当前位置:网站首页>Five day summary of software testing
Five day summary of software testing
2022-06-24 19:36:00 【Ssie-】
Software : A tool that controls the operation of computer hardware
software test : Use Technical means Verify whether the software meets the use requirements
The purpose of software testing : Reduce software defects , Guarantee software quality
Test mainstream skills :
- A functional test : It mainly verifies whether the function of the program meets the requirements
- automated testing : Use the code / Tool instead of manual , Test the project . Automation is more efficient than manual work
- The interface test : Interface (1, Hardware interface 2. software interface ) Use the code / The tool tests the interface provided by the server , Check whether the access is normal . Interface testing can be implemented with tools or code
- Performance testing - Tool implementation : simulation Many people Use software , Find server defects
Test categories :
1. By test phase
(1) unit testing : Test the program source code
(2) Integration testing ( The interface test ): Test the access address between modules
(3) The system test : Test the whole system, including function 、 Non functional ( compatible 、 file ) Etc
(4) The acceptance test : It is mainly divided into internal test 、 Public survey , Use different people to discover project defects
2. By code visibility
(1) Black box testing ( The system test ): The source code is not visible ,UI Function visible
(2) Grey box testing ( Integration testing ): Part of the source code is visible ( You can see the interface ), The function is not visible
(3) White box testing ( unit testing ): All codes are visible ,UI The function is not visible
special : Performance testing 、 Security
Model
- Quality model : Weigh one good Software dimension 【 Functionality 、 performance 、 Compatibility ( Test in browser : Google 、IE、 Auburn 、 Apple 、 Whether Firefox can work properly ; On the operating system :win System (win7、win8、win10) And other things ; mobile phone : The resolution of the 、 brand 、 System 、 The Internet 、 other )、 Ease of use ( brief introduction 、 friendly 、 Fluent 、 beautiful )、 reliability ( No response 、 Carton 、 crash )、 Security 、 Portability 、 Maintainability 】
Testing process
- Requirements review : Ensure that all departments have a consistent understanding of the needs
- Plan preparation : What to measure 、 Who will test it 、 How to measure
- Use case design : Operation documents to verify whether the project meets the requirements
- Use case execution : After the project module development is completed, start to execute the use case document and implement the test
- Defect management : The process of managing defects
- Test report : Implement test result documentation
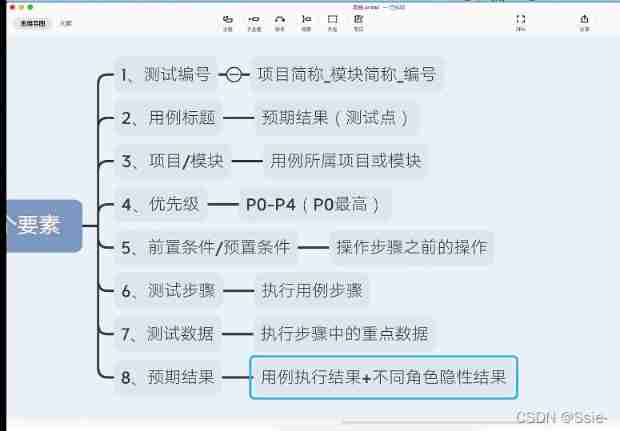
Use cases : User cases
The test case : Execution documents designed for test projects
The role of test cases
- Prevent missing measurement
- Standards for conducting tests

Equivalence class division
- explain : In all test data , Data sets with some common characteristics are divided
- classification :(1) Effective equivalence class : A collection of data that meets the needs (2) Invalid equivalence class : Data sets that do not meet the requirements
- step :(1) Clear requirements (2) Determine valid and invalid equivalence classes (3) Extract data and write test cases
Equivalence classes solve the problem of exhaustion : Test input for large amounts of data , But there's no exhaustive list of tests . for example : Input box 、 The drop-down list 、 Radio check box . Typical representative : Page input box class test .
Complete use cases should be written together with equivalence classes and boundary values
Solve the problem of boundary constraints : Use boundary values Solve the boundary digit limit problem
Boundary range node
Upper point : Points on the border ( It's exactly the same as )
Departure point : The point closest to the upper point ( Just bigger than 、 Just less than )
Inside point : Points in the range ( Interval data )

