当前位置:网站首页>[technical dry goods] the technical construction route and characteristics of zero trust in ant Office
[technical dry goods] the technical construction route and characteristics of zero trust in ant Office
2022-06-23 22:44:00 【Alipay Technology】
lead said
1 Zero trust security model and technical route
1.1 Traditional boundary security model
1.2 Zero trust security model
1.3 Zero trust typical security architecture
2 Zero trust in industry office from concept to implementation
3 Ant office zero trust integrated security protection
3.1 Zero trust SIM The core technology
3.1.1 SDP( Software defines boundaries )
3.1.2 IAM( Modern identity and access management )
3.1.3 Micro Segmentation( Micro isolation )
3.2 Ant office zero trust security architecture
3.2.1 SDP client
3.2.2 SDP gateway
3.2.3 SDP controller & IAM
3.3 Ant office zero trust landing practice
4 Future outlook
01
Zero trust security model and typical architecture

The shortcomings of being :
● The traditional border security model considers the Intranet environment to be reliable , Weak internal security protection , Lack of internal flow check .
● Once the network boundary is broken , The whole system will be under threat .
● The traditional security model is constantly developing itself , for example : In depth protection concept , Through multipoint protection , Exchange space for detection time , But active defense is still lacking .
1.2 Zero trust security model
Zero trust is essentially for people 、 equipment 、 All assets such as servers are identified , Build a trust evaluation and dynamic access control system based on identity , Ensure secure access to business data , Here's the picture 2, That is, access the model through zero trust business , Make sure the right people , Use the correct terminal , Use the correct permissions at any network location , Access to the right business , Get the right data . The zero trust model performs security verification for each link of the access process , Insert security and trust assessment and protection into each key link . Even if a link is broken , Other security checkpoints remain in effect .

The basic principle of :
● As long as you're on the network , No user is trusted .
● Under the zero trust model , Any time, any environment 、 equipment 、 Identity permissions need to be continuously verified .
● Security is built on a chain of trust , If the chain of trust is broken , Then access to the resource will be automatically cancelled .
1.3 Zero trust typical security architecture
The implementation of zero trust architecture has successfully improved the enterprise security situation , Input and cooperation from all stakeholders of the enterprise are required , To solve this key problem, the National Institute of standards and Technology NIST stay 2020 It was proposed that 《NIST SP800-207: Zero trust architecture draft 》, It mainly provides a top-level overview of the risk management framework and how to help develop and implement the zero trust architecture , Here's the picture 3.

chart 3 NIST A typical zero trust architecture
Where the access agent 、 Access control engine and 4A Systems are the basic capabilities that most enterprises already have , The difficulty lies in how to clearly depict the subject and object of access with identity as the center , Effective fine-grained perception and accurate trust evaluation of the subject and object as well as the access process environment , Only then can we truly realize the trusted and secure dynamic access control . The specific functions of the core component module are as follows :
● Trust assessment engine : Add dynamic response factors that were missing or impossible to implement in previous boundary based architectures , Collect the access subjects in the enterprise as reasonably as possible 、 Objects and related assets in the access process environment 、 The Internet 、 file 、 Process and communication data , Conduct multidimensional dynamic trust evaluation by combining enterprise security policy and allow list .
● Access control engine : Each access request denies connection by default , To be granted access, you must authenticate and prove compliance with the enterprise security policy , Adhering to the principle of minimum authority , Access requests are context based 、 Dynamic authority determination of trust level and security policy .
● Agent access : For access unified closing , Untrusted interception , The access request passes the identity authentication and trusted assessment .
● Identity security basic platform : For people 、 equipment 、 All assets such as servers are identified , be based on 4A( authentication 、 Account 、 to grant authorization 、 Audit ) And the end security client and other system platforms establish a unified identity to provide personnel and equipment identity security evaluation capabilities .
02
Zero trust in industry office from concept to implementation
“ De borderlization security concept ” As early as 2004 It was proposed in .2009 In, Google faced APT The attack was the first to make a change ( BeyondCrop Project landing ), Completed the first integrity product with zero trust .NIST stay 2020 The principle of zero trust standard architecture construction was put forward in , Authority Forrester and Gartner It has also given the construction concept of zero trust . Domestic manufacturers are also gradually opening the industry zero trust exploration and landing , And started the construction of zero trust domestic standards .
Most domestic and foreign manufacturers are “ Identity is central ” Launched the construction of zero trust , Different manufacturers have different paths to build zero trust , Each has its own emphasis on its own advantages , There are self-development and acquisition . Network security manufacturers focus on their own advantageous fields , Build zero trust products based on the original network hardware system , Typical manufacturers such as Cisco , By acquiring something like Duo Security The company complements the identity security weakness , Zero trust integration . And most of Google and emerging zero trust vendors focus on identity centric solutions , Some horizontal integration covers network security 、 Data security and terminal security .

