当前位置:网站首页>Intranet penetration lanproxy deployment
Intranet penetration lanproxy deployment
2022-08-01 19:30:00 【little black note】
The environment used this time is centos 7.9
Both windows and Linux environments support the installation of both the server and the client.jdk
It is best to download the server and client as a set
Server: proxy-server
Client: proxy-client
1. Server deployment
1. In the server server, under the root directory, create a proxy directory
Instruction: mkdir /root/proxy
Verification means: ls /root Check whether the displayed content isContains proxy directory
2. Upload all files in the "server" directly to the /root/proxy directory
3. Start the intranet penetration service
Command: chmod +x /root/proxy/bin/startup.sh
Command: /root/proxy/bin/startup.sh
Verification method: ps -ef |grep lanproxy to see if there is any feedback
4. Set the service to start automatically at boot
Command: echo /root/proxy/bin/startup.sh >> /etc/rc.local
Verification method: cat /etc/rc.local to check whether it contains/root/proxy/bin/startup.sh
5. Web page login verification http://server IP: 8090 (I have to use the virtual machine for the experimental environment)
Username: admin Password: admin #Available in the configuration file /root/proxy/conf/config.Modify in properties
server.bind=0.0.0.0server.port=4900server.ssl.enable=trueserver.ssl.bind=0.0.0.0server.ssl.port=4993server.ssl.jksPath=testca.jksserver.ssl.keyStorePassword=testserver.ssl.keyManagerPassword=testserver.ssl.needsClientAuth=falseconfig.server.bind=0.0.0.0config.server.port=8090config.admin.username=adminconfig.admin.password=admin
6. Port opening
Cloud host release: 4900, 4993, 8090, 10000-11000 port segment
Second, client deployment
1. In the client, under the root directory, create a proxy directory
Instruction: mkdir /root/proxy
Verification method: ls /root Check whether the displayed content containsproxy directory
2. Upload all files in the "client" directly to the /root/proxy directory
3. Create a client
Log in to the server web management interface and create a client
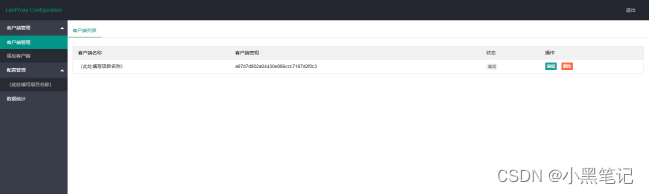
Copy client key
Log in to the client command line interface and modify the configuration file:
Modify the /root/proxy/conf/config.properties file as follows
ssl.enable=truessl.jksPath=testca.jksssl.keyStorePassword=testserver.host=192.168.163.100 #Here write the actual application scenario serverget IP#default ssl port is 4993server.port=4993client.key=a97d7d802a04430e886ccc7187d2f0c3 #client key4. Start the intranet penetration client
Command: chmod +x /root/proxy/bin/startup.sh
Command: /root/proxy/bin/startup.sh
Verification means: ps -ef |grep lanproxy to see if there is any feedback
5. Set the service to start automatically at boot
Command: echo /root/proxy/bin/startup.sh >> /etc/rc.local
Verification means: cat /etc/rc.local to see if it contains/root/proxy/bin/startup.sh
6. Log in to the web management interface of the server and check the online status of the client.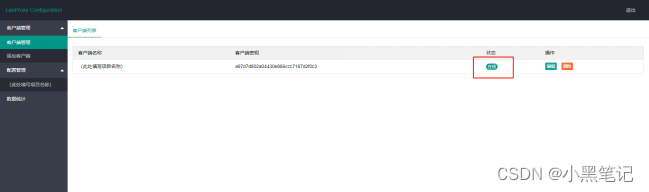
Do client port mapping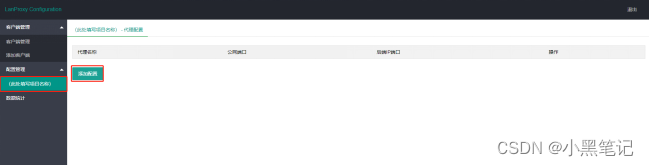
"Proxy name": Named after the port name that needs to be mapped, here is port 22
"Public network port": Port between 10000-11000, generally a single client is assigned 10 consecutive port numbers, the firstClient port range 10000-10009, and so on
"backend IP port": 127.0.0.1:22 (22 here is consistent with "proxy name")
Multiple ports can be added, for example:
边栏推荐
- 如何看待腾讯云数据库负责人林晓斌借了一个亿炒股?
- [pyqt5] Custom controls to achieve scaling sub-controls that maintain the aspect ratio
- 不恰当Equatable协议==方法的实现对SwiftUI中@State修饰属性的影响
- ExcelPatternTool: Excel表格-数据库互导工具
- OSPO 五阶段成熟度模型解析
- How to install voice pack in Win11?Win11 Voice Pack Installation Tutorial
- 手撸代码,Redis发布订阅机制实现
- Risc-v Process Attack
- cf:D. Magical Array【数学直觉 + 前缀和的和】
- [Server data recovery] Data recovery case of offline multiple disks in mdisk group of server Raid5 array
猜你喜欢
工作5年,测试用例都设计不好?来看看大神的用例设计总结

