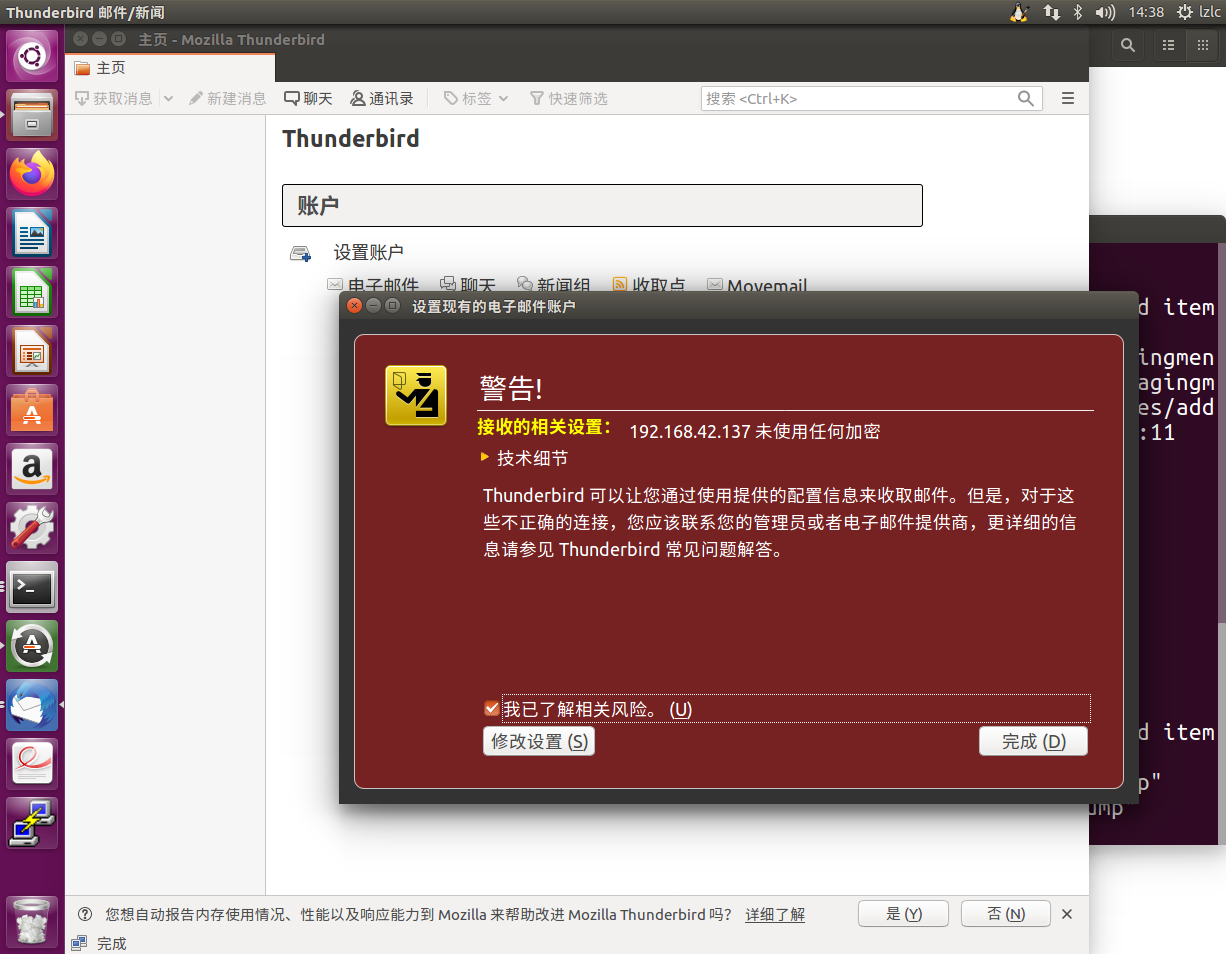
We have successfully added a new email account here
This is the time , We can also add a new one in another way test Account
Account settings > Account operation > Add account >

Because we didn't add test Account , So the server connection failure will be displayed here
Now let's use the previously logged in test The user to test1 Users send email
New message > [email protected] > just a test > now we test a smtp send email

