当前位置:网站首页>Redis master-slave replication, sentinel mode, cluster cluster
Redis master-slave replication, sentinel mode, cluster cluster
2022-06-27 13:54:00 【No such person found 0330】
One 、Redis Master slave copy
1、 Introduction to master-slave replication
Master slave copy , It means to put one Redis Server data , Copy to other Redis The server . The former is called the main node (Master), The latter is called the slave node (Slave); Data replication is one-way , From master to slave only .
By default , Each station Redis Servers are all primary nodes ; And a master node can have multiple slave nodes ( Or no slave ), But a slave node can only have one master node .
2、 The role of master-slave replication
- data redundancy : Master-slave replication realizes hot backup of data , It's a way of data redundancy beyond persistence .
- Fault recovery : When there is a problem with the master node , Can be served by a slave node , Fast fault recovery ; It's actually a redundancy of services .
- Load balancing : On the basis of master-slave replication , Cooperate with the separation of reading and writing , Write service can be provided by the master node , Read service provided by slave node ( The write Redis Connect master node when data is applied , read Redis Apply connection from node when data ), Share server load ; Especially in the situation of less writing and more reading , Sharing read load through multiple slave nodes , Can be greatly improved Redis Concurrency of servers .
- High availability cornerstone : In addition to the above functions , Master slave replication is also the foundation for sentinels and clusters to implement , So master-slave replication is Redis High availability Foundation .
3、 Master slave replication process :
(1) If you start a slave Machine processes , Then it will go to Master The machine sends a message “sync command” command , Request synchronous connection .
(2) Whether it's the first connection or reconnection ,Master The machine will start a background process , Save data snapshot to data file ( perform rdb operation ), meanwhile Master All commands to modify data are also recorded and cached in the data file .
(3) After the background process completes the cache operation ,Master The machine will turn to slave The machine sends data files ,slave The end machine saves the data file to the hard disk , Then load it into memory , next Master The machine will send all operations to modify the data to Slave End machine . if Slave Failure causes downtime , It will automatically reconnect after returning to normal .
(4)Master The machine received slave After the connection of the end machine , Send its complete data file to slave End machine , If Mater Receive multiple at the same time slave Synchronization request from , be Master A process will be started in the background to save the data file , Then send it to all slave End machine , Ensure that all slave The end machine is normal .
4、 build redis Master slave copy
master 192.168.52.140
slave1 192.168.52.130
slave2 192.168.52.120
4.1 All servers are set up redis database
Turn off firewall
systemctl stop firewalld
setenforce 0
# Install dependent environment
yum install -y gcc gcc-c++ make
# Unzip the file to the specified folder opt
tar zxvf redis-5.0.7.tar.gz -C /opt/
cd /opt/redis-5.0.7/
# install
make
make PREFIX=/usr/local/redis install
# Execute the... Provided by the software package install_server.sh Script files , Set up Redis Relevant configuration files required by the service
cd /opt/redis-5.0.7/utils
./install_server.sh
……
Enter slowly
Please select the redis executable path []
Manual input
/usr/local/redis/bin/redis-server
# Create soft link
ln -s /usr/local/redis/bin/* /usr/local/bin/
/etc/init.d/redis_6379 stop # stop it
/etc/init.d/redis_6379 start # start-up
/etc/init.d/redis_6379 restart # restart
/etc/init.d/redis_6379 status
# restart redis service
/etc/init.d/redis_6379 restartTurn off the firewall and download the dependent environment

Unzip package

compile

Install to specified directory

Execute the script file provided by the software package

Make soft links
![]()
start-up redis Service and view

Restart the service

4.2 modify Redis The configuration file (Master Node operation )
vim /etc/redis/6379.conf
bind 0.0.0.0 #70 That's ok , Change the listening address to 0.0.0.0
daemontze yes #137 That's ok , Start Daemons
logfile/var/log/redis_6379.1og #172 That's ok , Specify the log file directory
dir/var/lib/redis/6379 #264 That's ok , assign work directory
appendonly yes #700 That's ok , Turn on AOF Persistence function
/etc/init.d/redis_6379 restart





