当前位置:网站首页>横向越权与纵向越权[通俗易懂]
横向越权与纵向越权[通俗易懂]
2022-07-02 18:09:00 【全栈程序员站长】
大家好,又见面了,我是你们的朋友全栈君。
横向越权:横向越权指的是攻击者尝试访问与他拥有相同权限的用户的资源 纵向越权:纵向越权指的是一个低级别攻击者尝试访问高级别用户的资源
如何防止横向越权漏洞:
- 可通过建立用户和可操作资源的绑定关系,用户对任何资源进行操作时,通过该绑定关系确保该资源是属于该用户所有的。
- 对请求中的关键参数进行间接映射,避免使用原始关键参数名,比如使用索引1代替id值123等
如何防止纵向越权漏洞:
建议使用基于角色访问控制机制来防止纵向越权攻击,即预先定义不同的权限角色,为每个角色分配不同的权限,每个用户都属于特定的角色,即拥有固定的权限,当用户执行某个动作或产生某种行为时,通过用户所在的角色判定该动作或者行为是否允许。
发布者:全栈程序员栈长,转载请注明出处:https://javaforall.cn/148590.html原文链接:https://javaforall.cn
边栏推荐
- 聊聊电商系统中红包活动设计
- 教程篇(5.0) 09. RESTful API * FortiEDR * Fortinet 网络安全专家 NSE 5
- Stratégie touristique d'été de Singapour: un jour pour visiter l'île de San taosha à Singapour
- Processing strategy of message queue message loss and repeated message sending
- metric_logger小解
- C的内存管理
- 第一次去曼谷旅游怎么玩?这份省钱攻略请收好
- Reduce -- traverse element calculation. The specific calculation formula needs to be passed in and combined with BigDecimal
- 新加坡暑假旅游攻略:一天玩转新加坡圣淘沙岛
- 潇洒郎:彻底解决Markdown图片问题——无需上传图片——无需网络——转发给他人图片无缺失
猜你喜欢
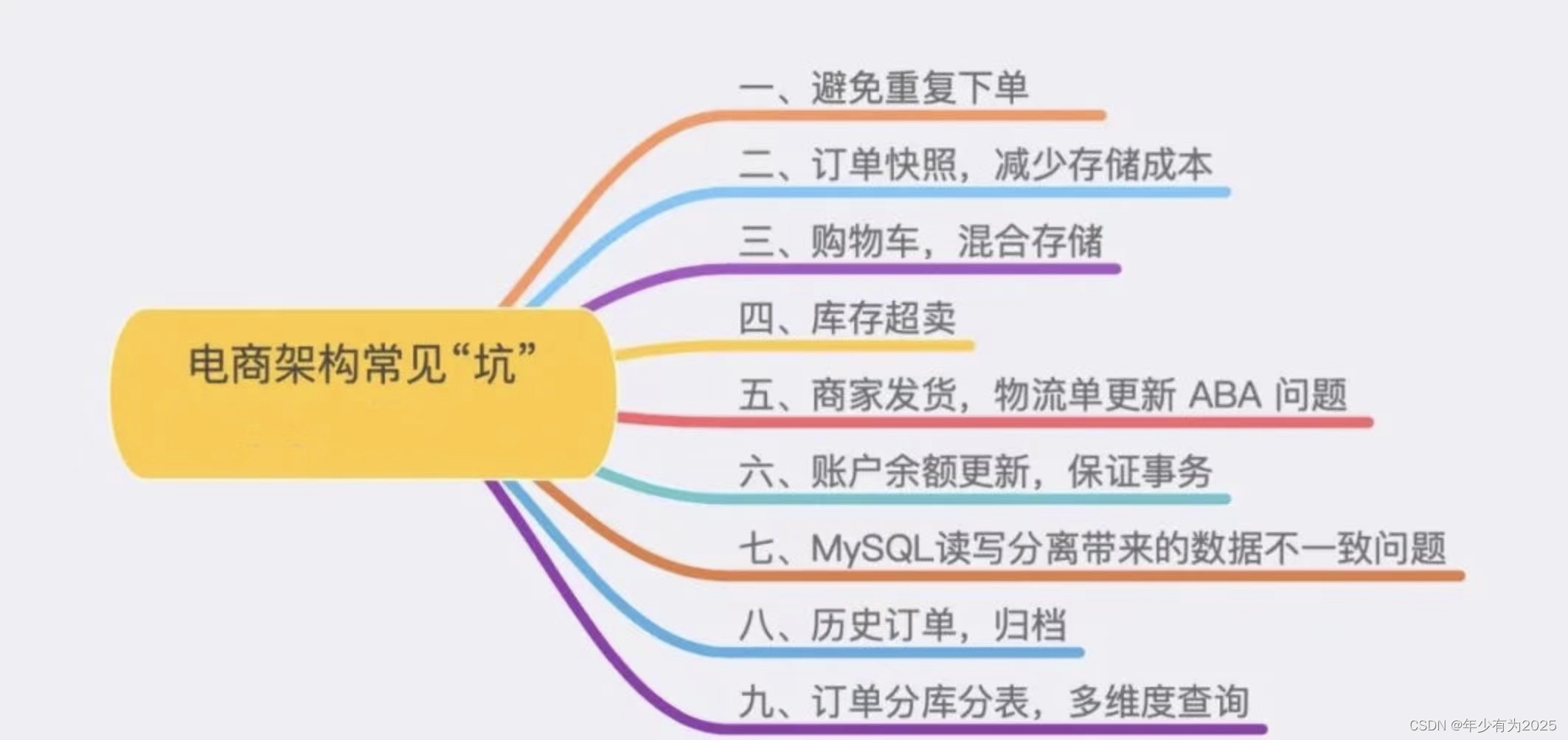
Have you stepped on the nine common pits in the e-commerce system?