We don't save , We received an email in our inbox
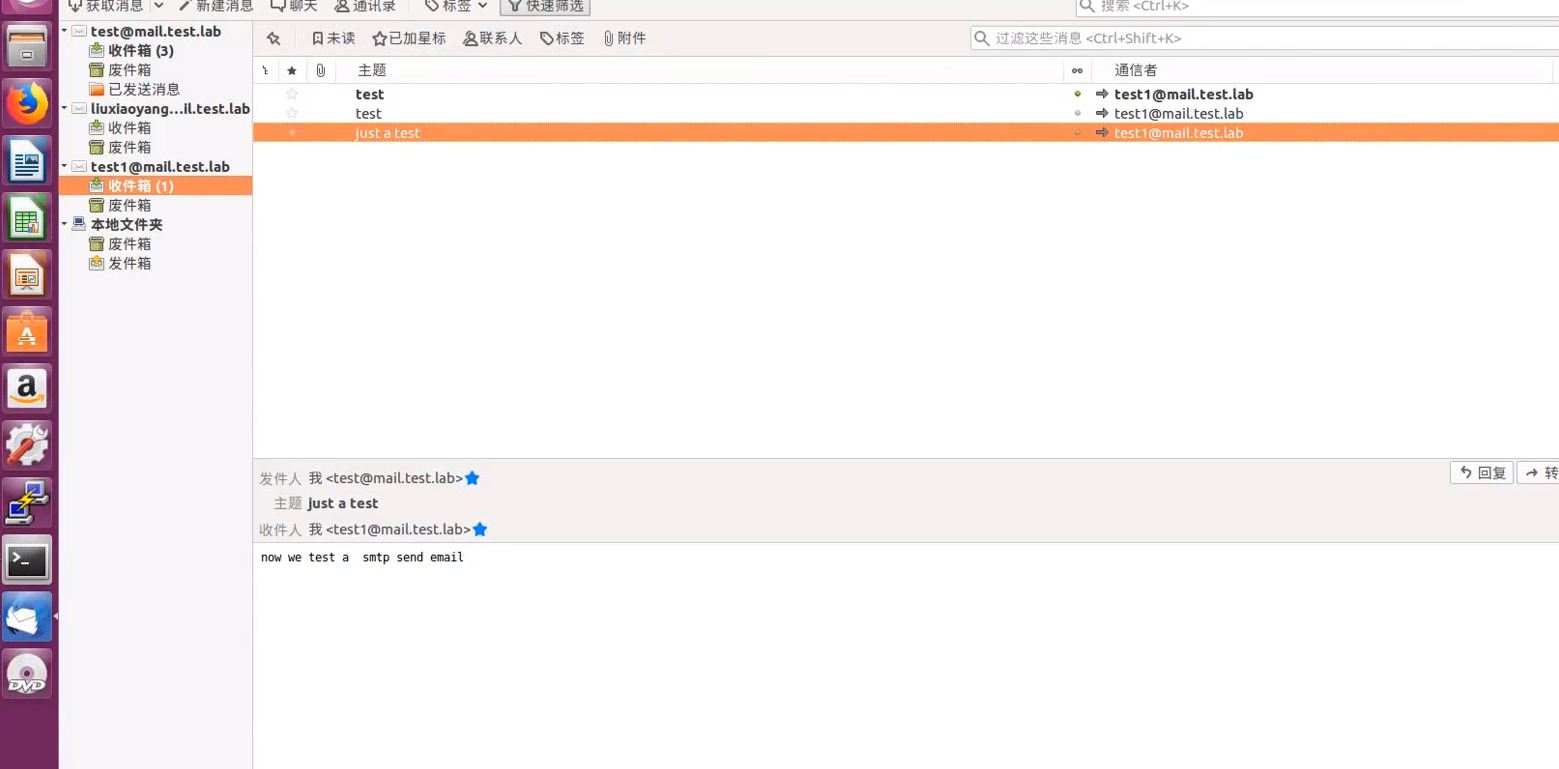
After sending , We just receive emails
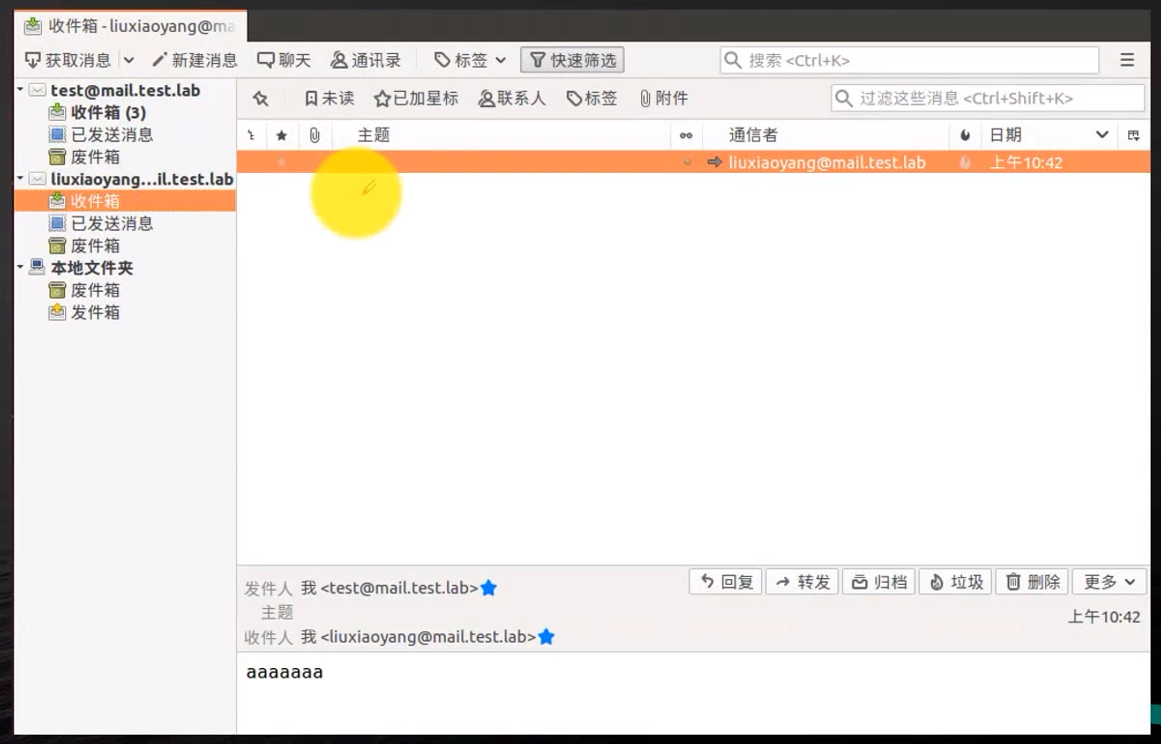
Receiving mail
Open the corresponding email directly , utilize thunderbird Receiving mail
边栏推荐
- Ecosystem long-term observation data product system
- Thinkphp5.0.24 deserialization chain analysis
- Redis learning notes (2) - power node of station B
- Visual studio code installation package download slow & Installation & environment configuration & new one-stop explanation
- Worthington carboxyl transfer carbonic anhydrase application and literature reference
- Start to build a three node Eureka cluster
- Fraud detection using CSP
- Target segmentation for 10000 frames of video, less than 1.4GB of video memory, open source code | ECCV 2022
- Open source demo | release of open source example of arcall applet
- Musk responded whether he would upload his brain to the cloud: already did it!
猜你喜欢

