当前位置:网站首页>Installation and configuration of grayog new generation log collection early warning system
Installation and configuration of grayog new generation log collection early warning system
2022-06-27 20:24:00 【51CTO】
In the company, I have been responsible for the construction of the monitoring system of the whole company , It mainly includes the hardware monitoring of the underlying server 、 System level monitoring 、 Monitoring of network equipment 、 Middleware and application level monitoring, etc . although Zabbix Support log monitoring , Because in the data volume 、 Search and log display are relatively weak , Only simple log alarms can be made . Therefore, log monitoring still needs to be done through professional tools . I compared it ELK、 Business log tool Splunk and Graylog, Later, I chose Graylog.Graylog Simply put, it is an open source log aggregation 、 analysis 、 Audit 、 Presentation and early warning tools . comparison ELK,Graylog A lightweight ,UI The interface is more beautiful , There are abundant and perfect API Interface . Currently, the logs of network devices are collected 、MySQL Error log 、Linux System logs, etc , We will consider accessing the microservice log later . Various logs are statistically analyzed according to the error level , By looking at Dashboards The report can confirm whether there are problems with thousands of online devices . The corresponding high-level logs pass Graylog +Python The program realizes the alarm function of wechat and e-mail .
One 、Graylog advantage
Zero development : Collect from -> Storage -> analysis -> Present the complete process .
Deployment and maintenance are simple : Integrated solutions , Unlike ELK Integration of three independent systems .
Multi day Zhiyuan access :syslog、Filebeat、Log4j、Logstash etc. .
Multi protocol access :UDP、TCP、HTTP、AMQP.
Custom panel : Provide curves 、 The pie chart 、 A rich list of graphics such as world maps .
Full text search : Support filtering and searching all logs by syntax .
Support alarm : Log analysis platform with alarm function , Currently only email is supported , Can pass API Realize wechat alarm .
Rights management : Flexible authority allocation and management .
Support clusters : The platform performance can be extended according to the application .
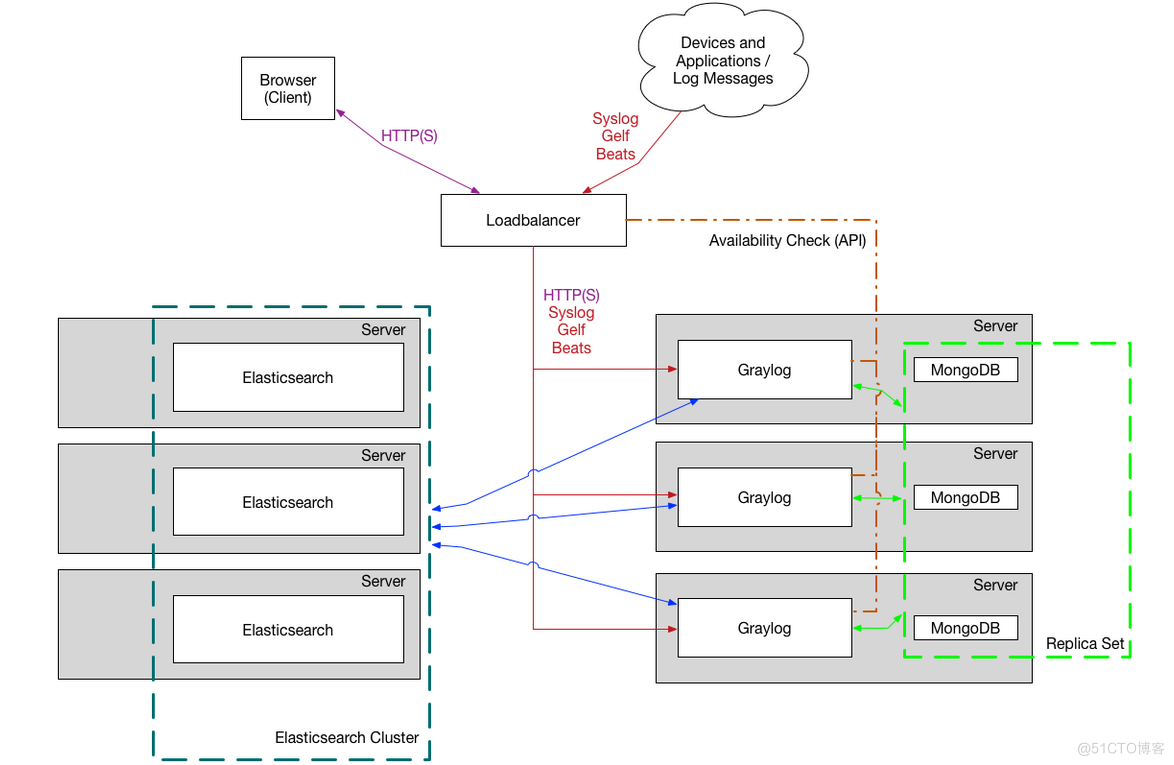
Two 、Graylog Architecture design , Support clusters
GrayLog: Provide GrayLog External interface , Belong to CPU Concentrated .
Elasticsearch: Persistent storage and retrieval of log files , Belong to IO Concentrated .
MongoDB: Store some GrayLog Configuration information .
3、 ... and 、 Installation configuration
3.1 adopt Docker install mongodb database .
3.2 adopt docker compose Mode of installation ES.
3.3 install Graylog service .
establish graylog Profile directory .
install graylog service .
Copy and edit graylog Configuration files and startup files .
start-up graylog service .
3.4 verification graylog Whether the service installation configuration is normal . adopt http://yourip:9000 To visit .

Four 、 summary
1)root_password_sha2 The password can be echo -n yourpassword | sha256sum To generate , there yourpassword Is used to log in graylog Of admin User's password . Generated root_password_sha2 Please delete the blank space and -, Otherwise, the login will not succeed .
2) edit graylog Startup file , Appoint graylog The path to the configuration file .
边栏推荐
- Bit. Store: long bear market, stable stacking products may become the main theme
- openssl客户端编程:一个不起眼的函数导致的SSL会话失败问题
- Database optimization
- Determine whether a variable is an array or an object?
- Question brushing record: easy array (continuously updated)
- UE4随笔:FString、FName 与 FText
- 429- binary tree (108. convert the ordered array into a binary search tree, 538. convert the binary search tree into an accumulation tree, 106. construct a binary tree from the middle order and post o
- 低代码开发平台是什么?为什么现在那么火?
- rust 中的结构体
- 蓄力中台,用友iuap筑牢社会级企业数智化新底座
猜你喜欢
随机推荐
【debug】平台工程接口调试
数据库锁问题
Database transactions
[help] troubleshooting of JVM's high CPU resource consumption
回溯相关问题
Golang map 并发读写问题源码分析
CSDN 技能树使用体验与产品分析(1)
Leetcode 821. 字符的最短距离(简单) - 续集
qt中文乱码
Mass lucky hash game system development - conflict resolution (code analysis)
SQL reported an unusual error, which confused the new interns
Redis集群
308. 二维区域和检索 - 可变 线段树/哈希
# Leetcode 821. 字符的最短距离(简单)
从指令交读掌握函数调用堆栈详细过程
Accumulating power in the middle stage, UFIDA IUAP builds a new base for digital intelligence of social enterprises
Data intelligence enters the "deep water area", and data governance is the key
When developing digital collections, how should cultural and Museum institutions grasp the scale of public welfare and Commerce? How to ensure the security of cultural relics data?
linux系统笑着玩Oracle数据库多表查询-连接查询
Pfsense plus22.01 Chinese customized version release