当前位置:网站首页>Computer network interview knowledge points
Computer network interview knowledge points
2022-07-01 13:16:00 【yue_ xin_ tech】
1. Computer network architecture model
- The physical layer : establish 、 maintain 、 Disconnect the physical connection .
- Data link layer : Establish logical connections 、 Address the hardware 、 Error checking and other functions .
- The network layer : Logical address addressing , Realize path selection between different networks .
- Transport layer : Define the protocol port number of data transmission , And flow control and error checking .
- The session layer : establish 、 management 、 Terminate the conversation ,( The application layer has been incorporated into the five layer model )
At one end of the session is the local host , The other end is the remote host . - The presentation layer : Presentation of data 、 Security 、 Compress .( The application layer has been incorporated into the five layer model )
The format is ,JPEG、ASCll、EBCDIC、 Encryption format, etc . - application layer : An interface between network services and end users .


The network protocol is actually an end-to-end Communication rules , With these rules , The communication between both sides is meaningful .
2. TCP/IP Header format for

among , There are several important points :
Serial number (seq): The serial number of the packet , Confirm the continuity of the package through the sequence number , Solve the disorder of packages .Response number (ack): Confirmation sequence number for the above field , For example, the server receives a request from the client , It contains seq Serial number , When the server responds back , Will be carried out in ack = seq + 1 Field settings for , Indicates the cumulative data received .Window: Slide the window to use , Used to feed back the packet size that the receiver can handle next , Prevent unequal processing capacity of data packets between both parties , It mainly solves the problem of flow control .TCP Flag:TCP Packet type , To assist in TCP Stage processing , such as SYN To establish a connection ,FIN Indicates that the connection is closed .
3. TCP The state of circulation

