当前位置:网站首页>NFT Platform Security Guide (2)
NFT Platform Security Guide (2)
2022-06-26 15:45:00 【NFT practitioner】
Immutable
Immutable For high quality 、 Highly scalable NFT project ( As the game ) And build a platform .Immutable Some famous projects in the past include Illuvium、Gods Unchained、Ember Sword and Guild of Guardians.
Consensus security
Immutable It's a zk-rollup, Use StarkWare Of StarkEx prove / Verify the system build . It means Immutable Yes L2 Transaction batch sorting , And generate a STARK To prove that these transactions are valid , Then submit the certificate to a L1 Smart contract “ Validator ” in , The validator updates some L1 state ( In our case , Refers to millions of users NFT/ The root of the balance Merkel tree ). It is important to , This is much more scalable than simply packaging transactions into batch transactions , because STARK The verification cost of proof increases linearly with the number of transactions .

Because all state transitions must obtain L1 Verification of smart contracts , therefore Immutable You can never put an invalid transaction into rollup in , Or steal user assets , Even in the Immutable You can't do it when your system is completely destroyed . This is an extremely powerful security attribute , That's why Vitalik call rollup by “ Ethereum is the key expansion solution in the foreseeable future ”.
However ,Immutable With “ Single operator ” rollup In the form of ( Only Immutable Able to sort or justify transactions ). It means Immutable can Extract by rushing or reordering transactions MEV. at present , Almost all rollup All are “ Single operator ” The pattern of , But most plan to gradually decentralize their rollup.
Bridging safety
Rollup A completely different bridge structure from the side chain is used , Because they are L1 Maintain a proven “ state ”, And this “ state ” Only through a valid certificate can it be updated to L1 On . If users want to bridge assets , The verified status must include the user's deposit / To withdraw money —— There is no multi sign system that can be attacked ( Such as Ronin), You can't add... By attacking the verifier's private key " invalid " State transition ( Such as Polygon) —— Every transaction has been verified , It's like this deal happened in L1 It's the same . This bridge to trust is to make rollup go by the name of “L2” Why —— Their security directly depends on the consensus of Ethereum , Instead of relying on a separate consensus mechanism with a trusted bridge .


At any time , Users can submit a “ To withdraw money ” transaction , Transfer their assets from L2 Bridge to L1. If Immutable Include this transaction in a proven set of state changes , Users can confidently mention their assets directly to Ethereum . If Immutable The withdrawal was not executed ( Whether due to system unavailability or deliberate review of transactions ), Users can always communicate directly with L1 Bridge contract interactions to perform “ Full withdrawal ” technological process .
If this newly submitted “ Full withdrawal ” The request was not answered , The transaction status will be frozen , All users will then be able to perform withdrawals by providing their asset path in the status Merkel tree . Even if Immutable Do evil or go offline , Can ensure that users can access these data , This is it. “rollup Data availability issues ”. In standard zk-rollup In structure , There is a simple solution : It is required to publish the necessary data to Ethereum before allowing status update L1 On . However , This introduces a small linear gas cost , And many apps are reluctant to pay . This cost will not change after the merger , But it will pass EIP-4488、proto-danksharding and ( The final ) sharding And so on , Because Ethereum accepted it as rollup The role of the basic verification and data availability layer .
However , Because these solutions are not online , And publish on the chain calldata The cost is for those who need high scalability NFT Casting such use cases is still prohibitive . Fortunately, ,Immutable Now as a validium rollup function .Validium rollups such zk-rollups Do not publish all the data needed to rebuild the State , In exchange for cheaper transaction fees . To ensure that these data are even in Immutable Still available offline or when doing evil ,Immutable Depends on a “ Data availability Committee ” (Data Availability Committee, DAC). This committee ( Composed of famous companies in the ecosystem ) The vast majority of the members and a few “ mandatory ” Members must sign each transaction batch , To prove that they have the necessary data . This is different from the multi signature mode of verifier : Just one of them DAC Members are honest , Users can successfully withdraw money . Even in all DAC And sequencer are being compromised in a data retention attack ,Immutable Contract upgrades can still be used to prevent blackmail attacks .

