当前位置:网站首页>Detailed explanation of switch link aggregation [Huawei ENSP]
Detailed explanation of switch link aggregation [Huawei ENSP]
2022-07-24 13:45:00 【Hua Weiyun】
@[toc]
One . Preface
This note records link aggregation , The content is relatively simple , There are only a few simple commands .
demand :
6、 Link aggregation is needed between two convergence layer switches to increase bandwidth , Considering the security of the two-layer network and the occupation of network resources, it is necessary to realize the two-layer isolation between different departments .
Manual link aggregation : Increase bandwidth , Link backup
Make sure it's reliable , Increase bandwidth
Be careful :1. The interfaces at both ends must be consistent
2. No configuration is allowed under the interface
Two . Experimental process
Let's get two new switches first , Here's the picture : The link ensures that the ports on both ends are consistent .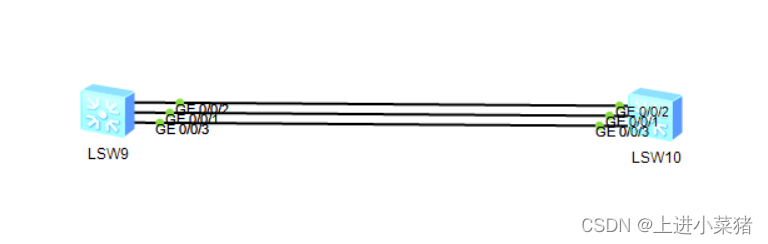
Get into SLW9:
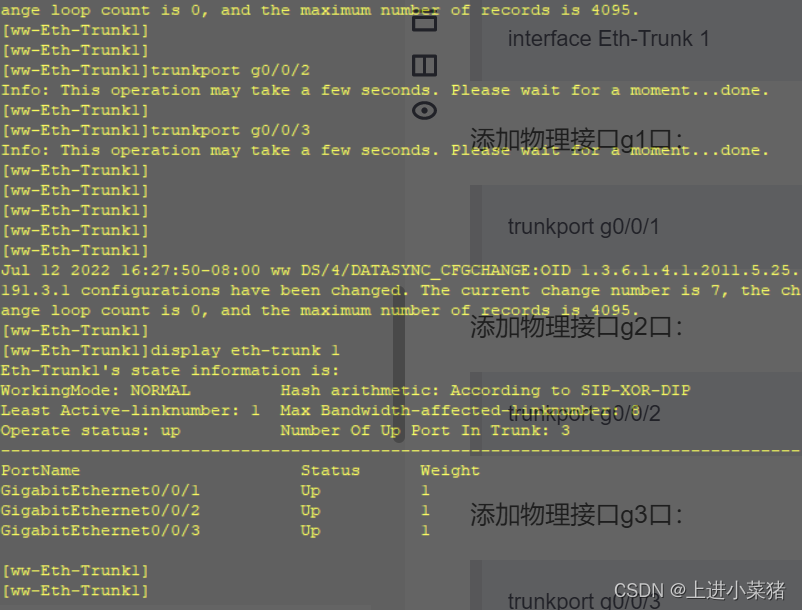
Create logical interface group
interface Eth-Trunk 1
Add physical interface g1 mouth :
trunkport g0/0/1
Add physical interface g2 mouth :
trunkport g0/0/2
Add physical interface g3 mouth :
trunkport g0/0/3
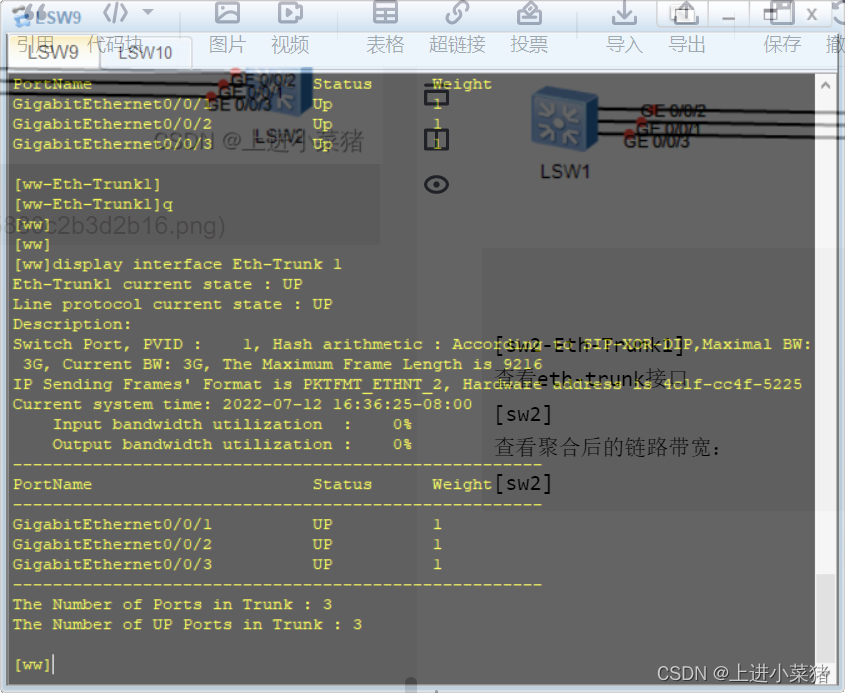
Check it out. eth-trunk Interface :
display eth-trunk 1
Get into SLW10:
Repeat the above steps .
It is mainly necessary to ensure that the interface corresponds . The configuration is as follows 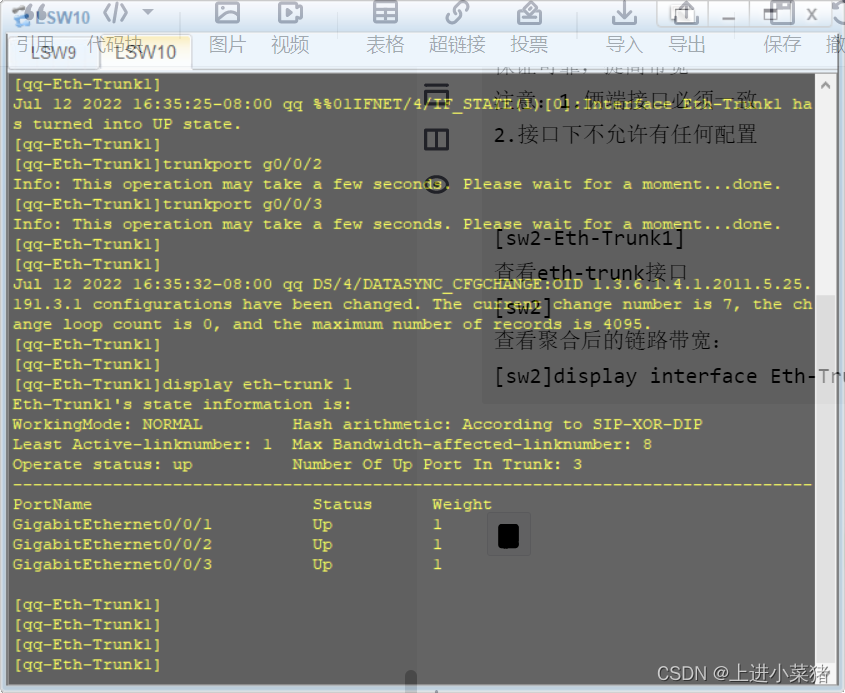
View the aggregated link bandwidth :3G
display interface Eth-Trunk 1
PS: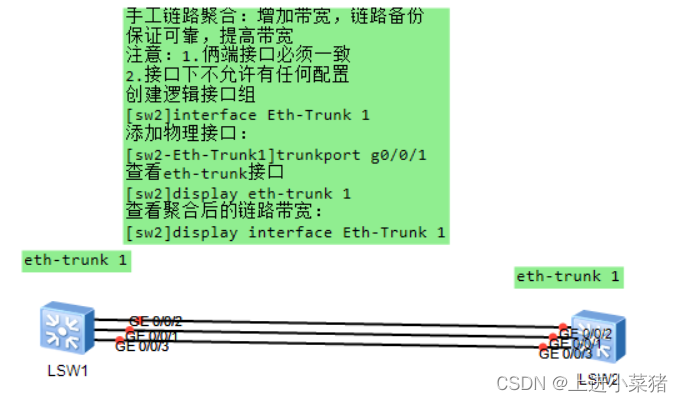
Configure command shortcut :
interface Eth-Trunk 1trunkport g0/0/1trunkport g0/0/2trunkport g0/0/3see eth-trunk Interface :
display eth-trunk 1View the aggregated link bandwidth :3G
display interface Eth-Trunk 1边栏推荐
猜你喜欢

