当前位置:网站首页>Intra domain information collection for intranet penetration
Intra domain information collection for intranet penetration
2022-06-25 20:19:00 【Bypass--】
When you get a computer in the domain Windows Server permissions , We need to collect as much information about the domain as we can , The more domain information is collected , The higher the success rate of domain control .
01、 Determine whether there is a domain
(1) Generally, we are collecting local information , Inquire about IP Network or system information , It's easy to find domain control .
ipconfig /all command 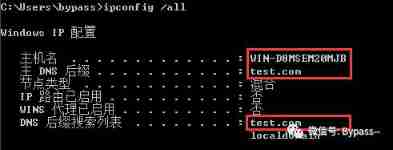
systeminfo command 
(2) View the current login domain and domain users
net config workstation
(3) All domain servers will act as time servers at the same time , So use the following command to determine the primary domain .
function net time /domain After the order , There are generally three situations as follows :
1. Domain of existence , But the current user is not a domain user , The prompt indicates that the permission is not enough
C:\Users>bypass>net time /domain
A system error occurred 5
Access denied .
2. Domain of existence , And the current user is a domain user
C:\Users\Administrator>net time /domain
\\dc.test.com The current time of is 2020/10/23 21:18:37
Command completed successfully .
3. The current network environment is workgroup , No domain exists
C:\Users\Administrator>net time /domain
Domain not found WORKGROUP Domain controller for .02、 Find a domain controller
(1) Generally speaking , Domain control server IP The address is DNS Server address , find DNS The server address can locate the domain controller .
nslookup/ping domain name , Resolve to domain control server IP Address 
(2) View the machine name of the domain controller
nltest /DCLIST:test.com
(3) View domain controllers
net group "Domain Controllers" /domain
3、 Get users and administrators in the domain
(1) Query the list of all user groups in the domain
net group /domain
(2) Query the list of domain Administrators
net group "Domain Admins" /domain
(3) Get a list of all domain users
net user /domain
(4) Get the specified domain user bypass Details of
net user bypass /domain
(5) Query the users of the built-in local administrator group in the domain
net localgroup administrators /domain
04、 Locate the domain administrator
If we can find which servers the domain administrator logged in to , You can attack these servers and try to take advantage of , To gain domain administrator privileges .
(1)PowerView
PowerView.ps1 Integrated into the PowerSploit In the frame , The script relies entirely on PowerShell and WMI Inquire about .
Domain user permissions , The information that can be obtained is related to user rights , Local administrator user cannot query .
Download address :
https://github.com/PowerShellEmpire/PowerToolsGet the login location information of all domain Administrators :

(2)PsLoggedOn
PsLoggedOn yes PSTools A small program in the toolkit , It shows the users who log in locally and the users who log in through the resources of the local computer or the remote computer .
Domain user permissions , The local administrator cannot query .
Download address :
https://docs.microsoft.com/en-us/sysinternals/downloads/psloggedonView the currently logged in user of domain controller :

(3)PVEFindADUser
Download address :
https://github.com/chrisdee/Tools/tree/master/AD/ADFindUsersLoggedOnUse domain users to perform , View the logged in users of all computers in the domain :

05、 Find domain management process
Compare with local processes and process users through the list of domain administrators , You can find the process run by the domain administrator .
net group "domain admins" /domain // Get the list of domain Administrators
tasklist /v // List all local processes and process users 
边栏推荐
- Transunet reading notes
- Redis practice: smart use of data types to achieve 100 million level data statistics
- Wechat applet cloud function does not have dependency option installed
- Jsonp non homologous interaction (click trigger)
- Use of serialize() and serializearray() methods for form data serialization
- 2.5 find the sum of the first n terms of the square root sequence
- 打新债证券开户安全吗
- Installing MySQL under Linux (CentOS 7)
- 4.ypthon function foundation
- Avoid material "minefields"! Play super high conversion rate
猜你喜欢

H5 application conversion fast application
Wechat applet cloud function does not have dependency option installed

Single chip microcomputer line selection method to store impression (address range) method + Example

Log in to Huawei game with a minor account, and pop up anti addiction prompt after startup
Pcl+vs2019 configuration and some source code test cases and demos

Web container basic configuration
Wechat applet connects to the server to display mqtt data information

200 OK (from memory cache) and 200 OK (from disk cache)

<C>. tic-tac-toe

Teach you how to create and publish a packaged NPM component
随机推荐
The functions in the applet page are better than those in app JS first execution solution
Is it safe to open a new bond account
206. reverse linked list (insert, iteration and recursion)
2.6 finding the sum of the first n terms of factorial sequence
How to understand var = a = b = C = 9? How to pre parse?
Short video is just the time. How can you quickly build your video creation ability in your app?
Automatic fitting when the applet reaches the top
PAT B1066
打新债证券开户安全吗
Pta--7-20 exchange minimum and maximum (15 points)
CSDN sign in cash reward
Pcl+vs2019 configuration and some source code test cases and demos
DICOM to NII
2.4 finding the sum of the first n terms of the interleaved sequence
The error log of vscode connecting to the server shows the problem of "insufficient permission". Directly use root to connect
Modifying routes without refreshing the interface
Panda weekly -2022/02/18
Skills of CCF question 2
Is it safe to open a new bond securities account
在打新债开户证券安全吗