4.3 modify Redis The configuration file (slave Node operation )
vim /etc/redis/6379.conf
bind 0.0.0.0 #70 That's ok , Change the listening address to 0.0.0.0
daemonize yes #137 That's ok , Start Daemons
logfile/var/log/redis 6379.1og #172 That's ok , Specify the log file directory
dir/var/lib/redis/6379 #264 That's ok , assign work directory
replicaof 192.168.52.140 6379#288 That's ok , Specify the to synchronize Master node IP And port
appendonly yes #700 That's ok , Turn on AOF Persistence function
/etc/init.d/redis_6379 restart
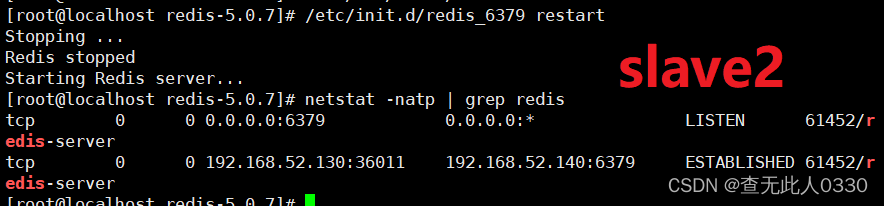
netstat -natp | grep redis
slave Node configuration and master Nodes are similar to scp Modify the command after remote transmission
scp /etc/redis/6379.conf 192.168.52.130:/etc/redis
scp /etc/redis/6379.conf 192.168.52.120:/etc/redis

Enter two slave Modify the server
vim /etc/redis/6379.conf
replicaof 192.168.52.140 6379#288 That's ok , Specify the to synchronize Master node IP And port
/etc/init.d/redis_6379 restart
netstat -natp | grep redis Check whether the master and slave servers are connected


4.4 Verify the master-slave effect
stay Master View the log on the node
tail /var/log/redis_6379.log
Replica 192.168.239.20:6379 asks for synchronization
Replica 192.168.239.30:6379 asks for synchronization

stay Master Verify the slave node on the node
redis-cli info replication

stay master Add data to the node View from the node



Two 、Redis Sentinel mode
The method of master-slave switching technology is : When the server goes down , You need to manually switch from a slave to a host , This requires human intervention , It not only takes time and effort, but also makes the service unavailable for a period of time . In order to solve the disadvantage of master-slave replication , There is a sentinel mechanism .
The core function of the sentry : On the basis of master-slave replication , Sentinel introduces automatic failover of the primary node .
1、 The role of sentinel mode
- monitor : The Sentry will constantly check whether the master and slave nodes are working properly .
- Automatic failover : When the master node is not working properly , Sentinels will start automatic failover operations , It will upgrade one of the failed master nodes from a node to a new master , And make the other slave nodes copy the new master node .
- notice ( remind ): Sentinels can send failover results to clients .
2、 The sentry structure consists of two parts , Sentinel nodes and data nodes
- The sentinel node : The sentinel system consists of one or more sentinel nodes , Sentinel nodes are special redis node , Don't store data , The number of sets must be greater than or equal to 3 Odd number .
- Data nodes : Both master and slave nodes are data nodes .