Tips :
- About scope limitations , Up to seven use cases
- Boundary value can solve the problem of digit limit , But it can't solve the type problem
step :
- Clear requirements
- Identify valid and invalid equivalents
- Determine the boundary range
- Extract data and write use cases

Decision table : solve Multiple conditions have dependencies test

step :

Summary of decision table :

Tips :
1. There are dependencies between multiple conditions , The decision table can be used for test coverage
2. The decision table is generally suitable for 4 Within conditional dependencies
3. If there are more than four conditions , It is not suitable to cover all conditions , Should adopt Orthogonal method To solve
Business test coverage
a key :
1. Covering business testing , Need to use Flow chart method
2. Test the business first , Retest the single function 、 Single module 、 Single page
Design and test the project business
flow chart : Use standard graphics and arrows to express the direction of the program or business , Business use cases are sorted out according to the flow chart
The function of the flow chart : Sort out business use cases
Use flow chart tools :excel、visio
Error recommendation method :

Time is tight and there are a lot of tasks : I will first determine with the product personnel what are the important businesses to cover the main businesses , And then carry out forward according to the function 、 Reverse walk , Will work overtime to complete .
Application scenarios : When the project use case is executed , And bug Repair completed , It's still some time before it goes online , During this period, the error recommendation method will be used to retest the main businesses or test the functions not covered
defects (bug): Any problems in the use of the software problem They are called software defects
Defect judgment criteria :

Caused by defects reason :
Demand stage : The requirement description is not easy to understand , Ambiguity 、 Errors, etc
design phase : There are errors or defects in the design documents
Encoding phase : Code error
Operation phase : The failure of software and hardware system itself leads to software defects
Software defects Life cycle :

It's solved A Defects may be injected B defects
defects Core elements

defects Submit elements

Defect classification
- Function error
- UI Page error
- Compatibility
- data ( database )
- Ease of use
- Suggest
- Architecture flaws
Workflow :
Design use cases -> Execute use cases ( Perform the test )-> defects ( Submit 、 verification 、 close )
Example defect report :

Submit defect notes :
Can be reproduced : Defects can be reproduced
Uniqueness : A defect reports a problem
Normative : Meet the requirements of the company or the project
Interview questions : When you find a defect , What would you do ?
The first thing is to see if it is reproducible , Check whether it is consistent with existing bug repeat , If not, submit
Defect tracking flow chart :

Defect management tools
- Project management tools - Management defects ( ZenTao 、JIRA\TFS)
- Excel Management defects
HTML
One of the three front-end cores HTML: Hypertext markup language , It's made up of a set of tags
Single label :< Tag name />
Double label :< Tag name ></ Tag name >
attribute : Describe a feature Example :<a Property name =’ Property value ’>
Html: Root tag , Everything should be here
Head: Head tag
Body: Body tags ( Code editing Office )
Note international shortcut key :ctrl+/
Test point : Before the front-end page is released online , Need to check ( Inappropriate words appear ) All comments or remove comments
Title Tag : adopt <h1>--<h6> And so on ,<h1> Maximum ,<h6> Minimum
Paragraph Tags : adopt <p> Tag definition , Monopolize one line , Have line feed function
Hyperlinks : adopt <a href=“http:// ” target=” ”></a>
href: Jump address ( No addition https, You will think it is a local file );
target: New window open (target=”_blank” Open for new window )
Picture label :<img src=”logo.jpg” title=” Blog ” alt=”logo” width=”104”/>
Src: Picture path
Title: cursor Hover and not loaded Displayed text ( There must be title attribute )
Alt: picture When not loaded Displayed text
Width: Image width
Height: Picture height
Relative paths : The starting point is the location of the current execution file . At the next higher level :../ At the same level :./
Line break :<br/>
Space : 
Big box : Monopolize one line <div>
Small box : You can put more than one in a row <span>
Tabs tab :
- Orderly :<ol></ol>
- disorder :<ul></ul>
- <li> label </li>

