当前位置:网站首页>Discussion and generation of digital signature and analysis of its advantages
Discussion and generation of digital signature and analysis of its advantages
2022-06-26 17:50:00 【lmn_】

0x01 Overview of digital signatures
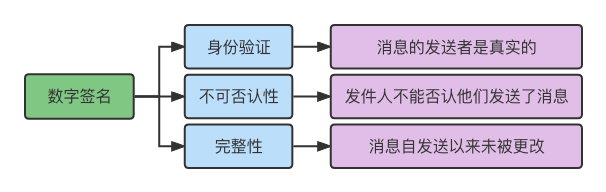
digital signature ( Public key digital signature ) Only the sender of information can produce a digital string that others can't forge , Is a scheme for verifying the authenticity of digital messages or documents , This digital string is also an effective proof of the authenticity of the information sent by the sender .
A valid digital signature that meets the prerequisites assures the recipient that the message was created by a known sender , Provides the authenticity of the information , And the message has not been changed during transmission , Provides information integrity .
Digital signature can also be called electronic signature , But pay attention to : Not all electronic signatures are called digital signatures .

Digital signatures are a standard element of most cryptographic protocol suites , Commonly used for software distribution 、 financial transactions 、 Contract management software , And other situations requiring detection of forgery or tampering .
Digital signature is usually used to implement electronic signature , This includes any electronic data with the intention of signing , But not all electronic signatures use digital signatures . Electronic signature has legal significance in some countries , Including Canada 、 South Africa 、 The United States 、 Algeria 、 Turkey 、 India 、 Brazil 、 Indonesia 、 Mexico 、 Saudi Arabia 、 Uruguay 、 Switzerland 、 Chile and EU countries .
0x02 Digital signature generation

The generation of digital signature is divided into three mechanisms , The first is the key generation algorithm , Generate a private key randomly in a group of private keys ; Signature algorithm , Used to generate a signature when the output private key and the message being signed ; Last , Signature verification algorithm , The algorithm checks the authenticity of the verification message together with the signature and public key .
All digital signatures are electronic , But not all electronic signatures are digital .
Digital signature just encrypts the data of the document to make it more secure , There are also a wider range of file types for colleague digital signatures , for example : video 、 voice 、 Music, etc .
0x03 Security functions and methods used in digital signature

- Personal identification number (PIN)、 Password and code : Used to verify and verify the identity of signers and approve their signatures .
- Asymmetric cryptography : Adopt the public key algorithm including private key and public key encryption and authentication .
- The checksum : A long string of letters and numbers , Represents the sum of correct numbers in a piece of numeric data , They can be compared to detect errors or changes . Checksums act as data fingerprints .
- Cyclic redundancy check (CRC): Error detection codes and verification functions for detecting changes in raw data in digital networks and storage devices .
- Certification authority (CA) verification :CA By accepting 、 authentication 、 Issue and maintain digital certificates to publish digital signatures and act as trusted third parties .
- Trust the service provider (TSP) verification :TSP It is an individual or legal entity that performs digital signature verification on behalf of the company and provides a signature verification report .
0x04 The advantages of digital signature
- Time stamp : By providing digitally signed data and time , Timestamps are very useful when time is critical , For example, stock trading 、 Lottery issuance and legal proceedings .
- Global acceptance and legal compliance : Public key infrastructure (PKI) Standards ensure that vendor generated keys are securely created and stored . Due to international standards , More and more countries accept that digital signatures are legally binding .
- Save time : Digital signatures simplify time-consuming physical document signatures 、 Storage and exchange procedures , Enable organizations to quickly access and sign documents .
- Cost savings : Organizations can be paperless , And save time previously spent on physical resources and on managing and transporting those resources 、 Funds for people and office space .
- traceability : Digital signatures create an audit trail , Make it easier to keep internal records . Because all content is digitally recorded and stored , The chance of manual signers or recorders making mistakes or misplacing is reduced .
References: https://blog.signaturit.com/en/what-is-a-digital-signature https://www.techtarget.com/searchsecurity/definition/digital-signature
边栏推荐
- 背包问题求方案数
- I want to know. I am in Zhaoqing. Where can I open an account? Is it safe to open an account online?
- Prometeus 2.34.0 new features
- Cache breakdown! Don't even know how to write code???
- LeetCode——226. 翻轉二叉樹(BFS)
- When I was in the library, I thought of the yuan sharing mode
- Army chat -- registration of Registration Center
- Microservice architecture practice: user login and account switching design, order query design of the mall
- 有依赖的背包问题
- Chen Qiang: Alibaba's 100 billion level large-scale digital business knowledge map helps business growth
猜你喜欢

Viewing the task arrangement ability of monorepo tool from turborepo

【推荐系统学习】推荐系统架构

Troubleshooting ideas that can solve 80% of faults!

VSCode使用 - Remote-SSH 配置说明

vutils.make_grid()与黑白图像有关的一个小体会

数据加密标准(DES)概念及工作原理

MySQL add column failed because there was data before, not null by default

14《MySQL 教程》INSERT 插入数据

SIGIR 2022 | University of Hong Kong and others proposed the application of hypergraph comparative learning in Recommendation System

深层次安全定义剖析及加密技术
随机推荐
Several key points in divorce agreement
The latest masterpiece of Alibaba, which took 182 days to produce 1015 pages of distributed full stack manual, is so delicious
无需人工先验!港大&同济&LunarAI&旷视提出基于语义分组的自监督视觉表征学习,显著提升目标检测、实例分割和语义分割任务!
Please advise tonghuashun which securities firm to choose for opening an account? Is it safe to open an account online now?
Prometeus 2.34.0 新特性
[buuctf.reverse] 126-130
[dynamic planning] Jianzhi offer II 091 Paint the house
【Unity】在Unity中使用C#执行外部文件,如.exe或者.bat
Introduction to distributed cache / cache cluster
离婚协议中的几个重点
Jouer avec Linux et installer et configurer MySQL facilement
【QNX】命令
What does the equals method compare? Who told you
腾讯钱智明:信息流业务中的预训练方法探索与应用实践
国信证券怎么开户?通过链接办理股票开户安全吗
ZCMU--1367: Data Structure
贝叶斯网络详解
ZCMU--1367: Data Structure
Synchronized description of concurrency
[qt learning notes]qt inter thread data communication and data sharing