当前位置:网站首页>[oauth2] v. oauth2loginauthenticationfilter
[oauth2] v. oauth2loginauthenticationfilter
2022-07-26 13:29:00 【Beicheng Xiaolin】
One 、OAuth2LoginAuthenticationFilter
When gitee received OAuth2 After the authorization request , Will send a message to the browser 302 Redirect to redirect_uri Response . Because by default, the callback path satisfies /login/oauth2/code/*, The path will be OAuth2LoginAuthenticationFilter Filter interception processing .
Two 、OAuth2LoginAuthenticationFilter Structure

1、 DEFAULT_FILTER_PROCESSES_URI = “/login/oauth2/code/*”;
Default intercept path
2、 ClientRegistrationRepository
Client information
3、OAuth2AuthorizedClientRepository ;
OAuth2 Authorize client repositories
4、AuthorizationRequestRepository authorizationRequestRepository
from http Operation authorized in OAuth2 client
5、 Converter<OAuth2LoginAuthenticationToken, OAuth2AuthenticationToken> authenticationResultConverter
token converter
3、 ... and 、OAuth2 Login authentication logic
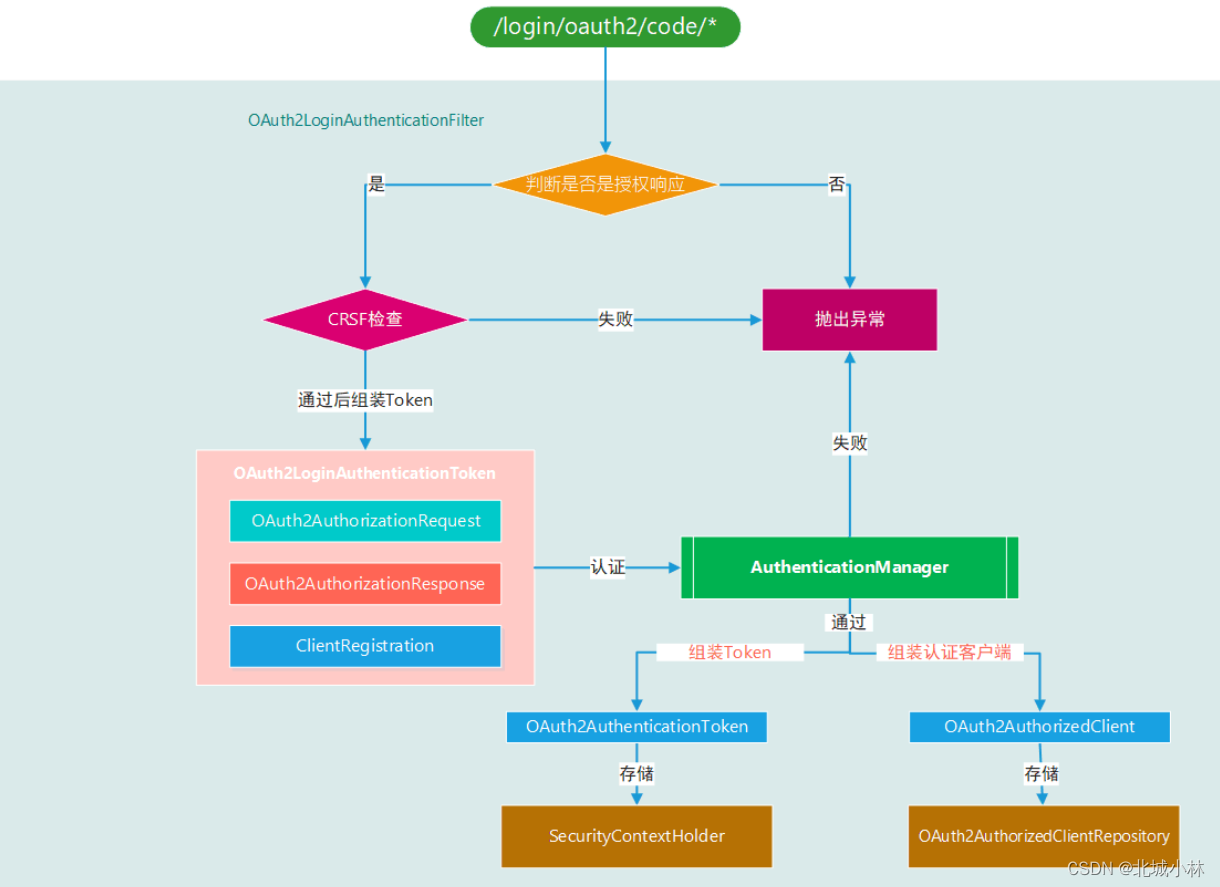
OAuth2LoginAuthenticationFilter The core of all 
In the method . It mainly implements the following logic :
- Check logic
- Verify whether it is a response to the authorization request .
- Verify whether the current authorization request really exists , Prevent forgery .
- Verify the of the current authorization request OAuth2 Whether the client is compliant .
- assemble OAuth2LoginAuthenticationToken And to OAuth2LoginAuthenticationProvider Processing authentication
- Certified OAuth2LoginAuthenticationToken adopt authenticationResultConverter Function to OAuth2AuthenticationToken
- Initialize authenticated OAuth2 Client object OAuth2AuthorizedClient And persist
- Will step ③ Generated OAuth2AuthenticationToken return

