当前位置:网站首页>Echo framework: implementing timeout Middleware
Echo framework: implementing timeout Middleware
2022-06-24 01:20:00 【Trespass 】
Introduce
Through a complete example , Based on Echo Framework in microservices 【 Overtime 】 middleware .
We will use rk-boot To start up Echo Microservices of the framework .
Please visit the following address for a complete tutorial :
install
go get github.com/rookie-ninja/rk-boot go get github.com/rookie-ninja/rk-echo
Quick start
Support global timeout and API Timeout settings .
1. establish boot.yaml
boot.yaml File tell rk-boot How to start Echo service .
In order to verify , We launched the following options :
- commonService:commonService It contains a series of general API. details
Set the global timeout to 5 second , Give Way GC The timeout for is 1 millisecond ,GC Usually more than 1 millisecond .
---
echo:
- name: greeter # Required
port: 8080 # Required
enabled: true # Required
commonService:
enabled: true # Optional, Enable common service for testing
interceptors:
timeout:
enabled: true # Optional, default: false
timeoutMs: 5000 # Optional, default: 5000
paths:
- path: "/rk/v1/gc" # Optional, default: ""
timeoutMs: 1 # Optional, default: 50002. establish main.go
// Copyright (c) 2021 rookie-ninja
//
// Use of this source code is governed by an Apache-style
// license that can be found in the LICENSE file.
package main
import (
"context"
"github.com/rookie-ninja/rk-boot"
_ "github.com/rookie-ninja/rk-echo/boot"
)
// Application entrance.
func main() {
// Create a new boot instance.
boot := rkboot.NewBoot()
// Bootstrap
boot.Bootstrap(context.Background())
// Wait for shutdown sig
boot.WaitForShutdownSig(context.Background())
}3. start-up main.go
$ go run main.go
4. verification
send out GC request .
$ curl -X GET localhost:8080/rk/v1/gc
{
"error":{
"code":408,
"status":"Request Timeout",
"message":"Request timed out!",
"details":[]
}
}边栏推荐
- [applet] indicator of relative path and absolute path
- ShardingSphere-proxy-5.0.0容量范围分片的实现(五)
- "Ai+ education" and "Ai education": one for education and the other for Education
- How to view kubernetes API traffic by grabbing packets
- Golang gets the start timestamp and end timestamp of a past or future week or month
- 4 most common automated test challenges and Countermeasures
- Architecture solutions
- 【Flutter】如何使用Flutter包和插件
- version `ZLIB_1.2.9‘ not found (required by /lib64/libpng16.so.16)
- How to build a "preemptive" remote control system (- - memory chapter)
猜你喜欢

ShardingSphere-proxy-5.0.0容量范围分片的实现(五)
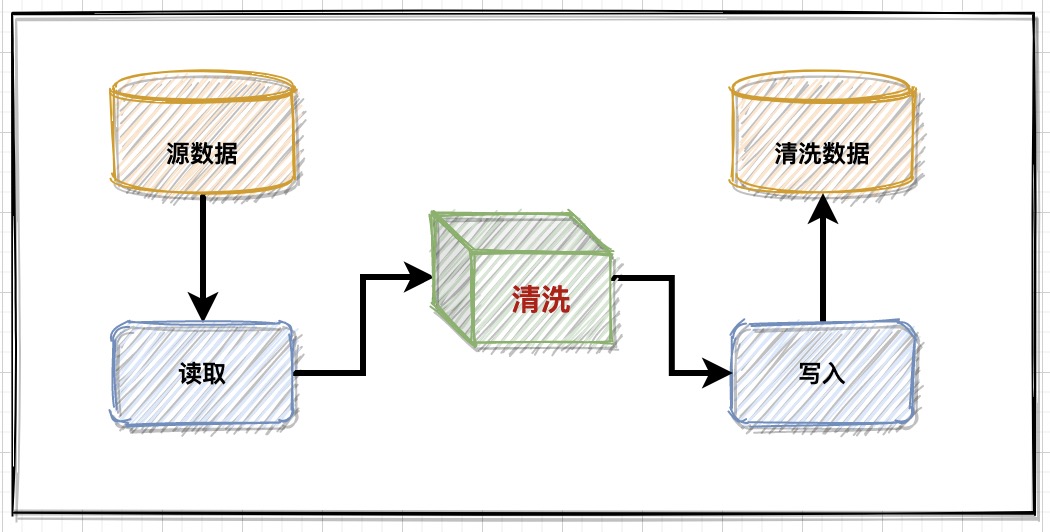
Data management: business data cleaning and implementation scheme

Open source model library of flying propeller industry: accelerating the development and application of enterprise AI tasks
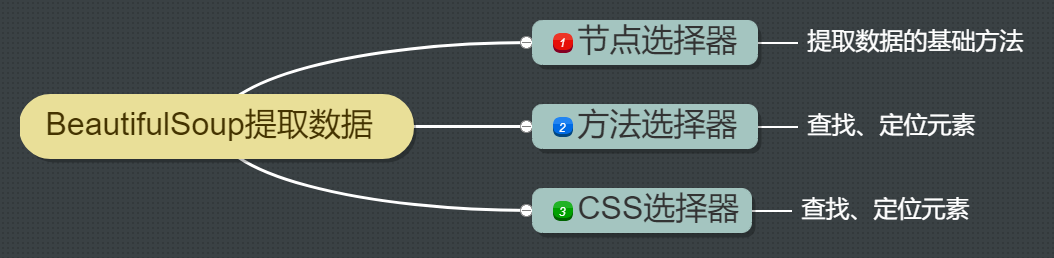
13 `bs_duixiang.tag标签`得到一个tag对象

13 `bs_ duixiang. Tag tag ` get a tag object

The concept of TP FP TN FN in machine learning

机器学习中 TP FP TN FN的概念

应用配置管理,基础原理分析

How to write peer-reviewed papers

Niu Xuechang's anniversary celebration: software promotion, limited time and free registration code!
随机推荐
Thread safety and lock optimization
One article introduces you to the world of kubernetes
Why traifik ingress?
Vs2022 save formatting plug-in
numpy.linalg.lstsq(a,b,rcond=-1)解析
Zhongshanshan: engineers after being blasted will take off | ONEFLOW u
The dispute between traditional IT development and low code development is heated, and the technical development rules may be restructured?
Force buckle deletes duplicates in the sort array
Coordinate system "slang" in GIS world
Niu Xuechang's anniversary celebration: software promotion, limited time and free registration code!
An accident caused by a MySQL misoperation, and the "high availability" cannot withstand it!
Law / principle / rule / rule / theorem / axiom / essence / Law
S2b2c e-commerce platform in the pharmaceutical and medical industry enables enterprises to grasp differentiated competitive advantages and improve supply chain efficiency
Data management: business data cleaning and implementation scheme
Use recursion to form a multi-level directory tree structure, with possibly the most detailed notes of the whole network.
Intelligent + fault-tolerant server is the best partner in the edge computing scenario
Millions of routers are at risk of attack, and hackers supported by North Korea are invading the United States and Britain | November 19 global network security hotspot
CODING CD
Attack and defense world PyC trade
jdbc