Immutable Of rollup The verifier contract can be upgraded , But there will be a period of 14 Days of time lock , If users are not satisfied with the new contract, they can have the opportunity to exit the system ( Even in the Immutable In the case of malicious review of transactions ).
Immutable positive Volition Pattern shift , In this mode , individual “ Vault ” ( user 、 Tokens, 、 Number tuple ) Can be marked as requiring data on the chain . Because it's stored in rollup Most of the value is either the balance with many tokens /ETH The account of , Or collect high-value NFT, These values can be stored in a relatively small chain data repository . This structure may make rollup Most of the value in the Treasury is supported by data on the chain , Reduce data availability risk , At the same time, keep it cheap 、 Highly scalable NFT The ability to cast , This is very important for games and other projects .
Solana
Solana As a completely independent L1 Blockchain operation , Through one Custom consensus mechanism Focus on achieving low cost 、 Highly scalable transactions .
Consensus security
Solana There are currently more than 1500 Active nodes , But it does impose... On these nodes High hardware requirements To achieve its higher TPS ( However, this reduces the ability of individuals to participate in verification transactions , This is a very important principle for the decentralization of blockchain ). It is important to , only 20 Nodes Such a small number of people hold online pledge SOL Token 33% above . If these nodes conspire , Or being attacked , They can shut down the network or arbitrarily censor transactions .
Bridging safety
As a completely independent L1,Solana There is no official bridge between and Ethereum . however , Yes Solana Most commonly used by users ( Semi official ) The bridge is Wormhole ( Wormhole ), It allows the transfer of assets between multiple chains .Wormhole The security of Depending on a group called guardian ( The guardian ) The verifier of , All bridging deals need to be done ⅔+1 Of PoA Consensus . There are 19 An active guardian . because Solana The transaction with Ethereum cannot be verified , When users need to bridge assets , The bridge contract depends entirely on the consensus reached by the guardian . It means , If ⅔ Your guardian has been attacked ,Wormhole All user assets in the can be stolen . This mechanism is actually related to Ronin The mechanisms used are very similar , And unfortunately , The guardian's private key must also remain online to sign new transactions .

stay 2022 Beginning of the year ,Wormhole One of the bridges bug bring 3.25 Billion dollars of user funds were stolen . This incident is not actually an attack on the verifier system , Instead, the attacker discovered a vulnerability in a smart contract , And through this loophole, cheat and Bridge in Solana No deposit on Ethereum was made on the issue ETH.Jump Crypto Intervention allows users to get compensation —— This is a surprising indication of how much assets are in the pocket of cryptocurrency , But with the development of this field , This is a completely unsustainable model . This is not true Solana or Wormhole The charge of —— All systems on the chain are prone to smart contract vulnerabilities . Although there can be no absolute guarantee , But it's best to use audited or formally validated contracts , The contract has stood the test of time and public scrutiny —— for example ,Wormhole After the loophole appeared, it was strictly examined , No more loopholes were found later .
Optimism
Optimism It's a by Optimism PBC The development of Ethereum optimistic rollup. It's on 2021 year 8 Monthly online main network ( The white list system is adopted at the initial stage of launch ), up to now ,NFT The application of the project is limited , But in the Quixotic When there is an early community in the market .
Consensus security
Optimistic rollup The principle of operation is similar to zk-rollup: Collect transactions and upload a compressed version of the final state of all these state transitions . However , When zk-rollups Provide one for each state transition “ Proof of validity ” when ,optimistic rollup The state transition of is assumed to be effective , Unless someone can come up with a ” Proof of fraud “, This means that the transaction is invalid . A person who proves fraud will be rewarded , And those who publish invalid transactions will be punished . To allow this challenge to happen ,optimistic rollup There needs to be a one week delay before the transaction is fully finalized . This asynchrony introduces an interesting class of Potential economic attack , Mitigating these attacks is an active research topic .
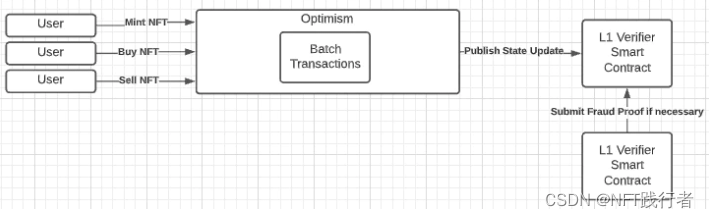
However ,Optimism Of Fraud proofing is currently prohibited —— signify Optimism ( Or any damage Optimism People with polysemy ) You can steal all user funds by submitting invalid state transitions . Of course , This is a temporary situation , Once the new fraud proof system is ready , It will be upgraded , But in the current state, this poses a serious threat to users' funds . because Optimism It is the of a single ordered person rollup, It will also face potential MEV extract .
Bridging safety
Optimistic rollup It also provides a trust bridge to Ethereum . However , Because any user can challenge the validity of this batch of transactions at any time during the dispute period of one week , Be withdrawn to L1 At least for this period of time . For homogeneous token assets , have access to “ Quick cash out ” To avoid this asset lock-in ( Assuming that the state transition does not include fraudulent transactions , Effectively lend to users ). However , because NFT Is unique and cannot be replaced , Users must wait for the entire dispute period ( For a week ), Then they can transfer their assets back to Ethereum L1 On .
Optimism ( Like all optimisitic rollup equally ) Intermediate transaction data need to be released on the chain , So it can be effectively challenged —— This incurs higher costs , But it avoids any complex data availability Architecture , As in analyzing Immutable As in the discussion .
Security that needs to be considered outside the core platform
If the security of your project is attacked by other mechanisms , So even if this project is on the core platform with the best security . In order to really make a wise decision ,NFT The project also needs to consider consensus / Factors other than bridging safety , Include :
- Wallet security : How the user's private key is stored ? If this storage system is attacked , What will be the impact ( for example , A vendor hosting a wallet , Some bad local wallet app , A poor quality browser extension depends on )?
- Metadata security : Metadata of assets ( Include images ) How is it stored ? If these metadata are changed or replaced due to an attack , What impact will it have on the market ?
- Project safety : Projects on any platform usually keep some administrator private keys for their projects . If these private keys are attacked , What's going to happen ? Does your project have the ability to actively monitor vulnerabilities ? Does your platform support best practices for private key management ?
- Treasury security : Most platforms have large token reserves ( for example , To reward or subsidize ). How these funds are kept ? How to authorize and execute the asset transfer in the Treasury ? What will be the impact if attacked ?
- Market security : How the market supporting the agreement protects users , Let it avoid malicious transactions like Shanzhai projects ?
Any link mentioned above is attacked , May harm users who have the most secure underlying platform —— obviously , No one can be trusted to boast that his project is impeccable . Unfortunately , When dealing with a new asset class , In particular, an asset class that has grown so rapidly , There will be some people constantly looking for new vulnerabilities and exploitable points . In such an environment , When choosing the right platform for your project , It's important to fully understand the trade-offs you face .
边栏推荐
- 【文件】VFS四大struct:file、dentry、inode、super_block 是什么?区别?关系?--编辑中
- 手机上怎么开户?在线开户安全么?
- Database - sequence
- 【leetcode】112. 路径总和 - 113. 路径总和 II
- JS simple deepcopy (Introduction recursion)
- 【ceph】CephFS 内部实现(三):快照
- 我想知道如何通过线上股票开户?在线开户安全么?
- 买股票通过券商经理的开户二维码开户资金是否安全?想开户炒股
- IntelliJ idea -- Method for formatting SQL files
- 为什么图像分割任务中经常用到编码器和解码器结构?
猜你喜欢

