当前位置:网站首页>QT TCP UDP network communication < theory >
QT TCP UDP network communication < theory >
2022-06-25 12:37:00 【haoming Hu】
It takes about three or four blogs to talk about QT The content of network communication inside , Actually, it can't be said that QT Network communication , No matter what language , It's almost the same , The essence lies in the different ways of implementation , The mechanism of communication is the same
Chapter one : Basic knowledge of network communication
Network communication overview : Network programming is the foundation of the interconnection of all things , What's in use now TCP/IP agreement , It itself is divided into four layers : application layer 、 Transport layer 、 The layer 、 Network interface layer . But as an ordinary programmer , We only use the transport layer and application layer when we write the program . Now common network communication protocols mainly include :TCP UDP FTP HTTP, Whether in the window still Linux, The system provides a unified socket , That's what they say socket, stay QT in ,QT The network module has been encapsulated QtNetwor, The integration is very high , Basically meet the basic needs .
Transmission control protocol (transmission control protocol ,TCP) It's a reliable 、 Connection oriented 、 Transport protocols for data streams ,HTTP、FTP There are TCP Shadow ,TCP The protocol is suitable for continuous data transmission , It's also a transmission with guaranteed data security .
TCP working principle :TCP Protocol can provide reliable communication connection , So that the byte stream sent by my computer can be sent to other specified computers on the network without error , Its reliability is mainly due to its request ---- The reply This set of safe mechanism , It's not a simple request and response , It's a complex connection process , Here's the picture :
Three handshakes and four waves are more important , This mainly introduces the communication mechanism , About tcp Connect three handshakes and four waves, and add to other blogs next time .
Start the server first , Start the client after a while , It establishes a connection with this server after three handshakes . For some time after that , The client sends a request to the server , The server processes the request , And send back a response for the client . This process continues , Until the client sends a file terminator to the server , And close the client connection , Then the server also closes the connection on the server side , End running or wait for a new client connection .
Because of the complicated communication process , So the communication speed must be slower than UDP communication .
UDP:
User datagram protocol (User Data Protocol, UDP) It's a simple lightweight 、 unreliable 、 For datagram 、
Connectionless transport layer protocol , It can be used when reliability is not very important , Short message 、 Broadcast information, etc .
There are several situations suitable for application :
● Most of the network data is short message ;
● Have a large number of clients ;
● No special requirements for data security ;
● The burden of the Internet is very heavy , But it requires high response speed .
This is obvious , for instance :QQ And wechat are fully in line with the above applications .
working principle :UDP Client to UDP The server sends a certain length of request message , The limitation of message size is related to the protocol implementation of each system , But not beyond the lower level IP Under the agreement 64KB; UDP The server also responds in the form of a message . If the server does not receive this request , The client does not resend , So the transmission of message is unreliable .
Communication process :
The client doesn't have to connect to the server , Only responsible for sending message data to the server , Of course, the server does not need to manage whether the client is connected , Just listen to the client .
边栏推荐
- The first techo day Tencent technology open day in 2022 will be held online on June 28
- Penetration tool environment - installing sqli labs in centos7 environment
- Network | indicators and test methods to measure the quality of the network
- Ten commandments of self-learning in machine learning
- Go novice exploration pause
- The dist function of R language calculates the distance between two samples in dataframe data, returns the distance matrix between samples, and specifies the distance calculation method through the me
- The R language cartools package divides data, the scale function scales data, and the NaiveBayes function of e1071 package constructs a naive Bayesian model
- Learning notes 2022 overview | automatic graph machine learning, describing AGML methods, libraries and directions
- PHP takes the difference set of two arrays
- Ubuntu uninstalling PHP
猜你喜欢

Go novice exploration road 2

Zhangxiaobai's road of penetration (VI) -- the idea and process of SQL injection and the concat series functions and information of SQL_ Schema database explanation

laravel 9
![[regression analysis] understand ridge regression with case teaching](/img/95/91f6f2a018b8d320945b12562492eb.jpg)
[regression analysis] understand ridge regression with case teaching

