当前位置:网站首页>[advanced C language] string and memory function (II)
[advanced C language] string and memory function (II)
2022-06-30 00:10:00 【Haozai lives today】
List of articles
1、strtok function
1、strtok The string will be separated according to the separator , Split into markers , And change the separator in the divided mark into ‘\0’, At the same time, a pointer to this tag will be returned
2、 Be careful :strtok Function changes the string being manipulated , So use strtok Function , It is generally used in the content copied at zero time
3、strtok When the function finds the first tag , The first argument of the function is not NULL, The position of the first mark will be strtok Function save
4、strtok When the function finds a non first tag , The first argument to the function is NULL, The segmentation will continue at the save location of the first mark
5、 When strtok After the function cannot find the tag , Will return a NULL
6、 Examples of function usage 
2、strerror function
1、 Return the error message corresponding to the error code 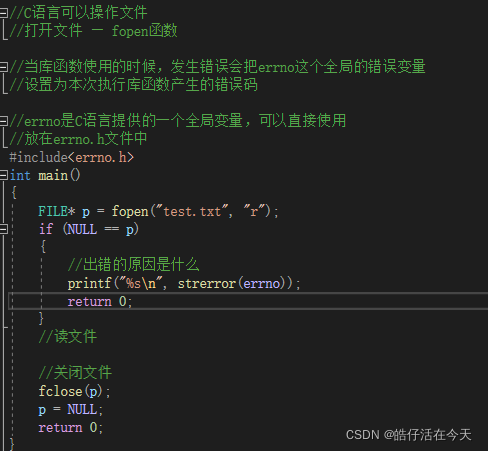
3、 Character classification function
1、iscntrl function : Any control character
2、isdigit:10 Hexadecimal Numbers 0~9
3、isxdigit: Hexadecimal number , Contains all decimal digits , Lowercase letters a~f, Capitalization A ~F
4、isslower: Determine if it's lowercase a~z
5、isspace: Determine whether it is a blank character : Returns a non-zero value , Not just back 0
6、isupper: The judgment is that they are all capital letters A~F
7、isalpha: Judgment is all letters , Regardless of case
8、isalnum: Determine whether it is a letter or a number
9、tolower: Character conversion , Convert capital letters to lowercase
10、toupper: Character conversion , Convert lowercase letters to uppercase
The actual cases 
4、 Memory function
4.1、memcpy function
1、 differ strcpy Functions can only copy strings ,memcpy Function can copy all types in memory
2、memcpy() Of 3 Parameters , The first is Destination space , The second is Source space , The third parameter is Number of bytes of copied content
3、 The actual cases 
4、 Simulation Implementation memcpy function
#include <stdio.h>
#include <string.h>
#include <assert.h>
void* my_memcpy(void* dest, const void* src, size_t num)//num Unit is byte
{
void* ret = dest;
assert(dest && src);
while (num--)
{
*(char*)dest = *(char*)src;// The effect of cast is only valid in the current statement
// The cast effect is temporary
dest = (char*)dest + 1;// So not directly dest++, But in this form
src = (char*)src + 1;//src Empathy
}
return ret;
}
int main()
{
int arr1[] = {
1,2,3,4,5,6,7,8,9,10 };
int arr2[5] = {
0 };
my_memcpy(arr2, arr1, 5 * sizeof(arr1[0]));
int i = 0;
for (i = 0; i < 5; i++)
{
printf("%d ", arr2[i]);
}
return 0;
}
4.2、memmove function
1、memmove and memcpy The usage of is basically the same , The difference is that , If Destination space and Source space There is overlap ,memmove It can still be copied correctly , however memcpy You can't copy correctly ( Examples are attached below )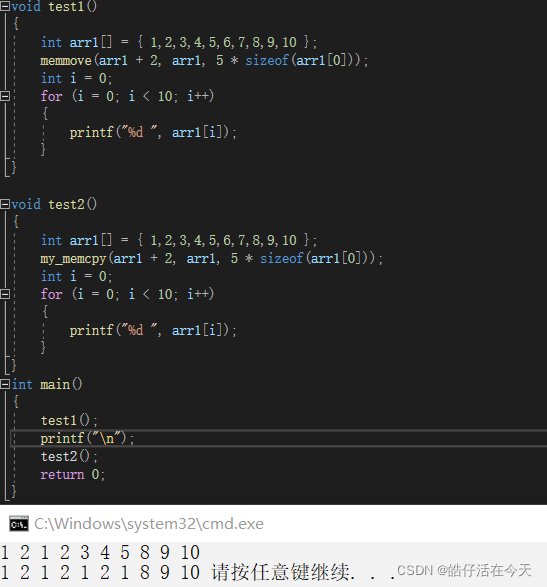
2、C Language requirements :
memcpy You can copy non overlapping memory space
memmove To handle those overlapping memory copies
3、 Simulation Implementation memmove function
#include <stdio.h>
#include <string.h>
#include <assert.h>
void* my_memmove(void* dest, const void* src, size_t num)
{
void* ret = dest;
assert(dest && src);
if (dest < src)
{
// front -> after
while (num--)
{
*(char*)dest = *(char*)src;
dest = (char*)dest + 1;
src = (char*)src + 1;
}
}
else
{
while (num--)
{
*((char*)dest + num) = *((char*)src + num);
}
}
return ret;
}
void test1()
{
int arr1[] = {
1,2,3,4,5,6,7,8,9,10 };
my_memmove(arr1 + 2, arr1, 5 * sizeof(arr1[0]));
int i = 0;
for (i = 0; i < 10; i++)
{
printf("%d ", arr1[i]);
}
}
int main()
{
test1();
return 0;
}
4.3、memcmp function
1、 Function declaration
int memcmp(const void *str1, const void *str2, size_t n)
2、 Return value
str1<str2 <0
str1=str2 =0
str1>str2 >0
3、 Use cases
// By entering the number of bytes n, Compare the two arrays starting from the first address n Bytes
#include<stdio.h>
#include<string.h>
int main() {
int arr1[5] = {
1,2,3,4,5 };
int arr2[5] = {
1,2,3,4,0x11223305 };
int ret = memcmp(arr1, arr2, 16);
printf("%d", ret);
return 0;
}
4.4、memset function
1、memset A function is an initialization function , You can initialize a continuous piece of memory to a certain value .
2、memset It is initialized in bytes
3、memset When initializing a function, you don't care what type of array you want to initialize , Are initialized in bytes
边栏推荐
- Solr basic operation 8
- QT learning 02 GUI program example analysis
- modelsim的TCL脚本的define incdir命令解析
- 基于zfoo开发项目的一些规范
- Color space conversion in video tonemapping (HDR to SDR) (bt2020 to bt709, YCbCr, YUV and RGB)
- Solr基础操作13
- Bee常用配置
- Bee common configuration
- Construction of module 5 of actual combat Battalion
- 如何实现搜索引擎中的拼写纠错功能——思路
猜你喜欢

