stay 6 month 10 Held by the Institute of information technology in Japan “ Safe operation development forum ” On ,
Sinomeni and the Academy of communications jointly released the first in China 《 Host security capacity building guide 》
. At the meeting , Ivy COO This guide has been interpreted in detail .

Scan the QR code to download the complete report
One 、 Host safety critical capability analysis
As attacks evolve , The host security protection technology is also continuously updated , A series of host security products with different sub categories have been derived , Its security capability is based on maturity and matching user requirements , It can be divided into three levels : Basic level 、 Enhanced and advanced .

chart 1: Different levels of host security capabilities
1、 Basic level : Four abilities
Major enterprises building basic level host security capabilities , The number of hosts is generally less than 1000 platform , The number of the security team is 1-5 Between people , The annual host security budget is 20 ten thousand —100 Ten thousand yuan between . Such enterprises need to use a limited budget to build the most basic 、 The most important security capability , To solve most of the security problems , It mainly includes asset inventory 、 Risk discovery 、 Intrusion detection 、 Compliance baseline, etc .

chart 2: Basic level host security capability
Asset count :
You can't protect assets you can't see . All threat and vulnerability operations need to rely on assets . To further improve the management efficiency of large-scale cluster hosts , Need to improve automation , Reduce human intervention .

chart 3: Value of items and usage scenarios for asset inventory
Risk discovery :
The ability of risk discovery can enable security managers to reinforce the system before an attack occurs , Risk reduction points exist .

chart 4: Use case value of risk discovery
Intrusion detection :
Host intrusion detection refers to the ability to identify the intrusion events that occur in the host and analyze its intrusion signs , Help security personnel monitor and analyze the intrusion process , It mainly includes two methods : Misuse detection system ( Knowledge based detection ) And anomaly detection system ( Behavior based detection ).

chart 5: Attacker intrusion path and intrusion detection value
Compliance baseline :
Compliance is the basic principle of enterprise security protection . If the baseline management and system reinforcement of the enterprise are insufficient , It is difficult to respond quickly and control the situation in case of emergency .

chart 6: Three challenges and solutions of compliance baseline
2、 Enhanced : Four abilities
Build a major enterprise to enhance the security capability of the first-class host , The number of hosts is generally in 1000 platform —6000 Between the tables , The security team is in 5—10 Between people , The annual host security budget is 100 ten thousand —5000 Ten thousand yuan between . This kind of enterprise business is more complex , Vulnerable to advanced attacks , Therefore, in addition to the basic level safety capability , You also need to have the ability to detect and kill viruses 、 Document integrity monitoring and control 、 Memory horse detection 、 Enhanced security capabilities such as host honeypots .

chart 7: Enhance the level host security capability
Virus killing :
Virus detection and killing assume the security role of the host entrance , Prevent malicious programs from entering . One side , It takes less time and money to detect and prevent viruses in advance than to repair them afterwards ; On the other hand , From a business perspective , The virus may cause the personal data of customers to be leaked or spread through phishing emails , It is difficult to make up for the loss of corporate reputation .

chart 8: The process of virus detection and killing
Document integrity :
File integrity capability is crucial to ensure the security and compliance of enterprise information systems , It can help enterprises monitor key system files 、 Directory etc. , To detect any unauthorized changes .

chart 9: Basic requirements for document integrity
Memory horse detection :
In order to improve the behavior privacy and bypass the possibility of application rule detection , File free attacks based on macros and scripts can achieve the above goals , Become a trend , Memory horse attack is a common type of file free attack , The two most common methods are memory Webshell And memory malicious code , The corresponding detection capability is very necessary .