3、 Failover mechanism
The sentinel node regularly monitors and finds out whether the primary node has failed
Every sentinel node every 1 Seconds to the master node 、 Send once from node and other sentinel nodes ping Command to do a heartbeat test . If the master node does not reply within a certain time range or replies to an error message , Then the sentinel will think that the master node is offline ( One sided ). When more than half of the sentinel nodes think that the master node is offline , In this way, the objective offline .. When the master node fails , The sentinel node will pass through Raft Algorithm ( Election algorithm ) Realize the election mechanism and jointly elect a sentinel node as leader, To handle the failover and notification of the primary node . Therefore, the number of clusters running sentinels should not be less than 3 Nodes .
from leader Sentinel node performs failover , The process is as follows :
- Promote a slave node to a new master node , Let other slave nodes point to the new master node ;
- If the original master node is restored, it will also become a slave node , And point to the new master node ;
- Notify the client that the master node has been replaced .
Here's the thing to watch out for , Objective offline is the only concept of the master node ; If the slave and sentinel nodes fail , By sentinels subjective offline , There will be no further objective offline and failover operations
The election of the main node
- Filter out unhealthy ( Offline ), No reply to the sentry ping The slave node of the response .
- Select the node with the highest priority in the configuration file .(replica-priority, The default value is 100)
- Select maximum copy offset , That is, copy the most complete slave node .
The start of the sentry depends on the master-slave mode , Therefore, we must install the master-slave mode before doing sentinel mode
build redis Sentinel mode
master 192.168.239.10
slave1 192.168.239.20
slave2 192.168.239.30
sentinel-1: 1992.168.239.40
sentinel-2: 1992.168.239.50
sentinel-3: 1992.168.239.60
All sentinel servers are installed redis service
Modify any one sentinel Sentinel mode profile
vim /opt/redis-5.0.7/sentinel.conf
protected-mode no #17 That's ok , Turn off protection mode
port 26379 #21 That's ok ,Redis Sentry's default listening port
daemonize yes #26 That's ok , Appoint sentine1 Start for background
logfile"/var/log/sentinel.log" #36 That's ok , Specify the log storage path
dir"/var/lib/redis/6379" #65 That's ok , Specify the database storage path
sentinel monitor mymaster 192.168.239.10 6379 2
#84 That's ok , Modify the specified sentinel node monitoring 192.168.239.10:6379 This master node , The name of the master node is mymaster, final 2 The meaning of is related to the fault determination of the master node : Need at least 2 Sentinel nodes agree , To determine the failure of the primary node and carry out failover
sentinel down-after-milliseconds mymaster 3000
#113 That's ok , Decision server down Lost time period , Default 30000 millisecond (30 second )
sentinel failover-timeout mymaster 180000
#146 That's ok , The same sentine1 To the same master two failover The time between (180 second )
# Remote transfer transfers configuration files to other sentinel servers
scp /opt/redis-5.0.7/sentinel.conf 192.168.239.50:/opt/redis-5.0.7/
scp /opt/redis-5.0.7/sentinel.conf 192.168.239.60:/opt/redis-5.0.7/



