当前位置:网站首页>Is there anyone who plans to open source an industrial "seckill" system architecture?
Is there anyone who plans to open source an industrial "seckill" system architecture?
2022-06-23 09:46:00 【58 Shen Jian】
Want to figure out a set of architectural solutions , The most fundamental way , Is to go practice it .
But , Most programmers , There is no such business , I can't touch such a scene , What shall I do? ?
A friend set up a set automatically , can Let everyone instantly experience and tune the seckill architecture with high concurrency , Share with you !
For seckill business , On the system How can it be optimized ?
In the direction of , There are two main points :
First of all , Try to intercept the request upstream of the system , Don't let lock conflicts fall on the database .
The reason why the traditional seckill system hangs , It's because the requests are pushed to the back-end data layer , Data read-write lock conflict is serious , High concurrency and slow response , Almost all requests time out , High traffic , The effective flow of successful orders is small .
second , Make the most of the cache .
Second kill buy tickets , This is a typical business scenario with more reading and less writing :
(1) Train number inquiry , read , Large amount of ;
(2) Check the remaining tickets , read , Large amount of ;
(3) Order and pay , Write , Small quantity ;
Great for using caching to optimize .
Second kill business , How about the common system layered architecture ?

Second kill business , You can use a typical service layered architecture , How should these four layers be optimized ?
One 、 Request interception on end
JS level , You can restrict users to x Only one request can be submitted in seconds , So as to reduce the system load .
Voice over : Submit frequently , Friendly tips “ The frequency is too fast ”.
APP level , You can do something similar , Although users are crazily shaking wechat to grab red packets , But in fact x Seconds to send a request back .
Voice over : That's what's called “ Try to intercept the request upstream of the system ”, browser /APP Layer can intercept 80%+ Request .
Two 、 Site level request interception
How to resist programmers writing for Cycle call http Interface , The first thing to do is to identify the unique identity of the user , Block frequent users .
What to use as the unique identification of users ?
All ticket businesses need to log in , use uid Can identify users .
At the site level , To the same uid Request count and speed limit , for example : One uid,5 Seconds only pass through 1 A request , This will stop 99% Of for Loop request .
One uid,5s Only through a request , What about the rest of the requests ?
cache , Page caching ,5 Other requests to the site layer within seconds , All return to the last page .
3、 ... and 、 Request interception of service layer
Concurrent requests have reached the service level , How to intercept ?
The service level is very clear about the inventory of the business , Very clear about the database's ability to withstand pressure , According to these two, we can cut the peak and speed limit .
for example , Business services know very well , A train has nothing but 2000 Tickets , At this time, transmission through 10w Request to database , It doesn't make sense .
Voice over : If the database can only resist 500 Write a request , Just pass through 500 individual .
With what to cut the peak ?
Request queue .
For write requests , Make a request queue , Only a limited number of write requests are transmitted to the data layer at a time ( Place the order , Pay for writing business like this ).
Only 2000 Train tickets , Even if 10w Please come here , Only through transmission 2000 Go to the database :
(1) If all previous requests are successful , Put down another batch of ;
(2) If the previous request is out of stock , Then all subsequent requests return “ It's sold out ”;
For read requests , How to optimize the ?
cache resist , Whether it's memcached still redis, Single machine anti per second 10w There should be no problem .
Voice over : Expand the cache horizontally , It's easy to expand linearly .
Such peak clipping and current limiting , There are very few requests to write , And very little read caching mis The request will penetrate to the data layer , And then there is 99% Our request was stopped .
Four 、 Database layer
After the first three layers of optimization :
(1) The browser blocked 80% request ;
(2) The site layer intercepted 99% request , And do page caching ;
(3) Service layer according to business inventory , And the database's ability to withstand pressure , Write request queue and data cache are done ;
You'll find that , Every request that penetrates to the database layer is controllable .db Basically there's no pressure , walk .
Voice over : This kind of business data volume is not large , There's no need for sub Treasury , Make a highly available database .
According to the optimization scheme above , In fact, the most pressure is the site layer , Suppose that the number of real valid requests is... Per second 100w, How to deal with this part of the pressure ?
There are two ways to solve this problem :
(1) Site level expansion , Expand capacity by adding machines , A resistance 5W,20 It's done ;
(2) service degradation , Abandon the request , For example, abandon 50%;
The principle is to protect the system , Can't let all users fail .
How to experience the seckill business , Build a set of micro service layered seckill system architecture ?
(1) First , Buy hardware resources on the cloud ;
(2) next , Build the underlying foundation components : The storage system (MySQL、MongoDB、TiDB etc. )、 High performance cache system (Redis etc. )、 Highly reliable message system (RocketMQ、Kafka、Pulsar etc. )、 Search engine system (Elasticsearch、Solr etc. ) And many other basic components ;
(3) The third step , Build a microservice management platform :Docker Containers 、Kubernetes Management platform and other highly concurrent flexible container management platforms 、CI/CD And so on ;
(4) Step four , Build a micro service layered architecture : Low code microservice seckill business architecture design 、 Code landing 、 Test verification ;
(5) Step five , Optimize the three high design : Implement high performance 、 High availability 、 High reliability and other design guarantees , Ensure the robustness of seckill system ;
(6) Last , Set up a visual performance management background : It is convenient to see the throughput of the whole link of the system through three-dimensional and multi-dimensional visualization , Flow ;
Voice over : Put aside hundreds of thousands of machine costs , The whole stack 20 People build teams , One year can almost build a prototype .
Is there a quick way to experience ?
In order to make more children's shoes experience quickly “ seckill ” System architecture , My friend @ Xuanjie Founded Naixue , And lead the team through 2 Years of research and development , Created an exclusive set , Industrial grade “ Second kill architecture ” laboratory , It integrates all the above functions , The user only needs to open a web page , You can experience and code tuning “ Second kill architecture ”:
(1) left : Spike architecture knowledge points ;
(2) On the right side :terminal Direct connection server , Can operate ng,web-server,service etc. , You can modify the code directly , Tune the architecture ;
(3) meanwhile : There is also the background to manage the architecture , And visual monitoring .
Voice over : Details are shown below .
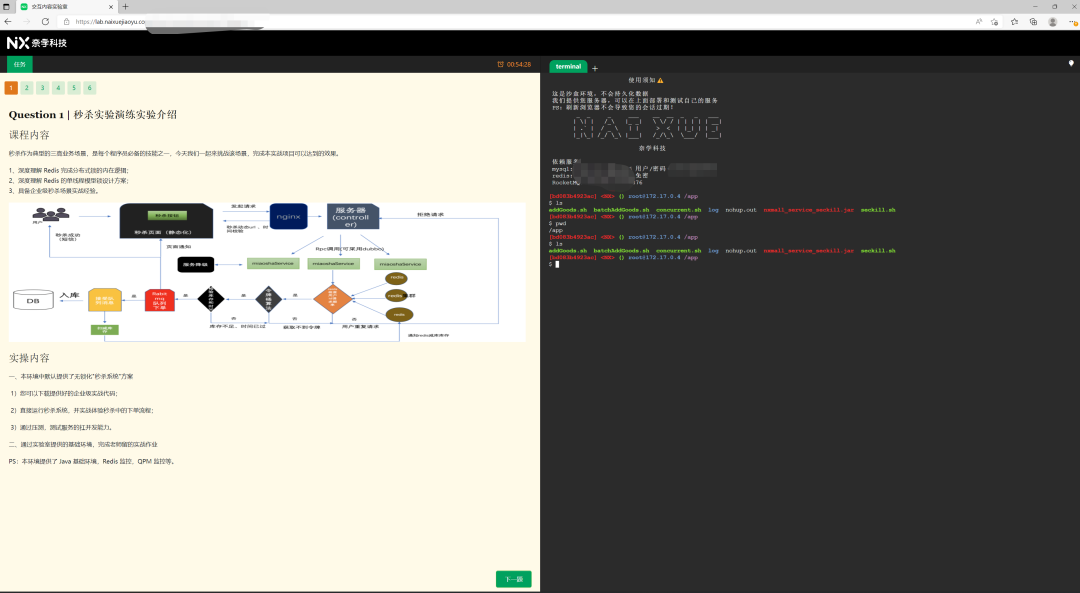
Figure 1 : left - Architecture diagram , On the right side - Practice environment

