当前位置:网站首页>Game Security 03: A Simple Explanation of Buffer Overflow Attacks
Game Security 03: A Simple Explanation of Buffer Overflow Attacks
2022-08-01 01:20:00 【Xie Baiyu】
文章目录
一、concrete example
void add()
{
}
int32_t verify(const char* password)
{
add();
}
int main()
{
char password[1024];
int valid;
while(1)
{
scanf("%s",password);
valid = veryfy(password)
if(valid)
{
}
else
{
}
}
}
假设密码设置为1234567,When the incoming string length is greater thanstrlen (1234567)时,will return a result that successfully matches the password(比如传入8个8:)
二、缓冲区Overflow attack principle
备注:
Buffers can be either stack or heap危害
Data with excess buffer length may overwrite data in other areas(内存越界)
(1)stack frame basics
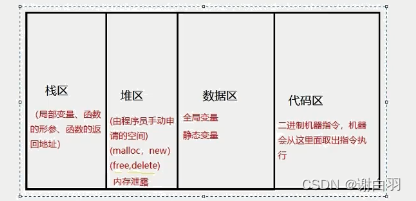

1)栈区(stack):由编译器自动分配与释放,Stored as runtime function
allocated local variables、函数参数、返回数据、返回地址等.its operation class
似于数据结构中的栈.
2)堆区(heap):一般由程序员自动分配,If the programmer does not explain
放,程序结束时可能有OS回收.其分配类似于链表.
3)全局区(静态区static):数据段,程序结束后由系统释放.全
The local area is divided into the initialized global area(data),Used to store save global and static
initialized variables and uninitialized global area(bss),Used to save global peace
state uninitialized variable.
4)常量区(文字常量区):数据段,存放常量字符串,程序结束
after system release.
5)代码区:存放函数体(类成员函数和全局区)的二进制代码,
This segment in memory in general is marked as read-only,Any write to this area will result in
segfault(Segmentation Fault).
- 栈的特点:
先进后出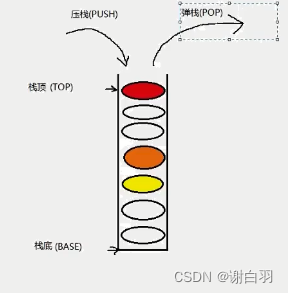
- 基础知识
1)用OD查看堆栈
register transfer gate(A little bit of assembly knowledge I summed up)
ESP :栈指针,指向栈顶
EBP :帧指针,Point to the bottom of the current activity(若在add函数里面,就只想add和verifythe former border)
EIP:指令寄存器:执行指令的地址(EIPis the execution flow of the program)
函数:调用的时候,The system will open up a stack frame for this function(函数作用域)
系统栈:The stack of the entire program call

Each cell is a stack frame for a specific function
(2)函数调用约定
//What is the order in which function parameters are pushed onto the stack??a,b,c,d
int test(int a,int b, int c, int d)
{
return a + b + c + d ;
}
int main()
{
int a = 10;
printf("%d ,%d,%d,%d",a =a +1,a = a+ 1,a= a+1,a=a + 1);
}
//打印结果是14 13 12 11(栈的先进后出)
(3)Overflow attack principle
当程序写入超过缓冲区的边界时,就会产生所谓的“缓冲区溢出”.发生缓冲区溢出时,就会覆盖下一个相邻的内存块(Overwrite the stack frame of adjacent functions),导致程序发生一些不可预料的结果:也许程序可以继续,也许程序的执行出现奇怪现象,也许程序完全失败或者崩溃等.
(4)Buffer overflow attack classification and examples
栈溢出、堆溢出、BSSOverflow and formatted string overflow.其中,stack overflow is the easiest,It is also the most common type of overflow..
1)没有保证足够的存储空间存储复制过来的数据
void function(char *str)
{
char buffer[10];
strcpy(buffer,str);
}
上面的strcpy()将直接把str中的内容copy到buffer中.这样只要str的长度大于 10 ,就会造成buffer的溢出,使程序运行出错.existential imagestrcpyStandard functions for such problems are alsostrcat(),sprintf(),vsprintf(),gets(),scanf()等.对应的有更加安全的函数,即在函数名后加上_s,如scanf_s()函数.
2)整数溢出
(1)整数溢出
把一个宽度较大的操作数赋给宽度较小的操作数,就有可能发生数据截断或符号位丢失
#include<stdio.h>
int main()
{
signed int value1 = 10;
usigned int value2 = (unsigned int)value1;
}
(1)算术溢出
该程序即使在接受用户输入的时候对a、b的赋值做安全性检查,a+b依旧可能溢出:
#include<stdio.h>
int main()
{
int a;
int b;
int c=a*b;
return 0;
}
3)数组索引不在合法范围内
enum {TABLESIZE = 100};
int *table = NULL;
int insert_in_table(int pos, int value) {
if(!table) {
table = (int *)malloc(sizeof(int) *TABLESIZE);
}
if(pos >= TABLESIZE) {
return -1;
}
table[pos] = value;
return 0;
}
其中:pos为int类型,可能为负数,This results in writes outside the bounds of the memory referenced by the array,可以将pos类型改为size_t避免
4)空字符错误
//错误
char array[]={
'0','1','2','3','4','5','6','7','8'};
//正确的写法应为:
char array[]={
'0','1','2','3','4','5','6','7','8',’\0’};
//或者
char array[11]={
'0','1','2','3','4','5','6','7','8','9’};
边栏推荐
猜你喜欢
【元胞自动机】基于matlab界面聚合元胞自动机模拟【含Matlab源码 2004期】

