边栏推荐
猜你喜欢

【NILM】非入侵式负荷分解模块nilmtk安装教程

Alibaba cloud full link data governance

免费ICP域名备案查接口

保留一位小数和保留两位小数

图形技术之管线概念

Cloud development who is the source code of undercover applet
![[vulhub shooting range]] ZABBIX SQL injection (cve-2016-10134) vulnerability recurrence](/img/c5/f548223666d7379a7d4aaed2953587.png)
[vulhub shooting range]] ZABBIX SQL injection (cve-2016-10134) vulnerability recurrence

More than 60 million shovel excrement officials, can they hold a spring of domestic staple food?
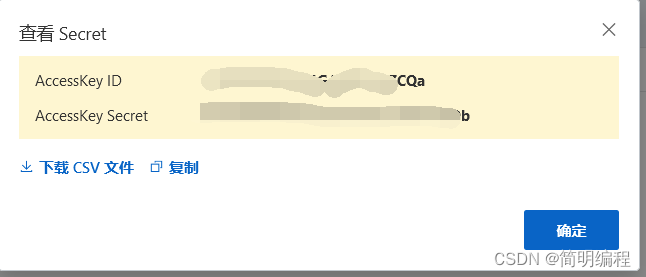
Maxcompute remote connection, uploading and downloading data files

Combine with (& &) logic or (||), dynamic binding and ternary operation
随机推荐
站在风暴中心:如何给飞奔中的腾讯更换引擎
Exploration on Optimization of elastic expansion engineering
[special session] SME growth plan - ECS special session
Knowledge points of 2022 system integration project management engineer examination: ITSS information technology service
L2TP connection failure guide in VPN
向量操作与坐标转换相关方法
鸿蒙os开发三
Ke Yi fallible point
用Ngrok 配置属于自己的免费外网域名
Unity Culling 相关技术
Tencent cloud security and privacy computing has passed the evaluation of the ICT Institute and obtained national recognition
The two most frequently asked locks in the interview
使用 kubeconfig 文件组织集群访问
云开发谁是卧底小程序源码
位运算
火线,零线,地线,你知道这三根线的作用是什么吗?
atguigu----16-自定义指令
A case of bouncing around the system firewall
Extend ado Net to realize object-oriented CRUD (.Net core/framework)
科一易错点