Figure 2 : left - Operation instructions , On the right side - One click automation architecture , Check the log

Figure 3 : left - Architecture description , On the right side - View and modify the code
 Figure 4 : Visualization platform
Figure 4 : Visualization platform
How to apply for experience ?

1 Meta scan code , Apply for the experience now , Only 100 Accounts
1 Meta scan code , Apply for the experience now .
meanwhile , Free gift :
(1)6.27-6.29, Explanation of secsha core architecture ;
(2) Industrial grade “ Second kill architecture ” Introduction to laboratory functions ;
(3) Source code and courseware ;
Explain , Due to engineering grade “ Second kill architecture ” The server resources required are large , Limited account , Front only 100 people .
Read the original , Get involved right now , Pro automatic handwriting code optimization , Actual industrial grade “ Second kill architecture ”.
边栏推荐
- [CISCN2019 华北赛区 Day2 Web1]Hack World
- Game of life of leetcode topic analysis
- Gorm 高级查询
- 薄膜干涉数据处理
- What is a closure function
- 快速排序的简单理解
- [plugin:vite:import-analysis]Failed to resolve import “@/“ from ““.Does the file exist
- 基於STM32設計的寵物投喂器
- Typora set up image upload service
- Redis learning notes - data type: ordered set (Zset)
猜你喜欢
Redis learning notes - publish and subscribe

Bioinformatics | effective drug target correlation prediction based on interacting neural network

Go语言JSON 处理
![[GXYCTF2019]BabySQli](/img/51/a866a170dd6c0160ce98d553333624.png)
[GXYCTF2019]BabySQli

Pizza ordering design - simple factory model

Go 单元测试

Go language JSON processing

基於STM32設計的寵物投喂器

cooding代码库的使用笔记

Zone d'entrée du formulaire ionic5 et boutons radio
随机推荐
JSP getting started summary
Gorm advanced query
漫画 | Code Review快把我逼疯了!
Zone d'entrée du formulaire ionic5 et boutons radio
Sequential representation and implementation of sequencelist -- linear structure
MySQL optimistic lock and pessimistic lock
Redis learning notes RDB of persistence mechanism
Bioinformatics | effective drug target correlation prediction based on interacting neural network
安装typescript环境并开启VSCode自动监视编译ts文件为js文件
ICLR 2022 | 视频中的动态卷积TAdaConv以及高效的卷积视频理解模型TAdaConvNeXt
mysql innodb 的 redo log buffer 中未 commit 的事务持久化到 redo log 后,万一事务 rollback 了怎么办?redo log 怎么处理这个事务操作?
Set the CPU to have 16 address lines and 8 data lines, and use mreq as the access control line number Connection between memory and CPU
How should junior programmers who enter a small company improve themselves?
Precautions for map interface
xml相关面试题
高性能算力中心 — RDMA — 实现技术
Three methods to find the limit of univariate function -- lobida's rule and Taylor's formula
swagger UI :%E2%80%8B
Redis learning notes - single key management
Embedded system overview (learning notes)