IDEA本地代理后,无法下载插件

Don't remove custom line breaks on reformat
![[tcapulusdb knowledge base] Introduction to tcapulusdb system management](/img/5a/28aaf8b115cbf4798cf0b201e4c068.png)
[tcapulusdb knowledge base] Introduction to tcapulusdb system management
![[file] VFS four structs: file, dentry, inode and super_ What is a block? difference? Relationship-- Editing](/img/b6/d288065747425863b9af95ec6fd554.png)
[file] VFS four structs: file, dentry, inode and super_ What is a block? difference? Relationship-- Editing

HW safety response

【ceph】cephfs的锁 笔记

【问题解决】新版webots纹理等资源文件加载/下载时间过长
![[tcapulusdb knowledge base] tcapulusdb OMS business personnel permission introduction](/img/7b/8c4f1549054ee8c0184495d9e8e378.png)
[tcapulusdb knowledge base] tcapulusdb OMS business personnel permission introduction

Analysis of ble packet capturing debugging information

High frequency interview 𞓜 Flink Shuangliu join
随机推荐
AbortController的使用
Don't remove custom line breaks on reformat
2Gcsv文件打不开怎么处理,使用byzer工具
【SNMP】snmp trap 介绍、安装、命令|Trap的发送与接收代码实现
【ceph】CEPHFS 内部实现(一):概念篇--未消化
音视频学习(三)——sip协议
我想知道如何通过线上股票开户?在线开户安全么?
【leetcode】112. 路径总和 - 113. 路径总和 II
svg野人动画代码
How to configure and use the new single line lidar
[tcapulusdb knowledge base] tcapulusdb system user group introduction
【TcaplusDB知识库】TcaplusDB单据受理-创建游戏区介绍
Utilisation d'abortcontroller
JS之手写 bind、apply、call
[tcapulusdb knowledge base] tcapulusdb operation and maintenance doc introduction
[tcapulusdb knowledge base] tcapulusdb doc acceptance - table creation approval introduction
NFT 项目的开发、部署、上线的流程(1)
svg canvas画布拖拽
AUTO sharding policy will apply DATA sharding policy as it failed to apply FILE sharding policy
Summary of students' learning career (2022)