4. TCP Three handshakes of 、 How about four waves ? Why is it designed this way? ?
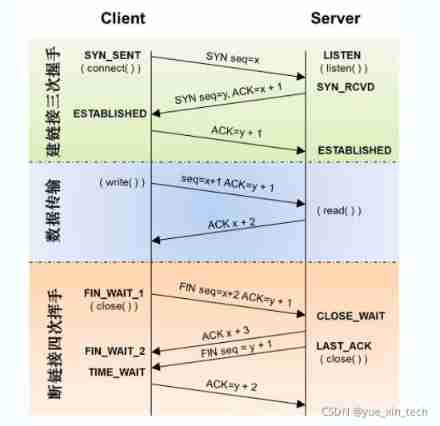
If we only do 2 A handshake establishes a connection , So for Server It's too easy to establish a connection , Basically, a client came , that Server The connection is about to be established . This situation will lead to too low connection cost ,Server The end is very tolerant of overload .
Four waves because TCP yes full duplex Of , There are two behaviors of data sending and receiving , Data inflow and outflow in both directions need to be closed .
5. What is semi connection ? Related to it SYN What is the attack like ?
When the service receives a client request to connect SYN, Then respond to the client ACK and SYN after , The connection will be maintained to the semi connection queue . When the client replies again ACk after , The current connection will be maintained in the full connection queue .
SYN The attack was DOS A type of attack , Establish a connection by forging a large number of requests , Make the semi connected queue exceed the maximum capacity , Other normal requests cannot be processed .
6. Why does the initiator in the four waves need to wait TIME_WAIT Time to close the connection ?
TIME_WAIT Is a timing setting , stay 2*MSL(MSL Represents the lifetime of a packet in a network environment , It's usually 2 minute , Linux Li Wei 30s) After time, it will really CLOSED.
Why not close it immediately , It is mainly to allow the passive shutdown party to have enough time to receive the final Ack package , If not received , The passive party will resend Fin package , Re trigger the active party to send the last Ack package . In this case , We can try our best to ensure that the passive shutdown party closes the connection as soon as possible , After all, the active shutdown party needs to bear the main responsibility , So there will be TIME_WAIT I'm waiting for you .
Another reason is the fear that the current connection will be released immediately , There is a certain probability that the current connection ID will be reused ( Quintuples ), The old network packet was received at this time due to delay , There may be package confusion .
7. TCP What is the retransmission mechanism of ?
TCP All packets sent need to be sent by the receiver Ack Package response , If there is no response within a certain time , Then the sender will think that the packet did not arrive correctly , Retransmission action is required . This is it. TCP The retransmission mechanism .
TCP The retransmission mechanism in will have a timeout judgment , This timeout is not very accurate , Or it's not very standard , After all, different network environments , The arrival of the package will be different .
therefore TCP A sampling time is used , First, the time of a packet from sending to response confirmation under normal conditions is recorded , That is to say RTT(Round Trip Time) Time , Make some formula calculations according to this time , Get the value of timeout :RTO(Retransmission TimeOut)
For the retransmission mechanism , There is another trigger mechanism . The above situation belongs to the sender to find out the sending situation , There is another situation that the receiver can detect . For example, the sender sent 1, 2, 3 My bag , But in fact, the receiver only receives 1 and 3, I haven't been able to receive 2 This package , Then the receiver will respond to three consecutive About 2 Of ack package .
When the sender receives such a continuous 3 individual ack After package , You know you need to retransmit 2 了 , There is no need to wait until 2 The timeout of was not acknowledged and triggered , Can be retransmitted in advance 2 This bag. .
8. introduce TCP Flow control of , What about sliding windows ?
TCP use The sliding window The flow is controlled , The so-called sliding window means that the sender and receiver maintain a window respectively , In this window, the corresponding packet will be maintained , To perceive the current data processing .
The window on the receiver side is called Receiving window , It specifically represents the current packet size that can be received , The formula is : Current maximum acceptable buffer size - Currently received size , When the connection is established, it is generally 65535 byte .
After calculating the acceptable size , The receiver will set this value to TCP In the head Window Field , Then respond back to the sender , The sender will know the current packet size allowed to be sent .
The window on the sender side is called Send window , In normal logic , The sending window maintains the data to be sent , That is, the transmission data calculated according to the size of the reception window just fed back .
But because a packet needs to be sent with ACK Response is the complete process , So for these “ Sent unresponsive ” The data should also be included in the management of the sending window , And only really ACK Respond back , To continue the preparation of the next packet .