JS execution mechanism

Network security - error injection

脑注意力机制启发的群体智能协同避障方法

Simple order management system small exercise

网络安全——Web信息收集

网络安全——文件上传白名单绕过
Network security - filtering bypass injection

网络安全——文件上传黑名单绕过

Network security - use exchange SSRF vulnerabilities in combination with NTLM trunking for penetration testing

Icml2022 | branch reinforcement learning
随机推荐
Aike AI frontier promotion (7.24)
简易订单管理系统小练习
Flink综合案例(九)
Group intelligence decision-making in an open environment: concepts, challenges and leading technologies
Network security - file upload whitelist bypass
R language uses the tablestack function of epidisplay package to make statistical summary tables (descriptive statistics based on the grouping of target variables, hypothesis testing, etc.), set the b
Wildcard (Pan domain name) SSL certificate
CSDN垃圾的没有底线!
Data type binary string type
Adjust the array order so that odd numbers precede even numbers
Paper notes: swing UNET: UNET like pure transformer for medicalimage segmentation
基于图正则化的贝叶斯宽度学习系统
Flink高级特性和新特性(八)v2
Interview question 01.02. determine whether it is character rearrangement
R language uses the statstack function of epidisplay package to view the statistics (mean, median, etc.) of continuous variables and the corresponding hypothesis test in a hierarchical manner based on
支持鹏程系列开源大模型应用生态演化的可持续学习能力探索
OWASP ZAP安全测试工具使用教程(高级)
The R language uses the sort function to sort vector data and return the actually sorted data (ascending by default)
SQL Server 启停作业脚本
网络安全——过滤绕过注入