chart 10: Memory horse detection capability requirements
Host honeypot :
The host honeypot hosts by arranging decoys 、 Network service or file , Entice the attacker to attack the bait , So as to capture and analyze the attack behavior , Understand the tools and methods used by the attacker , Speculate on the intention and motive of the attack .
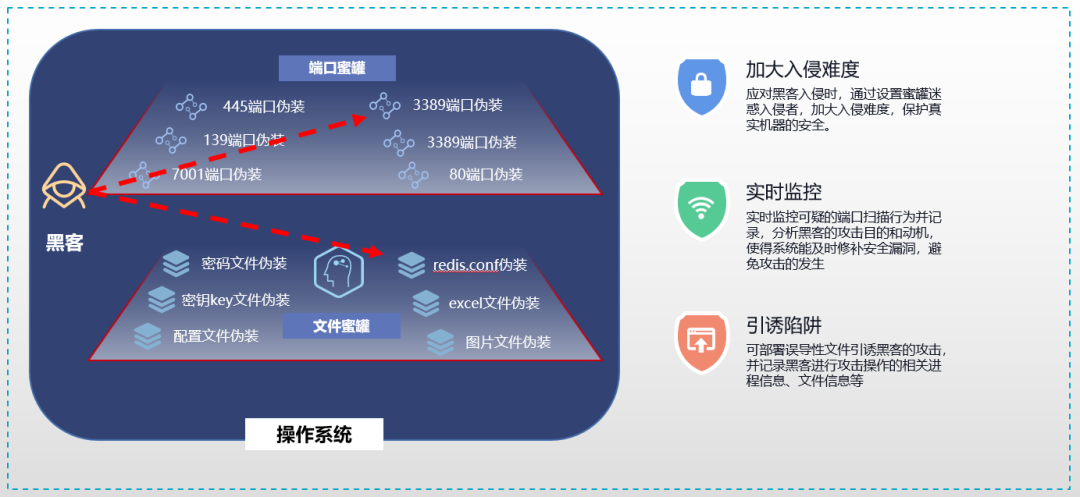
chart 11: The use scenario value of the host honeypot
3、 Advanced level : Three abilities
Major enterprises building advanced mainframe security capabilities , The number of hosts is generally in 6000 Table above , The security team is in 10 More people , The annual host security budget is 500 More than ten thousand yuan . Such enterprises have high business value , Complex business relationships , Very attractive to attackers , Vulnerable to attacks from hostile groups 、 Malicious attacks launched by threat organizations with rich resources . So , Enterprises need to have more advanced host security capabilities , Including supply chain security 、 Micro isolation and threat hunting .

chart 12: Advanced host security capability
Supply chain security :
When the enterprise network security capability is strong , Attackers tend to turn their attention to suppliers , Suppliers are becoming the weakest link in the supply chain , Strengthening the security capability of supply chain has become an inevitable choice for enterprises .
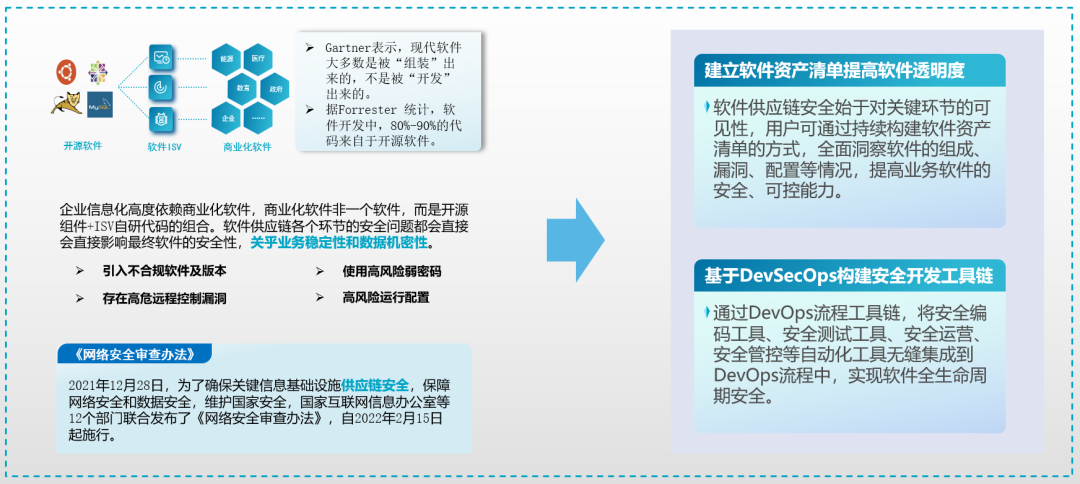
chart 13: Governance of supply chain security
Micro isolation :
Enterprise digital transformation , The cloud in business leads to the disappearance of traditional boundaries . The traditional firewall is only effective for north-south traffic , The east-west direction cannot be controlled . Once the attack penetrates the border , Lack of credit mechanism for access between intranets . Micro isolation architecture can provide protection against east-west traffic , Meet the development needs of the industry .