云原生爱好者周刊:炫酷的 Grafana 监控面板集合

Teach you step by step to install webwind notes on edge browser

8软件工程环境

漫画安全HIDS、EDR、NDR、XDR
![[advanced C language] address book implementation](/img/e6/8a51d519d31ec323cf04c59a556325.png)
[advanced C language] address book implementation

Cloud native enthusiast weekly: cool collection of grafana monitoring panels

Basic operations such as MySQL startup under Windows platform
![[rust weekly library] Tokei - a utility for statistics of code lines and other information](/img/6c/4569cc0edaa01e4605c9c256193c31.png)
[rust weekly library] Tokei - a utility for statistics of code lines and other information
Siemens low code version 9.14: meet different needs

Introduction to reptiles: data capture of Betta barrage, with 11 introductory notes attached
随机推荐
There is no web-based development for the reward platform. Which is suitable for native development or mixed development?
Siemens low code platform connects MySQL through database connector to realize addition, deletion, modification and query
Set up enterprise NTP time server
What is flush software? Is it safe to open an account online?
克隆无向图[bfs访问每条边而不止节点]
Golang6 reflection
History of deep learning
如何实现搜索引擎中的拼写纠错功能——思路
Copy linked list with random pointer [space for time --hash record]
Clone undirected graph [bfs accesses each edge but not only nodes]
Solr基础操作8
AI首席架构师9-胡晓光 《飞桨模型库与行业应用》
Sword finger offer 15 Number of 1 in binary
项目一:部署 LAMP ecshop电商平台
How to realize the spelling correction function in search engine
Do mysqlcdc data not support windowing functions like row_ Number, lead
Cacti maximum monitoring number test
一步步教你在Edge浏览器上安装网风笔记
golang7_ TCP programming
How long will it take to open a mobile account? In addition, is it safe to open a mobile account?