当前位置:网站首页>How to view Apache log4j 2 remote code execution vulnerability?
How to view Apache log4j 2 remote code execution vulnerability?
2022-07-05 21:50:00 【Blue bridge cloud class】
Apache Log4j2 Is a first-class Java Log framework , A large number of business frameworks use this component .
2021 year 11 month 24 Japan , Alibaba cloud security team to Apache The official report Apache Log4j2 Remote code execution vulnerability , This loophole Trigger condition low , Great harm .

12 month 10 Early morning ,Apache Open source project Log4j Remote Code Execution Vulnerability of Details are made public , because Apache Log4j2 Some functions have recursive parsing function , Attackers can directly construct malicious requests , Trigger Remote Code Execution Vulnerability .
CVE Number :CVE-2021-44228
Affected version :log4j2 2.0-beta9~2.14.1
As soon as this news comes out , It makes it difficult for many safety engineers to sleep , Immediately get up and enter “ Combat Defense status ”. This reminds me of the recent epidemic in Zhejiang , The medical staff rushed in overnight “ Combat status ”.
(PS: There has been a high incidence of the epidemic recently , Friends must wash their hands frequently 、 With mask 、 Don't run around !)

In addition to the safety personnel of various enterprises , Major safety manufacturers also immediately started Verification of vulnerability authenticity , And urgently notify users to upgrade rules to resist the latest vulnerabilities , Avoid serious spread of vulnerability hazards .
How serious is it ? Let me just say one , Feel for yourself :
Enterprise patching may take several hours , Even to It took several days , But hacking , But only need A few minutes Time ! Is patching faster , Or hackers attack faster , I don't need to say more ?
Apache Log4j2 Not a specific Web service , But a third-party logging framework for processing logs ( library ), whatever Java Web It is possible to use this logging framework , Use Log4j2 It's really super much , Too many to count .
I really need to count one or two , It's better to count without using Log4j2 Come faster . As one can imagine , After being attacked , How wide is the coverage .
How about Reproduce this loophole , And fix it ?
We can do a lot based on Java Developed Web service To reproduce this loophole , As long as the service uses log4j2 library ( Versions within the scope of vulnerability ) that will do , such as Apache Solr .
The method of triggering the vulnerability is very simple , Only need to Solr Administrator interface action Parameter sending Payload , Because the interface will call log4j Log , Therefore, the vulnerability execution will be triggered . The interface is as follows :
http://127.0.0.1:8983/solr/admin/cores?action=
Next use DNSlog To construct a verification Payload.
DNS Log For most students of penetration test , Should be familiar with , It is often used to test the loopholes of blind typing and blind injection .
If you don't know , It can be simply understood as : We get a temporary domain name , If the remote server tries to access the domain name , Will be in DNS Leave access records on , At this time, we can get some out of pocket information by querying the record .