Style:Css label ;script:js label ;link: External load css label
Form labels :<input type=” ” />
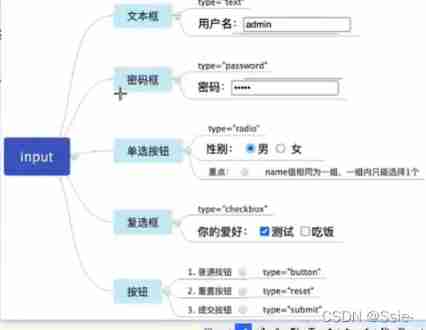
Single choice effect :
- The same group radio To make a single choice
- The settings are the same ( Group name )name Attribute values are a set of
for example :
<input type=“radio” name=“one”/> male
<input type=“radio” name=“two”/> Woman
Button test point : Unified use value Assign a value
Tips : Normal buttons have no execution effect by default , Need to cooperate with js Realization
<form> effect : Submit the data entered on the page to the background or the specified page
<form action=”” method=””></form>
attribute :
- action: Specify which page to submit the data to
- method: Method of submitting parameters (get、post)
get( Query usage ): Parameters url In clear text ; Fast submission ; The submission parameter has a length Limit
post( Submit data 、 Sign in 、 register ): Parameters url Non plaintext display ; Slow submission speed ‘ The length of the submission parameter unlimited
边栏推荐
- Internet of things? Come and see Arduino on the cloud
- cdc+mysql connector从维表中join的日期时间字段会被+8:00,请问阿里云托管的
- php OSS文件讀取和寫入文件,workerman生成臨時文件並輸出瀏覽器下載
- IBPS开源表单设计器有什么功能?
- Technology implementation | Apache Doris cold and hot data storage (I)
- Geoscience remote sensing data collection online
- LCD12864 (ST7565P) Chinese character display (STM32F103)
- 实时渲染:实时、离线、云渲染、混合渲染的区别
- Server lease error in Hong Kong may lead to serious consequences
- PHP OSS file reads and writes files, and workman generates temporary files and outputs them to the browser for download
猜你喜欢

R language 4.1.0 software installation package and installation tutorial
一文详解|Go 分布式链路追踪实现原理
Power efficiency test

模块五

Unity mobile game performance optimization spectrum CPU time-consuming optimization divided by engine modules

Vs2017 setting function Chinese Notes

starring V6平台开发接出点流程

Tkde2022: Dialogue recommendation system based on knowledge enhanced sampling
![[R tidyverse] use of select verb](/img/2d/768391bc6ec497432915024bc90842.jpg)
[R tidyverse] use of select verb

Internet of things? Come and see Arduino on the cloud
随机推荐
Does finkcdc support sqlserver2008?
Network security review office starts network security review on HowNet
Database index can improve query efficiency. Ask what will improve, what is the difference between inapplicable index and index use, and what will happen.
Xiaodi class massive data processing business short chain platform
Necessary fault handling system for enterprise network administrator
How to deal with the problem that the Flink CDC reads MySQL in full and always reports this error
BSS应用程序云原生部署的8大挑战
Landcover100, planned land cover website
R语言corrplot相关热图美化实例分析
R language 4.1.0 software installation package and installation tutorial
starring开发HttpJson接入点+数据库
What are the functions of IBPs open source form designer?
Would you like to ask whether the same multiple tasks of the PgSQL CDC account will have an impact? I now have only one of the three tasks
thinkphp6中怎么使用jwt认证
Digital twin industry case: Digital Smart port
试驾 Citus 11.0 beta(官方博客)
Write a positive integer to the node and return a floating-point number multiplied by 0.85 when reading the node
High dimension low code: component rendering sub component
A detailed explanation of the implementation principle of go Distributed Link Tracking
Fabric ledger data block structure analysis (I): how to analyze the smart contract transaction data in the ledger