chart 4 Google BeyondCorp
At present, the well-known zero trust scheme , Pictured above 4 For the often mentioned Google BeyondCorp, The core components ( Trust inference evaluation engine 、 Access to the agent 、 Single sign on 、 Certificate management ) And basic data and platform ( user / Group data 、 Certificate issue 、 Equipment list database ) Polish and blend , It took more or less 6 More years , Solved a series of complex problems ( Recall accuracy of equipment asset data 、 Business scenario adaptation 、 Low performance 、 Data fault tolerance 、 High Availability Disaster Recovery protection, etc ), By extending the access control measures from the network boundary to the internal access process , Enables users to work safely almost anywhere , Without resorting to tradition VPN, You can safely access various systems in the office network .
although Google BeyondCorp The scheme is worth learning from , But many enterprise networks and application environments are different , There are still many restrictions on zero trust adaptation , There are two typical types :
● Risk behavior control : The trust evaluation engine will detect and mark the access traffic ( Judge black / white / ash ), about “ gray ” Traffic , The user needs to confirm again , And it needs the combination of zero trust and risk behavior control , The risk can be assessed ;
● Data protection : At home “ The trinity ” Safety laws and regulations , Data protection is becoming increasingly important , Zero trust is currently mainly used for dynamic access control , Data protection scenarios need to be further expanded .
03
Ant office zero trust integrated security protection
3.1 Zero trust SIM The core technology
For the construction of zero trust products, different manufacturers and enterprises are different , But you can also do simple classification and analysis to find your own way . At present, there are three main technical construction routes in the industry (SIM) Or a mixture of the three .
3.1.1 SDP( Software defines boundaries )
Software defines boundaries ( SDP ) The concept comes from the Defense Information Systems Agency ( DISA ), In the past decade, the concept has been officially recognized and popularized by the cloud security alliance .SDP It embodies the core dynamic security control in the zero trust security architecture , The identity boundary based on zero trust can be flexibly and dynamically controlled by software definition , Evaluate the trust of the requested access to the system and grant minimal access . Here's the picture 5 SDP Rely on the controller to manage dynamic security access to the network , Entities communicating on the protected network ( Connect to the initiating host ) Must run SDP Client software , And pass SDP Controller and SDP The gateway performs dynamic authentication and access control .
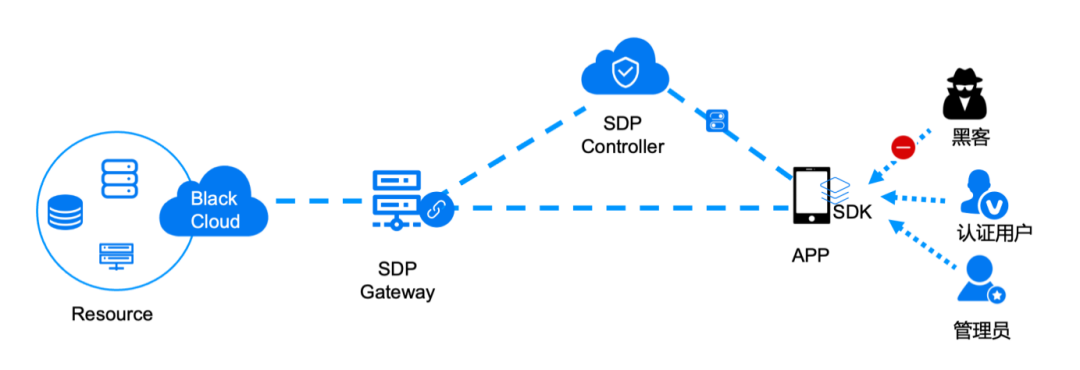
chart 5 SDP Model
Core components :SDP client ( Verify identity , The request is sent to the gateway )、SDP controller ( Responsible for dynamic identity authentication and access control )、SDP gateway ( Protect business systems 、 Defense attacks )
characteristic : All apps hide 、 Visitors don't know where the application is ; All traffic is encrypted , Point to point communication ; Continuous Certification 、 Fine grained context control 、 Signaling separation
To protect : User to business access security
3.1.2 IAM( Modern identity and access management )
IAM The core of is to establish identity before users enter the network , This is also the basis of the zero trust model . adopt IAM System ( Here's the picture 6 IAM framework ) Unique identification of identity , It is helpful for the zero trust system to confirm the user's trust , Establish a terminal for user identity through a unique identity 、 Trust in resources , And when the risk is found, the key user related access connection is blocked .