Opengauss kernel analysis: query rewriting

Peripherals: interrupt system of keys and CPU

Cloud native platform, let edge applications play out!

Target segmentation for 10000 frames of video, less than 1.4GB of video memory, open source code | ECCV 2022

Actf questions (dropper+master_of_dns)
![[leetcode] 3. Longest substring without repeated characters - go language problem solution](/img/63/57d3557d77d44b51b7d0f71669568f.png)
[leetcode] 3. Longest substring without repeated characters - go language problem solution

Worthington carboxyl transfer carbonic anhydrase application and literature reference

MySQL series | log module
![Nacos hand to hand teaching [i] dynamic configuration of Nacos](/img/c4/ae29475c795e879683227de5ba3cfc.png)
Nacos hand to hand teaching [i] dynamic configuration of Nacos
![[C + + primer notes] Chapter 6 functions](/img/9a/b79e7c3013678038420faee329d6b6.jpg)
[C + + primer notes] Chapter 6 functions
随机推荐
G024-db-gs-ins-01 openeuler deployment opengauss (single instance)
[27. Expression evaluation (infix expression)]
Target segmentation for 10000 frames of video, less than 1.4GB of video memory, open source code | ECCV 2022
How SAP Spartacus redefines login component
Specificity and five applications of Worthington alcohol dehydrogenase
What are the important trends revealed by the release of "operator data viability index"?
Google Earth engine - 1980 present global pressure, temperature, wind and other data sets
VC hesitates to invest in Henan
Visual studio code installation package download slow & Installation & environment configuration & new one-stop explanation
Kernel structure and design
JVM Foundation
Open source demo | release of open source example of arcall applet
Completefuture parallel asynchronous return processing
[summer daily question] Luogu p1605 maze
Harbor installation
Boutique solution | Haitai cloud password application service solution to create secure and compliant Cloud Applications
The difference between sigsuspend and sigwait
The cloud ecology conference comes with the "peak"!
Several application scenarios of NAT
Data integration | what are the tools for data integration at home and abroad?