当前位置:网站首页>Golang:[]byte to string
Golang:[]byte to string
2022-07-02 19:22:00 【Full stack programmer webmaster】
Hello everyone , I meet you again , I'm your friend, Quan Jun .
golang in , Character slices []byte convert to string The easiest way to do it is
package main
import (
"fmt"
_ "unsafe"
)
func main() {
bytes := []byte("I am byte array !")
str := string(bytes)
bytes[0] = 'i'// Pay attention to this line ,bytes The data is modified here , however str The printed ones are still unchanged ,
fmt.Println(str)
}Print information :I am byte array !
The above code bytes The data is modified here , however str The printed ones are still unchanged , Because []byte Memory of has been copied . Now let's look at the following code
package main
import (
"fmt"
"unsafe"
)
func main() {
bytes := []byte("I am byte array !")
str := (*string)(unsafe.Pointer(&bytes))
bytes[0] = 'i'
fmt.Println(*str)
}Print information :i am byte array !
Now the printed information has changed , Now you can see str and bytes Share a piece of memory .
The point of this is , In network communication , Most acceptance methods are []byte, If []byte The data is relatively large , Memory copy will affect the performance of the system .
Publisher : Full stack programmer stack length , Reprint please indicate the source :https://javaforall.cn/148601.html Link to the original text :https://javaforall.cn
边栏推荐
- Golang并发编程——goroutine、channel、sync
- Memory management of C
- Gamefi链游系统开发(NFT链游开发功能)丨NFT链游系统开发(Gamefi链游开发源码)
- 机器学习笔记 - 时间序列预测研究:法国香槟的月销量
- Use cheat engine to modify money, life and stars in Kingdom rush
- Introduction to the paper | analysis and criticism of using the pre training language model as a knowledge base
- mybatiesHelperPro工具必须的可以生成到对应项目文件夹下
- 使用xml文件打印mybaties-log插件的方式
- 2022软件工程期末考试 回忆版
- Chic Lang: completely solve the problem of markdown pictures - no need to upload pictures - no need to network - there is no lack of pictures forwarded to others
猜你喜欢

juypter notebook 修改默认打开文件夹以及默认浏览器
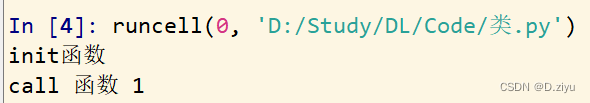
PyTorch函数中的__call__和forward函数

Codeworks 5 questions per day (1700 average) - day 4
Tutorial (5.0) 10 Troubleshooting * fortiedr * Fortinet network security expert NSE 5

Transformation of thinking consciousness is the key to the success or failure of digital transformation of construction enterprises

新手必看,點擊兩個按鈕切換至不同的內容

How to play when you travel to Bangkok for the first time? Please keep this money saving strategy
Yolov3 trains its own data set to generate train txt

ICDE 2023|TKDE Poster Session(CFP)

思维意识转变是施工企业数字化转型成败的关键
随机推荐
QT中的QPropertyAnimation使用和toast案列
STM32G0 USB DFU 升级校验出错-2
新手必看,点击两个按钮切换至不同的内容
"Patient's family, please come here" reading notes
In pytorch function__ call__ And forward functions
xml开发方式下AutowiredAnnotationBeanPostProcessor的注册时机
Digital scroll strip animation
IEDA refactor的用法
MySQL advanced learning summary 7: MySQL data structure - Comparison of hash index, AVL tree, B tree and b+ tree
《病人家属,请来一下》读书笔记
Talk about the design of red envelope activities in e-commerce system
【JVM调优实战100例】01——JVM的介绍与程序计数器
Masa framework - DDD design (1)
Page title component
#gStore-weekly | gStore源码解析(四):安全机制之黑白名单配置解析
metric_logger小解
Obligatoire pour les débutants, cliquez sur deux boutons pour passer à un contenu différent
PyTorch函数中的__call__和forward函数
R language uses the lsnofunction function function of epidisplay package to list all objects in the current space, except user-defined function objects
机器学习笔记 - 时间序列预测研究:法国香槟的月销量