STK8321 I2C (Shengjia-accelerometer) example
YOLO怎么入门?怎么实现自己的训练集?

元宇宙改变人类工作模式的四种方式

Unity3D学习笔记10——纹理数组

Google engineer fired for claiming AI awareness: breach of nondisclosure agreement

MYSQL关键字Explain解析
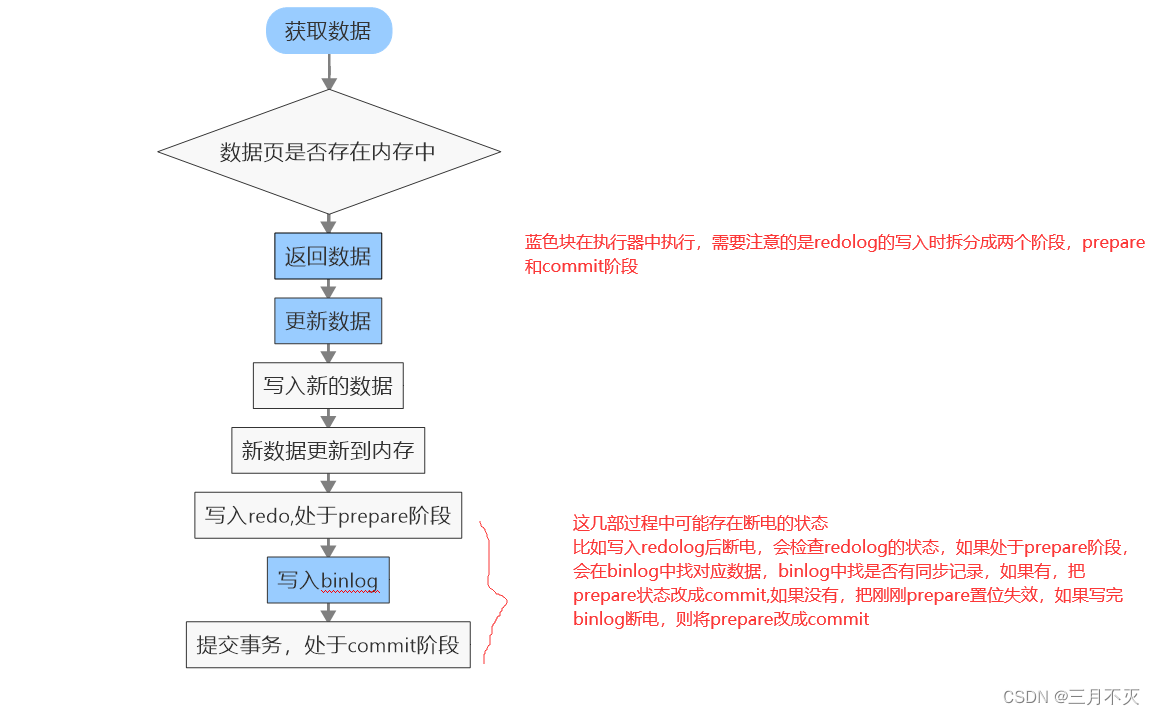
MYSQL two-phase commit