chart 6 IAM
Core components : authentication center 、 Identity authority center 、 Audit Center
characteristic : For people in the network 、 Applications are given logical identities , Minimize dynamic permission access control with identity as the access principal
To protect : User to business access security
3.1.3 Micro Segmentation( Micro isolation )
Micro isolation has multiple forms , Cloud native control is common among virtualization platform providers ( Pictured 7), On the virtualization platform 、hypervisor Or in the infrastructure , Generally, it belongs to the same cloud platform supplier , It is deeply coupled with the cloud platform system , Support automated orchestration , More suitable for isolation , East west management ability is limited .
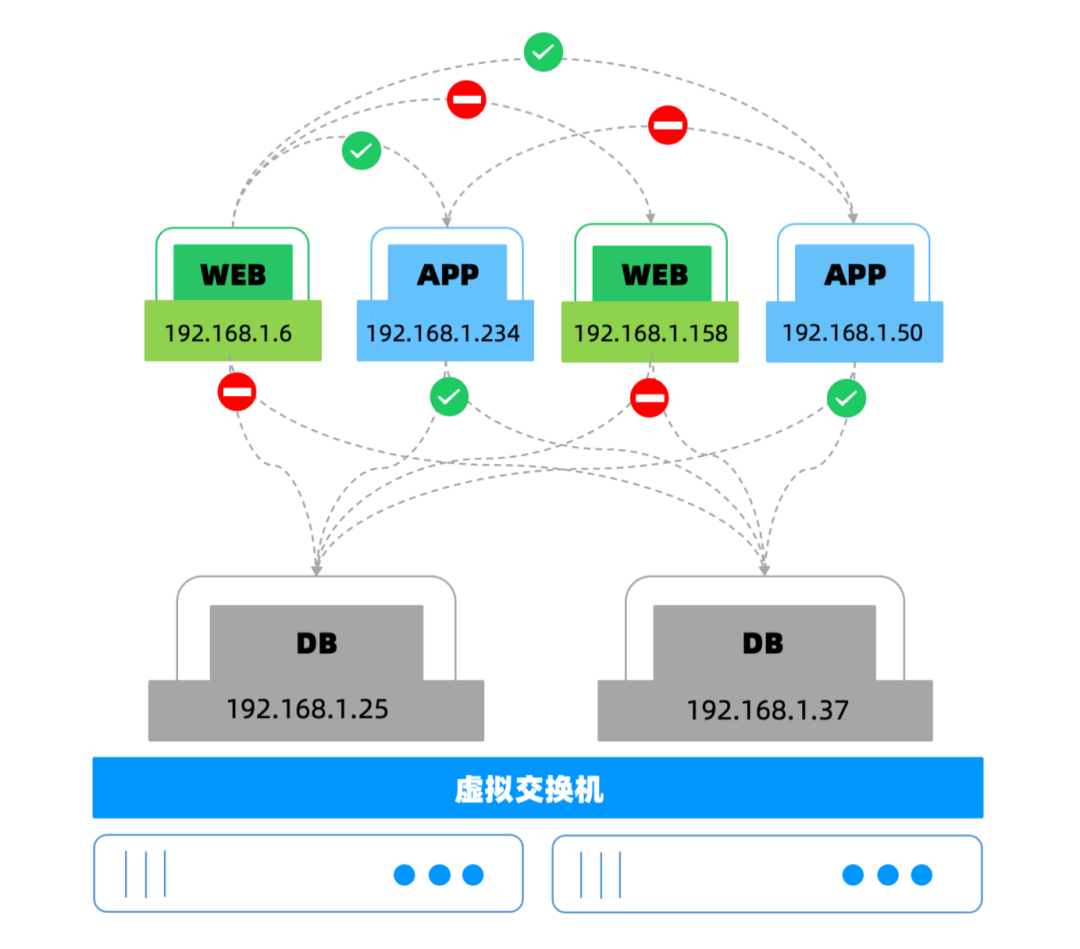
chart 7 Micro isolation model
Core components : Based on cloud technology 、 Network virtualization technology
characteristic : Micro isolation is a way to create security zones in data centers and cloud deployments , This approach enables enterprise organizations to separate workloads and protect them separately
To protect : Business to business access security
3.2 Ant office zero trust security architecture
be based on SDP + IAM + MSG Zero trust core technology , Combined with the actual situation of ant enterprises , Build an office zero trust security management and control platform with identity as the boundary . Here's the picture 8 , Install on the terminal SDP After the client , The control terminal can be realized 、 Cross network connection 、 Apply stealth 、 The terminal is trusted 、 Virus detection and many other functions , Secure access to office personnel and equipment ;SDP The gateway bundles the access request in the specified link , Better reduce north-south exposure ;SDP The controller dynamically integrates multidimensional trust evaluation and effective identity authorization . Through ants SDP client + SDP gateway + SDP The controller is a combination of the three , Add dynamic access control capability , Play in multidimensional integrated protection .
The enterprise identity authentication authority management center is integrated with the new zero trust architecture , From boundary centric static authentication to identity centric new generation adaptive authentication and dynamic authentication , Micro isolation is realized between applications through application service authentication , It also reduces the security risk of Intranet horizontal movement , At the same time, it integrates the existing assets of ants / operating / Workflow and other basic platform data and capabilities , Enrich zero trust access context , Build multi-dimensional risk identification and diversified risk disposal capabilities , Ensure that users are more secure when accessing applications and data .