How to use ARIMA model for prediction?
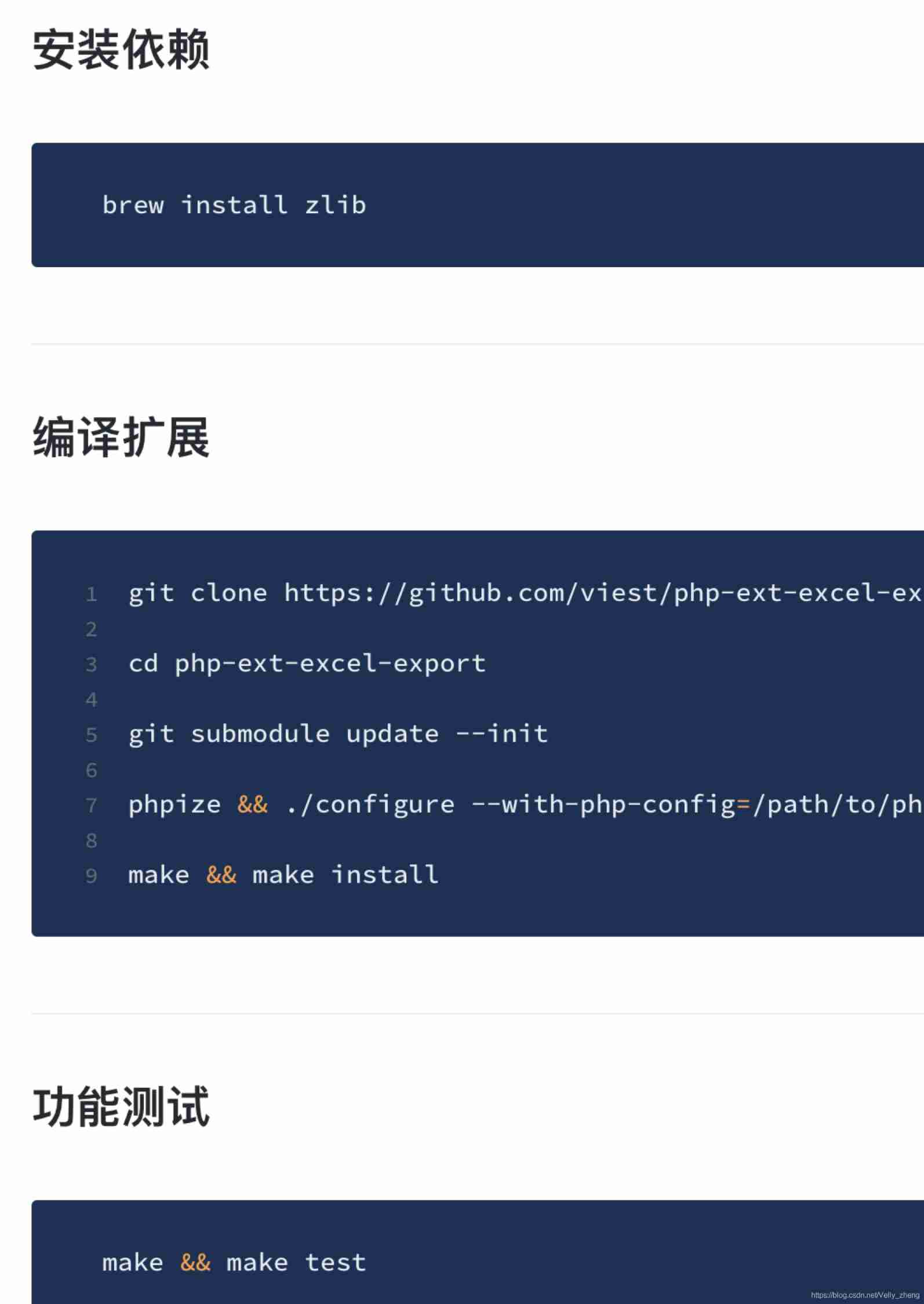
High performance + million level Excel data import and export

The server reported an error 503 service unavailable:the system returned: (71) protocol error

Jeecgboot startup popup configuration is still incorrect

Execution order of MySQL query statements join, on and where

Time series analysis - how to use unit root test (ADF) correctly?
随机推荐
ECSHOP commodity wholesale multi attribute multi specification multi inventory batch purchase ECSHOP wholesale plug-in ECSHOP multi attribute order
Penetration tool environment - Installation of sqlmap
Does sklearex make your sklearn machine learning model training fly fast?
Penetration tool environment -- use of cknife Chinese kitchen knife
R language uses the scale function to scale the input data of neural network to the minimum and maximum, scale the data to between 0 and 1, and divide the data set into training set and test set
[data midrange] what is the oneid of the data midrange? Isn't the master data fragrant?
Huile optimization system -- sharing of secondary development source code of huile optimization app system
Huikan source code -- Huikan app system secondary development source code sharing
揭秘GaussDB(for Redis):全面对比Codis
19. Implementation of MVVM architecture based on WPF event to command
Disconnected: No supported authentication methods available (server sent: )
Set the transparency of the picture to gradient from left to right
PHP replaces the key of a two-dimensional array with a specified element value
2022 meisai D topic ideas sharing + translation
Summary of common MySQL database commands (from my own view)
Fun pocket mall -- sharing the development source code of fun pocket app system
Digital currency exchange -- digital currency exchange system development source code sharing
MySQL and excel tables importing database data (Excel for MySQL)
Yunfan mall -- Yunfan mall system development source code sharing
Today, I will explain to you what is DFI and its development prospects