It should be noted that , If the sender receives Window The size is 0, It means that the current receiver is no longer capable of processing new packets , At this point, the sender will no longer send data , Until the receiver sends a Window announcement , Before continuing to send data .
But here's a situation to consider , The receiver failed to deliver the window notification to the sender due to network problems , Then the sender will be waiting . So for the sender , It will start Window detection action , The receiver is required to ACK Its current receive window size , If exceeded 3 The first discovery action , Then directly disconnect .
9. TCP How to perceive and control the congestion in the network environment ?
TCP The protocol Abstracts Congestion window (cwnd) The concept of , It will adjust dynamically according to the current degree of network congestion . Due to the consideration of congestion , The sending window we mentioned above cannot only consider the receiving window , Need to carry out min( Congestion window , Receiving window ) Your choice was sent .
10. MTU and MSS What is it? ?
MSS Express Network transmission data The maximum of , If MSS Plus the Baotou size , Indicates the maximum network transmission message :MTU .
stay Internet In this kind of Internet , commonly MTU Defined as 576 byte , subtract TCP、IP The baotou 40 byte , You can get MSS = 536 Byte value ; And in a LAN like Ethernet , commonly MTU It'll be bigger :1500 byte ,MSS by 1460 byte .
11. TCP What is the slow start of ? What are the links ?
When the connection is established , When starting data transfer ,TCP The protocol stipulates that large packets cannot be sent at the beginning , This avoids problems in the network environment , Newly added connections exacerbate congestion . therefore , For new connections , You need to increase the amount of data bit by bit , That's what's called Slow start .
among , The calculation process of congestion window involved in slow start is as follows :
- When you first set up a connection , Congestion window = 1
- Whenever you receive a ACK Packet time , Congestion window = Congestion window + 1, At this time, it increases linearly .
- Every time I pass a RTT, Congestion window = Congestion window * 2, At this time, it shows an exponential upward trend .
12. What is congestion avoidance ?
From the slow start algorithm , Every time I pass by RTT after , The growth rate of congestion window will become very severe , If there are no restrictions , Then the bandwidth will be full soon . therefore , TCP The protocol uses a threshold called slow start (ssthresh) The variable of ( Usually take 65535 byte ). When cwnd( Congestion window ) Beyond this limit , Will enter the so-called Congestion avoidance Stage .
In the congestion avoidance phase , The calculation process of congestion window is as follows :
- Every time I receive one ACK Packet time , Congestion window = Congestion window + 1/ Congestion window
- Every time I pass a RTT, Congestion window = Congestion window + 1
As can be seen from the above algorithm , After entering the congestion avoidance phase , The sending size of packets will increase linearly . In this way , bring TCP The transmission is very fast in the early stage , Then slowly lower , Reach the best value of the network .
13. When congestion happens ,TCP What will happen to ?
When congestion occurs , The calculation of congestion window is in different TCP The version will be different , There are mainly the following 3 Kind of version :
Tahoe edition
Tahoe The version is TCP The earliest version of , When it finds that it needs to retransmit , That triggers RTO Timeout or sender receives three duplicates ACK Packet time , At this time, the action will be :
- sshthresh( Slow start threshold ) = cwnd( Congestion window ) / 2
- cwnd Reset to 1
- Go back to the slow start phase
Reno edition
Reno The action of version is :
- sshthresh( Slow start threshold ) = cwnd( Congestion window ) / 2
- cwnd( Congestion window ) = sshthresh( Slow start threshold ) + 3 * MSS ( take 3 A repetition ACK Take into account )
- Enter the rapid recovery phase
among , The calculation of rapid recovery phase is as follows :
- When the retransmitted packet is sent out , Received a retransmission packet ACK after ,cwnd( Congestion window ) = cwnd( Congestion window ) + 1
- When a new packet is received ACK after , The quick recovery process is now complete , be cwnd = sshthresh, Then return to the congestion avoidance phase
NewReno edition
NewReno It's right Reno Improvement , It mainly optimizes the rapid recovery phase , stay Reno In the version , What is considered is the loss of a packet . However , In practice , Send a data window , There may be a lot of packet loss .
In this case , Will trigger multiple times cwnd and ssthresh Halve , once cwnd Reduce to less than 3 when , That is, the sending window will appear less than 3 The circumstances of , This will no longer trigger 3 A fast retransmission , Can only rely on RTO Overtime , In general RTO The value of is relatively large ( Too small will often trigger retransmission ) Of , At this time, the whole transmission speed will be greatly reduced .
therefore NewReno The fast recovery phase will not end until all packets are confirmed , such cwnd and sshthresh It won't be easily reduced .
NewReno It mainly uses a recover Variable , As in the current data window , Maximum sequence number of possible packet loss . That is, if packet loss occurs , And greater than the current recover value , The value is updated .
When receiving the receiver's ack after , Will be carried out in ack_seq The judgment of the , If ack_seq > recover, At this point, you can end the rapid recovery phase ; If ack_seq < recover, It means that multiple packets are lost , Can't end the fast recovery phase yet . Through such control , To improve the throughput of the whole .
14. TCP What algorithms or mechanisms are there to improve efficiency ?
Nagle Algorithm
Nagle The algorithm combines multiple small packets into one segment , And wait until certain conditions are met , Send it together . The specific trigger conditions are as follows :
- If the packet length reaches MSS, Is allowed to send
- If you include FIN, Is allowed to send
- If set TCP_NODELAY, Is allowed to send
- Not set TCP_CORK Option , If all the small packets sent ( Packet length less than MSS) All is confirmed , Is allowed to send
When none of the above conditions are met , But a timeout occurred ( It's usually 200ms), Send immediately .