力扣刷题之移动零

屏:全贴合工艺之GFF、OGS、Oncell、Incell

明日盛会|ApacheCon Asia 2022 Pulsar 技术议题一览
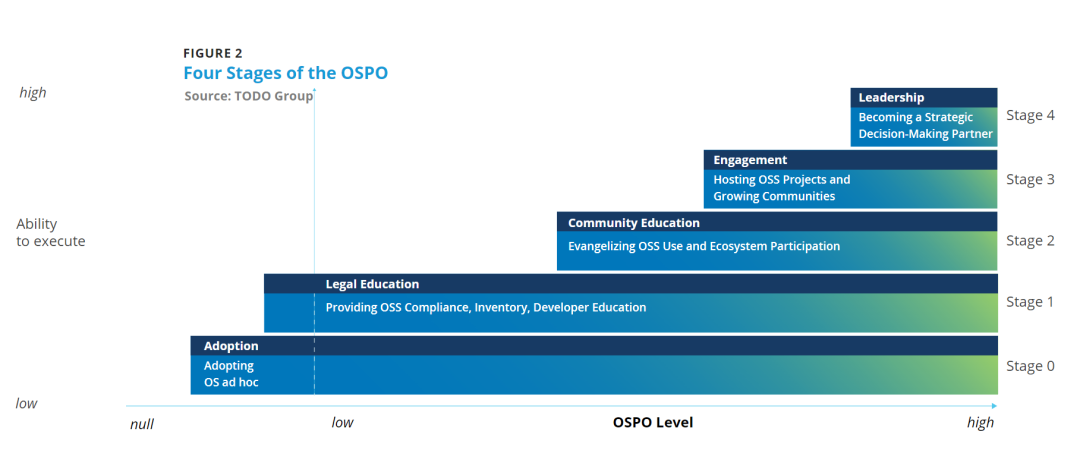
OSPO 五阶段成熟度模型解析
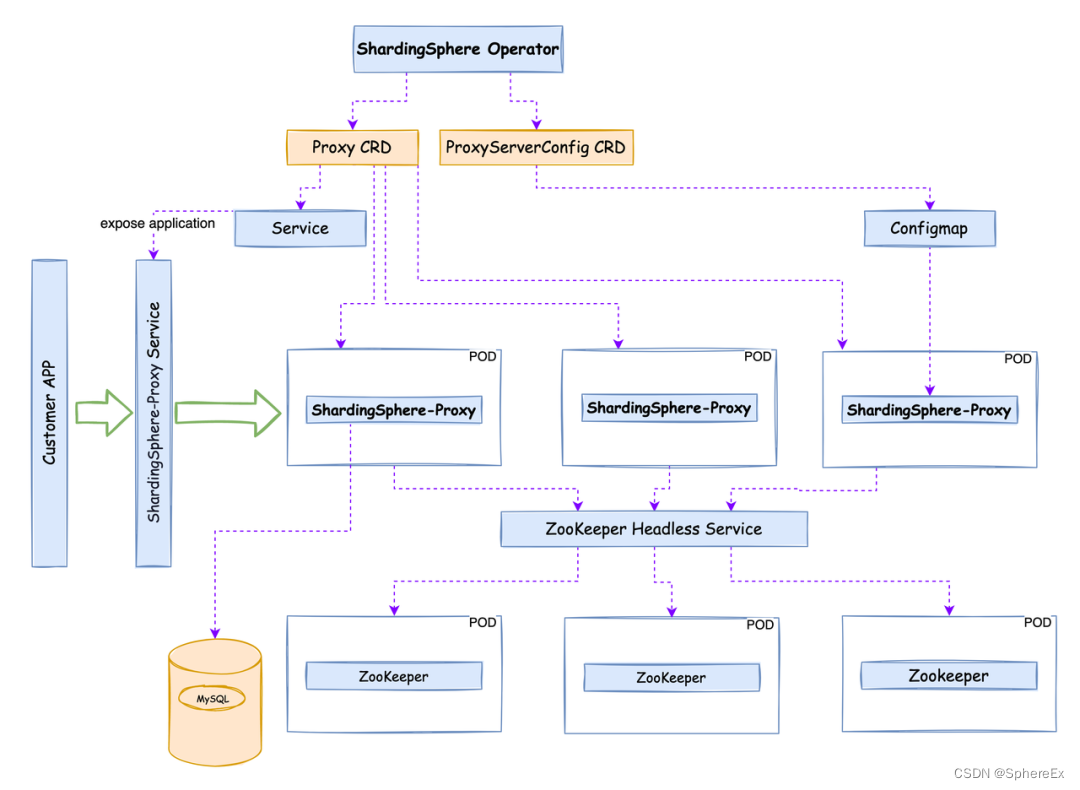
Database Plus 的云上之旅:SphereEx 正式开源 ShardingSphere on Cloud 解决方案
Creo5.0草绘如何绘制正六边形
#yyds干货盘点# 面试必刷TOP101: 链表中倒数最后k个结点

开源视界 | StreamNative 盛宇帆:和浪漫的人一起做最浪漫的事

Screen: GFF, OGS, Oncell, Incell of full lamination process
随机推荐
哈哈!一个 print 函数,还挺会玩啊!
Try compiling QT test on Allwinner V853 development board
SaaS管理系统的应用优势在哪里?如何高效提升食品制造业数智化发展水平?
nacos安装与配置
mysql解压版简洁式本地配置方式
MySQL你到底都加了什么锁?
安装win32gui失败,解决问题
DAO开发教程【WEB3.0】
modbus总线模块DAM-8082
安徽建筑大学&杭州电子科技大学|基于机器学习方法的建筑可再生能源优化控制
内网穿透 lanproxy部署
C#/VB.NET 从PDF中提取表格
Screen: GFF, OGS, Oncell, Incell of full lamination process
选择合适的 DevOps 工具,从理解 DevOps 开始
【Redis】缓存雪崩、缓存穿透、缓存预热、缓存更新、缓存击穿、缓存降级
对于web性能优化我有话说!
openresty 动态黑白名单
Combining two ordered arrays
Win11校园网无法连接怎么办?Win11连接不到校园网的解决方法
重保特辑|拦截99%恶意流量,揭秘WAF攻防演练最佳实践