chart 8 Ant zero trust security architecture
3.2.1 SDP client
Ant office zero trust SDP client , It is mainly used for trust evaluation and localized security protection of terminals , At the same time SDP Gateway and controller are linked , Accurately identify assets , Effectively identify risks for near end access control , The following for SDP Key client security capabilities :
● Telecommuting
Secure access for remote office , Support multiple link channels , Link to the company intranet .
Telecommuting network acceleration ,SSH Link background services , Process service management and maintenance .
● Terminal data protection
For software on the computer 、 System and other settings , Such as virus detection 、 Software control 、U Coil control 、 File protection .
Support terminal health detection , Find safety problems in time , It provides a powerful guarantee for the computer security of enterprises .
● Illegal application detection
Identify and check unsafe applications .
● Asset inventory
Support to view hardware information 、 Quickly export asset information 、 Timely remind hardware changes , All equipment of the company shall be under unified safety management .
Check the relationship between people and equipment , Asset information verification .
● Safety reporting
Support users to report security problems : Copy and outgoing report for record 、 account number / Equipment borrowing 、 High risk software installation application , More human it management , Timely grasp risk information .
● User self management :
Trusted device management , Satisfy users BYoD The needs of , Support adding personal devices , Bring the equipment into the zero trust management system .
3.2.2 SDP gateway
SDP The gateway is at the zero trust protection traffic entry position , Mainly as SDP Strategy execution point , At the same time, it is used to hide applications and reduce the attack surface , And provide SSL Secure links and dynamic load balancing capabilities .
●SDP Strategy execution point
SDP The gateway is the enforcement point for running resources and security policies , The gateway supports dynamic plug-in functions , Respond to requests .
● Hide apps
Provide external access , Through the seventh floor HTTP agent , Or four layer network traffic proxy , Implement the proxy of internal resources to external access .
Apply port concealment to prevent scanning .
Hide protected resources , The Internet is invisible , Greatly reduce the network exposure , Effectively mitigate a variety of network attacks .