如何编辑epub电子书的目录
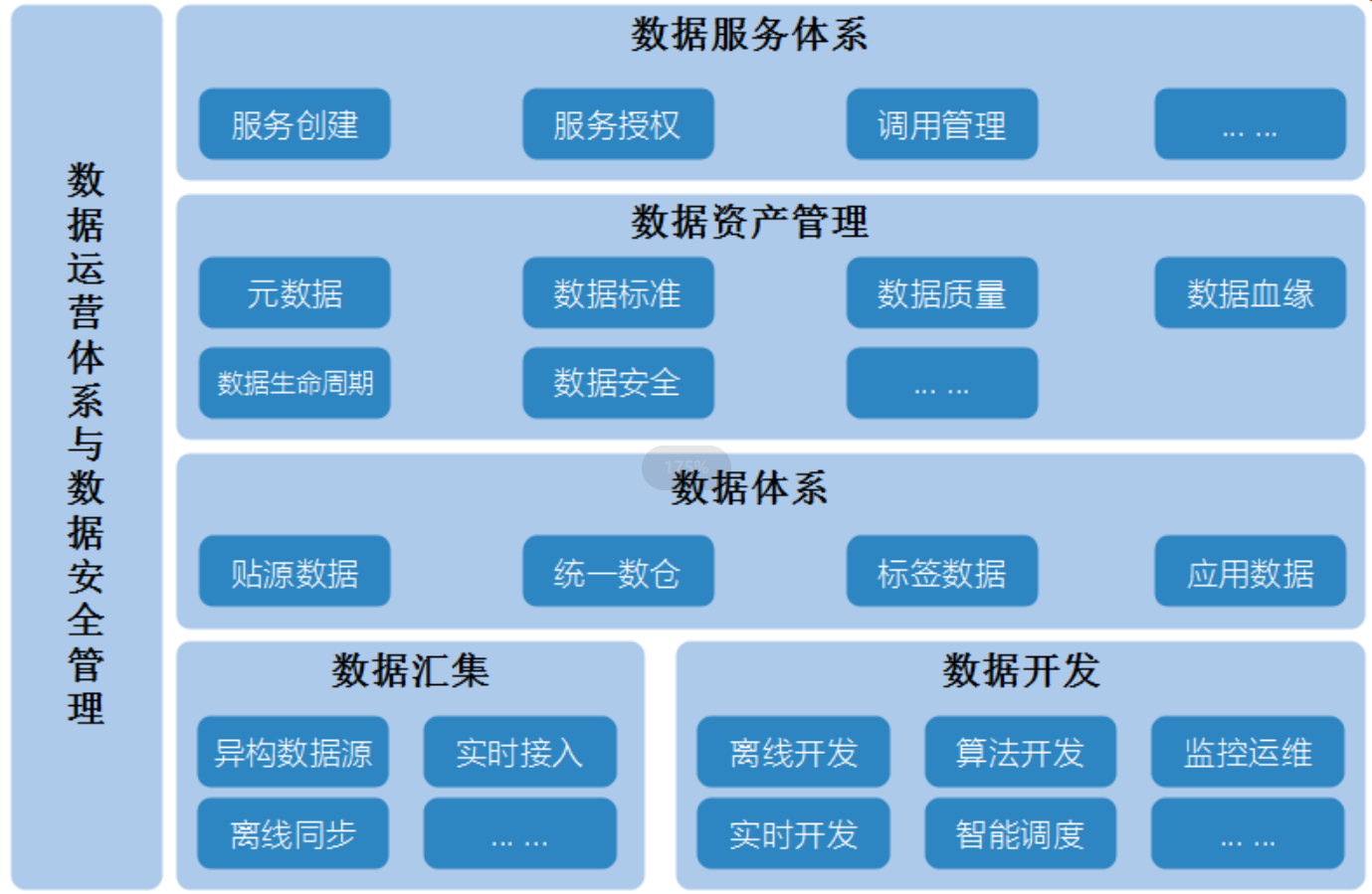
Data Middle Office Construction (VII): Data Asset Management
随机推荐
ROS2 series of knowledge (4): understand the concept of [service]
leetcode:1562. 查找大小为 M 的最新分组【模拟 + 端点记录 + 范围合并】
Rasa 3.x 学习系列-使用查找表改进实体提取
OSD read SAP CRM One Order application log way of optimization
Detailed explanation of TCP protocol
IDEA无法识别module(module右下角没有蓝色小方块)
Super like the keyboard made from zero, IT people love it
Nmap 操作手册 - 完整版
微信小程序之小程序页面语法
TCP协议详解
考研备考方案
How to get started with YOLO?How to implement your own training set?
JQESAP系统里的胖接口Fat interface
An open source and easy-to-use flowchart drawing tool drawio
MYSQL逻辑架构
Rasa 3.x Study Series - Rasa - Issues 4918 Study Notes
YOLO怎么入门?怎么实现自己的训练集?
ECCV2022 Workshop | Multi-Object Tracking and Segmentation in Complex Environments
Introduction to machine learning how to?
GDB 源码分析系列文章五:动态库延迟断点实现机制