chart 14: Four requirements for micro isolation
Threatening to hunt :
Threat hunting is an active 、 Hypothesis driven threat discovery activities , It can help enterprises find controls that are not covered by the passive monitoring function 、 Activities or attackers TTP.

chart 15: Threat hunting process
Two 、 Analysis of host security capability requirements in key industries
In the actual operation of the enterprise , The driving factors for safety construction in different industries are different , And there are differences in the degree of risk faced by the business relationship , Comprehensive construction cost 、 Talents, technical foundation and other factors , Enterprises have different priorities for the security capacity-building of each host , Should be in manpower 、 With limited financial resources , Give priority to the most urgent needs 、 Capacity building that best matches business security requirements .
The following figure shows the demand priorities of different industries for the security capabilities of each host .
More details , Please scan the above QR code , Download the full report .

chart 16: The priority of different industries' requirements for host security capabilities
3、 ... and 、 Host security construction process
When enterprises build host security capabilities based on the host security platform , There are two problems , First, the host security product is a relatively new product category , Especially based on Agent Product form of the mode , Many enterprises are not familiar with it , It will take some time to take full advantage of these systems ; Second, the enterprise has its own unique needs , Different departments in a single enterprise may also have their own special needs , Such as security department and operation and maintenance department , Requirements need to be prioritized . therefore , When enterprises are building host security capability , It needs to combine the needs of the industry and enterprises , Specify the host security capabilities required by the platform , At the same time, it is also necessary to comprehensively consider the overall performance of the platform . When evaluating the capabilities of the host security platform , It mainly includes the following aspects :

chart 17: Evaluation elements of host security platform capability
besides , Enterprises are building host security capabilities , When it is necessary to purchase the host security products , Qualification evaluation also needs to be considered 、 Cost evaluation and contract signing .
Four 、 summary
In the whole safety protection system , The host hosts the core business and data of the enterprise , Is the favorite target of attackers , It is also the last active position of the attacker . Guard the last mile of safety , Host security becomes key . But in terms of host security construction , Different industries 、 Enterprises at different stages of development need different emphasis on safety capabilities . One side , Enterprises should combine the needs of industries and enterprises , Specify the host security capabilities required by the platform , On the other hand, it is also necessary to comprehensively consider the overall performance of the platform , And comprehensively consider the qualification evaluation 、 Cost assessment 、 Contract signing and other factors .《 Host security capacity building guide 》 By analyzing the development trend and key technical requirements , Sort out the demand priorities and key points in the construction of host security capacity in key industries , The main engine safety construction process and evaluation elements are defined , It can help enterprises choose products that meet their needs , Build an efficient host security capability system .
For details , Click the link to download the full report !
《 Host security capacity building guide 》
原网站版权声明
本文为[InfoQ]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/164/202206131059169708.html


















![[tcapulusdb knowledge base] tcapulusdb tmonitor module architecture introduction](/img/fb/effd0732d85819d7fe50c4fadef977.png)


![[tcapulusdb knowledge base] tcapulusdb cluster management introduction](/img/c1/62276c344ded6c260070f0d60bce81.png)