● Dynamic load balancing : It provides internal protection for internal services , It also provides load balancing for applications 、 The ability to divert .
●SSL Security link : Support SSL uninstall
3.2.3 SDP controller & IAM
Here's the picture 9, Zero trust in ant office SDP Controller construction , In the early stage, basic components are mainly established to meet the basic control requirements , Subsequently, with the upgrading of security risk management and control , It has experienced multiple version iterations , The zero trust scripted protection rules in the early basic version are iterated step by step , Complete the unification of security protection rule engine based on big data system . The current focus is on SDP client + gateway + controller + IAM Realize integrated dynamic protection , Zero trust access context Context take ( End health 、 Location 、 Time 、 The Internet 、 application 、 Intelligence, etc ) Information and data are introduced into the continuous trust evaluation engine for multi-dimensional calculation ; At the same time, it also increases the richer risk handling capacity ( for example : Risk behavior control 、 Approval and filing, etc ); Connection between identity authentication and access management , It also provides adaptive authentication and Context Context access control capability ; Support FIDO2 (Windows HELO/MacOS TouchID) The blessing of the new authentication method , Better improve the user experience .
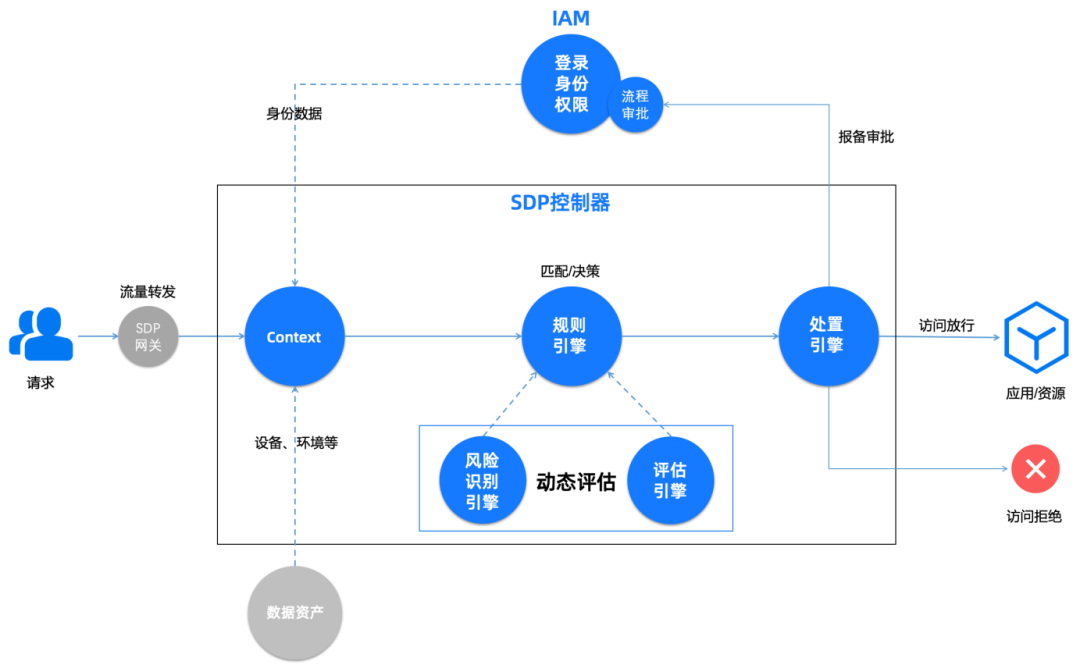
chart 9 Ant office zero trust SDP controller &IAM
3.3 Ant office zero trust landing practice
Ant office zero trust builds an integrated office zero trust security management and control platform with identity as the boundary , Polish and blend SDP( client + gateway + controller )+EIAM+MSG Zero trust core technology , Implement continuous authentication for each access request , Can identify all kinds of abnormal behaviors 、 Sensitive data presentation 、 Unauthorized access 、 Identity theft 、 Documents are sent out 、 Threat attack and other risks , To solve the problem of access control risk in the process of the subject accessing the object, and to reinforce and protect the data .
Ant office has a new security architecture with zero trust , Integrate multi-dimensional trust sources ( personnel 、 End 、 Network and application, etc ), Build multidimensional and three-dimensional zero trust evaluation capability , It has dynamic and diversified multi-dimensional control means for various risks , Provide applications /URL Zero trust control 、 Office data protection 、 Zero trust integrated protection capability .

