当前位置:网站首页>Software component analysis: 5 major capabilities to protect software supply chain security
Software component analysis: 5 major capabilities to protect software supply chain security
2022-08-02 12:19:00 【InfoQ】
This article is shared from HUAWEI CLOUD Community "
HUAWEI CLOUD Releases Open Source Software Governance Services - Software Component Analysis
", author: HuaweiCloud PaaS service Xiaozhi.
Software component analysis, which refers to the static analysis of software source code, binary software packages, etc., to discover security compliance risks such as open source compliance and known vulnerabilities.A common security testing method; recently, HUAWEI CLOUD, with its leading edge in software component analysis products and technologies, passed the evaluation of the Institute of Information and Communications Technology and won the evaluation certification of open source governance tools.

Forge open source governance tools and protectYour software supply chain security
- No need to rely on source code
Users only need to upload binary packages/Firmware, the service will use static detection technology to quickly analyze the security risk issues in binary software packages/firmware without building a running environment or running a program, and output a professional analysis report.
- Independent of the architecture platform of the object under test
Supports desktop (Windows and Linux) applications, mobile applications (APK, IPA, Hap, etc.), embedded system firmware (u-boot, Android sparse, etc.), etc.
- Mainstream programming languages are fully supported
Support C/C++, Java, Go, Python,JavaScript, Rust, etc., the coverage of languages continues to increaseVulnerability library capability to actively manage newly discovered vulnerability alerts in the BOM of the historical scanning software.
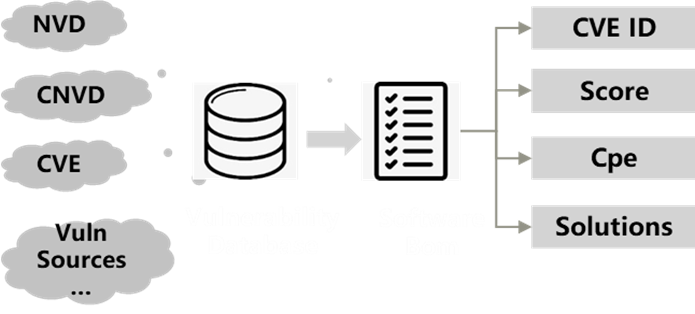
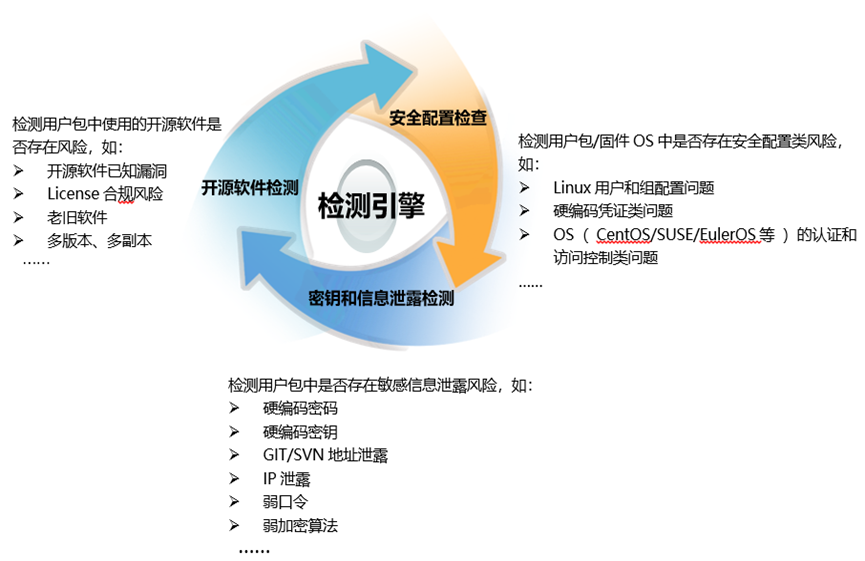
- Strong risk detection capabilities, and rules continue to increase
Provide comprehensive and rapid investigation capabilities for risks in user release packages/firmware packages, covering open source softwareThere are 3 major categories of 26 sub-categories of risk, information leakage risk, and configuration risk, and the detection rules continue to increase.
Passed the evaluation of CITIC and won theOpen source governance tool evaluation certification
Trusted open source governance tool (SCA), as the most important detection tool in trusted open source, provides enterprises and evaluation agencies to use open source software to determine whether software products are safe or not.Provides an automated detection capability and quantifiable, visual detection results.
At the "OSCAR Open Source Pioneer Day" meeting in May this year,
Huawei Cloud Computing Technology Co., Ltd.'s R&D security service (component analysis) (SaaS version) passed theCertification of the Trusted Open Source Governance Tool of the China Academy of Information and Communications Technology
, and has provided commercial services on Huawei's public cloud.

HUAWEI CLOUD DevCloudWe have been committed to providing customers with an R&D environment that improves end-to-end efficiency and provides full-link security. Huawei's R&D tool capabilities continue to spill over. Currently, HUAWEI CLOUD software component analysis provides binary component analysis capabilities. Source code analysis will be officially released in the future, so stay tuned.
Click to follow and learn about HUAWEI CLOUD's new technologies for the first time~
边栏推荐
- Create an application operation process using the kubesphere GUI
- Problem solving in the process of using mosquitto
- kvm部署
- An example of type3 voltage loop compensator taking Boost as an example
- CCF paper conference IEEE how to query all articles of a conference journal
- 1.3快速生成树协议RSTP
- 【Acunetix-忘记密码】
- Pytorch 占用cpu资源过多
- SQL函数 TRIM
- 智能图像分析-智能家用电器图像目标检测统计计数检测与识别-艾科瑞特科技(iCREDIT)
猜你喜欢
随机推荐
解决anaconda下载pytorch速度极慢的方法
Crack detection technology based on deep learning
喜迎八一 《社会企业开展应聘文职人员培训规范》团体标准出版发行会暨橄榄枝大课堂上线发布会在北京举行
30行代码实现无服务器实时健康码识别--操作手册
面积曲线AUC(area under curve)
前男友买辣椒水威胁要抢女儿,女方能否申请人身安全保护令?
Leek 151 - Reverse words in a string
MD5 detailed explanation (check file integrity)
Hand rolled architecture, 41 Redis interview asked
翻译英语的软件-免费翻译软件-各种语言互相翻译
解决导出excel文件名中文乱码的问题
项目监控六大事项
QAbstractScrollArea、QScrollArea
中原银行实时风控体系建设实践
分布式限流利器,手撕&redisson实现
【项目管理技术的优势】
DTG-SSOD:最新半监督检测框架,Dense Teacher(附论文下载)
Chapter 14 Manually create a REST service (2)
redis cluster cluster, the ultimate solution?
NVIDIA NeMo Metrics 轻量性能采集系统