Start sentinel mode
# All sentinel servers execute
cd /opt/redis-5.0.7/
redis-sentinel sentinel.conf &
View sentry messages
redis-cli -p 26379 info sentinel
# Sentinel
sentinel_masters:1
sentinel_tilt:0
sentinel_running_scripts:0
sentinel_scripts_queue_length:0
sentinel_simulate_failure_flags:0
master0:name=mymaster,status=ok,address=192.168.239.10:6379,slaves=2,sentinels=3
[1]+ complete redis-sentinel sentinel.conf
fault simulation
# stay master Node view redis-server Process number
ps -ef | grep redis
# Kill master node redis-server process
kill -9 21981
The verification results
verification master Whether to switch to the slave server
tail -f /var/log/sentinel.log
Check whether the conversion is successful on the sentry
redis-cli -p 26379 info sentinel
Fault recovery
rm -rf /var/run/redis_6379.pid # Delete pid File if pid If the file is not deleted, the service cannot start
/etc/init.d/redis_6379 start # Start the service
netstat -natp |grep 6379
# Master server view
redis-cli info replication
Redis Cluster mode
colony , namely Redis cluster, yes Redis3.0 The introduction of distributed storage scheme .
A cluster consists of multiple nodes (Node) form ,Redis Data is distributed among these nodes . The nodes in the cluster are divided into master and slave nodes : Only the master node is responsible for the maintenance of read-write requests and cluster information ; The slave node only copies the master node data and status information .
The role of clusters , It can be summed up in two points
(1) Data partition : Data partition ( Or data fragmentation ) It is the core function of cluster .
Clusters spread data across multiple nodes , On the one hand, it has broken through Redis The limit of single machine memory size , There's a huge increase in storage capacity ; On the other hand, each master node can provide external reading and writing services , It greatly improves the response ability of the cluster .
Redis The size of single machine memory is limited , Both persistence and master-slave replication are mentioned ; for example , If the single machine memory is too large ,bgsave and bgrewriteaof Of fork Operation may cause the main process to block , When the host is switched in the master-slave environment, the slave node may be unable to provide services for a long time , During the full replication phase, the replication buffer of the master node may overflow .
(2) High availability : Cluster supports master-slave replication and automatic fail over of master nodes ( Like a sentry ); When any node fails , Clusters can still provide external services .
Redis Data fragmentation of cluster
- Redis Cluster introduces the concept of hash slot
- Redis Cluster has 16384 Hash slot ( Number 0-16383)
- Each node of the cluster is responsible for a portion of the hash slot
- Every Key adopt CRC16 Check pair 16384 Take the rest to decide which Hashi slot to place , By this value , Go to find the node corresponding to the corresponding slot , Then directly and automatically jump to the corresponding node for access operation
With 3 Take a cluster of nodes as an example
node A contain 0 To 5460 Hash slot
node B contain 5461 To 10922 Hash slot
node c contain 10923 To 16383 Hash slot
build Redis Cluster mode
redis Clusters generally need 6 Nodes ,3 Lord 3 from .
| Server type | Systems and IP Address | Components that need to be installed |
|---|---|---|
| master1 | 192.168.239.10 | redis-5.0.7.tar.gz |
| master2 | 192.168.239.20 | redis-5.0.7.tar.gz |
| master3 | 192.168.239.30 | redis-5.0.7.tar.gz |
| slave1 | 192.168.239.40 | redis-5.0.7.tar.gz |
| slave2 | 192.168.239.50 | redis-5.0.7.tar.gz |
| slave3 | 192.168.239.60 | redis-5.0.7.tar.gz |
Initialization environment
# Turn off firewall
systemctl stop firewalld.service
systemctl disable firewalld.service
setenforce 0
Turn on the cluster function
Modify any server configuration file
vim /opt/redis-5.0.7/redis.conf
bind 192.168.239.10 #69 That's ok , Comment out bind term , Change to yourself
protected-mode no #88 That's ok , modify , Turn off protection mode
port 6379 #92 That's ok redis Default listening port ,
daemonize yes #136 That's ok , Start Daemons , Start as a separate process
cluster-enabled yes #832 That's ok , uncomment , Turn on the cluster function
cluster-config-file nodes-6001.conf #840 That's ok , uncomment , Cluster name file settings
cluster-node-timeout 15000 #846 That's ok , Uncomment cluster timeout setting
appendonly yes #700 That's ok , modify , Turn on AOF Persistence
# After remote transmission, you should change the listening address to yourself
scp /opt/redis-5.0.7/redis.conf 192.168.239.20:/opt/redis-5.0.7/
scp /opt/redis-5.0.7/redis.conf 192.168.239.30:/opt/redis-5.0.7/
scp /opt/redis-5.0.7/redis.conf 192.168.239.40:/opt/redis-5.0.7/
scp /opt/redis-5.0.7/redis.conf 192.168.239.50:/opt/redis-5.0.7/
scp /opt/redis-5.0.7/redis.conf 192.168.239.60:/opt/redis-5.0.7/
Modify the monitoring address of other nodes to the server configuration file
start-up redis node
All nodes execute
cd /opt/redis-5.0.7/
redis-server redis.conf # start-up redis node
Start cluster
redis-cli --cluster create 192.168.239.20:6379 192.168.239.30:6379 192.168.239.10:6379 192.168.239.40:6379 192.168.239.50:6379 192.168.239.60:6379 --cluster-replicas 1
# The six examples are divided into three groups , One master and one slave in each group , When the former master node interacts with the latter slave node, you need to enter yes To create --replicas 1 Indicates that each master node has a slave node
Test cluster
redis-cli -h 192.168.239.10 -p 6379 -c # Add -c Parameters , Nodes can jump to each other
192.168.239.10:6379> cluster slots # View the node hash slot number range
1) 1) (integer) 5461
2) (integer) 10922 # Hash slot number range
3) 1) "192.168.239.30"
2) (integer) 6379 # Master node ip And port
3) "093fd0ff72272a5b3c91b01fbcc106184971b818"
4) 1) "192.168.239.60"
2) (integer) 6379 # From the node ip And port
3) "97b3832b9be3df6455f3ba34269a92ee07bd46e3"
2) 1) (integer) 0
2) (integer) 5460
3) 1) "192.168.239.20"
2) (integer) 6379
3) "03523dfb1c9efd1da17f9380e94276c171ef2041"
4) 1) "192.168.239.50"
2) (integer) 6379
3) "33bb54b95acfcb61960317f3eaaf19f74fd5cafa"
3) 1) (integer) 10923
2) (integer) 16383
3) 1) "192.168.239.10"
2) (integer) 6379
3) "a0515c00438a99c928e16bd0ec704013e74cc2e7"
4) 1) "192.168.239.40"
2) (integer) 6379
3) "efbb3e371167be32d67462e496ba538ee94fad07"
边栏推荐
- Half find (half find)
- Using FRP tool to realize intranet penetration
- POSIX AIO -- Introduction to glibc version asynchronous IO
- 简析国内外电商的区别
- How to split microservices
- Quickly set up a website to visit foreign countries, set up SS and start BBR to quickly surf the Internet
- 【PHP代码注入】PHP语言常见可注入函数以及PHP代码注入漏洞的利用实例
- Dynamic Networks and Conditional Computation论文简读和代码合集
- Crane: a new way of dealing with dictionary items and associated data
- Completely solve the problem of Chinese garbled code in Web Engineering at one time
猜你喜欢