新手必看,点击两个按钮切换至不同的内容
![[0701] [paper reading] allowing data imbalance issue with perforated input during influence](/img/c7/9b7dc4b4bda4ecfe07aec1367fe059.png)
[0701] [paper reading] allowing data imbalance issue with perforated input during influence

Web2.0的巨头纷纷布局VC,Tiger DAO VC或成抵达Web3捷径
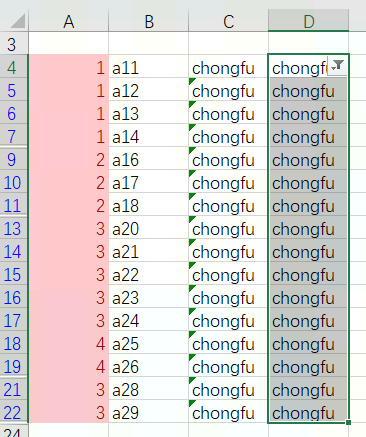
Excel finds the same value in a column, deletes the row or replaces it with a blank value

What is 9D movie like? (+ common sense of dimension space)

思维意识转变是施工企业数字化转型成败的关键
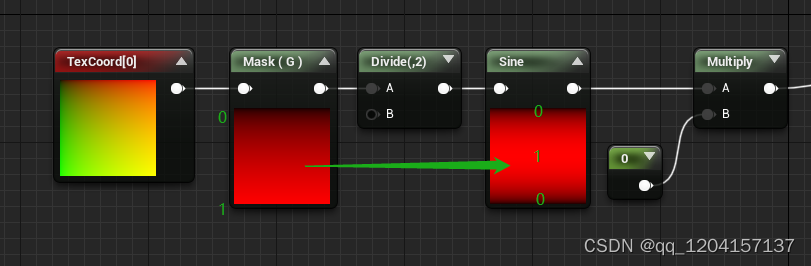
Tips for material UV masking