chart 10 Ant office zero trust integrated protection
The difficulty in the implementation of zero trust products lies in the environment and IT Differences in facilities , How to quickly meet the security needs of different enterprises with one set of products . Ant office zero trust starts from the request originator 、 Internal engine 、 Disposal means and basic platform , Componentize the core modules of the zero trust system , External docking standardization 、 Terminal equipment trustworthiness , And lighten the dependent basic services . Pictured above 10, The system supports a variety of trusted terminals , And put the end information in Context Layer data model standardization 、 The internal rules engine is the core to handle the risk flow 、 Relying on the evaluation engine and risk analysis engine of big data , Support zero trust protection rule dynamic , And provide diversified strategy configuration for operators , Meet extensible 、 Various means of disposal .
For risks that are difficult to define “ ash ” Traffic , Support secondary core / Approval and filing and other differentiated risk confirmation behavior control capabilities , It can identify and intercept employees' malicious access behavior , Prevent unauthorized access . The zero trust system can also be connected to the original employee systems of different enterprises 、 Foundation platform 、 Asset system, etc , These systems provide a variety of access context data bases for zero trust , And then support the engine to provide more complete and reliable evaluation and judgment . The ant office zero trust system gets through the staff 、 End 、 Full link security dynamic protection of Guanhe cloud , Ensure the security of the enterprise's internal network and the new environment .
High cost for enterprise data protection access & Cover difficult problems such as easy omission , Zero trust protection expands data protection scenarios , Sensitive data identification 、 Web watermarking and zero trust , Provide security protection capability implantation without business intrusion , Support data protection capability, non inductive and minimal access, and fast and low-cost protection capability coverage .
04
Future outlook
Domestic zero trust is currently in the stage from concept to implementation , Focus on customer needs 、 Value and effectiveness are particularly important , Focus on simpler & More secure & Faster zero trust protection , Oppose the generalization of zero trust 、 Indiscriminate and conceptualized . Different industries have different concerns about the application of zero trust , Remote access is the main driver and priority for enterprises to implement zero trust , Most of the products of the industry focus on this field , Telecommuting 、 Remote branch access 、 The three scenarios of remote operation and maintenance account for the top three , It needs to be polished during landing .
In practice , Ant office zero trust product design takes identity as the boundary SDP( client + gateway + controller ) And enterprise modern identity access management EIAM、 The trust evaluation decision is accurate and complete 、 The core of safety protection components is rich and flexible , Will identity 、 System 、 data 、 End deep fusion , Building a multidimensional and three-dimensional zero trust evaluation system to meet the requirements of safe water level in the new environment . Standardize interfaces and data 、 Business specific scripting , Low cost horizontal expansion , Improve the ability of rapid integration of security components , Improve the protective water level and the ultimate user experience , Build an integrated active safety protection system .
On the road of zero trust security , Ants will continue to explore .
reference
[1] Jeffr Pack, Betsy Beyer, Colin Beske and Max Saltionstall.Migrating to BeyondCorp[EB/OL].USENIX.2018
[2] Rory Ward and Betsy Beyer.A New Approach to Enterprise Security[EB/OL].USENIX.2018
[3] Barclay Osborn, Justin McWillias, Betsy Beyer and Max Saltionstall.Design to Deployment at Google[EB/OL].USENIX.2018
[4] Luca Cuttadinim, Batz Spear, Betsy Beyer and Max Saltonstall.The Access Proxy[EB/OL].USENIX.2018
[5] Victor Escobedo, Batz Spear, Max Saltonstall and Filip Zyzniewski.The User Experience.[EB/OL].USENIX.2018
This article is from WeChat official account. - Alipay Technology (Ant-Techfin).
If there is any infringement , Please contact the [email protected] Delete .
Participation of this paper “OSC Source creation plan ”, You are welcome to join us , share .
边栏推荐
- Performance test - LoadRunner obtains the return value and user-defined parameters (parameter operation)
- 5 minutes to explain what is redis?
- Error message - Customizing incorrectly maintained – in transaction code ML81N
- Tencent News's practice based on Flink pipeline model
- Core features and technical implementation of FISCO bcos v3.0
- How does the national standard gb28181 security video platform easygbs download device video through the interface?
- Targeted, real-time audio and video optimization in remote control
- Shell automatically obtains hardware information
- Trident tutorial
- How does the fortress machine log in to the production server? What is the function of the fortress machine?
猜你喜欢
Game security - call analysis - write code

