当前位置:网站首页>P100 MSSQL database penetration test of secondary vocational network security skills competition
P100 MSSQL database penetration test of secondary vocational network security skills competition
2022-07-25 03:22:00 【Beluga】
What is penetration testing
Penetration testing is a process of actively evaluating users' information security measures . Through systematic operation and analysis , Actively discover various defects and weaknesses in the system and network , Such as design defects and technical defects .
Penetration testing is about any weakness of the system 、 Technical defects 、 Active vulnerability analysis process . This active analysis is carried out from the possible location of an attacker , And take the initiative to exploit security vulnerabilities conditionally from this position .
Penetration testing is different from other evaluation methods , The usual evaluation method is to find all relevant security problems according to known information resources or other evaluated objects . Penetration testing is based on known exploitable security vulnerabilities , To find out whether there are corresponding information resources . Usually the evaluation method Evaluation of The results are more comprehensive , Penetration testing pays more attention to the severity of security vulnerabilities .
mssql Database penetration test
1. In the local PC Penetration testing platform BT5 Use in zenmap Tool scan server scenario p100_win03-20 Network segment ( for example :172.16.101.0/24) Live hosts in range IP Address and designated open 1433、3306、80 port . And take the string that needs to be added in the command used by this operation as FLAG Submit ;
Use the command at the command terminal zenmap Open the scanning tool

Fill in the target address , And add after the default parameter -p 1433,3306,80
边栏推荐
- Force deduction brush question 7. Integer inversion
- Electronic bidding procurement mall system: optimize traditional procurement business and speed up enterprise digital upgrading
- Backtracking to solve subset problem
- Test question f: statistical submatrix
- [Kali's sshd service is enabled]
- Innobackupex parameter description
- Li Kou 343 integer partition dynamic programming
- Take a database statement note: when the field is empty, assign the default value to the result
- How to use two queues to simulate the implementation of a stack
- Bubble sort / heap sort
猜你喜欢
![[Kali's sshd service is enabled]](/img/1b/180534d51049177254e30c4b783eba.png)
[Kali's sshd service is enabled]
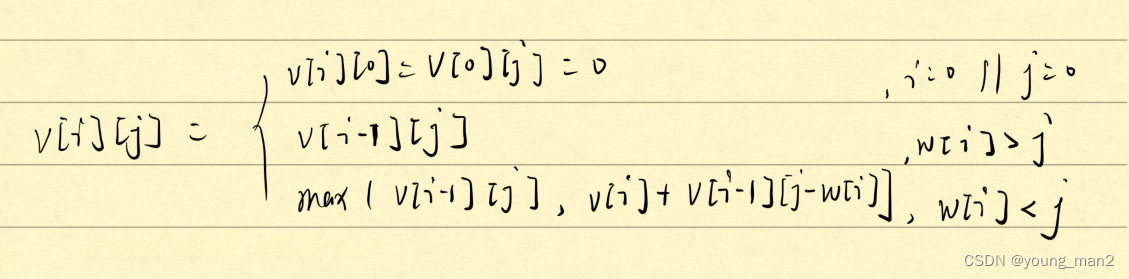
Dynamic planning of force buckle punch in summary

mysql_ Master slave synchronization_ Show slave status details

How chemical enterprises choose digital service providers with dual prevention mechanism

Learning Record V
How does Jupiter notebook change themes and font sizes?

Calculation method of confusion matrix

Page performance: how to optimize pages systematically?

Unified return data format

From input URL to page presentation
随机推荐
List type to string type
[template engine] microservice Learning Notes 6: freemaker
Introduction to Apache Doris grafana monitoring indicators
Task02 | EDA initial experience
ECMAScript new features
Openlayers draw circles and ellipses
Leetcode.745. prefix and suffix search____ Double dictionary tree + double pointer
Day 9 (capture traffic and routing strategy)
Handwriting promise
Swagger key configuration items
The relationship between private domain traffic and fission marketing. What is super app? Can our enterprise own it?
Banana pie bpi-m5 toss record (3) -- compile BSP
Enter an integer and a binary tree
Ffmpeg 4.3 add custom demuxer
Riotboard development board series notes (VII) -- the use of framebuffer
Hashcode details
FLASH read / write problem of stm32cubemx
Wechat H5 record
Use and introduction of vim file editor
CVPR 2020 | social stgcnn: pedestrian trajectory prediction based on graph convolution