about TCP In terms of agreement , By default Nagle Algorithm , Reduce network load , Reduce network congestion , Improve network throughput .
Delay Ack( Delay confirmation )
stay TCP In the confirmation mechanism , It is possible not to each in the communication process TCP Data packets are processed separately ACK Package response , But when transmitting data , By the way, the ACK The message is sent with the packet , This can improve the utilization of network traffic .
If in a certain period of time ( commonly 40 ms) No packets to send , At this time, it will be carried out separately ACK Package response . This process is also called Delay Ack.
15. TCP How about sticking and unpacking in ?
TCP Is byte stream oriented transport , It will load and send some data according to the packet processing capacity of the receiver and the current network congestion , Plus there are Nagle This algorithm for integrating small packets exists . So for the receiver , The received data may be glued together , It may also be split , The so-called sticking and unpacking .
For sticking and unpacking , Common solutions are :
- Add the length of the current packet to be transmitted at the header of the packet , Let the receiver cut according to the length .
- Encapsulate packets into fixed lengths , Not enough to make up 0, Let the receiver parse by a fixed length .
- Artificially adding boundaries to packets , For example, add special characters at the end of the packet , When parsing to special characters , The receiver thinks it has read a complete and meaningful data segment .
16. TCP Why is it reliable ?
TCP The connection and disconnection of both parties are carried out through mutual communication ( Three handshakes 、 Four waves ). In the process of data transmission, response confirmation will be carried out 、 Over time retransmission 、 flow control 、 Congestion control 、 Congestion avoidance and other means to ensure the accuracy of transmission .
17. TCP and UDP The difference between
TCP It is a reliable connection for byte stream , and UDP It is data message oriented connection , Reliable connection is not guaranteed , But the transmission is relatively fast .TCP Often used in mail 、 File transfer, which requires high accuracy , and UDP It is often used in live video transmission .
18. TCP and UDP Common application layer protocols
- TCP application layer :HTTP( Hypertext transfer protocol )、FTP( File transfer protocol )、SMTP( Mail transfer )
- UDP application layer :DNS、TFTP( Simple file transfer protocol )、NTP( Network time protocol )
19. HTTP Why is it stateless ?
HTTP Is based on TCP Short connection to protocol , On request - Respond to communicate . Each request is independent , It has nothing to do with last time . Even though TCP It's stateful , But its state is for transmission , For example, message serial number 、 Send auxiliary information such as window size , These and HTTP Your request doesn't matter .
Http Although there are keep-alive Field control , But that is to improve transmission efficiency , Let the life cycle of this request connection be as long as possible , Not to establish connections frequently - Destroy connection . in addition ,cookie Conversation is just HTTP A supplement to , It is allowed to close or forge , It is not the communication dependence of the Protocol .
20. Input from the browser url To the whole process of displaying web pages
First , According to the domain name DNS Parsing , To get the IP Address . Get IP After the address, it will shake hands with the server three times , establish TCP Connect . Then we will follow HTTP Request for agreement - Response to transmit web content . Last ,TCP End the connection with four waves .
21. HTTP 1.0/1.1/2.0 as well as https The difference between
HTTP 1.0
Each request - The response will be established once TCP Connect , The server will be disconnected after processing TCP Connect . I added Connection: keep-alive To delay TCP Connection time , Try to make the request - The response uses the same connection
HTTP 1.1
- Default TCP Persistent connection , No declaration required Connection Field , But the same domain name is maintained TCP There won't be too many persistent connections , commonly 6 individual ;
- Introduce pipeline mechanism , The client can use the same TCP The connection sends multiple requests at the same time , The server responds in the order of the received requests ; But this is a pseudo pipeline pattern , Because after sending multiple at the same time , The client still needs to block and wait for all responses from the server before continuing with subsequent requests .
- Added PUT、DELETE、OPTIONS Etc
HTTP 2.0
- Use binary format instead of text format
- Real pipeline mode , Non blocking waiting for all responses , Equivalent to full duplex
- The message header will be compressed and then sent
HTTPS
HTTPS It's solved HTTP Secure transmission of , stay HTTP Under this layer of agreement SSL layer . That is, end-to-end encryption / Authentication , To ensure that the data will not be stolen or tampered .
HTTPS The process is as follows :
22. ping Principle ?
ping Adopted ICMP agreement ,ICMP The agreement is used in IP host 、 Routing control messages between routers . Control message means that the network is not accessible 、 Whether the host can reach 、 Whether the route is available and so on . Although these control messages do not transmit user data , But it plays an important role in the transmission of user data .
23. What is? DOS attack ?
DOS: Denial of service , Its purpose is to make the computer or network unable to provide normal services . The most common DoS Attacks include computer network bandwidth attacks and connectivity attacks , image SYN Flood attack is also a kind of , It USES TCP The protocol sends a large number of semi connection requests , Consume server's CPU And memory resources .
Interested friends can search the official account 「 Read new technology 」, Pay attention to more push articles .
If you can , Just like it by the way 、 Leave a message 、 Under the share , Thank you for your support !
Read new technology , Read more new knowledge .
边栏推荐
- Shangtang technology crash: a script written at the time of IPO
- 逆向调试入门-PE结构-输入表输出表05/07
- JS变色的乐高积木
- MySQL statistical bill information (Part 2): data import and query
- 游戏公会在去中心化游戏中的未来
- Report on the "14th five year plan" and investment strategy recommendations for China's industrial robot industry 2022 ~ 2028
- Simple two ball loading
- Manage nodejs with NVM (downgrade the high version to the low version)
- A Fletter version of Notepad
- Apache-Atlas-2.2.0 独立编译部署
猜你喜欢

