当前位置:网站首页>Secondary vocational group network security - memory Forensics
Secondary vocational group network security - memory Forensics
2022-07-04 04:55:00 【Beluga】
volatility -f test2.raw imageinfo
Get image details profile Parameters are important It will be used later

volatility -f test2.raw --profile=Win7SP1x64 hashdump
Get mirrored hash Value and user name After obtaining, you can use john Tools for dictionary decryption Or use ophcrack Crack
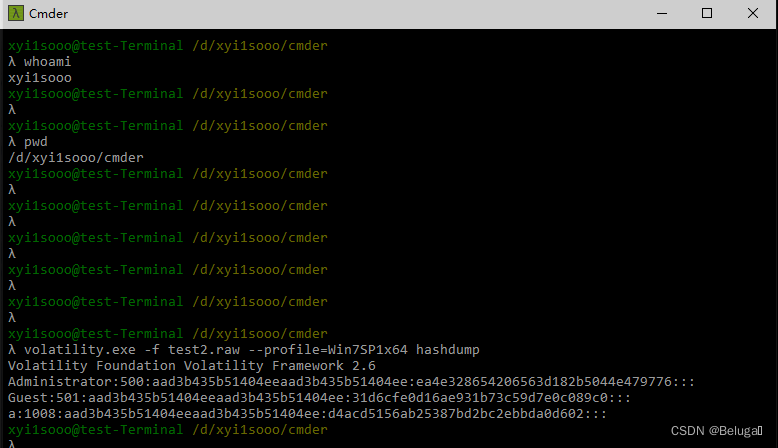
If there is mimikatz plug-in unit You can use it directly mimikatz To crack Direct password
The other is lsadump Can come out intermittent password It's not complete
volatility -f test2.raw --profile=Win7SP1x64 netscan Check the network connection

A lot of information will come out here ip According to the open port, we judge that 10.30.21.96 Go to the virtual machine to detect So it is
volatility -f test2.raw --profile=Win7SP1x64 envars | grep USERNAME