Four 、OAuth2LoginAuthenticationProvider
1、springsecurity Our certification system

2 、AuthenticationProvider
spring Supported by default in 17 Authentication method in 
3、OAuth2LoginAuthenticationToken Corresponding AuthenticationProvider
OAuth2LoginAuthenticationProvider,For ordinary OAuth2 Login authentication .OidcAuthorizationCodeAuthenticationProvider, be used for OIDC authentication .
4、OAuth2LoginAuthenticationProvider
OAuth2LoginAuthenticationProvider Responsible for using the token endpoint of the authorization server (token-uri) Authenticate the authorization code credentials , If the certification is valid , Then exchange it as access token credentials OAuth2AccessToken.
It will also use OAuth2UserService From the user information endpoint (user-info-uri) Get end users ( Resource owner ) User information for , User information to OAuth2User Create a Principal . And then OAuth2User Related to OAuth2LoginAuthenticationToken To complete authentication . The flow chart is as follows :
From the above description and flow chart, we can summarize the following two key points :
5、 ... and 、OAuth2AuthorizationCodeAuthenticationProvider
OAuth2LoginAuthenticationProvider There is also a OAuth2AuthorizationCodeAuthenticationProvider. It is responsible for using the token endpoint of the authorization server to authenticate the authorization code credentials .
- Authentication authorization code
First of all, from the OAuth2AuthorizationCodeAuthenticationToken Medium OAuth2AuthorizationExchange extract OAuth2AuthorizationResponse, Judge whether it is OAuth2 Abnormal response .
If not , And authorization request object OAuth2AuthorizationRequest Medium state Value for consistency comparison , once OAuth2 Before and after authorization request state Must be consistent .
obtain OAuth2AccessToken
And then through OAuth2AccessTokenResponseClient, The bottom one is RestTemplate, according to OAuth2 Of token-uri Just encapsulate . Wechat in the back OAuth2 We will customize this interface in Web authorization .obtain OAuth2User
Get OAuth2AccessToken Jump back OAuth2LoginAuthenticationProvider. With token Naturally, you can call the personal information interface user-info-uri 了 ,Spring Security Abstract this process as OAuth2UserService Interface :‘
Many times, the bottom layer of this interface also passes RestTemplate Realized . And in actual development OAuth2UserService The probability should be customized , Also behind wechat OAuth2 We will customize this interface in Web authorization .
Extra logic
OAuth2LoginAuthenticationProvider This is the end of the implementation , What we deal with later is AbstractAuthenticationProcessingFilter The logic of , and Form Login The logical process is consistent = What needs to be emphasized is that it has been certified OAuth2 The client object will be stored , Currently certified OAuth2AuthenticationToken Will be stored in the security context SecurityContext in .
边栏推荐
- LeetCode 217. 存在重复元素
- [flower carving hands-on] fun music visualization series small project (12) -- meter tube fast rhythm light
- The parent component accesses the methods or parameters of the child component (the child component exposes the method defineexpose)
- JSON数据传递参数&日期型参数传递
- Win11+vs2019 configuration yolox
- Some practical operations of vector
- 【花雕动手做】有趣好玩的音乐可视化系列小项目(13)---有机棒立柱灯
- Unicode file parsing methods and existing problems
- With 8 years of product experience, I have summarized these practical experience of continuous and efficient research and development
- 重押海外:阿里、京东、顺丰再拼“内力”
猜你喜欢

时间复杂度和空间复杂度

一笔画问题(中国邮递员问题)

飞盘,2022年“黑红”顶流

Can I take your subdomain? Exploring Same-Site Attacks in the Modern Web

Oom caused by improper use of multithreading
AI theory knowledge map 1 Foundation

AI-理论-知识图谱1-基础

力扣------字符串中的单词数

Learn about Pinia state getters actions plugins

El table implements editable table
随机推荐
Click El dropdown item/@click.native
Detailed relation extraction model casrel
[turn] judge the relationship between two geometries in ArcGIS
Parent class reference to child class (parent class reference points to child class object)
Tianjin emergency response Bureau and central enterprises in Tianjin signed an agreement to deepen the construction of emergency linkage mechanism
Sword finger offer (VII): Fibonacci sequence
【花雕动手做】有趣好玩的音乐可视化系列小项目(12)---米管快速节奏灯
Dimension disaster dimension disaster suspense
A college archives management system based on asp.net
PostgreSQL official website download error
Multi objective optimization series 1 --- explanation of non dominated sorting function of NSGA2
终极套娃 2.0 | 云原生交付的封装
B+ tree (3) clustered index, secondary index -- MySQL from entry to proficiency (XV)
JSON data transfer parameters & date type parameter transfer
Time complexity analysis of bubble sorting
【OAuth2】八、OAuth2登录的配置逻辑-OAuth2LoginConfigurer和OAuth2ClientConfigurer
Leetcode 217. there are duplicate elements
Algorithm -- continuous sequence (kotlin)
B+ tree selection index (1) -- MySQL from entry to proficiency (22)
Activity.onStop() 延迟10秒?精彩绝伦的排查历程