游戏公会在去中心化游戏中的未来

不同的测试技术区分

VM虚拟机配置动态ip和静态ip访问

Zabbix 6.0 源码安装以及 HA 配置

Google Earth Engine(GEE)——全球人类居住区网格数据 1975-1990-2000-2014 (P2016)

Colorful five pointed star SVG dynamic web page background JS special effect

Nexus builds NPM dependent private database

一款Flutter版的记事本

Fundamentals of number theory and its code implementation

CS5268优势替代AG9321MCQ Typec多合一扩展坞方案
随机推荐
Machine learning - performance metrics
软件测试中功能测试流程
JS变色的乐高积木
Content Audit Technology
Analysis report on the development trend and Prospect of new ceramic materials in the world and China Ⓐ 2022 ~ 2027
Tencent always takes epoll, which is annoying
Jenkins+webhooks-多分支参数化构建-
I spent tens of thousands of dollars to learn and bring goods: I earned 3 yuan in three days, and the transaction depends on the bill
Function test process in software testing
数字化转型再下一城,数字孪生厂商优锘科技宣布完成超3亿元融资
Report on the 14th five year plan and future development trend of China's integrated circuit packaging industry Ⓓ 2022 ~ 2028
Vs code set code auto save
流量管理技术
Cs5268 advantages replace ag9321mcq typec multi in one docking station scheme
Fiori 应用通过 Adaptation Project 的增强方式分享
【大型电商项目开发】性能压测-压力测试基本概念&JMeter-38
Meta enlarge again! VR new model posted on CVPR oral: read and understand voice like a human
How to count the status of network sockets?
How to play with the reading and writing operations of blocking sockets?
Investment analysis and prospect prediction report of global and Chinese dimethyl sulfoxide industry Ⓦ 2022 ~ 2028