Yes, of course , DNS log Just as one of the ways to verify the existence of vulnerabilities , Is not the only solution .
Blue bridge cloud class Slightly rubbed a heat picture , Launched 《 Apache Log4j 2 Detailed explanation of Remote Code Execution Vulnerability 》, use Hands-on experiment To help you reproduce Apache Log4j2 Remote code execution vulnerability .
This course will introduce this vulnerability in detail principle 、 Utilization mode 、 Excavation method and repair method , It also includes hands-on Online experimental environment , Understand the loopholes more deeply .
The key is coming. ! Immediately , Learn for free !
Apache Log4j 2 Remote code execution vulnerability
Now? , Let's talk about the loopholes Mining methods and tools .
Vulnerability mining can be carried out from White box and black box From two angles :
- If you are reviewing whether your application is affected by log4j2 Holes affect , White box testing is the way you should first choose , It can help you do the most comprehensive inspection from the source code level .
- Black box testing has great uncertainty , Because from a black box perspective , Any parameter may trigger log4j2 Loophole . Therefore, the accuracy of black box test , A large part depends on whether the parameters tested are comprehensive .
I recommend two tools , For your reference :
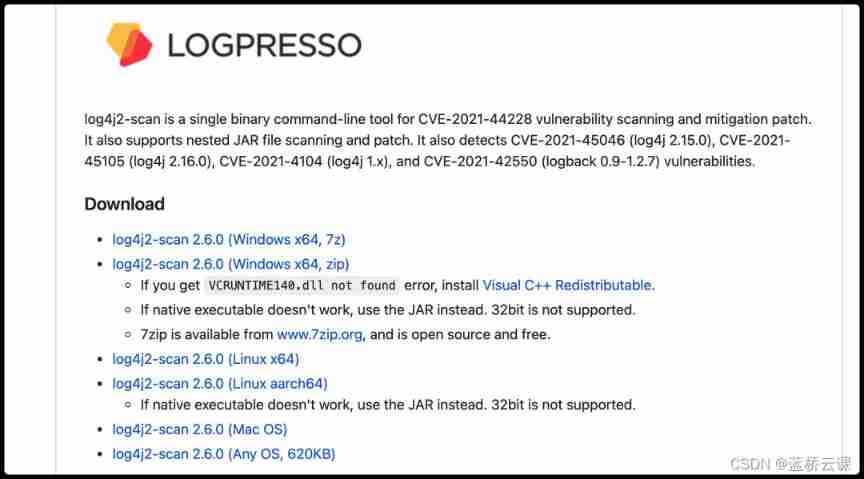
1、 The following tool is recommended for white box testing to scan the source code :
CVE-2021-44228-Scanner
You can download the corresponding version according to the platform :
2、 The following tool is recommended for black box testing :
BurpSuite Pro plug-in unit
open BurpSuite Pro, Switch to Extender -> BApp Store, Search in the search box on the right log4, You can see two plug-ins ( end 2021 year 12 month 22 Japan ):
- log4shell Everywhere: Passive scanning plug-in
- log4Shell Scanner: Active scanning plug-in
Install the above two plug-ins respectively , And then in Active Scan and Passive Scan It will automatically check log4j Loophole , If a loophole is found , The result will be Dashboard Show in .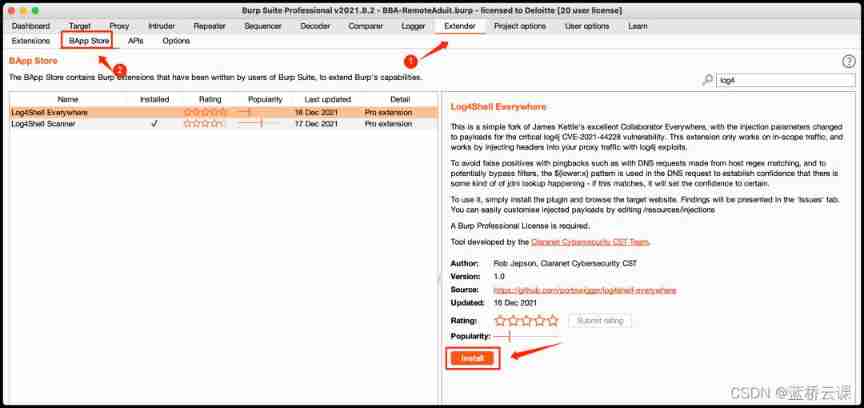
Okay , Today's Apache Log4j 2 Remote code execution vulnerabilities are shared here . If you want to duplicate this vulnerability , And practice by yourself , You can poke the link below for free ~
Apache Log4j 2 Remote code execution vulnerability
边栏推荐
- 微服务入门(RestTemplate、Eureka、Nacos、Feign、Gateway)
- Poj 3237 Tree (Tree Chain Split)
- 2022-07-03-cka- latest feedback from fans
- Comprehensive optimization of event R & D workflow | Erda version 2.2 comes as "7"
- Experienced inductance manufacturers tell you what makes the inductance noisy. Inductance noise is a common inductance fault. If the used inductance makes noise, you don't have to worry. You just need
- Alibaba cloud award winning experience: build a highly available system with polardb-x
- HYSBZ 2243 染色 (树链拆分)
- Exercise 1 simple training of R language drawing
- Feng Tang's "spring breeze is not as good as you" digital collection, logged into xirang on July 8!
- Interview questions for basic software testing
猜你喜欢

Parker driver maintenance COMPAX controller maintenance cpx0200h
EasyExcel的讀寫操作
Kingbasees v8r3 cluster maintenance case -- online addition of standby database management node

Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned
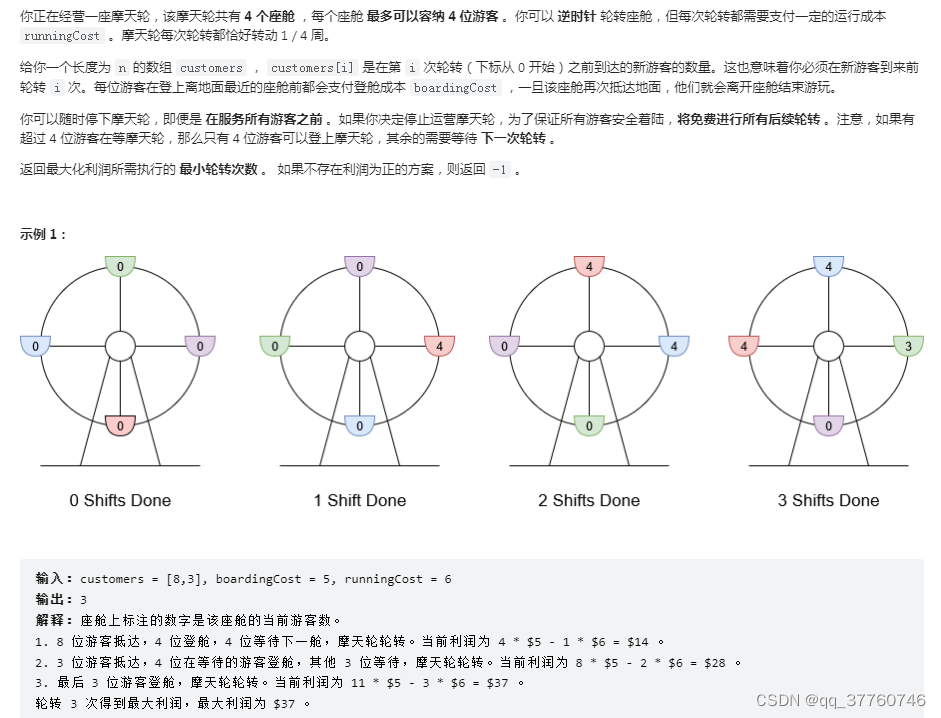
Li Kou ----- the maximum profit of operating Ferris wheel
PIP install beatifulsoup4 installation failed
华为快游戏调用登录接口失败,返回错误码 -1
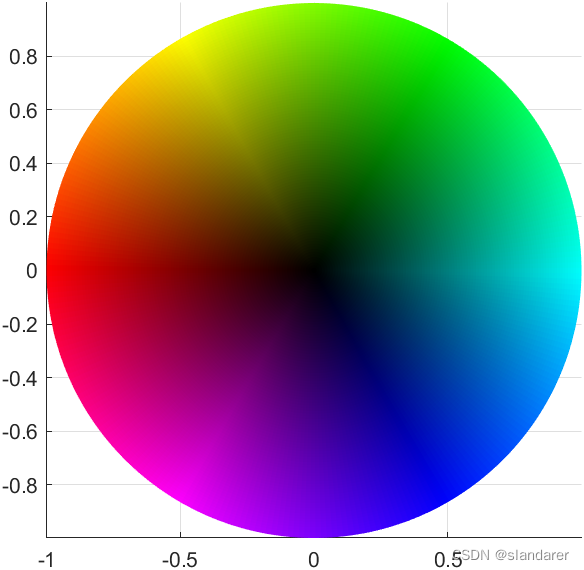
Drawing HSV color wheel with MATLAB

What should I do to prepare for the interview algorithm position during school recruitment?
Implementing Lmax disruptor queue from scratch (IV) principle analysis of multithreaded producer multiproducersequencer
随机推荐
Two ways to realize video recording based on avfoundation
Teach yourself to train pytorch model to Caffe (2)
MMAP
Yolov5 training custom data set (pycharm ultra detailed version)
Huawei game multimedia service calls the method of shielding the voice of the specified player, and the error code 3010 is returned
oracle 控制文件的多路复用
datagrid直接编辑保存“设计缺陷”
crm创建基于fetch自己的自定义报告
What should I do to prepare for the interview algorithm position during school recruitment?
DBeaver同时执行多条insert into报错处理
xlrd常见操作
Robot operation mechanism
123456
EasyExcel的讀寫操作
Opérations de lecture et d'écriture pour easyexcel
Problems encountered in office--
Evolution of zhenai microservice underlying framework from open source component encapsulation to self-development
阿里云有奖体验:用PolarDB-X搭建一个高可用系统
2.2.5 basic sentences of R language drawing
"Grain mall" -- Summary and induction