Tutorial (5.0) 09 Restful API * fortiedr * Fortinet network security expert NSE 5
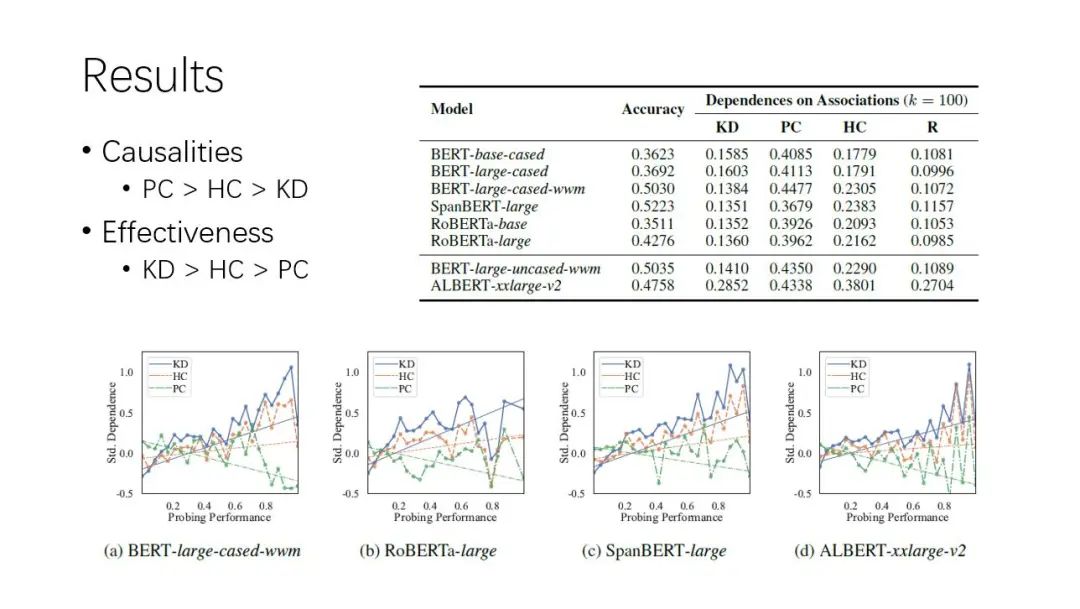
论文导读 | 关于将预训练语言模型作为知识库的分析与批评
随机推荐
Have you stepped on the nine common pits in the e-commerce system?
R language uses lrtest function of epidisplay package to perform likelihood ratio test on multiple GLM models (logisti regression). Compare whether the performance of the two models is different, and
教程篇(5.0) 09. RESTful API * FortiEDR * Fortinet 网络安全专家 NSE 5
Learning summary of MySQL advanced 6: concept and understanding of index, detailed explanation of b+ tree generation process, comparison between MyISAM and InnoDB
拦截器与过滤器的区别
Compile oglpg-9th-edition source code with clion
C文件输入操作
Develop fixed asset management system, what voice is used to develop fixed asset management system
论文导读 | 机器学习在数据库基数估计中的应用
Mysql高级篇学习总结6:索引的概念及理解、B+树产生过程详解、MyISAM与InnoDB的对比
Masa framework - DDD design (1)
R语言使用epiDisplay包的lsNoFunction函数列出当前空间中的所有对象、除了用户自定义的函数对象
R language ggplot2 visual Facet: gganimate package is based on Transition_ Time function to create dynamic scatter animation (GIF)
M2dgr: slam data set of multi-source and multi scene ground robot (ICRA 2022)
SLC、MLC、TLC 和 QLC NAND SSD 之间的区别:哪个更好?
从list转化成map的时候,如果根据某一属性可能会导致key重复而异常,可以设置处理这种重复的方式
LightGroupButton* sender = static_ cast<LightGroupButton*>(QObject::sender());
Deep learning mathematics foundation
聊聊电商系统中红包活动设计
According to the atlas of data security products and services issued by the China Academy of information technology, meichuang technology has achieved full coverage of four major sectors