线程同步之信号量

Learning records of numpy Library

高效率取幂运算

Step by step expansion of variable parameters in class templates

enable_if

Redis持久化

【业务安全-02】业务数据安全测试及商品订购数量篡改实例

【微服务|Sentinel】热点规则|授权规则|集群流控|机器列表

Rereading the classic: the craft of research (1)

What is the difference between the FAT32 and NTFS formats on the USB flash disk
随机推荐
POSIX AIO -- glibc 版本异步 IO 简介
全球芯片市场或陷入停滞,中国芯片逆势扩张加速提升自给率
Half find (half find)
Prometheus 2.26.0 new features
POSIX AIO -- Introduction to glibc version asynchronous IO
CMOS level circuit analysis
#yyds干货盘点# 解决剑指offer:剪绳子(进阶版)
Bidding announcement: Oracle all-in-one machine software and hardware maintenance project of Shanghai R & D Public Service Platform Management Center
Quickly set up a website to visit foreign countries, set up SS and start BBR to quickly surf the Internet
力扣 第 81 场双周赛
现在开户有优惠吗?网上开户是否安全么?
解析Activity启动-生命周期角度
Can flush open an account for stock trading? Is it safe?
Kyndryl partnered with Oracle and Veritas
美国芯片再遭重击,继Intel后又一家芯片企业将被中国芯片超越
How ASP connects Excel
crane:字典项与关联数据处理的新思路
American chips are hit hard again, and another chip enterprise after Intel will be overtaken by Chinese chips
【问题解决】Tensorflow中run究竟运行了哪些节点?
A statistical problem of shell script