Opengauss Developer Day 2022 was officially launched to build an open source database root community with developers

解密抖音春节红包背后的技术设计与实践

Pourquoi une seule valeur apparaît - elle sur votre carte de données?

应用实践 | Apache Doris 整合 Iceberg + Flink CDC 构建实时湖仓一体的联邦查询分析架构
Beauty of script │ VBS introduction interactive practice

In the eyes of the universe, how to correctly care about counting East and West?

Hackinglab penetration test question 8:key can't find it again

Slsa: accelerator for successful SBOM

脚本之美│VBS 入门交互实战
随机推荐
Beauty of script │ VBS introduction interactive practice
Six supervised learning methods: classification of poisonous mushrooms
Heat transfer oil electric heater
Application practice | Apache Doris integrates iceberg + Flink CDC to build a real-time federated query and analysis architecture integrating lake and warehouse
5 minutes to explain what is redis?
2008R2 CFS with NFS protocol
[tutorial] build a personal email system using Tencent lightweight cloud
The old CVM of Tencent cloud is migrated to the new CVM, and the IP remains unchanged
Use elastic security to detect the vulnerability exploitation of cve-2021-44228 (log4j2)
Semaphore semaphore details
在宇宙的眼眸下,如何正确地关心东数西算?
How do fortress computers log in to the server? What is the role of the fortress machine?
How to set dynamic background for website construction what are the benefits of dynamic background
The article "essence" introduces you to VMware vSphere network, vswitch and port group!
Opengauss Developer Day 2022 was officially launched to build an open source database root community with developers
Intelligent storage | high speed HD media processing capability
Talk about the problems and solutions of IT enterprise fixed assets management system
Role of API service gateway benefits of independent API gateway
Introduction to tcapulusdb lossless relocation
SLSA: 成功SBOM的促进剂