You can view the host name , Be careful to remove the back $ Symbol
obtain flag Document ideas :
1. Get the desktop file name , Guess its content
volatility -f test2.raw --profile=Win7SP1x64 filescan | grep Desktop
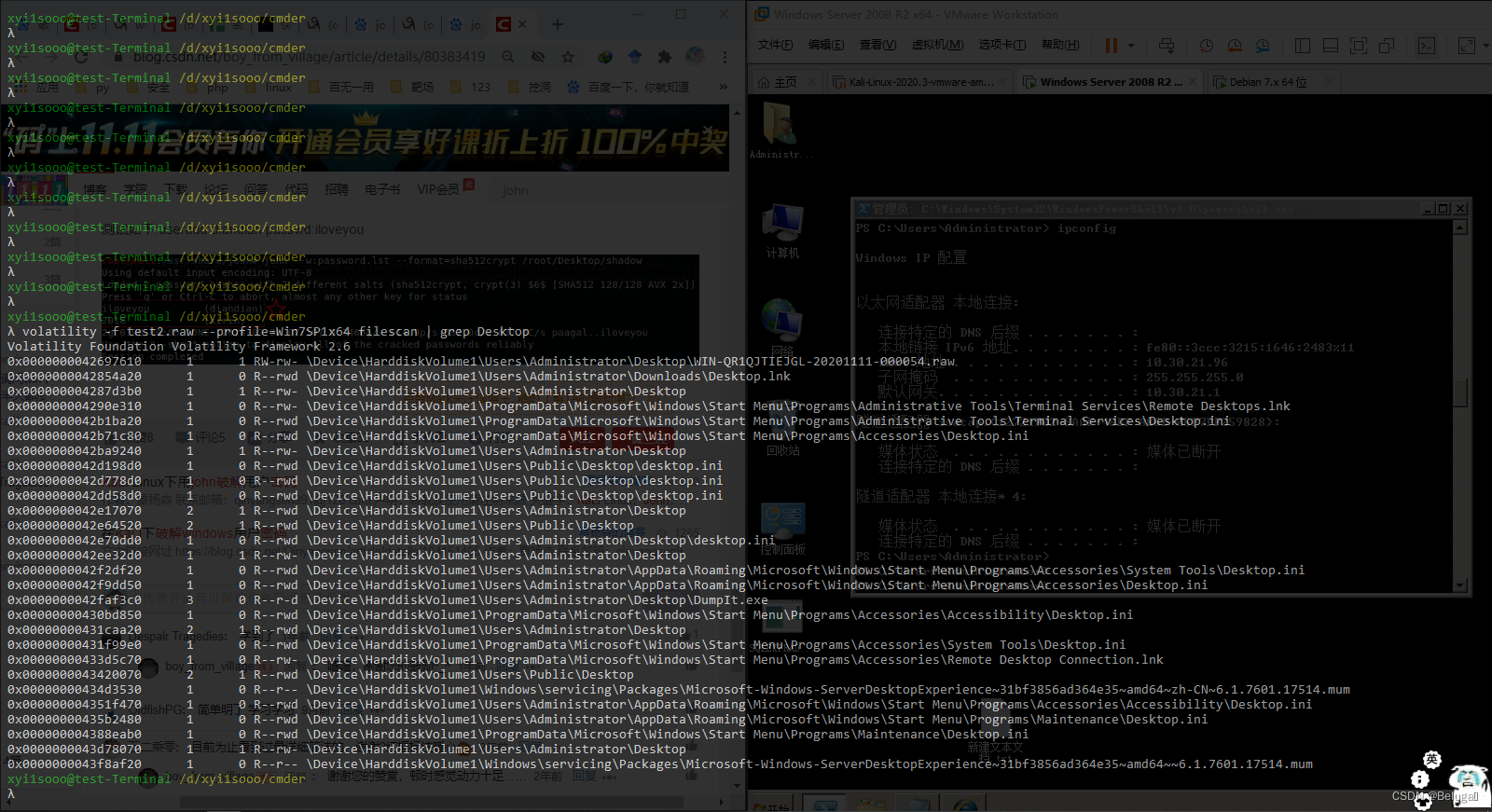
You can see the files on the desktop But can't read its contents
2. Maybe the desktop opens a notepad Program Use notepad You can see
volatility -f test2.raw --profile=Win7SP1x64 notepad
Mining process ideas :
1. First find the process with abnormal name such as Explore.exe The original system process is explorer.exe
2. In the case of Wei Guo in the previous way, the start time of the monitoring system process Judging from the starting time
3. Anyway, only the port and ip, Find external ip Try one by one
volatility -f test2.raw --profile=Win7SP1x64 netscan/connscan
volatility -f test2.raw --profile=Win7SP1x64 svcscan
volatility -f test2.raw --profile=Win7SP1x64 hivelist
Get browser history
volatility -f test2.raw iehistory
I'll give you one url From the parameters inside, you can see what has been searched
边栏推荐
- Binary search tree
- 中科磐云—2022广东木马信息获取解析
- Beipiao programmer, 20K monthly salary, 15W a year, normal?
- 附件二:攻防演练保密协议.docx
- 中科磐云—D模块解析以及评分标准
- Distributed cap theory
- Wobo Union ended its strategic evaluation and decided to retain Bozi's business with excellent performance
- C basic (VII) document operation
- AcWing第 58 场周赛
- 附件一:202x年xxx攻防演习授权委托书
猜你喜欢

C basic (VII) document operation
抓包整理外篇fiddler———— 会话栏与过滤器

测试 CS4344 立体声DA转换器

What is context?
Annex VI: defense work briefing docx

Technology Management - learning / practice
PostgreSQL 正式超越 MySQL,这家伙也太强了吧!
关于solidworks standard无法获得许可 8544问题的总结

RAC delete damaged disk group

The five pictures tell you: why is there such a big gap between people in the workplace?
随机推荐
Technology Management - learning / practice
(pointer) write function void fun (int x, int *pp, int *n)
MySQL indexes and transactions
cmake
[cloud native] those lines of code that look awesome but have a very simple principle
【MATLAB】MATLAB 仿真 — 低通高斯白噪声
6-5漏洞利用-SSH弱口令破解利用
【MATLAB】通信信号调制通用函数 — 插值函数
Eig launched Grupo Cerro, a renewable energy platform in Chile
Kivy教程之 07 组件和属性绑定实现按钮button点击修改label组件(教程含源码)
Solve the problem of failed to load property source from location 'classpathapplication YML 'problem
Y55. Chapter III kubernetes from entry to proficiency -- HPA controller and metrics server (28)
RPC - gRPC简单的demo - 学习/实践
附件六:防守工作简报.docx
网络设备应急响应指南
Annex II: confidentiality agreement for offensive and defensive drills docx
Use units of measure in your code for a better life
Kivy tutorial 07 component and attribute binding implementation button button click to modify the label component (tutorial includes source code)
Zhengzhou zhengqingyuan Culture Communication Co., Ltd.: seven marketing skills for small enterprises
【MATLAB】MATLAB 仿真模拟调制系统 — AM 已调信号的功率谱与相干解调